

In This Section: |
A Virtual Private Network (VPN) provides a secure connection, typically over the Internet. VPNs accomplish this by creating an encrypted tunnel that provides the same security available as in a private network. This allows workers who are in the field or working at home to securely connect to a remote corporate server and also allows companies to securely connect to branch offices and other companies over the Internet. The VPN tunnel guarantees:
Types of tunnels and the number of tunnels can be managed with the following features:
The status of all VPN tunnels can be viewed in SmartView Monitor. For more information on monitoring see the Monitoring Tunnels chapter in the R77 SmartView Monitor Administration Guide.
As companies have become more dependent on VPNs for communication to other sites, uninterrupted connectivity has become more crucial than ever before. Therefore it is essential to make sure that the VPN tunnels are kept up and running. Permanent Tunnels are constantly kept active and as a result, make it easier to recognize malfunctions and connectivity problems. Administrators can monitor the two sides of a VPN tunnel and identify problems without delay.
Each VPN tunnel in the community may be set to be a Permanent Tunnel. Since Permanent Tunnels are constantly monitored, if the VPN tunnel is down, then a log, alert, or user defined action, can be issued. A VPN tunnel is monitored by periodically sending "tunnel test" packets. As long as responses to the packets are received the VPN tunnel is considered "up." If no response is received within a given time period, the VPN tunnel is considered "down." Permanent Tunnels can only be established between Check Point Security Gateways. The configuration of Permanent Tunnels takes place on the community level and:
In a Multiple Entry Point (MEP) environment, VPN tunnels that are active are rerouted from the predefined primary Security Gateway to the backup Security Gateway if the primary Security Gateway becomes unavailable. When a Permanent Tunnel is configured between Security Gateways in a MEP environment where RIM is enabled, the satellite Security Gateways see the center Security Gateways as "unified." As a result, the connection will not fail but will fail over to another center Security Gateway on a newly created permanent tunnel. For more information on MEP see Multiple Entry Point VPNs.
In this scenario:
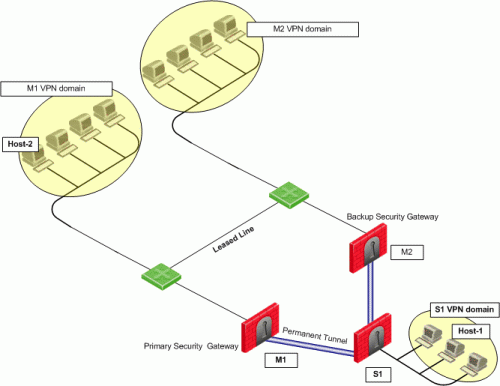
In this case, should Security Gateway M1 become unavailable, the connection would continue through a newly created permanent tunnel between S1 and M2.
Check Point uses a proprietary protocol to test if VPN tunnels are active, and supports any site-to-site VPN configuration. Tunnel testing requires two Security Gateways, and uses UDP port 18234. Check Point tunnel testing protocol does not support 3rd party Security Gateways.
In addition to Tunnel Testing, Dead Peer Detection (DPD) is a different method to test if VPN tunnels are active. Dead Peer Detection does support 3rd party Security Gateways and supports permanent tunnels with interoperable devices based on IKEv1/IKEv2 DPD (IKEv1 DPD is based on RFC 3706). It uses IPsec traffic patterns to minimize the number of messages required to confirm the availability of a peer.
The tunnel testing mechanism is the recommended keepalive mechanism for Check Point to Check Point VPN gateways because it is based on IPsec traffic and requires an IPsec established tunnel. DPD is based on IKE encryption keys only.
DPD has two modes:
In this mode the Check Point gateway sends the IKEv1 DPD Vendor ID to peers, from which the DPD Vendor ID was received.
To enable DPD Responder Mode:
ckp_regedit -a SOFTWARE/CheckPoint/VPN1 forceSendDPDPayload -n 1
To disable DPD Responder Mode:
ckp_regedit -d SOFTWARE/CheckPoint/VPN1 forceSendDPDPayload
Note - Enable the keep_IKE_SAs property in SmartDashboard to prevent a problem, where the Check Point gateway deletes IKE SAs. The DPD mechanism is based on IKE SA keys. In some situations, the Check Point gateway deletes IKE SAs and a peer, usually a 3rd Party gateway, sends DPD requests without response and concludes that the Check Point gateway is down. The peer can then delete the IKE and IPsec keys, which causes encrypted traffic from the Check Point gateway to be dropped by the remote peer.
DPD can monitor remote peers with the permanent tunnel feature. All related behavior and configurations of permanent tunnels are supported.
To configure DPD for a permanent tunnel, the permanent tunnel must be in the VPN community. After you configure the permanent tunnel, configure Permanent Tunnel mode Based on DPD. There are different possibilities for permanent tunnel mode:
Note: To use this mode for only some gateways, enable the forceSendDPDPayload registry key on Check Point remote peers.
To enable DPD monitoring:
On each VPN gateway in the VPN community, configure the tunnel_keepalive_method property, in GuiDBedit Tool (see sk13009) or dbedit (see skI3301). This includes 3rd Party gateways. (You cannot configure different monitor mechanisms for the same gateway).
Optional Configuration
Edit the property in GuiDBedit Tool (see sk13009) > Network Objects > network_objects > <gateway Name> > VPN.
To disable this feature, set the DPD_DONT_DEL_SA environment variable to 0:
cpstop
export DPD_DONT_DEL_SA=0
cpstart
$CPDIR/tmp/.CPprofile.sh file:DPD_DONT_DEL_SA=0 ; export DPD_DONT_DEL_SA
Note - To re-enable the feature, remove the DPD_DONT_DEL_SA environment variable.
Tunnel test is a proprietary Check Point protocol used to see if VPN tunnels are active. Tunnel testing requires two Security Gateways and uses UDP port 18234. Third party gateways do not support tunnel testing.
VPN Tunnel Sharing provides interoperability and scalability by controlling the number of VPN tunnels created between peer Security Gateways. There are three available settings:
To configure Tunnel Management options, proceed as follows:
The Tunnel Management window is displayed.
In the Community Properties window on the Tunnel Management page, select Set Permanent Tunnels and the following Permanent Tunnel modes are then made available:
To configure all tunnels as permanent, select On all tunnels in the community. Clear this option to terminate all Permanent Tunnels in the community.
To configure on all tunnels of specific Security Gateways:
The Select Security Gateways window is displayed.
To terminate Permanent Tunnels connected to a specific Security Gateway, highlight the Security Gateway and click Remove.
To configure on specific tunnels in the community:
The Select Permanent Tunnels window opens.
To terminate the Permanent Tunnel between these two Security Gateways, clear Set these tunnels to be permanent tunnels.
In SmartDashboard:
The Global Properties window is displayed.
The Advanced configuration window is displayed.
Several types of alerts can be configured to keep administrators up to date on the status of the VPN tunnels. The Tracking settings can be configured on the Tunnel Management page of the Community Properties screen for all VPN tunnels or they can be set individually when configuring the permanent tunnels themselves. The different options are Log, Popup Alert, Mail Alert, SNMP Trap Alert, and User Defined Alert. Choosing one of these alert types will enable immediate identification of the problem and the ability to respond to these issues more effectively.
Once a Permanent Tunnel is no longer required, the tunnel can be shut down. Permanent Tunnels are shut down by deselecting the configuration options to make them active and re-installing the policy.
For a VPN community, the configuration is set on the Tunnel Management page of the Community Properties window.
For a specific Security Gateway, the configuration is set on the VPN Advanced page of the Security Gateway properties window.
VPN Tunnel Sharing provides greater interoperability and scalability by controlling the number of VPN tunnels created between peer Security Gateways. Configuration of VPN Tunnel Sharing can be set on both the VPN community and Security Gateway object.
In case of a conflict between the tunnel properties of a VPN community and a Security Gateway object that is a member of that same community, the "stricter" setting is followed. For example, a Security Gateway that was set to One VPN Tunnel per each pair of hosts and a community that was set to One VPN Tunnel per subnet pair, would follow One VPN Tunnel per each pair of hosts.