
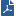

These are the options to enable connectivity between Virtual Systems and a RADIUS or TACACS/TACACS+ server:
For Multi-Domain Server configurations, make sure that you configure the SecurID or Remote Authentication settings of the Domain Management Server that manages the Virtual Systems.
Included Topics |
Configure shared authentication so that all the Virtual Systems on the VSX Gateway authenticate to the remote RADIUS or TACACS/TACACS+ server.
To configure shared authentication for RADIUS or TACACS/TACACS+:
The Virtual Systems General Properties window opens.
Do all of the previous steps for each Virtual System.
table.def file.$FWDIR/lib/table.def %FWDIR%\lib\table.def no_hide_services_ports parameter contains the UDP ports for RADIUS or TACACS, or the TCP ports for TACACS+. The default ports are:Sample RADIUS parameter with Hide NAT disabled:
no_hide_services_ports = { <49, 6>, <49, 17>, <500, 17>, <259, 17>, <1701, 17>, <123, 17>, <1645, 17> };
For private configurations, the active and standby Virtual Systems use the same encryption key to authenticate to the remote RADIUS or TACACS/TACACS+ server.
For High Availability configurations, make sure that the active and standby Virtual Systems on each cluster member use the same VIP.
To configure private authentication:
The VSX Gateway General Properties window opens.
Do all of the previous steps for each Virtual System.
For Multi-Domain Server, use the Domain Management Server that manages the Virtual System.
table.def file.$FWDIR/lib/table.def %FWDIR%\lib\table.def no_hide_services_ports parameter DOES NOT contain the UDP ports for RADIUS or TACACS, or the TCP ports for TACACS+. The default ports are:
Sample parameter with Hide NAT enabled:
no_hide_services_ports = { <500, 17>, <259, 17>, <1701, 17>, <123, 17> };