

In This Section: |
Important - Transit VPC is a deprecated solution. Refer to sk153473 - How to migrate from Transit VPC to AWS Transit Gateway.
The Amazon Global Transit Network is used to perform transitive routing between spoke networks through a central hub. Use this document to deploy a hub-and-spoke network topology that routes all traffic through a network transit center, a Transit VPC.
The Transit VPC simplifies network management and minimizes the number of connections needed to connect multiple Amazon VPCs and remote networks. You can create as many virtual networks as necessary and design different options for connecting the networks to each other.
Use Check Point CloudGuard together with the Transit VPC. CloudGuard delivers comprehensive security for cloud workloads and assets with VPC perimeter security services, seamless security segmentation between VPCs, and automatically established IPsec VPN connectivity between cloud environments. The solution automatically connects spoke VPCs to a central security hub VPC for seamless security inspection, VPN and NAT services.
CloudGuard integrates easily with AWS. Once you deploy the Security Management Server and security hub, every new or existing VPC that is specifically tagged is automatically configured to route all traffic. The traffic is routed through an AWS managed VPN gateway into the security hub. The VPN gateways are also added as IPsec interoperable devices. The Security Gateways are added to the automatically established route-based VPN process, (powered by Border Gateway Protocol (BGP)), to propagate network route changes to on-premises and in cloud tenants.
The solution provides the Check Point award winning Threat Prevention suite in transit architecture. It offers industry leading Firewall (according to NSS and Gartner), IPS, HTTPS Inspection, Anti-Bot and Anti-Virus, and Zero-day protection engines. These Threat Prevention features safeguard published applications, Internet-bound traffic, and inbound access to cloud assets with complete security visibility and event analysis.
Check Point CloudGuard for AWS easily extends comprehensive Threat Prevention security to the AWS cloud and protects assets in the cloud from attacks, and at the same time enables secure connectivity.
CloudGuard IaaS lets you enforce consistent Security Policies across your entire organization. It protects data between the corporate network and the Amazon VPC. CloudGuard IaaS also inspects data that enters and leaves the private subnet in the Amazon VPC to prevent attacks and mitigate data loss or leakage. CloudGuard IaaS protects services in the public cloud from the most sophisticated threats as well as unauthorized access, and at the same time prevents application layer Denial of Service (DoS) attacks.
Check Point CloudGuard for AWS meets organizational cloud security needs:
You are responsible for the cost of the AWS services that you use, when you deploy the solution described in this guide.
The AWS CloudFormation template for the Transit VPC includes configuration parameters that you can customize. Some of these settings, such as instance type, affect the cost of deployment. For estimated costs, see the AWS pricing calculator.
This Transit VPC solution uses Amazon Machine Images (AMIs) from the AWS Marketplace. You must subscribe to Check Point CloudGuard in the AWS Marketplace before you start the deployment.
You need a license to use the Check Point CloudGuard Security Gateways, Check Point CloudGuard Security Management Server, and AWS CloudFormation templates described in this guide. There are two licensing options:
To purchase BYOL licenses, contact Check Point Sales.
Before you use this solution, make sure you are familiar with these AWS services:
If you are new to AWS, see Getting Started with AWS.
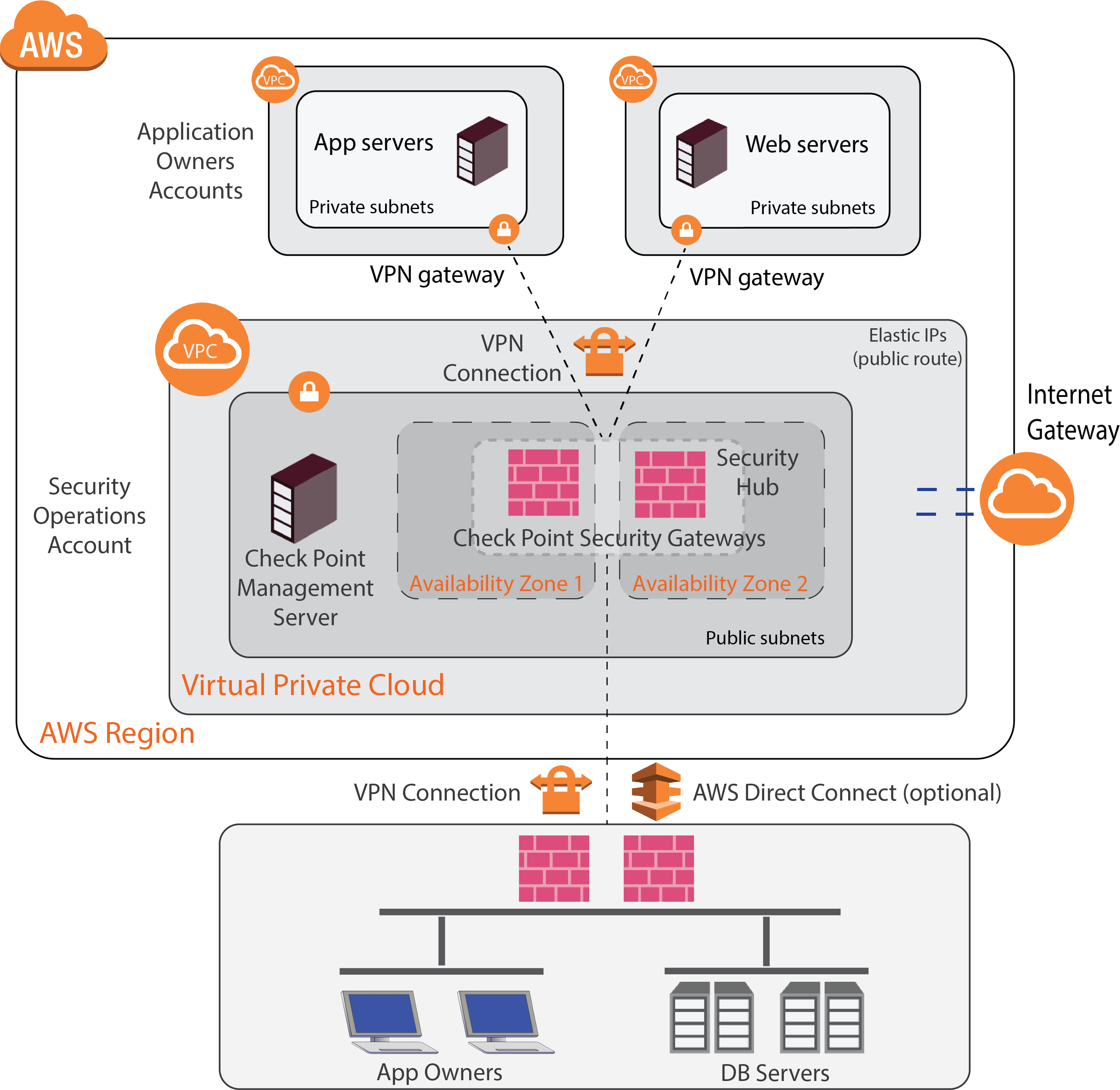
The diagram shows the end-to-end solution, which includes:
These are the examples of how you can set up your Transit VPC architecture:
Architecture |
Description |
|---|---|
Transparent proxy |
The transparent proxy provides secured proxy services to the spoke VPCs. It is transparent in that the security proxy services are seamless and do not require topological changes to the protected spoke VPCs. With this solution, you do not need a CloudGuard Gateway for AWS in each of the spoke VPCs. The solution relies on VPN connections to the central (hub) VPC for Internet-bound connections. DevOps and application owners can use the transparent proxy to deploy solutions in designated VPCs, rely on AWS native security controls only, and have advanced Threat Prevention, Next Generation Firewall, and compliance, seamlessly from the central VPC. |
Cloud perimeter |
The Transit VPC, as a cloud perimeter, provides Threat Prevention and Access Control to the spoke VPCs. Each VPC can be deployed in multiple Availability Zones and provide security services to multiple spoke VPCs in the environment. Only the central VPC has access to the Internet, and the spokes are limited to private subnets. All traffic to and from the spoke VPCs is steered through the central VPC. The security controls are concentrated in a single central VPC. |
Hybrid cloud |
With a Hybrid cloud setup, you can connect your on-premises and cloud environments, and cloud assets can have secured access to on-premises assets. The connection is established through a secured VPN connection between your Check Point Security Gateway and a CloudGuard Gateway in AWS. You can also implement a secure connection with AWS Direct Connect tunnels. For example, a front-end server in the cloud can connect to an on-premises backend database to retrieve confidential data or business logic. For more information, see sk120534. |
Direct Connect |
Direct Connect makes it easy to establish a dedicated network connection from on-premises to AWS. When you use AWS Direct Connect, it is transparent to Check Point Security Gateways. For example, you can connect route and tunnels from Transit Gateways directly to corporate gateways. You must configure the Direct Connect manually, when you connect corporate gateways and Transit Gateways. Automation is not supported. For more information, see sk120534. |
A VPN Domain is a collection of internal networks that use VPN Security Gateways to send and receive their traffic. VPN Security Gateways are joined into a VPN Community. A VPN Community is a collection of VPN tunnels and their attributes. Networks from different VPN Domains can communicate securely with each other through VPN tunnels that terminate at the Security Gateways in the VPN communities.
VPN communities used for this Transit solution are based on a Star topology. In a Star VPN Community, each satellite gateway, an AWS VPN connection represented by an Interoperable Device object, has a VPN tunnel to the central CloudGuard Security Gateway, and through it to other satellite gateways in the Star VPN Community.
Transit solution uses Route Based VPN, where VPN traffic is routed based on the BGP routing settings of the CloudGuard Gateway. The CloudGuard Gateway uses a VPN Tunnel Interface (VTI) to send the VPN traffic, as if it were a physical interface.
Because of the Route Based VPN, there is no need to set a VPN Domain on the CloudGuard Security Gateway. The Transit service creates an empty Group object that is used when you configure the CloudGuard Gateway in SmartConsole. This ensures that Domain Based VPN is not used.
The config-community.sh script creates a Star VPN Community with these required settings for Transit:
For information on this script, see the Configuring the VPN Community with the 'config-community.sh' Script section.
For more information on Check Point VPN solutions, see the R80.10 Site to Site VPN Administration Guide.
A Security Policy package is a collection of different types of policies that are enforced after you install the policy on the Security Gateways.
A policy package can have one or more of these policy types:
The Standard policy package is the default Security Policy defined in a newly deployed Security Management Server. Every policy package contains a default cleanup rule that drops all traffic.
When you configure the <Check Point Security Management Server with the autoprov-cfg utility, specify the name of the Security Policy package to be installed on the Transit Gateways with the -po parameter. For the default Security Policy, use the value "Standard" (a capital "S" is required), for this parameter.
If you want to configure additional policy packages and install a different policy package on the Security Gateways deployed for the transit solution, then specify the name that you want to give that policy package when you run autoprov-cfg. Afterwards, create and configure the policy by connecting to your Security Management Server with SmartConsole.
For more information, see ‘autprov-cfg’
There are two deployment options:
Option |
Description |
|---|---|
Deploy the Check Point CloudGuard transit solution as a new VPC |
This option builds a new AWS transit environment that consists of the VPC, subnets, security groups, and other infrastructure components. It then deploys the Check Point CloudGuard IaaS Security Gateways into this new VPC and an optional preconfigured Security Management Server to manage them. |
Deploy the Check Point CloudGuard transit solution into an existing VPC |
This option provisions Check Point CloudGuard IaaS Security Gateways and an optional preconfigured Security Management Server to manage them into your existing AWS infrastructure. |
There are separate CloudFormation templates for each option. The templates let you configure CIDR blocks, instance types, and Check Point CloudGuard IaaS settings.
See Step 3 for links to the templates.