Interface - Topology Settings
What can I do here?
Use this window to configure the interface's topology.

|
Getting Here - Gateways & Servers> Select gateway > Edit > Network Management > Click the Expand button > Select an interface > Edit > Topology section > Modify
|
Understanding Topology
An interface can be defined as being External (leading to the Internet) or Internal (leading to the LAN).
The type of network that the interface :
- or - This is the default setting. It is automatically calculated from the topology of the gateway. To update the topology of an internal network after changes to static routes, click > in the window of the gateway.
- - Override the default setting.
If you the default setting:
- - All external/Internet addresses
- -
- - All IP addresses behind this interface are considered a part of the internal network that connects to this interface
- - Only the network that directly connects to this internal interface
- - The gateway dynamically calculates the topology behind this interface. If the network changes, there is no need to click "Get Interfaces" and install a policy.
- - A specific network object (a network, a host, an address range, or a network group) behind this internal interface
- - The DMZ that directly connects to this internal interface
VPN Tunnel Interfaces
If the interface is part of a VPN Tunnel, then the interface a network. The interface is one end of the point to point connection. All traffic in the network behind the interface is part of the point to point connection. Click to define a specific network.
Preventing IP Spoofing
IP spoofing replaces the untrusted source IP address with a fake, trusted one, to hijack connections to your network. Attackers use IP spoofing to send malware and bots to your protected network, to execute DoS attacks, or to gain unauthorized access.
Anti-Spoofing detects if a packet with an IP address that is behind a certain interface, arrives from a different interface. For example, if a packet from an external network has an internal IP address, Anti-Spoofing blocks that packet.
Example:
The diagram shows a Gateway with interfaces 2 and 3, and 4, and some example networks behind the interfaces.
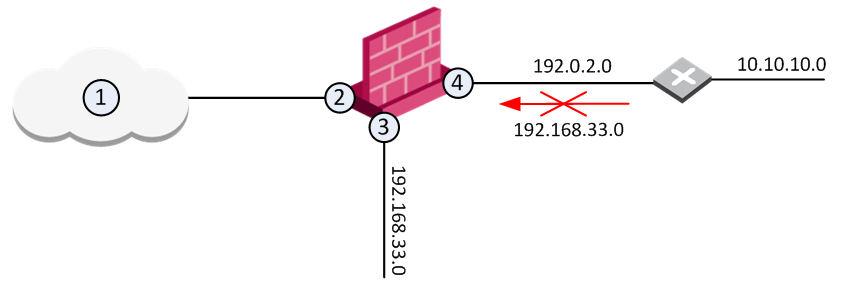
For the Gateway, anti-spoofing makes sure that
- All incoming packets to 2 come from the Internet (1)
- All incoming packets to 3 come from 192.168.33.0
- All incoming packets to 4 come from 192.0.2.0 or 10.10.10.0
If an incoming packet to B has a source IP address in network 192.168.33.0, the packet is blocked, because the source address is spoofed.
When you configure Anti-Spoofing protection on a Check Point Security Gateway interface, the Anti-Spoofing is done based on the interface topology. The interface topology defines where the interface (for example, External (Internet) or Internal), and the of interface.
Configuring Anti-Spoofing
Make sure to configure Anti-Spoofing protection on all the interfaces of the Security Gateway, including internal interfaces.
To configure Anti-Spoofing for an interface:
- In SmartConsole, go to and double-click the Gateway object.
The window of the Gateway opens.
- From the navigation tree, select .
- Click .
- Click .
The gateway network topology shows. If SmartConsole fails to automatically retrieve the topology, make sure that the details in the section are correct and the Security Gateway, the Security Management Server, and the SmartConsole can communicate with each other.
- Select an interface and click .
The properties window opens.
- From the navigation tree, select .
- In the section of the page, click .
The window opens.
- Select the type of network that the interface :
- or - This is the default setting. It is automatically calculated from the topology of the gateway. To update the topology of an internal network after changes to static routes, click > in the window of the gateway.
- - Override the default setting.
If you the default setting:
- - All external/Internet addresses
- -
- - All IP addresses behind this interface are considered a part of the internal network that connects to this interface
- - Only the network that directly connects to this internal interface
- - A specific network object (a network, a host, an address range, or a network group) behind this internal interface
- - The DMZ that directly connects to this internal interface
- Optional: In the section, choose the zone of the interface.
- Configureoptions. Make sure that is selected.
- Select an :
- - Drops spoofed packets
- - Allows spoofed packets. To monitor traffic and to learn about the network topology without dropping packets, select this option together with the option.
- Configure Anti-Spoofing exceptions (optional). For example, configure addresses, from which packets are not inspected by Anti-Spoofing:
- Select .
- Select an object from the drop-down list, or click to create a new object.
- Configure - select the tracking action that is done when spoofed packets are detected:
- - Create a log entry (default)
- - Show an alert
- - Do not log or alert
- Click twice to save Anti-Spoofing settings for the interface.
For each interface, repeat the configuration steps. When finished, install the policy.
Anti-Spoofing Options
- - Select this option to enable spoofing protection on this external interface.
- - Select this option to define if packets will be rejected (the Prevent option) or whether the packets will be monitored (the Detect option). The Detect option is used for monitoring purposes and should be used in conjunction with one of the tracking options. It serves as a tool for learning the topology of a network without actually preventing packets from passing.
- - Select this option to make sure anti-spoofing does not take place for traffic from internal networks that reaches the external interface. Define a network object that represents those internal networks with valid addresses, and from the drop-down list, select that network object. The anti-spoofing enforcement mechanism disregards objects selected in the drop-down menu.
- - Select a tracking option.



