

In This Section: |
The Check Point Endpoint Security On Demand scanner enforces endpoint compliance by scanning the endpoint to see if it complies with a pre-defined endpoint compliance policy. For example, an endpoint compliance policy can make sure that the endpoint client has updated Anti-Virus software and an active firewall. If the endpoint is compliant with the endpoint compliance policy, the user is allowed to access the portal.
By ensuring that endpoints comply with a security policy, Endpoint Security On Demand protects enterprises from threats emanating from unsecured endpoint computers that can result in data loss and excessive bandwidth consumption.
The endpoint compliance policy is made up of rules. A policy can specify, for example, that the endpoint machine must have an approved Anti-Virus application, and that it must be free of spyware. A policy could also specify that a machine must be managed by the organization in order to gain full access to internal data and applications.
On gateways of version R71 and higher, a combination of Endpoint Compliance Policy and Secure Workspace Policy can require the following Policy: Any client connecting to the gateway from a machine that is not managed by the organization or that does not meet a specific enforcement policy, must use Check Point Secure Workspace. This ensures that no unauthorized information is accessed.
The administrators can make compliance with a policy a requirement for accessing either the portal or specific applications. This makes it possible to assign varying levels of security clearance to the portal and to Mobile Access applications.
Endpoint Compliance policies can be assigned to Mobile Access gateways. They can also be assigned to Protection Levels, which are in turn associated with Mobile Access applications.
In order to access that application, the endpoint machine must comply with the policy associated with the Protection Level, in addition to the policy associated with the gateway.
In either case, the scan takes place before logging in to the portal. Only one scan is performed. Compliance to policies is determined according to the results of the scan.
There are different types of Endpoint Compliance policy rules, for different types of security applications. It is possible to have multiple rules of the same type, each with different settings.
Windows security rules perform Windows-specific checks. For example:
Endpoint computers running Windows must pass these checks in order to gain access to the network.
At least one of the Hotfixes in the rule must be active on the endpoint computer in order for the endpoint to be considered compliant and be granted access to the portal.
The rules also specify the action to be taken if an endpoint computer fails to comply with a rule and the error message that is presented to users in the event of non-compliance, such as remediation information.
Choose which Anti-Spyware applications endpoint computers (on the Windows platform) must have to gain access to the network.
Ensure that appropriate Anti-Spyware software is running on endpoint computers, and that the software version and virus signature files are up-to-date.
At least one of the Anti-Spyware applications in the rule must be active on the endpoint computer in order for the endpoint to be considered compliant and be granted access to the portal.
For convenience, Anti-Spyware enforcement rules are pre-configured with supported anti-spyware providers. To require a non-supported Anti-Spyware provider, use a custom check rule.
The rules also specify the action to be taken if an endpoint computer fails to comply with a rule and the error message that is presented to users in the event of non-compliance, such as remediation information.
Choose which Anti-Virus applications the endpoint computer must have in order to gain access to the network.
Ensure that appropriate Anti-Virus software is running on endpoint computers, and that the software version and virus signature files are up-to-date.
At least one of the Anti-Virus applications in the rule must be active on the endpoint computer in order for the endpoint to be considered compliant and be granted access to the portal.
For convenience, Anti-Virus enforcement rules are pre-configured with supported Anti-Virus providers. To require a non-supported anti-virus provider, use a custom check rule.
The rules also specify the action to be taken if an endpoint computer fails to comply with a rule and the error message that is presented to users in the event of non-compliance, such as remediation information.
Choose which personal firewall applications endpoint computers (on Windows, Linux or Macintosh platforms) must have to gain access to your network.
Ensure that appropriate firewall software is installed, enabled and running on endpoint computers.
At least one of the firewall applications in the rule must be active on the endpoint computer in order for the endpoint to be considered compliant and be granted access to the portal.
For convenience, firewall enforcement rules are pre-configured with supported firewall providers. To require a non-supported firewall provider, use a custom check rule.
The rules also specify the action to be taken if an endpoint computer fails to comply with a rule and the error message that is presented to users in the event of non-compliance, such as remediation information.
Perform custom checks on endpoint computers (on the Windows, Linux or Macintosh platforms) that are not covered by any of the other rule types. For example:
Custom check rules can be configured to check for specific versions and modification dates.
The rules also specify the action to be taken if an endpoint computer fails to comply with a rule, and the error message that is presented to users in the event of non-compliance, such as remediation information.
An "OR Group of Rules" rule includes a list of previously defined rules. An endpoint satisfies a rule of type "OR Group of Rules" if it satisfies one or more of the rules included in the "OR Group of Rules" rule.
The rules also specify the action to be taken if an endpoint computer fails to comply with a rule and the error message that is presented to users in the event of non-compliance, such as remediation information.
Select the action that should take place for each type of spyware present on endpoint computers. You can change the protections for types of spyware threats.
Spyware Type |
Description |
|---|---|
Dialer |
Software that change the user's dial-up connection settings so that instead of connecting to a local Internet Service Provider, the user connects to a different network, usually a toll number or international phone number. |
Worm |
Programs that replicate over a network for the purpose of disrupting communications or damaging software or data. |
Keystroke Logger |
Programs that record user input activity (keystrokes or mouse activity). Some keystroke loggers transmit the recorded information to third parties. |
Hacker Tool |
Tools that facilitate unauthorized access to a computer and/or extraction of data from a computer. |
Remote Administration Tool |
Commercially developed software that allows remote system access and control. |
Trojan |
Malicious programs that masquerade as harmless applications. |
Adware |
Programs that display advertisements or record information about Web use habits and forward it to marketers or advertisers without the user's authorization or knowledge. |
Other |
Any unsolicited software that secretly performs undesirable actions on a user's computer and does not fit any of the above descriptions. |
Screen Logger |
Software that record what a user's monitor displays. |
Tracking Cookie |
Cookies that are used to deliver information about the user's Internet activity to marketers. |
Browser Plug-in |
Software that modifies or adds browser functionality. Browser plug-ins change the default search page to a pay-per-search site, change the user's home page, or transmit the browser history to a third party. |
You define an exception list of spyware software. For example, you can allow that a signature that is recognized as spyware by Mobile Access, but which you see as legitimate.
In the rule, set the action to take if an endpoint computer fails to comply. Set the error message that users see in the event of non-compliance, such as remediation information.
If the end user machine is not compliant with one or more of the Endpoint Compliance policy rules, Mobile Access generates Endpoint Compliance-specific logs with the category "Endpoint Security on Demand" (Endpoint Security On Demand). The log entries appear in SmartLog, and include the:
|
Note - Mobile Access logs non-compliant rules from all policies, not only the Endpoint Compliance policy that is assigned to the gateway or to an application. This means that there may be entries in SmartLog for rules that do not appear in the report presented to the end user. |
unwantedexample.3rd party cookie.symptom type: URL. Symptom value: cookie:bob@unwantedexample.net.The workflow for configuring Endpoint Compliance enforcement is below. Each step is described in detail in the sections that follow:
Decide on security clearance levels for Mobile Access portals and applications. For example, is it OK for users to gain access to all Mobile Access applications as long as they comply with a single policy? If some resources are more sensitive than others, you may wish to draw up a more stringent policy for some applications than for others.
Set up a stand-alone test computer with all the endpoint security applications you want to create enforcement rules for, and the run the ICSinfo tool to obtain the information needed to correctly define Endpoint Compliance policy rules.
Policies are made up of rules. In order to comply with the policy, endpoints must comply with all rules in the policy. Rules can be used in more than one policy. Rules that are not in a policy are not used.
There are different types of rules for different security applications. The Endpoint Compliance policy configuration tool comes with a number of predefined rules which can be edited to match the needs of the organization.
Configure which Endpoint Compliance Policies should be assigned to which applications and gateways.
Configure tracking options for the endpoint scan results, then save and install the security policy
Defining the Endpoint Compliance policy for Mobile Access clients involves some planning, prior to performing the SmartDashboard configuration.
You need to define security clearance levels for the both the Mobile Access portal (that is, the gateway) and for portal applications. There are various approaches, and the best one to use depends on how granular you need to make the policy.
Basic Approach:
The simplest approach is to define a single Endpoint Compliance policy for the gateway and all applications accessed via the gateway. In this approach, all applications accessed via the gateway are protected by the Endpoint Compliance policy of the gateway. Users whose client machines comply with the policy have access to the portal and all applications.
For example:
Resource |
Endpoint Compliance Policy |
|---|---|
Gateway A |
Low Security |
Web App P |
Rely on gateway requirements |
Web App Q |
Rely on gateway requirements |
File Share R |
Rely on gateway requirements |
Advanced Approach:
A more advanced approach is appropriate if there is one application (or a small number of applications) that has stricter security requirements than other applications. These additional requirements are specified in a separate Endpoint Compliance policy, which is enforced in addition to the gateway policy. To access the Mobile Access portal, all users must fulfill the threshold security requirements of the gateway policy. Users clicking a link in the portal to an application with additional security requirements are only allowed access to the application if they fulfill those additional requirements.
For example:
Resource |
Endpoint Compliance Policy |
|---|---|
Gateway A |
Low Security |
Web App P |
Rely on gateway requirements |
Web App Q |
High Security |
File Share R |
Rely on gateway requirements |
Very Advanced Approach:
Where most or every application has its own endpoint security requirements, it is possible to define an individual Endpoint Compliance policy for each application. In this scenario, there are no gateway security requirements: All users are able to access the portal. However, when clicking a link to an application, users are only allowed access if they fulfill the requirements for that application. If no requirements are configured for the application, users are allowed to access it.
For example:
Resource |
Endpoint Compliance policy |
|---|---|
Gateway A |
None |
Web App P |
Low Security |
Web App Q |
High Security |
File Share R |
Medium Security |
The following table illustrates Endpoint Compliance policies with different rules, for different security requirements.
Rule |
Description |
High Security Endpoint Compliance Policy |
Medium Security Endpoint Compliance Policy |
Low Security Endpoint Compliance Policy |
|---|---|---|---|---|
1 |
Default Windows Security rule |
Yes |
Yes |
No |
2 |
Anti-Virus applications check |
Yes |
Yes |
Yes |
3 |
Firewall applications check |
Yes |
Yes |
Yes |
4 |
Spyware Scan rule |
Yes |
No |
No |
When defining Endpoint Compliance policy rules, you must use the correct format. This format varies from vendor to vendor. The ICSinfo.exe utility scans your computer, and generates an xml file that gives you the information in the correct format for all supported security programs it finds.
Run ICSinfo before configuring the Endpoint Compliance policy rules.
To use the ICSinfo.exe utility:
ICSinfo tool from the Mobile Access gateway to the test computer. The tool is located at $CVPNDIR/htdocs/ICS/components/ICSinfo.exe.ICSinfo.exe. This utility lists all detected security software, along with the required information in the correct format. The xml format output file ICSinfo.xml can be viewed in a browser. The sections of the file can be collapsed or expanded by clicking the - or +.To configure Endpoint Compliance policies:
SmartDashboard opens and shows the Mobile Access tab.
The Endpoint Compliance policy configuration tool opens at the Policies page.
The Policies > New Policy page opens.
The Policies > Edit Policy page opens.
Note - This option is disabled if there is no Spyware Scan rule in the policy.
The Add Enforcement Rules page opens. Select a rule and click OK.
Note - For explanations of fields in the Endpoint Compliance rules, see the online help.
After the Endpoint Compliance policies are configured, Endpoint Compliance settings can be configured to make use of the polices.
To configure Endpoint Compliance:
The gateway window opens and shows the General Properties page.
To assign a policy to the gateway and require an Endpoint Compliance scan to connect to the gateway:
To make sure that the applications use the gateway settings for their Endpoint compliance:
The Web Application settings window opens.
To configure the gateway settings:
To make sure that the applications use the gateway settings for their Endpoint compliance:
The Web Application settings window opens.
To define a new Protection Level, click Manage and define the protection level.
To configure the gateway settings:
To configure an individual policy for each application:
The Web Application settings window opens.
Note - If This application relies on the security requirements of the gateway is selected for the Mobile Access application, users are allowed to access the application without any Endpoint Compliance requirements.
To define a new Protection Level, click Manage and define the protection level.
You can edit the Advanced Endpoint Compliance Settings to configure whether or not to allow access to the gateway and applications if the Endpoint Compliance scanner is not supported on the endpoint operating system.
The Advanced Endpoint Compliance Settings window opens.
In this window you can decide whether or not to allow access to the gateway and applications if the Endpoint Compliance scanner is not supported on the endpoint operating system.
The Endpoint Compliance scanner supports the following operating systems: Windows, Mac, and Linux.
If you want to allow some endpoint operating systems to bypass Endpoint Compliance requirements, you must select the Allow access option in the Advanced Endpoint Compliance Settings window.
For details, see the operating system compatibility table in the Mobile Access Release Notes.
To configure different rules on endpoints with different operating systems, see SecureKnowledge solution sk34989.
Configuring Endpoint Compliance Settings per Protection Level lets you set Platform-Based Bypass per application.
By default all Advanced Endpoint Compliance Settings are taken from the SmartDashboard configuration, in the Advanced Endpoint Compliance Settings page.
Enabling Platform Based Bypass per Protection Level
To configure different access permissions for various Protection Levels for Endpoint Compliance scanning, run:
|
To return to the default setting, change true to false in the above command.
Configuring the Protection Levels that are Bypassed
In the Mobile Access tab of SmartDashboard, under Additional Settings > Protection Levels, is a list of Protection Levels. From this page you can edit the Authentication and Endpoint Security settings that are required for applications assigned to each Protection Level. You can also create new Protection Levels.
In the Mobile Access application properties, assign a Protection Level to an application. For example, if you want to allow access to an application only if the user is compliant with Endpoint Compliance policy1, but you also need to accommodate the user connecting from an endpoint that does not support Endpoint Compliance scanning (such as an iPhone), then:
To configure different access permissions for various Protection Levels for Endpoint Compliance, from the Mobile Access CLI, in expert mode, run:
|
You can add other Protection Levels as well.
To restore a Protection Level from being "Bypassed", for Endpoint Compliance:
|
To finalize the configuration of granular platform-based bypass for Endpoint Security On Demand:
cvpnrestart If the Mobile Access gateway is part of a cluster, be sure to make the same change on each cluster member.
Mobile Access generates Endpoint Compliance-specific logs. The logs can be viewed in SmartLog, and have the category Endpoint Security On Demand. The Endpoint Security On Demand information is in the info field of the logs.
To configure tracking options for the Endpoint Compliance scanner:
SmartDashboard opens and shows the Mobile Access tab.
The Tracking options are:
unwantedexample.3rd party cookie.symptom type: URL. Symptom value: cookie:bob@unwantedexample.net.To assign policies to gateways:
To assign policies to applications:
To exclude a spyware signature from a scan:
When Endpoint Security On Demand detects the spyware (irrespective of the action configured in the Spyware Scan rule), the name of the spyware (something like Win32.megaspy.passwordthief) is included in the report.
SmartDashboard opens and shows the Mobile Access tab.
By default, the end user computer is scanned by the Endpoint Compliance scanner every time the user logs in. This is the default, and most secure configuration.
It is possible to configure Mobile Access so that after logging in, the user is not scanned, even after logging in again, until the end of a timeout period.
For configuration details, see sk34844 (, https://support.checkpoint.com/results/sk/sk34844).
The Endpoint Compliance scanner on endpoint computers is supported on browsers that run ActiveX (for Windows with Internet Explorer), or Java.
When using the Endpoint Compliance scanner with Internet Explorer, the browser must be configured to download and run ActiveX controls and to allow Active Scripting. This section explains how to configure Internet Explorer to ensure that the Endpoint Compliance scanner will install and run properly on the endpoint computer.
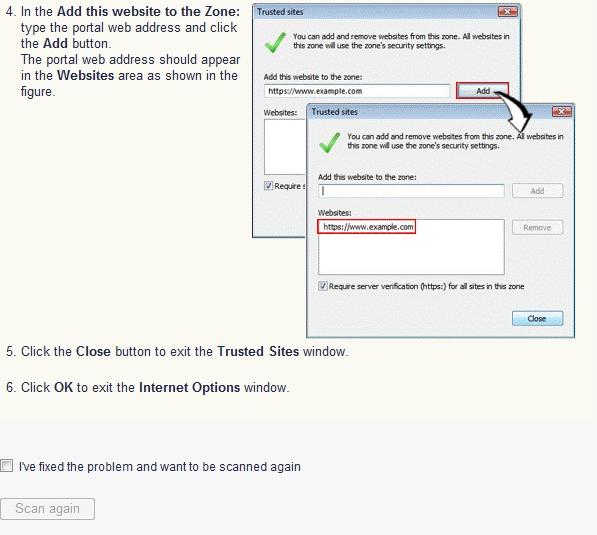
To configure Internet Explorer for the Endpoint Compliance scanner:
When a user connects to a portal where the Endpoint Compliance is enabled, the end user computer is scanned before the user sees the login screen.
|
Note - The Endpoint Compliance scan starts if Endpoint compliance is configured for a Mobile Access application in a portal, even if portal access does not require compliance with a policy. |
The Endpoint Compliance Scanner is installed on the endpoint machine, by using ActiveX (for Windows with Internet Explorer), or Java.
To login to the Mobile Access Portal with the Endpoint Compliance scanner enabled:
Some warnings may appear, regarding the Mobile Access site server certificate, and the downloaded applet.
If the endpoint computer fails to pass the scan, Endpoint Security On Demand displays a result screen showing the potentially harmful software and security rule violations detected during the scan.
|
Note - The user and administrator see the scan results as log entries in the Traffic Log. Each entry shows the user name, user group, source computer, malware name, malware type, and malware description. |
Endpoint Security On Demand for Mobile Access requires browsers that support ActiveX or Java.
The following sections describe Endpoint Security On Demand behavior when users attempt to access the Mobile Access Portal using an unsupported browser.
In this case, Endpoint Security On Demand presents an error message and generates a log entry in the administrator's traffic log.
The following steps can prevent users using unsupported browsers from gaining access to the Mobile Access Portal and applications without passing an Endpoint Compliance scan:
The Endpoint Compliance page shows:
If this is correct for your organization:
Secure Workspace is a security solution that allows remote users to connect to enterprise network resources safely and securely. The Secure Workspace virtual workspace provides a secure environment on endpoint computers that is segregated from the "real" workspace.
No data is allowed to leave this secure environment except through the Mobile Access portal. Secure Workspace users cannot access any applications, files, system tools, or other resources from the virtual workspace unless they are explicitly permitted by the Secure Workspace policy.
Administrators can easily configure Secure Workspace policy to allow or prevent activity according to enterprise requirements.
Secure Workspace creates an encrypted folder called My Secured Documents on the virtual desktop that contains temporary user files. It deletes this folder and all other session data when the session terminates.
After Secure Workspace is enabled, configure a gateway to either require all users to connect to the Mobile Access portal through Secure Workspace, or to give users the option of connecting through Secure Workspace or from their endpoint computers.
To enable Secure Workspace for an Mobile Access gateway:
SmartDashboard opens and shows the Mobile Access tab.
For details, see Configuring the Secure Workspace Policy.
The gateway window opens and shows the General Properties page.
In the Endpoint Security On Demand > Secure Workspace page, in the Advanced Secure Workspace Settings section, click Edit. The Advanced Secure Workspace Settings window opens.
In this window you can decide whether or not to allow access to the gateway and applications if Secure Workspace is not supported on the endpoint operating system.
To configure advanced operating system-specific settings, see sk34989.
If you want to let some endpoint operating systems to bypass Secure Workspace requirements, you must select the Allow access option in the Advanced Secure Workspace Settings window.
To configure different rules on endpoints with different operating systems, see sk34989.
Configuring Secure Workspace Settings per Protection Level allows you to configure “Platform-Based Bypass” per application.
By default all Advanced Secure Workspace Settings are taken from the SmartDashboard configuration, in the Advanced Secure Workspace Settings page.
Enabling Platform Based Bypass per Protection Level
To configure different access permissions for various Protection Levels for Secure Workspace, from the CLI run:
|
To return to the default setting, change true to false in the above command.
Configuring the Protection Levels that are Bypassed
In the Mobile Access tab of SmartDashboard, under Additional Settings > Protection Levels, is a list of Protection Levels. From this page you can edit the Authentication and Endpoint Security settings that are required for applications assigned to each Protection Level. You can also create new Protection Levels. If you select, Applications using this protections level can only be accessed from within Check Point Secure Workspace, all applications assigned to that Protection level will only be accessed from within Secure Workspace.
However, if you want to allow access to an application only from Secure Workspace, but you also need to accommodate the user connecting from an endpoint that does not support Secure Workspace (such as an iPhone), then:
To configure different access permissions for various Protection Levels for Secure Workspace, from the Mobile Access CLI, in expert mode, run:
|
You can add other Protection Levels as well.
Restoring a Protection Level from being Bypassed for Secure Workspace
|
Finalize the Configuration for Secure Workspace
cvpnrestart.If the Mobile Access gateway is part of a cluster, make the same change on each cluster member.
In its default configuration, Secure Workspace allows access to a limited group of applications. This is usually sufficient for most end-users working with the Mobile Access Portal and retrieving information from network hosts.
See sk114454 for the list of supported applications.
When using SSL Network Extender inside Secure Workspace, Secure Workspace traffic and traffic from outside the Secure Workspace are encrypted.
Secure Workspace controls access to applications and directories on endpoint computers based on the Secure Workspace policy.
Each Mobile Access gateway has its own Secure Workspace policy. The policy:
You can add to the list of Approved Applications, and can add, edit, or delete applications from the list.
You can define locations where the application is allowed to save files that remain after Secure Workspace shuts down. These locations are called Allowed Save locations. There is no need to define locations for files that are not needed after Secure Workspace shuts down. Temporary files are deleted when the Secure Workspace is closed.
Secure Workspace includes a built-in Firewall that lets you define Outbound Firewall Rules. These are the IP addresses and ports that approved applications are allowed to access. By default, desktop applications are allowed to access all addresses and ports.
Note that settings for the approved applications, save locations, and Outbound Firewall Rules are independent. For example, the save locations are not restricted to a particular application, and similarly, Outbound Firewall Rules apply to all applications.
The Secure Workspace policy determines the permitted activities and behavior that end users will experience when working in Secure Workspace.
To configure the Secure Workspace Policy:
SmartDashboard opens and shows the Mobile Access tab.
The Secure Workspace Settings window opens.
Self Protection
This requires administrative privileges and the User Access Control (UAC) prompt might show during the Secure Workspace startup.
SSL Network Extender
Data Protection
Application Table
Approved applications show on the Secure Workspace desktop, and are allowed to run on endpoint computers. You can add, edit, or remove applications from the list.
When you add a new application or edit an application, you can include this information:
Enter the path in one of these formats:
<disk>:\<folder_path>\<binary_name>. Secure Workspace allows the endpoint to run the binary from specified location only. The full path is necessary if the location of the program does not appear in the PATH.\<binary_name>. Secure Workspace allows the endpoint to run the binary with the specified name from all locations on the disk. Use if the location appears in the PATH.<path_with_env_variable>\<binary_name>. Secure Workspace resolves the environment variable on the endpoint, and uses its value as part of the path to the executable.You can configure which applications users can access from Secure Workspace. If a vendor is trusted then all applications from this vendor are trusted. See sk114526 for the vendors trusted by default. You cannot add a vendor to the list.
Allowed Save locations are locations where applications are allowed to save files that remain after Secure Workspace shuts down. There is no need to define locations for temporary files that can be deleted after Secure Workspace shuts down.
To add an allowed save location:
Outbound Firewall Rules define which IP addresses and ports approved applications are allowed to access when they make outbound connections.
These options are available:
Best practice is to use the default rules. You can delete the default rules and replace them with more restrictive rules, but do so carefully.
You can add custom rules to the Secure Workspace virtual registry. Contact Check Point support for more information about this feature.
In the User Experience settings, configure what users see and how they interact with Secure Workspace.
General
Desktop Background - Change the Secure Workspace desktop background picture and its position.
Display Start dialog - Show a Start window that you customize.
A Secure Workspace policy that is configured in SmartDashboard applies to all Mobile Access gateways. To configure a Secure workspace policy for each gateway, see sk34939.
Secure Workspace can work together with the Check Point Endpoint Security Reputation Services to check whether an application that is not an approved application is legitimate. Reputation Services identifies programs according to their filename and MD5 hash.
For details of the Endpoint Security Reputation Services, see your version of the Endpoint Security Administration Guide. If you use Reputation Services, the sequence of Secure Workspace is:
This section provides an overview of the Secure Workspace workflow.
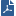
If users use Internet Explorer to open the Mobile Access portal on Windows Vista or higher, they must disable Internet Explorer Protected Mode. If Protected Mode is not disabled, SSL VPN might run, but they can have unexpected errors.
On Windows 7 and higher, protected mode is enabled by default. You can see that it is enabled:
If Endpoint Security on Demand is configured on the gateway, the scan detects that Protected mode is on and instruction to disable Protected mode open.
If Endpoint Security on Demand is not configured on the gateway, users are not alerted that they must disable Protected mode. However they must do the same steps to disable Protected mode so that they can access the SSL VPN portal without problems.
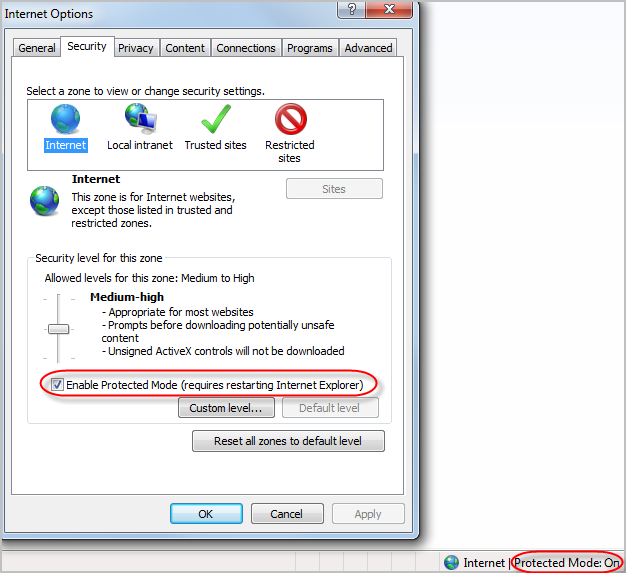
Here are the instructions that users get to disable Protected Mode. All users must do these steps even if they do not get the instructions automatically.
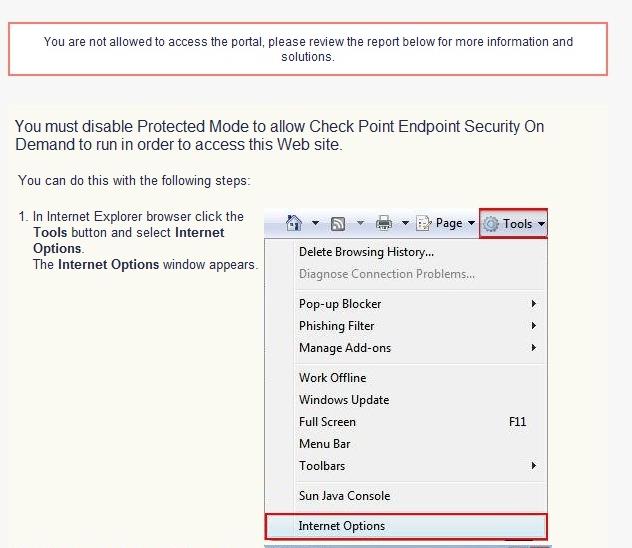
After these steps, close all Internet Explorer windows. The next time you open Internet Explorer, Protected mode is off.
Secure Workspace initializes when a user logs on to the Mobile Access Portal. If the administrator has configured the Mobile Access gateway to require Secure Workspace, this occurs automatically. If the administrator has configured the gateway to allow users to choose whether or not to use Endpoint Security On Demand, an option appears on the Login screen.
The Secure Workspace virtual desktop looks and feels like a normal Windows desktop.
The principal difference is that Secure Workspace only allows users to work with a limited number of pre-approved applications and files and, by default, does not allow users to print, customize the desktop or perform any system configuration activities. Since most users only use Secure Workspace to work with the Mobile Access Portal, these functions are rarely needed.
The virtual desktop Start menu and taskbar function in the same manner their "real" counterparts do. Configuration settings in the Secure Workspace policy determine which shortcuts and options are available to users.
Users occasionally need to download and save files from resources behind the Mobile Access gateway to "real" desktop folders. Conversely remote users may need to upload files to the corporate network from the endpoint computer.
To allow this, the administrator must configure the Secure Workspace policy to allow endpoints to switch between the secure and regular desktops. This is accomplished in the User Experience Settings section of the Secure Workspace policy editor.
Generally, users can access files and run applications in Secure Workspace in the same manner as on the "real" desktop. Since, by default, users have read-only (access) privileges to all folders and files, they can freely navigate the file system using Windows Explorer. When attempting to run a program or open a file for which a user does not have Secure Workspace permission, an error message appears.
Likewise, if a user attempts to save a file to a "real" desktop folder without Secure Workspace permissions, an error message appears.
When SSL Network Extender network mode users initiate a Secure Workspace session, permitted Endpoint Applications are available in the virtual desktop as follows:
An Endpoint Application defined in the Native Application as... |
... is available to Users as a |
|---|---|
Path and executable name (already installed) |
Shortcut in the Windows Start > Program menu. |
Runs via default browser |
Shortcut on the desktop. |
Downloaded-from-Mobile Access application |
Link in the Mobile Access Portal. |
Note - During a Secure Workspace session, SSL Network Extender cannot toggle between the Network Mode and the Application Mode. User can change the mode, but must start a new Secure Workspace session after doing so.
You can switch back and forth between the Secure Workspace virtual workspace and the "real" desktop at any time. To do so, click the lock icon, located in the tray area of the taskbar.
To exit Secure Workspace:
A confirmation and reminder to save open files appears.
Secure Workspace logs are automatically saved in %temp%\IswTmp\Logs when the environment variable ISWLOG is set to 0 (zero). If you have issues with Secure Workspace, you can examine these logs or send them to Check Point technical support.
If an application stops working, a Secure Workspace window opens to help you send technical information to Check Point. Users can manually open this window if a process hangs or they experience instability.
To collect technical information:
A Secure Workspace window opens to help you send technical information to Check Point.
Check Point provides Endpoint Compliance updates. You can download Endpoint Security On Demand updates from the Mobile Access tab in SmartDashboard.
You can configure Endpoint Security On Demand to retrieve updates automatically according to a defined schedule or you can manually download and install the updates.
You can periodically check for and automatically download Endpoint Compliance updates. You can choose to download updates from the Check Point Download Center or you can install updates previously downloaded to your Security Management Server.
|
Note - Before performing an Endpoint Security On Demand update, install a policy at least once. |
To configure automatic updates:
SmartDashboard opens and shows the Mobile Access tab.
The Automatic Updates window opens.
To perform a manual Endpoint Security On Demand update:
SmartDashboard opens and shows the Mobile Access tab.