

In This Section: |
A Security Gateway protects a network by enforcing a Security Policy on the traffic to and from that network that passes through the Security Gateway. A remote client, located outside the protected network, is vulnerable to attack because traffic to the remote client does not pass through the Security Gateway. No Security Policy is enforced on this traffic.
There is a further danger: An attacker might gain access to a protected network by compromising a remote client, which can then compromise the protected network (for example, by relaying a virus through the VPN tunnel). Even if the Security Gateway enforces a very restrictive Security Policy, the LAN remains vulnerable to attacks routed through unprotected remote clients.
Check Point clients that include Desktop Security, such as Endpoint Security VPN, protect remote clients by enforcing a Desktop Security Policy on the client. The administrator defines the Desktop Security Policy in the Desktop Rule Base in SmartDashboard. Rules can be assigned either to specific user groups or to all users, enabling the definition of flexible policies.
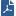
The Desktop Security Policy is downloaded by the Security Management Server to a Policy Server, a module installed on a Security Gateway, which serves as a repository for the Desktop Security Policy. Client machines download their Desktop Security Policies from the Policy Server.
When a client connects to the organization's Security Gateway to establish a VPN, it can connect to a Policy Server as well and retrieve its Desktop Security Policy and begin enforcing it. Clients can accept, encrypt or drop connections depending on their Source, Destination, and Service.
The Desktop Security Policy is divided into two parts:
A rule in a Desktop Security Policy specifies the following:
Connections to machine inside the organization (i.e. all the machines in the VPN domain of the Security Gateway) are automatically encrypted, even if the rule allowing them to pass is an accept rule.
In addition to the inbound and outbound rules explicitly defined by the administrator, implicit "cleanup" rules are automatically appended at the end of both the inbound and outbound policies:
You can define different rules for remote users based on location and user groups:
In addition, you can define rules to be enforced for all remote users, by not specifying a specific user group, but rather all users.
Rules do not specify individual users but rather user groups. Because the client does not know in which groups the currently logged-in user belongs, it must get this information from the Policy Server. After the client authenticates itself to the Policy Server, the Policy Server resolves the user groups to which the user belongs and sends this information to the client. Then the client is able to enforce the rules defined for that user. Rules can also be applied to radius groups on the RADIUS server.
When a client is started, and before it connects to the Policy Server, it enforces a "default policy," which consists of the rules defined for all users in the last policy downloaded from the Policy Server. This is because at this point, the client does not know to which groups the user belongs. The default policy is enforced until the user downloads an updated policy (and the current user's group information) from a Policy server.
If a client loses its connection to the Policy Server, it enforces the default policy until the connection is restored and a Policy is downloaded.
A Policy Server is installed on a Security Gateway, in the Gateway General Properties > Network Software Blades tab. It serves as a repository for the Desktop Security Policy. Client machines download their Desktop Security Policies from the Policy Server.
For load balancing and High Availability, you can configure multiple Policy Servers. Load balancing can be especially important at times of high load, for example, when a large number of users log in at the beginning of the work day.
When a user creates a VPN site on the client, a list of Policy Servers is downloaded to the client machine. If the user is using Connect mode (the default mode), a policy will be automatically downloaded from a Policy Server when the client machine connects to the site. The automatic policy download can also be disabled from the user's profile.
Logs and alert specified Desktop Security Policy can be viewed using the SecureClient Diagnostics. In addition, all alerts are saved and uploaded to the Security Management Server. When the client connects to a Policy Server, it uploads the alerts to a spooling process, which passes the alerts to the Security Management Server, where they can be viewed by the SmartView Tracker.
You should carefully plan your users policy, properly balancing considerations of security and convenience. The policy should allow the desktop users to work as freely as possible, but at the same time make it hard to attack the remote user's desktop. Here are some points to consider:
When using Policy Server High Availability, it is possible that users will connect to the organization through one Security Gateway and to a Policy Server which is installed on a different module. In this case they will be prompted twice for authentication — once for the Security Gateway module and the other for the Policy Server. If a user usually connects to the organization through a specific Security Gateway, and this Security Gateway has a Policy Server module installed on it, this double authentication can be avoided by configuring the user's profile to use the High Availability among all Policy Servers, trying selected first option, and selecting the primary Policy Server as that one the Security Gateway through which the user usually connects to the organization. This way, after the user authenticates to the Security Gateway, he will automatically be authorized to download the security policy from the Policy Server installed on that Security Gateway.
Desktop Security must be configured on the server and on the client machine.
To install desktop security on the server:
The Policy Server add-on should be installed only on machines that have Security Gateway modules installed on them.
In inbound rules, the SecureClient (the desktop) is the destination, and you can specify the users to which the rule is to be applied.
In outbound rules, the SecureClient (the desktop) is the source, and you can specify the users to which the rule is to be applied.
As an administrator, you can eliminate the user's need to configure these steps by creating a custom profile for them.