

In This Section: |
This section includes procedures and explanations for configuring Remote Access VPN. For configuration specific to Endpoint Security VPN, Check Point Mobile for Windows, and SecuRemote, see the Remote Access Clients Administration Guide.
This section shows the Remote Access VPN Workflow.
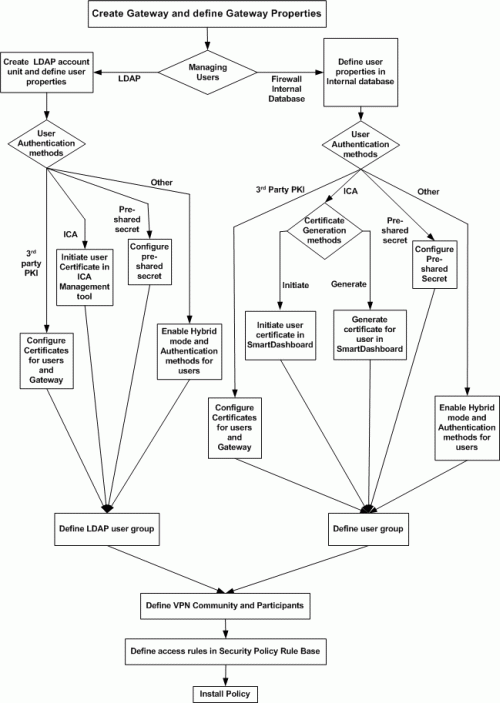
Start at the top, with Create Security Gateway and define Security Gateway properties, and trace a route down to Install policy. Sections following the chart detail step-by-step procedures for each phase.
This section contains procedures for creating Remote VPN user certificates and sending them to end users.
There are two basic procedures for supplying remote access VPN certificates to users.
To enable a user certificate:
After creating a user certificate, you must then make this certificate available to remote access users. Use this procedure to create a p12 certificate.
To create a p12 certificate file for remote access VPN users:
The new certificate shows in the Certificate. The status is set to Valid.
After creating a user certificate, you must then make this certificate available to remote access users. Use this procedure to create a certificate registration key that lets the user enroll the certificate for use with a device.
To create a certificate registration key:
Remote Access VPN users can use many different clients to connect to network resources. It is the administrator's responsibility to give appropriate instructions to end users to make sure that they successfully enroll the certificate.
The Creating Certificates section gives some general procedural guidelines that apply to many VPN clients. For detailed instructions, refer to the VPN client documentation.
The ICA automatically creates a certificate for the Security Gateway.
For more information see: LDAP and User Management in the R77 Security Management Server Administration Guide.
To use the ICA Management to enroll a user certificate:
Using third party PKI involves creating:
You can use a third-party OPSEC PKI certificate authority that supports the PKCS#12, CAPI or Entrust standards to issue certificates for Security Gateways and users. The Security Gateway must trust the CA and have a certificate issued by the CA.
For users managed on an LDAP server, the full distinguished name (DN) which appears on the certificate is the same as the user's name. But if the user is managed on the internal database, the user name and DN on the certificate will not match. For this reason, the user name in the internal database must be either the full DN which appears on the certificate or just the name which appears in the CN portion of the certificate. For example, if the DN which appears on the certificate is:
CN=John, OU=Finance, O=Widget Enterprises, C=US
The name of the user on the internal database must be either:
|
Note - The DN on the certificate must include the user's LDAP branch. Some PKI solutions do not include (by default) the whole branch information in the subject DN, for example the DN only includes the common name. This can be rectified in the CA configuration. |
To use a third-party PKI solution:
For users with certificates, it is possible to specify that only certificates with a specified suffix in their DN are accepted. This feature is enabled by default, and is required only if:
All certificates DN's are checked against this suffix.
|
Note - If an hierarchy of Certificate Authorities is used, the chain certificate of the user must reach the same root CA that the Security Gateway trusts |
Hybrid mode allows the Security Gateway and remote access client to use different methods of authentication.
To enable Hybrid Mode:
To enable this group authentication feature:
add_radius_groups property in objects.C to true.This method also works for Office Mode. The group listed in the ipassignment.conf file points to the group that authenticates using NT group authentication or RADIUS classes.
When using pre-shared secrets, the remote user and Security Gateway authenticate each other by verifying that the other party knows the shared secret: the user's password.
To enable the use of pre-shared secrets:
For more about LDAP User Groups, see Managing User Accounts in the R77 Security Management Server Administration Guide.
In SmartDashboard, create a group for remote access users. Add the appropriate users to this group.
Access control is a layer of security not connected with VPN. The existence of a remote access community does not mean that members of that community have free automatic access to the network. Appropriate rules need to be created in the Security Policy Rule Base blocking or allowing specific services.
Source |
Destination |
VPN |
Service |
Action |
Track |
|---|---|---|---|---|---|
Any |
SMTP_SRV |
Remote_Access_Community |
SMTP |
Accept |
Log |
Install the policy and instruct the users to create or update the site topology.
Managing user certificates involves:
Tracing the status of the user's certificate
The status of a user's certificate can be traced at any time in the Certificates tab of the user's Properties window. The status is shown in the Certificate state field. If the certificate has not been generated by the user by the date specified in the Pending until field, the registration key is deleted.
If the user is defined in LDAP, then tracing is performed by the ICA management tool.
Automatically renewing a certificate
ICA certificates for users can be automatically renewed a number of days before they expire. The client initiates a certificate renewal operation with the CA before the expiration date is reached. If successful, the client receives an updated certificate.
To configure automatic certificate renewal:
This is the number of days before the certificate for the user expires and the client renews the certificate.
Revoking certificates
The way in which certificates are revoked depends on whether they are managed internally or externally, using LDAP.
When a user is deleted, their certificate is automatically revoked. Certificates can be disabled or revoked at any time.
If the certificate is already active or was not completed by the user, you can revoke it by clicking Revoke in the Certificates tab of the User Properties window.
If users are managed in LDAP, certificates are revoked using the ICA management tool.
The status of a user's certificate can be traced at any time in the Certificates tab of the user's Properties window. The status is shown in the Certificate state field. If the certificate has not been generated by the user by the date specified in the Pending until field, the registration key is deleted.
If the user is defined in LDAP, then tracing is performed by the ICA management tool.
ICA certificates for users can be automatically renewed a number of days before they expire. The client initiates a certificate renewal operation with the CA before the expiration date is reached. If successful, the client receives an updated certificates.
To configure automatic certificate renewal:
The way in which certificates are revoked depends on whether they are managed internally or externally, using LDAP.
When a user is deleted, their certificate is automatically revoked. Certificates can be disabled or revoked at any time.
If you initiated a certificate generation that was not completed by the user, you can disable the pending certificate by clicking Disable in the Certificates tab of the User Properties window.
If the certificate is already active, you can revoke it by clicking Revoke in the Certificates tab of the User Properties window.
If users are managed in LDAP, certificates are revoked using the ICA management tool.
The encryption properties of the users participating in a Remote Access community are set by default. If you must modify the encryption algorithm, the data integrity method and/or the Diffie-Hellman group, you can either do this globally for all users or configure the properties per user.
To modify the user encryption properties globally:
To enforce the global encryption properties for some users while being able to modify them for specific users go to Policy > Global Properties > Remote Access > VPN - (IPsec Phase 2):
The IKE Phase 2 Properties window is displayed.
If you use SecurID for authentication, you must manage the users on RSA's ACE management server. ACE manages the database of RSA users and their assigned hard or soft tokens. The client contacts the site's Security Gateway. The Security Gateway contacts the ACE Server for user authentication information. This means:
Several versions of SecurID devices are available. The older format is a small device that displays a numeric code, called a tokencode, and time bars. The token code changes every sixty seconds, and provides the basis for authentication. To authenticate, the user must add to the beginning of the tokencode a special password called a PIN number. The time bar indicates how much time is left before the next tokencode is generated. The remote user is requested to enter both the PIN number and tokencode into the client connection window.
The newer format resembles a credit card, and displays the tokencode, time bars and a numeric pad for typing in the PIN number. These type of device mixes the tokencode with the entered PIN number to create a Passcode. The client requests only the passcode.
SoftID operates the same as the passcode device but consists only of software that sits on the desktop.

The Advanced view displays the tokencode and passcode with COPY buttons, allowing the user to cut and paste between softID and the client:
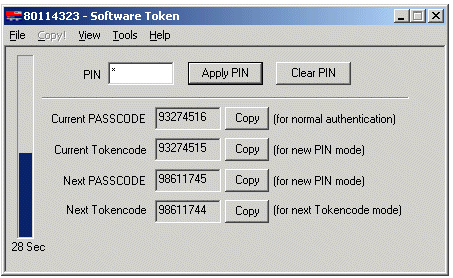
For remote users to successfully use RSA's softID:
userc.c property on SecureClient must be set in the OPTIONS section:support_rsa_soft_tokens (true)
When users login, they must enter the Token Serial Number and PIN.