

In This Section: |
This section describes virtual network components and their characteristics.
A Virtual System is a virtual security and routing domain that provides the functionality of a Security Gateway with full Firewall and VPN facilities. Multiple Virtual Systems can run concurrently on a single VSX Gateway.
Each Virtual System functions independently. Each Virtual System maintains its own Software Blades, interfaces, IP addresses, routing table, ARP table, and dynamic routing configuration. Each Virtual System also maintains its own:
A Virtual Router is an independent routing domain within a VSX Gateway that performs the functionality of physical routers. Virtual Routers are useful for connecting multiple Virtual Systems to a shared interface, such as the interface leading to the Internet, and for routing traffic from one Virtual System to another. Virtual Routers support dynamic routing.
Virtual Routers perform the following routing functions:
By providing layer-2 connectivity, a Virtual Switch connects Virtual Systems and facilitates sharing a common physical interface without segmenting the existing IP network. As with a physical switch, each Virtual Switch maintains a forwarding table with a list of MAC addresses and their associated ports.
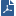
Many Enterprise environments are based on core networks. Situated adjacent to core network backbone switches, VSX protects the internal network by providing security at layer-2, layer-3 or both. VSX communicates with the core network using the existing infrastructure. With Virtual Systems in the Bridge Mode, VSX can protect departmental networks, while simultaneously preventing network segmentation. In this case, switches are located at the entrance to each department's network.
VSX ensures connectivity between the core network and the Internet or external networks, while providing perimeter security. Security can be configured on a per VLAN basis.
The main interface types in VSX are:

Item |
Description |
|
Item |
Description |
|---|---|---|---|---|
1 |
Internet |
|
8 |
Security Management Server |
2 |
Router |
|
9 |
Virtual Switch |
3 |
Physical interface |
|
10 |
Warp Link |
4 |
VLAN Switch |
|
11 |
Virtual System 1 |
5 |
Network 1 |
|
12 |
Virtual System 2 |
6 |
Network 2 |
|
13 |
VLAN Interface |
7 |
VSX Gateway |
|
14 |
VLAN Trunk |
Notes:
Physical interfaces connect a VSX Gateway to internal and external networks, as well as to the management server. There are different types of physical interfaces (four types for a VSX Cluster) used in a VSX Gateway:
Virtual Systems typically connect to protected VLAN networks using IEEE 802.1q compliant VLAN Interfaces. The networks are connected to ports on an 802.1q-compliant switch that trunks all traffic via a single physical interface to the VSX Gateway.
A Warp Link is a virtual point-to-point connection between a Virtual System and a Virtual Router or Virtual Switch. Each side of a Warp Link represents a virtual interface with the appropriate virtual device.
A VSX cluster has two or more identical, interconnected VSX Gateways for continuous data synchronization and transparent failover. Virtual System Load Sharing (VSLS) enhances throughput by distributing Virtual Systems, with their traffic load, among multiple, redundant machines.

Item |
Description |
|
Item |
Description |
|---|---|---|---|---|
1 |
Internet |
|
8 |
LAN Switches |
2 |
Core Network Backbone switch |
|
9 |
Sales |
3 |
VSX Cluster |
|
10 |
Finance |
4 |
Router |
|
|
Sync Network |
5 |
VLAN |
|
|
Physical Interface |
6 |
Member 1 |
|
|
VLAN Trunk |
7 |
Member 2 |
|
|
|
Load Sharing offers significant performance advantages while providing failover for individual Virtual Systems. Using multiple Gateways instead of a single gateway significantly increases performance for CPU intensive applications such as VPNs, Security servers, Policy servers, and Active Directory (LDAP).
By distributing Virtual System instances between different cluster members, the performance load is efficiently spread amongst the members. For example, active Virtual System 1 runs on member A, while active Virtual System 2 runs on member B. Standby and backup Virtual System instances are likewise distributed amongst members to maximize throughput, even in a failover scenario.
VSLS provides an excellent scalability solution, allowing administrators to add additional physical members to an existing VSLS cluster as traffic loads and performance requirements increase.
In a deployment scenario with three cluster members, each with three Virtual Systems: an equalized Load Sharing deployment might have one active Virtual System on each cluster member.

Item |
Description |
|
Item |
Description |
|---|---|---|---|---|
1 |
Member 1 |
|
8 |
VS 2 Backup |
2 |
Member 2 |
|
9 |
VS 3 Active |
3 |
Member 3 |
|
10 |
VS 1 Backup |
4 |
VS 1 Active |
|
11 |
VS 2 Active |
5 |
VS 2 Standby |
|
12 |
VS 3 Standby |
6 |
VS 3 Backup |
|
|
Sync Network |
7 |
VS 1 Standby |
|
|
|
A different member hosts the active peer for each Virtual System. This distribution spreads the load equally amongst the members. When you create a Virtual System, VSX automatically assigns standby and backup states to the appropriate peers and distributes them among the other cluster members.
In the event that a cluster member fails, VSLS directs traffic destined to affected Virtual Systems to their fully synchronized standby peers, which then become active. At the same time, a backup Virtual Systems switches to standby, and synchronizes with the newly active Virtual System.
In the event that an individual active Virtual System fails, it immediately fails over to its standby peer and one of its backup peers becomes the standby, synchronizing with the newly active peer.