
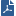

An Endpoint Security environment includes SmartEndpoint, Endpoint Security Management Server, and Endpoint Security clients. It is integrated with the Check Point Security Management and SmartConsole.
Endpoint Security Management Server
Item |
Description |
SmartEndpoint |
Check Point SmartConsole application to deploy, monitor and configure Endpoint Security clients and policies. Install on the Endpoint Security Management Server or on a computer that supports the client installation. |
Endpoint Security Management Server |
Software Blade on Security Management Server with Endpoint Security policy management and databases. It communicates with endpoint clients to update their policies and protection data. |
Endpoint Security Blades |
Software blades available on the Endpoint Security Management Server. You can install any or all of these blades on endpoint clients. See Software Blades. |
Endpoint Security Database |
Holds policies that enforce security on endpoint clients, holds user and computer objects, licensing, and Endpoint monitoring data. |
Directory Scanner |
Software component that synchronizes the structure and contents of the Active Directory with the Endpoint Security policy database. |
Endpoint Security Clients
Item |
Description |
||
|---|---|---|---|
Endpoint Security Clients |
Application installed on end-user computers to monitor security status and enforce security policies. |
||
Endpoint Agent |
Endpoint Security software on client computers. It operates as a container for Software Blades deployed on the endpoint client and communicates with the Endpoint Security Management Server. (Endpoint Agent is also known as the Device Agent or DA) |
||
Endpoint Security Blades |
Software blades deployed on the endpoint client. |
||
|
Note - When the term Endpoint Security Management Server is used, it refers to all Endpoint Security Servers in the environment. This includes Endpoint Security Management Servers or Endpoint Policy Servers. |
||
Related Topics |
To make sure that your Endpoint Security system runs efficiently and without unnecessary down time, you can also include these components in your system architecture: