

In This Section: |
Mobile Access can be deployed in a variety of ways depending on an organization's system architecture and preferences.
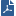
In the simplest Mobile Access deployment, one Mobile Access enabled Security Gateway inspects all traffic, including all Mobile Access traffic. IPS and Anti-Virus can be active on all traffic as well. The Security Gateway can be on the network perimeter.
This is the recommended deployment. It is also the least expensive and easiest to configure as it only requires one gateway machine for easy and secure remote access.
Item |
Description |
|---|---|
1 |
Internal servers |
2 |
Security Gateway with Mobile Access enabled |
3 |
SSL Tunnel through Internet |
4 |
Remote User |
When a Mobile Access enabled Security Gateway is put in the DMZ, traffic initiated both from the Internet and from the LAN to Mobile Access is subject to firewall restrictions. By deploying Mobile Access in the DMZ, the need to enable direct access from the Internet to the LAN is avoided. Remote users initiate an SSL connection to the Mobile Access Gateway. You must configure the Access Control Policy to allow traffic from the user to the Mobile Access server, where SSL termination, IPS and Anti-Virus inspection, authentication, and authorization take place. The Security Gateway forwards requests to the internal servers.
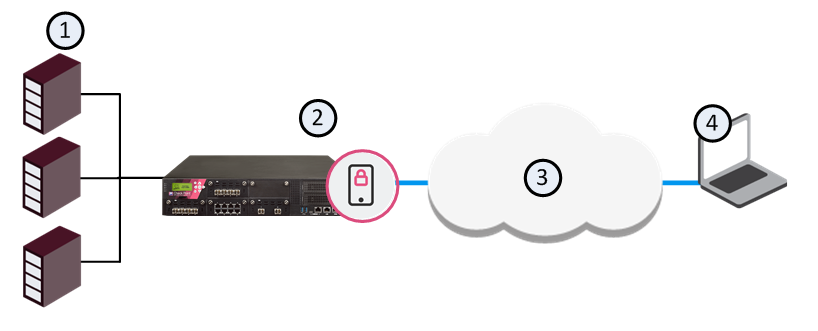
If you have large numbers of concurrent remote access users and continuous, uninterrupted remote access is crucial to your organization, you may choose to have Mobile Access active on a cluster. A cluster can be deployed in any of the deployments described above.
Item |
Description |
|---|---|
1 |
Internal servers |
2 |
Mobile Access enabled cluster member B |
3 |
Internet |
4 |
Remote User making SSL connection through Internet |
5 |
Mobile Access enabled cluster member A |
6 |
Secure Network (Sync) |
Each cluster member has three interfaces: one data interface leading to the organization, a second interface leading to the internet, and a third for synchronization. Each interface is on a different subnet.
In a simple deployment with the Mobile Access cluster in the DMZ, two interfaces suffice; a data interface leading to the organization and the internet, and a second interface for synchronization.
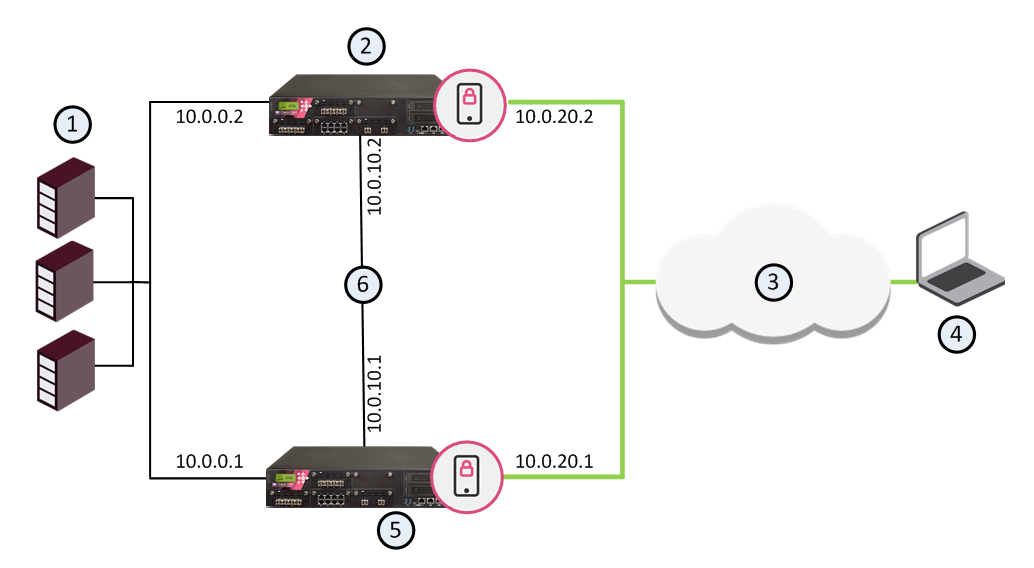
You can enable the Mobile Access Software Blade on VSX Virtual Systems.
This feature is supported in R77.10 and higher.
You can use a VSX deployment to support different Mobile Access scenarios. Each Virtual System can have a Mobile Access portal with different applications, access policies, authentication requirements, and mobile clients.
For example, in the picture below, a VSX Gateway has four Virtual Systems with Mobile Access enabled. Each Virtual System has Mobile Access configured with different settings to meet the company's needs for different users.
Item |
Description |
Example Mobile Access Portal URL |
|---|---|---|
1 |
Remote Users |
|
2 |
Internet |
|
3 |
Router |
|
4 |
VSX Gateway |
|
5 |
Virtual Switch |
|
6 |
Virtual System 4 with Mobile Access enabled |
https://guest.company.com/sslvpn |
7 |
Virtual System 3 with Mobile Access enabled |
https://finance.company.com/sslvpn |
8 |
Virtual System 2 with Mobile Access enabled |
https://sales.company.com/sslvpn |
9 |
Virtual System 1 with Mobile Access enabled |
https://dev.company.com/sslvpn |
This table shows an example of different settings that you can have on each Virtual System.
Virtual System |
Users |
Clients Allowed |
Authentication Schemes |
Endpoint Health Checks |
Applications Configured |
|---|---|---|---|---|---|
Virtual System 9 |
Development team |
Mobile Access Portal, SSL Network Extender, Capsule Workspace |
Certificate + AD Password |
Mobile Access Portal ESOD check for company Endpoint Security requirements Jail broken or rooted devices not allowed |
Development applications |
Virtual System 8 |
Sales team |
Capsule Workspace, Capsule Connect |
SecurID + AD password |
Jail broken or rooted devices not allowed |
Sales applications |
Virtual System 7 |
Finance team |
Mobile Access Portal, Capsule Workspace |
SecurID + AD password |
Cooperative enforcement with company MDM server |
Finance applications |
Virtual System 6 |
Contractors |
Mobile Access Portal |
Certificate that expires after 30 days |
Mobile Access Portal ESOD check for commercial AV solution and recent AV signature updates |
Contractor internal applications |
You can configure a Mobile Access gateway to be a reverse proxy for Web Applications on your servers, using Mobile Access. Reverse Proxy users browse to an address (URL) that is resolved to the gateway IP address. Then the gateway passes the request to an internal server, according to the Reverse Proxy rules. You control the security level (HTTP or HTTPS) of connections between users and resources.
See Reverse Proxy.
You can also enable Single Sign-on for Capsule Workspace with Capsule Docs users. See the Endpoint Security Administration Guide for details.
This is a high-level workflow to configure remote access to Mobile Access applications and resources.
Users can access mobile applications through the configured Mobile Access portal with the defined authentication method.
Enable Mobile Access |
|
Configure settings in Mobile Access wizard |
|
Select the policy type and add rules to policy |
|
Update the Authentication settings |
|
|
|
|
|
|
|
Users can access internal resources |
|
Users download app, open it, and enter settings |
|
Generate a certificate for the clients |
|
Install the Access Control Policy |
The Mobile Access Wizard runs when you enable the Mobile Access blade on a gateway. It lets you quickly allow selected remote users access to internal web or mail applications, through a web browser, mobile device, or remote access client.
See Check Point Remote Access Solutions to understand more about the remote access clients mentioned in the wizard. Many of the settings in the wizard are also in Gateway Properties > Mobile Access.
Select from where users can access the Mobile Access applications:
Enter the primary URL for the Mobile Access portal. The default is the https://<IP address of the gateway>/sslvpn. You can use the same IP address for all portals on the gateway with a variation in the path. You can import a p12 certificate for the portal to use for SSL negotiation. All portals on the same IP address use the same certificate.
Select the applications that will be available to web or mobile device users:
Select the AD domain, enter your credentials and test connectivity. If you do not use AD, select I don't want to use active directory now.
Select users and groups from Active Directory or internal users. You can also create a test user that will get access to the configured applications.
This window helps you understand steps that are required to complete the automatic configuration done by the Mobile Access wizard. Depending on the selections you made, you might see these steps:
Each Mobile Access-enabled Security Gateway leads to its own Mobile Access user portal. Remote users log in to the portal using an authentication scheme configured for that Security Gateway.
Remote users access the portal from a Web browser with https://<Gateway_IP>/sslvpn, where <Gateway_IP> is one of these:
Remote users that use HTTP are automatically redirected to the portal using HTTPS.
|
Note - If Hostname Translation is the method for link translation, FQDN is required. |
Set up the URL for the first time in the Mobile Access First Time Wizard.
To change the IP address used for the user portal:
From the properties of the Gateway object, select Mobile Access > Portal Settings.
To configure the look and feel of the portal:
From the properties of the Gateway object, select Mobile Access > Portal Customization.
Users can access Mobile Access applications remotely as defined by the policy rules.
On R80.x gateways, there are different policy options:
For pre-R80 gateways, use the Legacy Mobile Access Policy in the Policy page of the Mobile Access tab in SmartDashboard.
For all policy types, rules include these elements:
You can also include VPN and Remote Access clients in rules to define which client users can use to access the application.
The Mobile Access policy applies to the Mobile Access portal and Capsule Workspace. It does not apply to Desktop clients or Capsule Connect.
Settings related to what users can access from mobile devices are also defined in the Mobile Profile: SmartDashboard > Mobile Access tab > Capsule Workspace.
To make an R80.x Mobile Access gateway use the Unified Access Control Policy:
To create rules for Mobile Access in the Unified Access Control Policy:
See Configuring Mobile Access in the Unified Policy.
The order of the rules in the Legacy Policy is not important.
To create rules in the Mobile Access Rule Base:
SmartDashboard opens and shows the Mobile Access tab.
To enable devices to connect to the gateway with Capsule Workspace:
If necessary, manage certificates for authentication between the devices and the gateway.
If you use certificate authentication, we recommend that you include this information in the client certificate distribution email.
If you use certificates for mobile and desktop clients, use the Client Certificates page in SmartConsole to manage certificates for authentication between the devices and the gateway.
To configure client certificates:
The Certificate Creation and Distribution wizard opens
For more details see Managing Client Certificates.