

In This Section: |
From R80.20, ICAP Client functionality is available in Security Gateway, or Cluster.
Background
The Internet Content Adaptation Protocol (ICAP) is a lightweight HTTP-like protocol, which is used to extend transparent proxy servers. This frees up resources and standardizes the way in which new features are implemented. ICAP is usually used to implement virus scanning and content filters in transparent HTTP proxy caches.
The ICAP allows ICAP Clients to pass HTTP / HTTPS messages to ICAP Servers for content adaptation. The ICAP Server executes its transformation service on these HTTP / HTTPS messages and sends responses to the ICAP Client, usually with modified HTTP / HTTPS messages. The adapted HTTP / HTTPS messages can be HTTP / HTTPS requests, or HTTP / HTTPS responses.
ICAP is a request and response protocol that is equivalent in semantics and usage to HTTP/1.1. Despite the similarity, ICAP is neither HTTP / HTTPS , nor an application protocol that runs over HTTP / HTTPS . ICAP is specified in RFC 3507 (for more information, see ICAP Specification). In addition, see the Draft RFC - ICAP Extensions.
Usage Examples
ICAP packet structure
The ICAP protocol is encapsulated into the TCP protocol:

ICAP methods
Method |
Description |
|---|---|
REQMOD |
Client Request Modification. The ICAP Client uses this method for an HTTP / HTTPS request modification. |
RESPMOD |
Server Response Modification. The ICAP Client uses this method for an HTTP / HTTPS response modification. |
OPTIONS |
The ICAP Client uses this method to retrieve configuration information from the ICAP Server. |
ICAP decisions
ICAP Decision |
Description and Example |
|---|---|
Block |
|
Data Modification |
Modification of the HTTP content. For example, your Data Loss Prevention engine can replace the DOCX file attached to an email with a PDF file. |
Continue / Not modified |
Default gateway or Proxy server can forward the HTTP Request / Response to its original destination. |
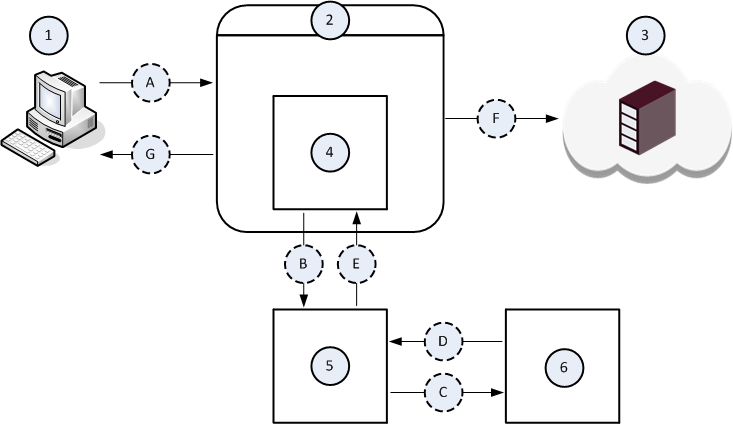
Example data flow in the Request Modification (REQMOD) mode
Item |
Description |
|---|---|
1 |
The Client computer. |
2 |
The Proxy server. |
3 |
The Server computer on the Internet. |
4 |
The ICAP Client component that runs on the Proxy server (2). |
5 |
The ICAP Server component that runs on some computer on the network. |
6 |
The Data Loss Prevention component that runs on some computer on the network. |
A |
The Client computer (1) initiates a file upload to the Server computer (3). |
B |
The ICAP Client component (4) intercepts the uploaded file and sends it to the ICAP Server component (5). |
C |
The ICAP Server component (5) forwards the uploaded file to the Data Loss Prevention component (6) for examination, whether the DLP policy allows this file to leave your network. |
D |
The Data Loss Prevention component (6) returns its verdict about the uploaded file. |
E |
The ICAP Server component (5) returns one of these to the ICAP Client component (4):
|
F |
The ICAP Client component (4) forwards the modified file from the ICAP Server component (5) to the Server computer (3). |
G |
The ICAP Client component (4) forwards the block message from the ICAP Server component (5) to the Client computer (1). |
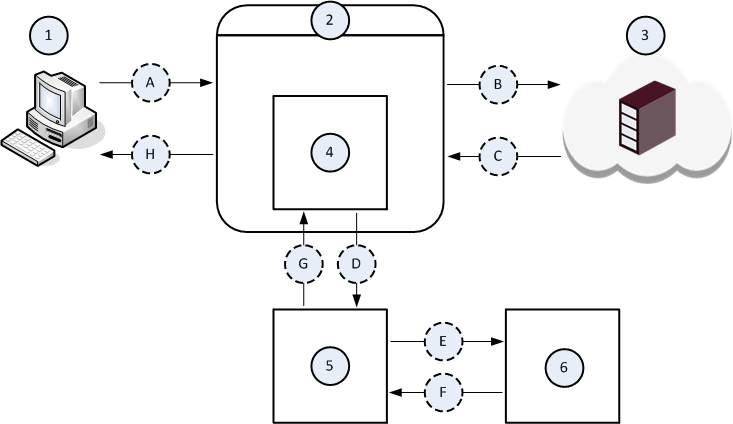
Example data flow in Server Response Modification (RESPMOD) mode
Item |
Description |
|---|---|
1 |
The Client computer. |
2 |
The Proxy server. |
3 |
The Server computer on the Internet. |
4 |
The ICAP Client component that runs on the Proxy server (2). |
5 |
The ICAP Server component that runs on some computer on the network. |
6 |
The Threat Emulation component that runs on some computer on the network. |
A |
The Client computer (1) initiates a file download from the Server computer (3). |
B |
The Proxy server (2) forwards the file download request to the Server computer (3). |
C |
The Server (3) sends the requested file. |
D |
The ICAP Client component (4) intercepts the downloaded file and sends it to the ICAP Server component (5). |
E |
The ICAP Server component (5) forwards the downloaded file to the Threat Emulation component (6) for examination, whether this file is malicious. |
F |
The Threat Emulation component (6) returns its verdict about the downloaded file. |
G |
The ICAP Server component (5) returns one of these to the ICAP Client component (4):
|
H |
The ICAP Client component (4) forwards one of these responses from the ICAP Server component (5) to the Client computer (1):
|
ICAP response codes
These are the ICAP response codes that are different from their HTTP counterparts (each code consists of 3 digits denoted as xyz):
Category |
Code |
Description |
|---|---|---|
1 |
100 |
Continue after ICAP preview. |
2 |
204 |
No Content. No modification is required. |
|
206 |
Partial Content. |
4 |
400 |
Bad request. |
|
404 |
ICAP Service not found. |
|
405 |
Method not allowed for service (for example, RESPMOD requested for service that supports only REQMOD). |
|
408 |
Request timeout. ICAP Server gave up while it waited for a request from an ICAP Client. |
|
418 |
Bad composition. ICAP Server needs encapsulated sections different from those in the request. |
5 |
500 |
Server error. Error on the ICAP Server, such as "out of disk space". |
|
501 |
Method not implemented. This response is illegal for an OPTIONS request, because implementation of OPTIONS is mandatory. |
|
502 |
Bad Gateway. This is an ICAP proxy, and the proxy operation produced an error. |
|
503 |
Service overloaded. The ICAP server has exceeded a maximum connections limit associated with this service. The ICAP Client should not exceed this limit in the future. |
|
505 |
ICAP version not supported by server. |