
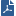

Component Name |
File Name |
Description |
|---|---|---|
Full Disk Encryption service |
|
The Full Disk Encryption service contains the current configuration data and initiates background encryption or decryption. By exchanging volume boot records, the Full Disk Encryption service identifies volumes that are targeted for encryption. |
Crypto core |
|
The Crypto core contains the encryption algorithms. |
Filter driver |
|
The Full Disk Encryption driver for encryption. The File Allocation Table (FAT) provides the driver with the location of sectors where data is stored. Full Disk Encryption encrypts every byte of the selected disk. Background encryption starts from the first sector of the selected volume and moves in sequence to the last sector. The entire operating system is encrypted. |
If system failure prevents the operating system from starting on a client computer, Full Disk Encryption has these options:
If system failure prevents the operating system from starting on a client computer, you can use Full Disk Encryption Recovery Media to decrypt the computer and recover the data. Client computers send recovery files to the Endpoint Security Management Server one time during the initial deployment so that you can create recovery media if necessary. After the recovery, the files are restored as decrypted, like they were before the Full Disk Encryption installation, and the operating system can run without the Pre-boot.
After the recovery, you must install Full Disk Encryption on the computer.
Recovery Media:
Users must authenticate to the recovery media with a username and password. There are the options for which credentials to use:
You can create Full Disk Encryption recovery media that can run on a failed computer to decrypt it. Create the recovery media on the server or with an external tool.
The media can be on a CD/DVD, USB device, or REC file.
|
Note - Creating a recovery media on a USB flash disk formats the device and removes all previous content. |
To create recovery media from the Endpoint Security Management Server:
The Full Disk Encryption Recovery Media Tool window opens.
The target retrieves the last known recovery data that was uploaded to the server by the client.
To create recovery media from the external recovery media tool on R77.20 and higher Management:
C:\Program Files\CheckPoint\Endpoint Security\Full Disk Encryption\ UseRec.exe and select Run as > Administrator.Use the newly created Full Disk Encryption recovery media to decrypt the failed computer.
To recover an encrypted computer:
The disk decrypts using partition keys contained in the Recovery Media.
|
Note - During the decryption process, the client cannot run other programs. |
Full Disk Encryption Drive Slaving Utility lets you access Full Disk Encryption protected disk drives that become corrupted as a result of an Operating System failure . The Drive Slaving Utility is hardware independent, and can access hard disks connected through USB ports.
Full Disk Encryption Dive Slaving Utility replaces older versions of Full Disk Encryption drive slaving functionality, and supports R73 and all E80.x versions. You can use the Full Disk Encryption Drive Slaving Utility instead of disk recovery.
The utility is supported in E80.51 clients and higher on R77.20 and higher management.
|
Notes -
|
Before you run the Full Disk Encryption Drive Slaving Utility, make sure to do these:
We recommend that you use a recovery file when you are not sure if the hard disk drive or the Full Disk Encryption internal database on your system are corrupted.
To use the Full Disk Encryption Drive Slaving Utility:
<x:>\Program files(x86)\CheckPoint\Endpoint Security\Full Disk Encryption\fde_drive_slaving.exeNote - To unlock a protected USB connected hard disk drive, you must first start the Drive Slaving Utility, and then connect the disk drive.
The Full Disk Encryption - Drive Slaving window opens.
Unlock volume(s) authentication window opens.
After successful authentication, use Windows explorer to access the disk drive. If you fail to access the locked disk drive, use the Full Disk Encryption Recovery file, then run the Drive Slaving Utility again.
|
Note - To prevent data corruption, shut down the system or use a safe removal utility before you disconnect the USB connected drive. |