

In This Section: |
The IPsec VPN Software Blade lets the Security Gateway encrypt and decrypt traffic to and from other gateways and clients. Use SmartDashboard to easily configure VPN connections between Security Gateways and remote devices. You can configure Star and Mesh topologies for large-scale VPN networks that include third-party gateways. The VPN tunnel guarantees:
IKE and IPsec
The Check Point VPN solution uses these secure VPN protocols to manage encryption keys, and send encrypted packets. IKE (Internet Key Exchange) is a standard key management protocol that is used to create the VPN tunnels. IPsec is protocol that supports secure IP communications that are authenticated and encrypted on private or public networks.
VPN is composed of:
The basis of Site to Site VPN is the encrypted VPN tunnel. Two Security Gateways negotiate a link and create a VPN tunnel and each tunnel can contain more than one VPN connection. One Security Gateway can maintain more than one VPN tunnel at the same time.
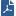
Item |
Description |
|---|---|
1 |
Security Gateway |
2 |
VPN tunnel |
3 |
Internal network in VPN domain |
4 |
Host 1 |
5 |
Host 6 |
In this sample VPN deployment, Host 1 and Host 6 securely send data to each other. The Firewalls do IKE negotiation and create a VPN tunnel. They use the IPsec protocol to encrypt and decrypt data that is sent between Host 1 and Host 6.
VPN Workflow
Host 1 sends packet |
|
Firewalls A & B create VPN tunnel |
|
Firewall A encrypts data |
|
|
|
|
|
Host 6 receives unencrypted data |
|
Firewall B decrypts data |
|
Encrypted data is sent through VPN tunnel |
A VPN Domain is a collection of internal networks that use Security Gateways to send and receive VPN traffic. Define the resources that are included in the VPN Domain for each Security Gateway. Then join the Security Gateways into a VPN community - collection of VPN tunnels and their attributes. Network resources of different VPN Domains can securely communicate with each other through VPN tunnels that terminate at the Security Gateways in the VPN communities.
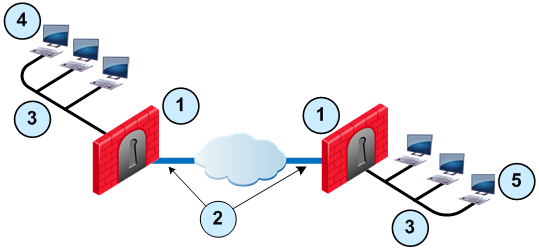
VPN communities are based on Star and Mesh topologies. In a Mesh community, there are VPN tunnels between each pair of Security Gateway. In a Star community, each satellite Security Gateway has a VPN tunnel to the central Security Gateway, but not to other Security Gateways in the community.
Mesh Topology |
Star Topology |
Item |
Description |
|---|---|
1 |
Security Gateway. For Star topology, the central Security Gateway. |
2 |
For Star topology, satellite Security Gateways. |
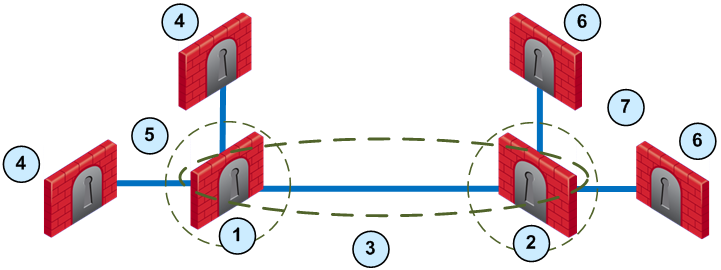
Item |
Description |
|---|---|
1 |
London Security Gateway |
2 |
New York Security Gateway |
3 |
London - New York Mesh community |
4 |
London company partner (external network) |
5 |
London Star community |
6 |
New York company partner (external network) |
7 |
New York Star community |
This deployment is composed of a Mesh community for London and New York Security Gateways that share internal networks. The Security Gateways for external networks of company partners do not have access to the London and New York internal networks. The Star VPN communities let the company partners access the internal networks.
Configure the Security Gateway to route VPN traffic based on VPN domains or based on the routing settings of the operating system.
|
Note - For each VPN gateway, you must configure an existing gateway as a default gateway. |
Domain Based VPN
The VPN traffic is routed according to the VPN domains that are defined in SmartDashboard. Use domain based routing to let satellite Security Gateways send VPN traffic to each other. The center Security Gateway creates VPN tunnels to each satellite and the traffic is routed to the correct VPN domain.
Route Based VPN
VPN traffic is routed according to the routing settings (static or dynamic) of the Security Gateway operating system. The Security Gateway uses a VTI (VPN Tunnel Interface) to send the VPN traffic as if it were a physical interface. The VTIs of Security Gateways in a VPN community connect and can support dynamic routing protocols.
The Link Selection feature gives you granular control of the VPN traffic in the network. Use this feature to enable the Security Gateway to:
If employees remotely access sensitive information from different locations and devices, system administrators must make sure that this access does not become a security vulnerability. Check Point's Remote Access VPN solutions let you create a VPN tunnel between a remote user and the internal network. The Mobile Access Software Blade extends the functionality of Remote Access solutions to include many clients and deployments.
Check Point remote access solutions use IPsec and SSL encryption protocols to create secure connections. All Check Point clients can work through NAT devices, hotspots, and proxies in situations with complex topologies, such as airports or hotels. These are the types of installations for remote access solutions: