

In This Section: |
The Check Point Next Generation Security Gateway includes:
To configure an effective security solution, you must understand how to configure the Next Generation Security Gateway features, and how to add rules to your security policy. This guide helps you understand the general principles of the Check Point Next Generation Security Gateway, and how to configure it.
To learn more about each feature, look at the administration guide for the feature. There is a link to the appropriate administration guide at the end of each section of this guide. To find the link, search for "To Learn More".
Chapter |
|
Feature |
Section |
|---|---|---|---|
|
Firewall |
||
|
Application Control |
Creating a Unified Access Control Policy:
|
|
|
URL Filtering |
||
|
Content Awareness |
||
Mobile Access |
|||
|
IPsec VPN |
||
IPS |
|
||
Anti-Bot |
|||
|
Anti-Virus |
||
|
Threat Emulation |
||
|
Threat Extraction |
||
|
HTTPS Inspection |
||
|
Geo Policy |
||
|
Identity Awareness |
|
|
|
Logging & Status SmartEvent |
|
|
|
Advanced Networking & Clustering |
CoreXL, SecureXL and Multi-Queue
|
|
|
Virtual Systems |
|
|
|
Data Loss Prevention |
|
|
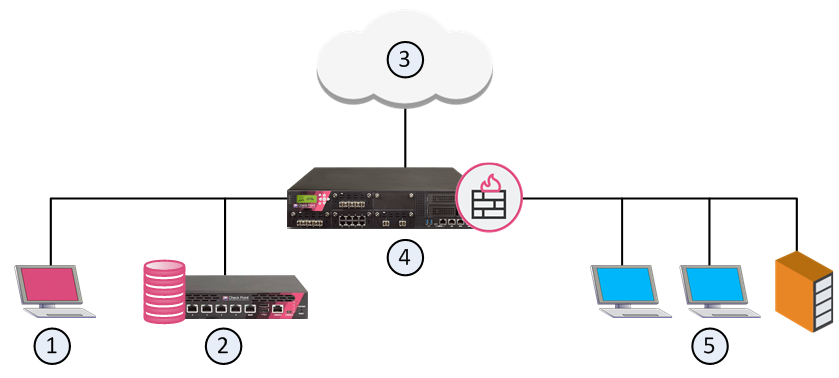
Item |
Description |
|---|---|
1 |
SmartConsole |
2 |
Security Management Server |
3 |
Internet and external networks |
4 |
Security Gateway |
5 |
Internal network |
These are the primary components of a Check Point firewall solution: