

In This Section: |
These trusted entities create VPN trust in a Multi-Domain Management deployment:
The ICA of the Domain Server issues certificates used by Domain Security Gateways to create SIC trust.
When you establish Global VPN Communities, it automates part of the configuration of Externally Managed Security Gateways and the exchange of certificates for each Domain Server. For more information on VPN with Externally Managed Gateways, see the R80.10 Site to Site VPN Administration Guide.
A VPN Domain is a collection of internal networks that use Security Gateways to send and receive VPN traffic. Define the resources that are included in the VPN Domain for each Security Gateway. Then join the Security Gateways into a VPN community - collection of VPN tunnels and their attributes. Network resources of different VPN Domains can securely communicate with each other through VPN tunnels that terminate at the Security Gateways in the VPN communities.
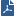
VPN communities are based on Star and Mesh topologies. In a Mesh community, there are VPN tunnels between each pair of Security Gateway. In a Star community, each satellite Security Gateway has a VPN tunnel to the central Security Gateway, but not to other Security Gateways in the community.
Note - Global VPN Communities are not supported in this release.
Mesh Topology |
Star Topology |
Item |
Description |
|---|---|
1 |
Security Gateway |
2 |
Satellite Security Gateways |
3 |
Central Security Gateway |
Sometimes Domains must establish VPN between Security Gateways that are managed by different Domain Servers. This might happen, for example, in large enterprises that created different Domain Servers to manage corporate networks in different cities or countries. Alternatively, an MSP deployment may require communication between partners, managed as different Domains.
Cross-Domain VPN is handled by the establishment of Global VPN Communities. This community is similar to the regular VPN community with the exception that it can deal with Security Gateways managed by different Domain Servers. An administrator creates a VPN connection between Domain Security Gateways using the Domain Server SmartDashboard. A Global VPN Community however is defined at the Multi-Domain Management level, using SmartConsole and Global SmartDashboard.
Multi-Domain Management utilizes its knowledge about different Domain network environments to ease the definition of VPN for environments run by different Domain Servers. In the standalone model, cross-Domain VPN is established by creating Security Gateways that are defined as externally managed Security Gateway objects. Then certificates and network information are imported into the Security Management Server databases.
In Multi-Domain Management, during the Global VPN Community setup, the Multi-Domain Server automatically exports relevant ICA information (such as the CA certificate) for each Domain Server, so that both sides can trust the other's ICA.
You can configure an existing Domain Security Gateway as a global Security Gateway. This action imports the Security Gateway into the global policy database, making it accessible by all other Domain Servers in your deployment.
Different Domains may coincidentally contain Security Gateways using the same name. Each global Security Gateway object must have its own unique Global Name. To resolve this issue, the Global Names Template automatically assigns a unique name for each global Security Gateway. The default global name format is g<Security Gateway name>_of_<Domain name>.
For example:
In a global VPN community, VPN tunnels are created between Security Gateways in neighboring Domains. This is analogous to externally managed VPN Security Gateways in a single-domain deployment.
Each Security Gateway supports certificates issued by the CAs of the other Domains.
The administrator defines each Domain Security Gateway using SmartDashboard. When defining if the Security Gateway is a VPN Security Gateway, the administrator specifies whether the VPN Domain is to be based on the network's topology or a specific address range.
You manage this network information at the Domain level. The is included in the Domain Server database. For VPN connections between Security Gateways, the VPN domain is flexible and can be defined by the Domain administrator.
Domain Server databases would have to maintain complete data on all other Domain networks, which could also be a security breach. Instead, Multi-Domain Management computes address ranges from those specified in VPN Security Gateway properties. It uses this list as the base for the VPN domain of a particular Security Gateway from another Domain network.
Check Point Security Gateway provides secure access control through its granular understanding of all underlying services and applications traveling on the network. Stateful Inspection technology provides full application-layer awareness, and comprehensive access control for more than 150 pre-defined applications, services and protocols as well as the ability to specify and define custom services.
Stateful Inspection extracts state-related information required for security decisions from all application layers and maintains this information in dynamic state tables for evaluating subsequent connection attempts. Access Control and Global VPN Communities
Configuring Security Gateways for a Domain Global VPN Community does not create a de facto access control policy between the Security Gateways. The fact that two Security Gateways belong to the same VPN community does not mean the Security Gateways have access to each other.
The configuration of the Security Gateways into a Global VPN Community means that if these Security Gateways are allowed to communicate using an access control policy, then that communication is encrypted. Access control is configured in the security policy rule base.
Using the VPN column of the security policy rule base, it is possible to create access control rules that apply only to members of a VPN community, for example:
Source |
Destination |
VPN |
Service |
Action |
|---|---|---|---|---|
Any |
Any |
Community_A |
HTTP |
Accept |
If all conditions of the rule are met, the rule is matched and the connection allowed.
Access control for global communities is the same as for a VPN community that belongs to a single Domain.
To learn more about access control for VPN communities, see the R80.10 VPN Administration Guide.
There are several steps necessary to join a Domain Security Gateway to a Global VPN Community. First, each Domain Security Gateway must be enabled for global use. Then a VPN Community must be defined in Global SmartDashboard, including the global Security Gateway objects representing participating Domain Security Gateways.
Lastly, a Global Policy must be assigned to participating Domains' Domain Servers, and installed on the Domain Security Gateway, for each Domain and Security Gateway participating in the VPN Community. All Security Gateways participating in the Global VPN Community must employ a Simplified VPN policy. The global policy itself may be either neutral or Simplified.
When assigning a global policy to one or more Domains, global objects are copied to the database of the Domain Server. Whether all the global objects in the database are copied, or only those related to the global policy, is configurable per Domain using the Domain Configuration window. Rules belonging to the global policy package being assigned are being added above and below the rules inside all local policies defined in that Domain Server database.
For more information about global policies, see Global Policy Management.
When you install policy on Security Gateways in a Domain, they receive the latest Domain Server policy, including the most recent Global Policy. You can make changes to the global policy, and then reassign the global policy to one or more Domains. When a Domain Server then installs the updated policy on the Domain Security Gateways, all modifications to global and local objects and rules are updated on the selected Security Gateways.
The assign and install procedures are two different processes. The administrator can assign a global policy without installing a local policy on Domain Security Gateways.
During the assignment process, each participating Domain receives the CA certificates of the other Domains. For each participating Domain, a global CA Server object is created in the Domain Server. The CA Server object represents the Certificate Authority of the peer Domains. This object allows authentication by Matching Criteria. If the certificate of the peer Domain was already imported manually into the Domain, the Matching Criteria refers to the existing certificate.
You must close the Global SmartDashboard and SmartDashboard (if they are open in Read/Write mode), in order to perform the Enable for Global Use operation. If they are open in Read Only mode, they can remain open.
|
Note - Security Gateways enabled for global use do not show in SmartConsole under a Domain Server this is assigned to all global objects, with these exceptions:
|
Repeat this step for all Security Gateways that are to participate in the Global VPN Community.
A global Security Gateway object and a VPN Domain object are created for the Domain Security Gateway in the Global Database.
In the Global Policies View, assign and install the Global Policy to Domains and selected Domain Security Gateways. The Global Policies View has two modes which allow slightly different activities, the Security Policies Mode and the VPN Communities Mode.
Different SmartConsole views allow you to perform this step in slightly different ways. You can assign the policy to one Domain at a time, for greater load management. Or you can assign the policy to all the Domains at once, if load management is not an issue.
Through the Security Policies Mode, select a global policy. Then choose Reassign/Install Global Policy from the Manage menu, or right-click the Domain and select Reassign/Install Global Policy. Select the Domain Security Gateways to which the policy should be installed. The policy is assigned to the Domain Server database, then to the selected Domain Security Gateways.
or
Use the VPN Communities Mode, but the procedure is much the same. Right click a Domain, then select Reassign/Install Global Policy from the Manage menu, or select Reassign/Install Global Policy from the mouse menu.
The procedure is through the Security Policies Mode, similar to the above. Select a Global Policy and right click, then select Manage > Assign/Install Global Policy or Reassign/Install Global Policy, or right-click and select Assign/Install Global Policy.
This operation assigns the Policy to all selected Domains, and then installs the Policy to all Domain Security Gateways, in one step. It does not allow you to select specific Security Gateways to which to install the Policy. If chosen, the Policy will be installed to all of the Security Gateways for the selected Domains. Assigning the Policy to many Domains and all their Security Gateways may take some time. Use this option with caution.
You can now create security rules regarding VPN using SmartDashboard for a Domain Server. Security Gateways which are external to a Domain but are part of the Global VPN Community, will appear as global externally managed Security Gateway objects in the Domain Server SmartDashboard.
The Domain own participating Security Gateways will appear as they usually do. It is not necessary to define authentication for the external global Security Gateway objects. Matching criteria are automatically defined for the global Security Gateway objects referring to the other Domain Server Certificate Authority.
A Domain can be assigned a Global Policy which references a Global VPN Community, in which, however, none of the Domain Security Gateways participate. If this happens, the Domain Server database will have an empty community (without community members).