

In This Section: |
|
Note - The procedures in this section are relevant for SecureClient. For other clients, see the most updated documentation for that client. |
Suppose a Remote Access Client user connects from behind a NAT device, using a non-private IP address that belongs to another organization. During the life of the connection, the Security Gateway routes all traffic intended for that non-private IP address to the client user, even traffic intended for the real owner of the IP address.
Set the vpn_restrict_client_phase2_id in the Objects_5_0.C file to the appropriate value, as follows:
value |
meaning |
||
|---|---|---|---|
om_only |
Clients behind NAT devices can only connect using Office Mode. |
||
private_and_om |
Clients can connect using either:
|
||
none |
This setting (the default) does not address the problem described above. |
||
|
Note - If the user is restricted to Office Mode or to the use of a private IP address, and attempts another type of connection, the connection will be dropped and a log will be sent to the SmartView Tracker. |
||
If a Remote Access Client located inside the VPN domain of one Security Gateway opens a connection to a host inside the VPN domain of another Security Gateway, the connection will be encrypted twice (once by the client and again by the Security Gateway) and decrypted only once (by the peer Security Gateway).
If a Remote Access Client located inside the VPN domain of one Security Gateway opens a connection to a host inside the VPN domain of another Security Gateway, the connection will be encrypted twice (once by the client and again by the Security Gateway) and decrypted only once (by the peer Security Gateway).
To prevent this from happening, configure the client not to encrypt if both the client and the host (the end-points of the connection) are in the VPN domains of Security Gateways managed by the same Security Management Server.
To do this, enable the send_clear_traffic_between_encryption_domains property in objects_5_0.C.
|
Note - If you enable this feature, ensure that a VPN is defined between the Security Gateways. This feature is disabled when more than one site is defined on the client. |
If the send_clear_traffic_between_encryption_domains property is enabled, a problem can arise when the Security Gateway's VPN domain includes private addresses, where the meaning of "private" is specified in the Non Unique IP Address Ranges page of the Global Properties window.
If the client connects from outside the VPN domain (for example, from a hotel) and is assigned (by the ISP or a NAT device) a private IP address which happens to be in the Security Gateway's VPN domain, then the client will not encrypt when connecting to the VPN domain, and the connection will be dropped because it is in the clear.
You can configure the client to encrypt this traffic as follows:
send_clear_except_for_non_unique property in objects_5_0.C.send_clear_except_for_specific_addresses property in objects_5_0.C.send_clear_except_for_address_group to the name of the group defined in step 1.
|
Note - This feature is disabled when more than one site is defined on the client. |
For users connected in Connect Mode, you can reduce the frequency of authentication by enabling the allow_clear_traffic_while_disconnected property in objects_5_0.C. The client will then not encrypt traffic to the peer encryption domain when not connected. This will prevent unnecessary authentication when connecting to unencrypted services in the peer encryption domain.
For example, if the site includes both private and public HTTP servers, there is no need to encrypt traffic to the public site. To prevent a user from unnecessarily authenticating only because she is an internal user, configure the following two rules in the Desktop Policy:
Source |
Destination |
Service |
Action |
||
|---|---|---|---|---|---|
encryption domain |
encryption domain |
Any |
Accept |
||
Any |
encryption domain |
Any |
Encrypt |
||
|
Note - If you enable this feature, you must ensure that a VPN is defined between the Security Gateways. This feature applies only to Connect Mode. This feature is disabled when more than one site is defined in the client. |
||||
To specify the length of time between re-authentications, select Policy> Global Properties - Remote Access and in the Authentication Timeout section, enter a value in Validation timeout. Alternatively, check Use default value.
For Connect Mode, the countdown to the timeout begins from the time that the Client is connected.
When the timeout expires, the user will be asked to authenticate again. If password-caching is enabled, clients will supply the cached password automatically and the authentication will take place transparently to the user. In other words, the user will not be aware that re-authentication has taken place.
Password caching is possible only for multiple-use passwords. If the user's authentication scheme implement one-time passwords (for example, SecurID), then passwords cannot be cached, and the user will be asked to re-authenticate when the authentication time-out expires. For these schemes, this feature should not be implemented.
Password caching is specified in the client's Authentication window.
To enable Secure Domain Logon (SDL), select Enable Secure Domain Logon from the Passwords menu.
Note the following:
If clients are configured in Connect Mode and Office Mode, clients automatically resolve the NT domain name using dynamic WINS.
Otherwise, clients resolve the NT domain name using either LMHOSTS or WINS.
Enter the relevant information (see below) the $FWDIR/conf/dnsinfo.C file on the Security Gateway, and install the policy.
|
When the topology is updated, the name resolution data will be automatically transferred to the dnsinfo entry of the userc.C file and then to its LMHOSTS file.
The WINS name resolution service can be used in dial-up configurations only. It is not supported on Win 9x platforms.
To use the WINS, proceed as follows on the virtual adapter:
|
Important - You must do this before enabling SDL. See Enabling and Disabling Secure Domain Logon. |
For example, if Domain Suffix is "checkpoint.com" and Match only *.suffix is selected (that is, the maximum prefix label count is in effect 1) then the SecuRemote DNS Server will be used to resolve "www.checkpoint.com" and "whatever.checkpoint.com" but not "www.internal.checkpoint.com."
For example, if Domain Suffix is "checkpoint.com" and Match up to...labels preceding the suffix is selected and set to 3, then the SecuRemote DNS Server will be used to resolve "www.checkpoint.com" and "www.internal.checkpoint.com" but not "www.internal.inside.checkpoint.com".
Split DNS is disabled in the following cases:
To override, set disable_split_dns_when_disconnected in the SecuRemote / SecureClient userc.C file to false.
To override, set disable_split_dns_in_om in the SecuRemote / SecureClient userc.C file to false.
Users consider multiple authentications during the course of a single session to be a nuisance. At the same time, these multiple authentications are an effective means of ensuring that the session has not been hijacked (for example, if the user steps away from the client for a period of time). The problem is finding the correct balance between convenience and security.
Multiple authentication can be reduced by:
When a Remote Access client user logs on to a domain controller, the user has not yet entered credentials and so the connection to the domain controller is not encrypted.
When the Secure Domain Logon (SDL) feature is enabled, then after the user enters the OS user name and password (but before the connection to the domain controller is started), the User Authentication window is displayed. When the user enters the client credentials, the connection to the domain controller takes place over an encrypted tunnel.
Because SDL depends on the synchronization of concurrent processes, flexibility in defining timeouts is important.
The SDL Timeout feature of Secure Domain Logon allows you to define the period during which a user must enter his or her domain controller credentials. When the allocated time expires and no cached information is used (if applicable), the logon fails.
The timeout is controlled by the sdl_netlogon_timeout (<value in seconds>) parameter in the file Objects_5_0.C.
|
Note - This feature is not applicable if Auto Local Logon is enabled (Connect Mode Only). |
When the SecuRemote / SecureClient machine successfully logs on to a domain controller, the user's profile is saved in cache. This cached information will be used if subsequent logons to the domain controller fail, for whatever reason.
To configure this option in the client registry, proceed as follows:
HKLM\Software\Microsoft\Windows NT\Current Version\Winlogon.CachedLogonCount with the valid range of values from 0 to 50. The value of the key is the number of previous logon attempts that a server will cache.A value of 0 disables logon caching and any value above 50 will only cache 50 logon attempts.
After you have rebooted the computer:
The SecuRemote Logon window is displayed.
If you fail to logon and no cached information is used, wait one minute and try again.
If SDL is already configured on the client, the administrator can customize SecuRemote / SecureClient installation packages with SDL enabled by default, thereby relieving the user of the need to configure SDL manually. This can be done in two ways:
You can configure clients to automatically update a site's topology either when starting SecuRemote or just before the IKE key exchange in the Remote Access page of the Global Properties window.
In this window, the system administrator can:
The following features become available if Update topology every ... hours is enabled:
If a SecuRemote / SecureClient is located behind a non-Check Point firewall, the following ports must be opened on the firewall to allow SecuRemote / SecureClient traffic to pass:
Port |
Description |
|---|---|
UDP port 500 |
Always, even if using IKE over TCP |
TCP port 500 |
Only if using IKE over TCP |
IP protocol 50 ESP |
Unless always using UDP encapsulation |
UDP port 2746 |
Only if using MEP, interface resolving or interface High Availability |
UDP port 259 |
Only if using MEP, interface resolving or interface High Availability |
The SecuRemote / SecureClient must resolve the names of internal hosts (behind the Security Gateway) with non-unique IP addresses using an internal DNS server.
The simplest solution is to use Connect Mode and Office Mode. Otherwise, use the split DNS feature by defining a SecuRemote DNS Server.
The SecuRemote DNS Server is an object that represents an internal DNS server that can be used to resolve internal names with private IP addresses (RFC 1918). It is best to encrypt the DNS resolution of these internal names. Not all DNS traffic should be encrypted, as this would mean that every DNS resolution would require authentication.
|
Note - The procedures in this section are relevant for SecureClient. For other clients, see the most updated documentation for that client. |
The Security Gateway provides a single point of entry to the internal network. It is the Security Gateway that makes the internal network "available" to remote machines. If the Security Gateway fails, the internal network is no longer available. It therefore makes good sense to have Multiple Entry Points (MEP) to the same network.
In a MEP environment, more than one Security Gateway is both protecting and giving access to the same VPN domain. How a remote user selects a Security Gateway in order to reach a destination IP address depends on how the MEP Security Gateways have been configured, which in turn depends on the requirements of the organization.
For more information, see Multiple Entry Point VPNs.
The Check Point solution for multiple entry points is based on a proprietary Probing Protocol (PP) that tests Security Gateway availability. The MEP Security Gateways do not have to be in the same location; they can be widely-spaced, geographically.
|
Note - In a MEP Security Gateway environment, the only remote client supported is the Check Point SecuRemote / SecureClient. |
There are three methods used to choose which Security Gateway will be used as the entry point for any given connection:
Preferred Backup Security Gateway allows remote hosts to choose which Security Gateway in the MEP configuration will be the backup Security Gateway. All other Security Gateways in the MEP configuration will be ignored should the first two Security Gateways become unavailable.
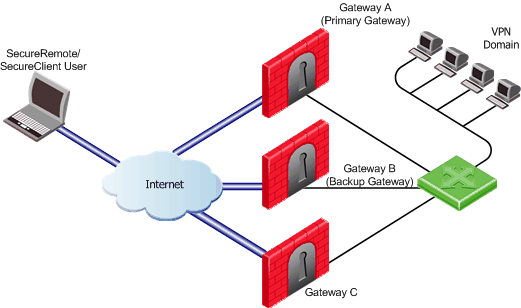
In this scenario:
Since the RDP Security Gateway discovery mechanism used in a MEP environment runs over UDP, this creates a special challenge for SecureClient in Visitor Mode, since all traffic is tunneled over a regular TCP connection.
In a MEP environment:
Must support visitor mode.
The user must be working with a Visitor Mode enabled profile.
To make sure return packets are routed correctly, the MEP Security Gateway makes use of IP pool NAT.
IP pool NAT is a type of NAT in which source IP addresses from remote VPN domains are mapped to an IP address drawing from a pool of registered IP addresses. In order to maintain symmetric sessions using MEP Security Gateways, the MEP Security Gateway performs NAT using a range of IP addresses dedicated to that specific Security Gateway and should be routed within the internal network to the originating Security Gateway. When the returning packets reach the Security Gateway, the Security Gateway restores the original source IP address and forwards the packets to the source.
|
Note - When Office Mode is enabled, there is no need to configure IP Pool NAT since Office Mode dynamically assigns IP's to remote hosts. |
When MEP is disabled, MEP RDP probing and fail over will not be performed. As a result, remote hosts will connect to the Security Gateway defined without considering the MEP configuration.
To configure MEP, decide on the MEP selection method:
When more than one Security Gateway leads to the same (overlapping) VPN domain, they are considered MEP by the remote peer, and the first Security Gateway to respond to the probing protocol is chosen. To configure first to respond, define that part of the network that is shared by all the Security Gateways into a single group and assign that group as the VPN domain.
On the Properties window of each Security Gateway network object, Topology page > VPN Domain section, select Manually defined, and define the same VPN domain for all Security Gateways.
Note - There must be no overlap between the VPN domain of the primary Security Gateway and the VPN domain of the backup Security Gateway(s); that is, no IP address can belong to both.
Checking this option also means that load distribution is dynamic, that is the remote client randomly selects a Security Gateway.
Return packets are handled with IP pool NAT addresses belonging to the Security Gateway.
In Global Properties > NAT page, select Enable IP Pool NAT for SecuRemote / SecureClient and Security Gateway to Security Gateway connections. Then:
In SmartDashboard:
The Connection Profile Properties opens.
Disabling MEP is configured by setting the following command to true in DBedit, the Check Point database tool: