

In This Section: |
If no external Endpoint Policy Servers are configured, the Endpoint Security Management Server, which contains an Endpoint Policy Server, manages all client requests and communication.
If you install more Endpoint Policy Servers, they manage most communication with the Endpoint Security clients. This keeps the Endpoint Security Management Server more available for other tasks. If you configure the Endpoint Security Management Server to behave as an Endpoint Policy Server in addition to other Endpoint Policy Servers, the work of communication with the clients is distributed to them all.
We recommend that you use a distributed deployment that contains external Endpoint Policy Servers on dedicated computers.
An Endpoint Policy Server is a Log Server that you configure as an Endpoint Policy Server.
To install an Endpoint Policy Server:
To install Endpoint Policy Server, install a Log Server and configure it as Endpoint Policy Server. Use the instructions in the R80.20 Installation and Upgrade Guide.
To define a new Endpoint Policy Server:
The Endpoint Server window opens.
To edit an existing server, select it from the list and click Edit.
A warning pop-up window shows.
The Install Database window opens.
The Close button becomes available.
External Endpoint Policy Servers decrease the load of the Endpoint Security Management Server and reduce the bandwidth required between sites. By default, the Endpoint Security Management Server also acts as an Endpoint Policy Server, in addition to the other Endpoint Policy Servers. The work of communication with the Endpoint Security clients is distributed among all of them.
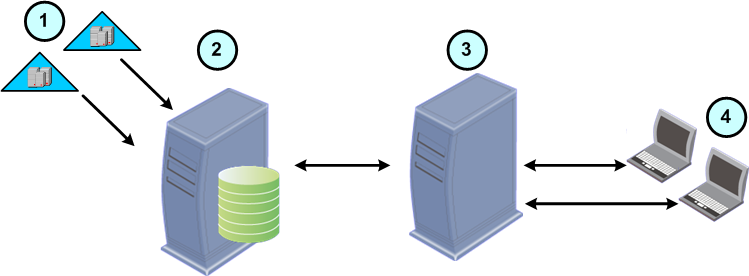
The Endpoint Policy Servers are located between the Endpoint Security clients and the Endpoint Security Management Server. For most tasks, Endpoint Security clients communicate with the Endpoint Policy Servers and the Endpoint Policy Servers communicate with the Endpoint Security Management Server.
If there are multiple Endpoint Policy Servers in an environment, each Endpoint Security client does an analysis to find which Endpoint Policy Server is "closest" (will be fastest for communication) and automatically communicates with that server.
Item |
Description |
|---|---|
1 |
Active Directory Domains |
2 |
Endpoint Security Management Server |
3 |
External Endpoint Policy Server |
4 |
Enterprise workstations with Endpoint Security clients installed |
The Endpoint Policy Server handles the most frequent and bandwidth-consuming communication. The Endpoint Policy Server handles these requests without forwarding them to the Endpoint Security Management Server:
The Endpoint Policy Server sends this data to the Endpoint Security Management Server:
The primary aspects of working with Endpoint Policy Servers that you can configure are:
In a large network, multiple Endpoint Policy Servers can be available for an endpoint client. In such an environment, the client does an analysis from a list of Endpoint Policy Servers to find the server closest to it. The client sends a specified HTTP request to all Endpoint Policy Servers on the list. The server that replies the fastest is considered to be closest.
The server list is an XML file named epsNetwork.xml. It is located at $UEPMDIR/engine/conf/ on the Endpoint Security Management Server. It contains:
How the proximity analysis works:
|
Note - Proximity is not based on the physical location of the server. A client in New York will connect to the California Endpoint Policy Server if the California Endpoint Policy Server replies before the New York Endpoint Policy Server. |
Clients continue to connect to the closest Endpoint Policy Server until the next proximity analysis.
|
Note - You cannot figure which particular Endpoint Policy Servers a client should use, only a list of servers for the client to choose from. |
To configure Endpoint Policy Server connections:
This value is the interval, in minutes, after which endpoint clients search for the closest available Endpoint Policy Server.
This option includes Endpoint Security Management Servers in the search for the closest Endpoint Policy Server.
Configure if the Endpoint Security Management Server behaves as an Endpoint Policy Server along with the other Endpoint Policy Servers.
The default is that the Endpoint Security Management Server does behave as an Endpoint Policy Server.
|
Note - If you do not explicitly enable the Endpoint Security Management Server to behave as an Endpoint Policy Server, it is still in the proximity analysis list. If no other Endpoint Policy Servers can reply to a client, the Endpoint Security Management Server replies. |
To configure the Endpoint Security Management Server to behave as an Endpoint Policy Server only if all Endpoint Policy Servers do not respond:
The communication between the Endpoint Security Management Server and the Endpoint Policy Servers includes:
You can change this in the $UEPMDIR/engine/conf/global.properties file on the Endpoint Security Management Server. The property name is connectionpoint.hb.interval.secs.
You can change this in the $UEPMDIR/engine/conf/global.properties file on the Endpoint Security Management Server. The property names are:
connectionpoint.emon.events.until.flush=1000connectionpoint.emon.seconds.until.flush=60Notes on the First Synchronization
After you create the Endpoint Policy Server and install the policy in SmartEndpoint, the first synchronization between the Endpoint Policy Server and Endpoint Security Management Server occurs. During the first synchronization, the Endpoint Policy Server does not handle endpoint requests and shows as Not Active in the Reporting tab.
The first synchronization can take a long time, based on the amount of policies and installation packages that the Endpoint Policy Server must download from the Endpoint Security Management Server.
When the first synchronization is complete, the Endpoint Policy Server will show as Active in the Reporting tab.
You can see the status of Endpoint Policy Servers in the Reporting tab of SmartEndpoint.
In the Reporting tab, select Endpoint Policy Servers Status.
For more detailed information, you can look at the log messages on the Endpoint Policy Server. They are in: $UEPMDIR/logs
You can see if there are errors in the logs and resolve them if necessary.