
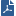

Configure RADIUS Accounting in the RADIUS Accounting Settings window. In the Check Point Gateway window > Identity Awareness page, click RADIUS Accounting > Settings.
Included Topics |
Gateway interfaces must be authorized to accept connections from RADIUS Accounting clients.
To select gateway interfaces:
|
Important - The All Interfaces and Internal Interface options have priority over Firewall Policy rules. If a Firewall rule is configured to block connections from RADIUS Accounting clients, connections continue to be allowed when one of these options are selected. |
An Identity Awareness Gateway accepts RADIUS Accounting requests only from authorized RADIUS Accounting clients. A RADIUS Accounting client is a host with a RADIUS client software installed.
To configure an authorized RADIUS client:
Click New to define a new host object for the RADIUS Accounting client. This host object is selected automatically.
Click the - icon to remove an existing RADIUS client from the list.
You can manually enter a shared secret. It is not necessary to generate a new shared secret when you add or remove clients from the list.
RADIUS Accounting Messages contain identity, authentication and administrative information for a connection. This information is contained in predefined attributes of the RADIUS Accounting Message packet.
The Message Attributes Indices section tells Identity Awareness which attributes in RADIUS Accounting Messages contain identity information used by Identity Awareness:
Select a message attribute for each of these values. The default attributes are correct for many Identity Awareness deployments.
|
Note - Vendor-Specific (26) is a user-defined attribute. There can be more than one Vendor-Specific attribute in a RADIUS Accounting message, each with a different value. |
To configure message attributes:
You can define the user session timeout. This parameter is the maximum time that a user session stays open without receiving an Accounting Start or Interim-Update message from the RADIUS Accounting client. To define the session timeout, enter or select a value in minutes (default = 720).
You can select which LDAP account units the Security Gateway searches for user or device information when it gets a RADIUS Accounting request. LDAP account units are configured in SmartDashboard.
To define the authorized LDAP account units:
Identities are acquired for Mobile Access clients and IPSec VPN clients configured to work in Office Mode when they connect to the Security Gateway. This option is enabled by default.
To configure Remote Access:
Select Remote Access to enable it, or clear this option to disable it.
|
Important - If there is more than one Security Gateway enabled with Identity Awareness that share identities with each other and have Office Mode configured, each gateway must be configured with different office mode ranges. |