Using Monitor Mode
Introduction to Monitor Mode
Monitor Mode can be configured on Check Point Security Gateway interfaces. It lets Check Point Security Gateways monitor traffic from a mirror port or span port on a switch. Use Monitor Mode to analyze network traffic without changing the production environment. The mirror port on a switch duplicates the network traffic and sends it to the monitor interface on the gateway to record the activity logs.
You can use mirror ports in these scenarios:
- To monitor the use of applications as a permanent part of your deployment
- To evaluate the capabilities of the Application Control and IPS blades before you buy them
The mirror port does not enforce a policy or do any active operation (prevent/drop/reject) on network traffic. It can be used only to evaluate the monitoring and detecting capabilities of the Software Blades.
All duplicated packets that arrive at the monitor interface of the gateway are terminated and will not be forwarded.
The Security Gateway does not send traffic through the monitor interface.
Supported Software Blades for Monitor Mode
These Software Blades support Monitor mode for Security Gateway deployment:
Supported Blade
|
Supports Gateways in Monitor Mode
|
Supports VS in Monitor Mode
|
Firewall
|
Yes
|
Yes
|
IPS
|
Yes
|
Yes
|
URL Filtering
|
Yes
|
Yes
|
DLP
|
Yes
|
No
|
Anti-Bot
|
Yes
|
Yes
|
Application Control
|
Yes
|
Yes
|
Identity Awareness
|
Yes
|
No
|
Threat Emulation
|
Yes
|
Yes
|
Monitor Mode - Software Blades Not Supported
These features, Software Blades and deployments are not supported in Monitor mode:
- NAT
- IPsec VPN
- HTTPS Inspection
- Mobile Access
- DLP with FTP
- HTTP/HTTPS proxy
- Anti-Spam and Email Security
- QoS
- Traditional Anti-Virus
- User Authentication
- Client Authentication
Unsupported Monitor Mode Deployments
These are deployments do not support Monitor Mode:
- Access to Portals
- Multiple TAP interfaces when the same traffic is monitored
Configuring Monitor Mode
You can configure a mirror or TAP port to duplicate network traffic that is sent to a Security Gateway. The gateway inspects the traffic but does not drop packets.
Connect the Security Gateway to a mirror port on the switch that duplicates the appropriate ports and VLANs.
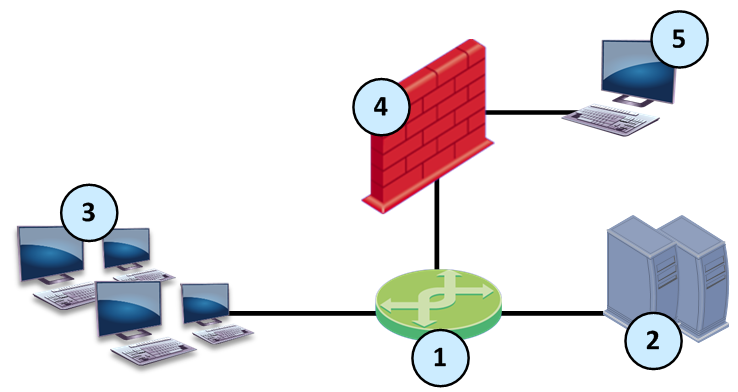
|
|
|
|
Item
|
Description
|
1
|
Switch with mirror port
|
2
|
Servers
|
3
|
Computers
|
4
|
Security Gateway in monitor mode
|
5
|
Management for Security Gateway
|

|
Note - Make sure that one mirror port on the switch is connected to one interface on the Security Gateway.
|
To enable monitor mode on the Security Gateway from the WebUI:
- From the navigation tree, click .
- Select the interface and click .
- Click the tab.
- Click .
- Click .
To enable monitor mode on the Security Gateway from the clish:
Run this command:
> set interface <int name> monitor-mode on
|



