SmartLSM Clusters
A SmartLSM Cluster is a logical entity that provides high-availability VPN connectivity by using two devices, each serving as an entry point to the same network. In a SmartLSM Cluster, there is no state synchronization between the devices: if the active SmartLSM Cluster member becomes unavailable, users are not automatically connected to the other member. The party that initiated the communication must actively intervene to reconnect the users.
To create a SmartLSM Cluster, you need two UTM-1 Edge SmartLSM Security Gateways. A gateway can participate in only one SmartLSM Cluster at a time.
To create a topology in which two UTM-1 Edge SmartLSM Security Gateways serve as entry points to the same network, a mechanism such as VRRP clustering must be configured for that network. This configuration handles the routing in situations where only one of the gateways is available, as well as in situations where both of the gateways are available.
Overview
The basic procedure for creating and configuring SmartLSM clusters includes these steps:
- Create a SmartLSM security profile in SmartDashboard. Profiles set common parameters and policies for SmartLSM clusters created using that profile.
- Create SmartLSM cluster objects in SmartProvisioning based on a SmartLSM security profile.
- Configure parameters for individual networks using SmartProvisioning, or using
LSMcli commands.
You define these common parameters in SmartLSM a cluster security profile:
- Cluster members.
- Cluster member physical interfaces.
- Interface network objective (Cluster, Sync etc.).
- Cluster interface names.
- Cluster and member interface IP addresses and net masks.
- When you create a SmartLSM cluster security profile, define complete IP addresses. These addresses are placeholders and you can override them when you create SmartLSM cluster objects in SmartProvisioning.
- Cluster and member name components - It is convenient to have a component of cluster and cluster member names describe the specific cluster, and another component, common to all clusters that are mapped to a given Profile, reflect the relative function in the cluster. The common component is defined at the Profile level. The cluster-specific component is defined in SmartProvisioning for the specific cluster, as a prefix or a suffix to the common component. For example, you could have two two-member clusters, named First_cluster and Second_cluster. You could then name the respective members First_member1, First_member2, Second_member1 and Second_member2. In this example, you would define the names _cluster, _member1 and _member2 at the Profile level. Then, when you define individual clusters, you will need to define only the names First and Second as name prefixes.
SmartProvisioning Clusters can be managed either by a Security Management Server or by a Domain Management Server.

|
Note - SmartProvisioning is not available for the members of a SmartProvisioning cluster, even if the member gateway runs the SecurePlatform OS.
|
Managing SmartLSM Clusters
Creating a SmartLSM Profile
A SmartProvisioning Security Clusterprofile is a template for policies that apply to SmartLSM clusters. When you define a new SmartLSM cluster, you select the SmartLSM profile to automatically assign the configuration settings and security policies. Use SmartDashboard to create SmartLSM Security Cluster Profiles.
When you make a new SmartLSM cluster using a profile, define prefixes and suffixes for the profile name to form the full cluster name. This makes it easy to identify which SmartLSM profile is assigned to a cluster.
To create a SmartLSM Security Cluster Profile:
- In SmartDashboard, right-click in the Network Objects tree.
- Select and then select the cluster you want:
- Check Point Appliance/Open Server Cluster
- 80 Series Cluster
The window opens.
- On the page, do these steps:
- Enter the profile .
The profile name becomes the middle section of all SmartLSM cluster names that you define using this profile. - If your clusters use a third-party clustering platform (such as IPSO or Crossbeam), clear .

|
Note - When using third party cluster platforms, create a different SmartLSM Profile for each platform type.
|
- Make sure that is selected, if clusters using this profile are part of a VPN community.
- On the page, add members to the Profile. These member names become the middle section of all member names defined using this Profile.
- Configure the applicable parameters on the or page.
- On the page, click .
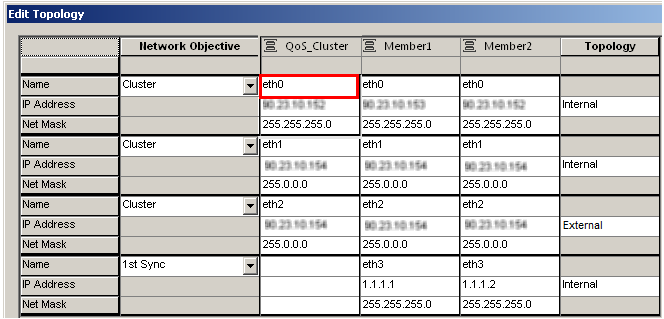
- Configure each interface in the cluster column. Set the options in the tab. The information in the other two tabs is according to the information in the Topology spreadsheet.
Use these guidelines:
- Make sure that the number of interfaces and their network objectives match those of the physical SmartLSM clusters.
- For interfaces with Private or Sync network objectives, do not enter information in the Cluster column.
- Every SmartLSM cluster mapped to this Profile will retain the host parts (by net mask) of the member IP addresses, and the name of the cluster (virtual) interface.
- The network parts of the members’ IP addresses and the whole cluster IP addresses are here only place holders. You will later define them in SmartLSM for each SmartLSM cluster.
- Make sure that the host ID for the external interface of the SmartLSM cluster profile is the same as the actual external interface of the cluster.
- The network parts of the members IP addresses must be identical for the same interface name, even though they are only place holders.
- Profile member interface names can be overridden for the actual SmartLSM cluster. However, they are usually the same for all clusters (eth0, eth1 and so on), so it is convenient to use the actual names here as well.
- Optionally change the interval on the page.
Select a Scheduled Event or create a new one.
- Configure other parameters as required. You define VPN domains for cluster objects using SmartProvisioning.
- Click to confirm the settings, and save the Policy Package.
- In SmartDashboard, install policies to the cluster Profile.
Configuring SmartLSM Clusters
Before you define a SmartLSM cluster, there must be an applicable SmartLSM Security Cluster Profile definition in SmartDashboard. Use SmartProvisioning to create and configure a SmartLSM cluster. SmartDashboard must be closed or in Read Only mode.

|
Note - Alternatively, you can use LSMcli commands (possibly, in a script) to define SmartLSM clusters, for example AddROBO VPN1Cluster”. Using LSMcli commands enables replacing a part of Profile names, which is not possible when using the SmartProvisioning interface.
|
To define a SmartLSM Cluster
- From the File menu, select New > SmartLSM Cluster.
- Enter a Cluster Name Prefix and/or Suffix to be added onto the Profile cluster and member names.
- Enter the main IP address of the SmartLSM cluster, and click Next.
- Define the SmartLSM Cluster Version and the SmartLSM Security Cluster Profile. Click Next.
- Verify the resulting names, and click Next.
The network overrides window opens. This window shows the interface topology defined on the Cluster Profile object in SmartDashboard. The profile topology includes generic (template) IPs for any SmartLSM Cluster mapped to this profile. The IP addresses in the list can be overridden with new values for a specific SmartLSM Cluster.
- Select each interface and Edit it.
The settings here will override Profile settings.
- For each interface, define:
- The Members’ Network Override address (usually the same for all interfaces).
- Members’ interface Name Override (must match the name defined in the operating system)
- The Cluster IP Address and Net Mask.
For fields left empty, the values will be taken from the Profile. You can define the overrides later on by editing the cluster object. You can also override interface topology by editing the cluster object.
- Click Next.
- Select each member, and, for each member, Initialize SIC communication (alternatively, you can do this later - edit the member object and, in the General tab, click Communication). The Communication window opens. SIC will be actually initialized only upon completing the wizard.
- Click Next.
- Specify whether to create a VPN certificate for the cluster.
The certificate will be actually created only upon completing the wizard. You can, later on, create VPN certificates for the individual cluster members - edit the member object and, in the VPN tab, click Generate.
- Click Next.
- Specify whether you will want to configure additional cluster options (such as VPN settings or Dynamic Objects) once the SmartLSM cluster object is created, and click Finish.
SmartProvisioning creates the SmartLSM Cluster object and its members.

|
Note - Once a SmartLSM Cluster is defined and mapped to a Profile, do not add or remove a member or an interface. Do not change a cluster (virtual) interface name.
|
- To retrieve the policy for the first time, from the command line of each SmartLSM Cluster member, run:
fw fetch_robo -n -f
Additional Configuration
You can configure the above and additional properties (VPN, Dynamic Objects, SIC etc.) by double-clicking cluster and/or member objects in SmartLSM. Member properties are also accessible from the Cluster tab of the cluster properties.
Various SmartLSM and ClusterXL options and commands are available for SmartLSM Clusters.
Pushing a Policy
In the general SmartLSM system, you can manually push a policy to a SmartLSM gateway. For a SmartLSM cluster, push the policy to the cluster object. All the cluster members will receive the policy.
To push a policy to a SmartLSM cluster:
- Right-click the SmartLSM cluster object in SmartLSM.
- From the Action menu, select Push Policy.
You can also push a policy using the command line interface.
Command Line Reference
This section covers:
LSMenabler
This general LSM command applies to SmartLSM Clusters.
To view parameters and the current LSM definition (Security Management Server, SmartLSM gateway etc.), run LSMenabler with no parameters.
Managing SmartLSM Clusters with LSMcli
Using the LSMcli command, you can define SmartLSM clusters, and configure most of the options available in SmartLSM (in the New SmartLSM Cluster wizard and in Edit windows).
The LSMcli command syntax is:
LSMcli [-d] <server> <user> <pswd> <action>
This section lists available actions for SmartLSM Clusters. Substitute the command syntaxes in this section for the <actions> field in the above syntax.
What You Can Do with LSMcli
The main SmartLSM Cluster actions are:
- Define a new SmartLSM cluster
- Change a SmartLSM cluster main IP address
- Resolve a dynamic object for a SmartLSM cluster
- Set the VPN domain of a SmartLSM cluster
- Define the topology of a cluster (virtual) interface (external/internal, anti-spoofing etc.)
- Manage overrides for cluster members’ interface names and network addresses, and for cluster interface IP addresses and net masks
- Delete a SmartLSM cluster
AddROBO VPN1Cluster
You can define a new SmartLSM cluster with the AddROBO VPN1Cluster action. You can configure all of the options available in the New SmartLSM Cluster wizard, with the AddROBO VPN1Cluster command parameters. The only exception is the Topology overrides.
To define a new SmartLSM cluster, substitute the following for <action> in the LSMcli syntax:
AddROBO VPN1Cluster <Profile> <MainIPAddress> <SuffixName> [-S=<SubstitutedNamePart>]
[-CA=<CaName> [-R=<KeyIdentifier#>] [-KEY=<AuthorizationCode>]]
Parameter
|
Description
|
SmartLSM GUI Location
|
<Profile>
|
Name of cluster Profile to which to map the new cluster.
|
New SmartLSM Cluster wizard.
|
<MainIPAddress>
|
Main IP address of cluster.
|
New SmartLSM Cluster wizard.
|
<SuffixName>
|
A suffix to be added to cluster and member Profile names.
|
New SmartLSM Cluster wizard.
|
<SubstitutedName
Part>
|
A part of the Profile name to be replaced by the suffix in the previous field.
|
SmartLSM GUI supports adding Prefix and/or Suffix, not substitution.
|
<CAName>
|
The name of the Trusted CA object, defined in SmartDashboard, to which a VPN certificate request will be sent.
|
VPN tab of Edit window (double-click SmartLSM object).
|
<KeyIdentifier#>
|
Number to identify the specific certificate, once generated.
|
VPN tab of Edit window (double-click SmartLSM object).
|
<AuthorizationCode>
|
Authorization Key to be sent to CA to enable certificate retrieval.
|
VPN tab of Edit window (double-click SmartLSM object).
|
ModifyROBO VPN1Cluster
-I - Changing the Main IP Address
You can change a SmartLSM cluster main IP address either in the tab of the cluster Edit window (double-click the cluster object), or with the ModifyROBO VPN1Cluster action.
To change a SmartLSM cluster main IP address with the ModifyROBO VPN1Cluster action, substitute the following for <action> in the LSMcli syntax:
ModifyROBO VPN1Cluster <ROBOClusterName> -I=<MainIPAddress>
where <ROBOClusterName> is the cluster name, and
<MainIPAddress> is the new IP address.
-D - Resolving a Dynamic Object
You can resolve a dynamic object for a SmartLSM cluster either in the tab of the cluster Edit window (double-click the cluster object), or with the ModifyROBO VPN1Cluster action.
To resolve a dynamic object for a SmartLSM cluster, substitute the following for <action> in the LSMcli .syntax:
ModifyROBO VPN1Cluster <ROBOClusterName> -D:<D.O. Name>=<IP|IP1-IP2>
where
<ROBOClusterName> is the cluster name,
<D.O. Name> is the Dynamic Object name, and
<IP|IP1-IP2> is an IP address or a range of IP addresses.
ModifyROBOTopology VPN1Cluster
You can set the VPN domain of a SmartLSM cluster either in the VPN Domain area in the Topology tab of the cluster Edit window (double-click the cluster object), or with the ModifyROBO VPN1Cluster action.
To set the VPN domain of a SmartLSM cluster, substitute the following for <action> in the LSMcli syntax:
ModifyROBOTopology VPN1Cluster <RoboClusterName>
-VPNDomain=<not_defined|external_ip_only|topology|manual>
The parameters are the same as in the regular (non-cluster) ModifyROBOTopology VPN1, at the cluster level.

|
Note - When the VPN domain is set to Manual, the IP address ranges are those set in the SmartLSM GUI or with the ModifyROBOManualVPNDomain action.
|
ModifyROBOManualVPNDomain
This general LSM command applies to SmartLSM Clusters, with the same syntax, using the cluster name for <ROBOName>.
ModifyROBONetaccess VPN1Cluster
You can, for the actual SmartLSM cluster, override the profile topology definitions of a cluster (virtual) interface either by editing the interface in the upper half of the cluster tab of the cluster window, and then going to the interfacetab, or with the ModifyROBONetaccess VPN1Cluster action.
To define the topology of an interface, substitute the following for <action> in the LSMcli syntax:
ModifyROBONetaccess VPN1Cluster <ClusterName> <InterfaceName>
-Mode=<by_profile|override> [-TopologyType=<external|internal>]
[-InternalIP=<not_defined|this|specific> [-AllowedGroup=<GroupName>]]
[-DMZAccess=<true|false>] [-AntiSpoof=<false|true> [-AllowedGroup=<GroupName>]
[-SpoofTrack=<none|log|alert>]]
Parameter
|
Description
|
<ClusterName>
|
Name of SmartLSM cluster.
|
<InterfaceName>
|
Name of cluster (virtual) interface. If the interface’s network objective (as defined in the Profile topology) is Sync only (not cluster+sync), there is no cluster interface, only member interface. In this case use the network objective (e.g., 1st Sync) for this parameter.
|
<-Mode>
|
by_profile to set as defined in cluster Profile, or override to here define the settings, in which case specify -TopologyType.
|
<-TopologyType>
|
external (leads out to the internet) or internal (leads to the local network).
|
<-InternalIP>
|
Defines hosts behind an internal interface: not_defined; network defined by IP and net mask of this interface; or: specific, by AllowedGroup.
|
<-DMZAccess>
|
true, if internal interface leads to DMZ. Otherwise, false.
|
<-AntiSpoof>
|
true, to perform Anti-Spoofing based on interface topology, in which case optionally define an AllowedGroup, and set SpoofTrack; or false, to not perform Anti-Spoofing. If the interface is internal and the addresses behind the interface are not defined, Anti-Spoofing is not possible.
|
<-AllowedGroup>
|
If TopologyType=external, AllowedGroup defines a group from which packets are not checked, if Anti-Spoofing is performed. If TopologyType=internal, AllowedGroup specifically (explicitly) defines the hosts behind the internal interface.
|
<-SpoofTrack>
|
Desired tracking action when detecting spoofing: none, log or alert.
|
ClusterSubnetOverride Actions (Add, Modify and Delete)
Cluster members’ interface names and network addresses, and cluster interface IP addresses and net masks, have default values from the Profiles they are associated with. These values can (and in the case of addresses, usually should) be overridden for the individual SmartLSM cluster.
In SmartLSM, this is done by editing the interface, either in the New SmartLSM Cluster wizard, or in the tab of the general window for the cluster (double-click the cluster object).
In LSMcli, substitute the following for <action> in the LSMcli syntax:
<Add|Modify|Delete>ClusterSubnetOverride VPN1Cluster <ROBOClusterName> <InterfaceName> [-IName=<MembersInterfaceName>] [-MNet=<MembersNetAddress>]
[-CIP=<ClusterIPAddress> -CNetMask=<ClusterNetMask>]
If there is a set override value, and you want to change it, use only ModifyClusterSubnetOverride. If the override value you want to set is not defined (except at the Profile level), because it has never been defined or because it was deleted, use only AddClusterSubnetOverride. To cancel a value and return to the Profile value, use DeleteClusterSubnetOverride.
The action must define at least one parameter: -IName, -MNet, or both -CIP and -CNetMask.

|
Note - To define overrides for a private (monitored or non-monitored) interface, use the PrivateSubnetOverride action.
|
Explanations of the parameters are:
Parameter
|
Description
|
Add|Modify|Delete
|
Defines the action - see above. No space after this parameter.
|
ROBOClusterName
|
The SmartLSM cluster to override values for.
|
InterfaceName
|
Name of cluster (virtual) interface, as defined in the Profile topology. Use the cluster interface name even though you may be setting values for members’ interfaces. If the interface’s network objective (as defined in the Profile topology) is Sync only (not cluster+sync), there is no cluster interface, only member interface. In this case use the network objective (e.g., 1st Sync) for this parameter.
|
-IName
|
New interface name for cluster members. The name must match the name defined in the operating system.
|
-MNet
|
New network address for cluster members. This address will be combined with the host parts defined in the Profile to produce complete IP addresses.
|
-CIP
|
New IP address for the cluster (virtual) interface.
|
-CNetMask
|
Net mask for ClusterIPAddress.
|
PrivateSubnetOverride Actions (Add, Modify and Delete)
This action is similar to the ClusterSubnetOverride action, for a private (monitored or non-monitored) interface. For a private interface, you can only override cluster members’ interface names and network addresses, not cluster interface IP addresses or net masks.
In LSMcli, substitute the following for <action> in the LSMcli syntax:
<Add|Modify|Delete>PrivateSubnetOverride VPN1ClusterMember <ROBOMemberName> <InterfaceName> [-IName=<MembersInterfaceName>] [-MNet=<MembersNetAddress>]
If there is a set override value, and you want to change it, use only ModifyPrivateSubnetOverride. If the override value you want to set is not defined (except at the Profile level), because it has never been defined or because it was deleted, use only AddPrivateSubnetOverride. To cancel a value and return to the Profile value, use DeletePrivateSubnetOverride.
The action must define at least one parameter: -IName or -MNet.
Explanations of the parameters are:
Parameter
|
Description
|
Add|Modify|Delete
|
Defines the action - see above. No space after this parameter.
|
ROBOMemberName
|
The SmartLSM cluster member to override values for.
|
InterfaceName
|
Current name of member interface, as defined in the Profile topology.
|
-IName
|
New interface name. The name must match the name defined in the operating system.
|
-MNet
|
New network address for this interface. This address will be combined with the host parts defined in the Profile to produce complete IP addresses.
|
RemoveCluster
This action will revoke all the certificates used by the SmartLSM cluster and its members, release all the licenses and, finally, will delete the SmartLSM cluster and member objects.
In LSMcli, substitute the following for <action> in the LSMcli syntax:
RemoveCluster <ROBOClusterName>
ResetSic
This general LSM command applies to SmartLSM Clusters, with the same syntax as for regular SmartLSM gateways, using a cluster member name for <ROBOName>
ResetIke
This general LSM command applies to SmartLSM Clusters, with the same syntax as for regular SmartLSM gateways. For <ROBOName> use either a cluster name, to reset IKE for the cluster, or a cluster member name, to reset IKE for that member.
ExportIke
This general LSM command applies to SmartLSM Clusters, with the same syntax as for regular SmartLSM gateways. For <ROBOName> use either a cluster name, to export IKE for the cluster, or a cluster member name, to export IKE for that member.
Convert Actions
There is no convert action for or to SmartLSM clusters.
SmartUpdate Actions
The SmartUpdate actions listed in this guide apply to SmartLSM cluster members, with the same syntax as for regular SmartLSM gateways.
Push Policy
This general LSM command applies to SmartLSM Clusters, with the same syntax as for regular SmartLSM gateways. In the command syntax, use the cluster name (not a cluster member name). The policy is pushed to all cluster members.
Other Push Actions
PushDOs and GetStatus are general LSM commands that apply to SmartLSM cluster members, with the same syntax as for regular SmartLSM gateways.
Activating a SmartLSM Cluster with QoS
This feature is supported in R77.10 (and higher) Clusters.
In SmartDashboard:
- Create a SmartLSM Cluster profile.
- On the SmartLSM page, select .
- On the page, click .
- Double-click the QoS cluster interface.
The window opens.
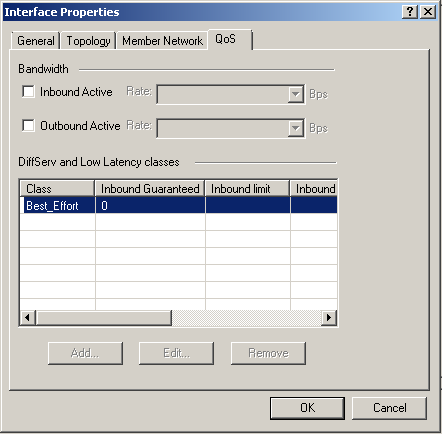
- On the tab, configure:
- On the main QoS tab in SmartDashboard, define QoS rules.
- Install the QoS policy on the SmartLSM profile.
In SmartProvisioning:
- Right-click the SmartLSM Cluster object.
- Select .
Note: These steps are not obligatory. Gateways periodically fetch their policies from the Security Management Server.
|
|



