

In This Section: |
SmartUpdate automatically distributes applications and updates for Check Point and OPSEC Certified products, and manages product licenses. It provides a centralized means to guarantee that Internet security throughout the enterprise network is always up to date. SmartUpdate turns time-consuming tasks that could otherwise be performed only by experts into simple point and click operations.
SmartUpdate extends your organization's ability to provide centralized policy management across enterprise-wide deployments. SmartUpdate can deliver automated software and license updates to hundreds of distributed security Gateways from a single management console. SmartUpdate ensures security deployments are always up-to-date by enforcing the most current security software. This provides greater control and efficiency while dramatically decreasing maintenance costs of managing global security installations.
SmartUpdate enables remote upgrade, installation and license management to be performed securely and easily. A system administrator can monitor and manage remote Gateways from a central location, and decide whether there is a need for software upgrade, new installations and license modification. It is possible to remotely upgrade:
All operations that can be performed via SmartUpdate can also be done via the command line interface. See The SmartUpdate Command Line for more information.
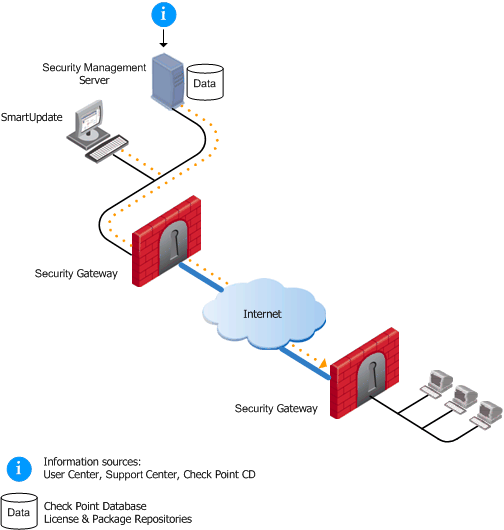
SmartUpdate installs two repositories on the Security Management Server:
%FWDIR%\conf\.$FWDIR/conf/.C:\SUroot./var/suroot.The Package Repository requires a separate license, in addition to the license for the Security Management Server. This license should stipulate the number of nodes that can be managed in the Package Repository.
Packages and licenses are loaded into these repositories from several sources:
cplic command lineOf the many processes that run on the Check Point Security Gateways distributed across the corporate network, two in particular are used for SmartUpdate. Upgrade operations require the cprid daemon, and license operations use the cpd daemon. These processes listen and wait for the information to be summoned by the Security Management Server.
From a remote location, an administrator logged into the Security Management Server initiates operations using the SmartUpdate tool. The Security Management Server makes contact with the Check Point Security Gateways via the processes that are running on these Gateways in order to execute the operations initiated by the system administrator (e.g., attach a license, or upload an upgrade). Information is taken from the repositories on the Security Management Server. For instance, if a new installation is being initiated, the information is retrieved from the Package Repository; if a new license is being attached to remote gateway, information is retrieved from the License & Contract Repository.
This entire process is Secure Initial Communication (SIC) based, and therefore completely secure.
SmartUpdate has two tabs:
These tabs are divided into a tree structure that displays the packages installed and the licenses attached to each managed Security Gateway.
The tree has three levels:
Additionally, the following panes can be displayed:
Installing package <X> on Gateway <Y>, or Attaching license <L> to Gateway <Y>.).Drag and Drop - Packages and licenses can be dragged and dropped from the Repositories onto the Security Gateways in the Package/Licenses Management tree. This drag and drop operation will invoke the distribute or attach operation respectively.
Search - To search for a text string: select Tools > Find. In Find what, enter a string to search for. Select search location: Network Objects License & Contract tab or Package Repository.
Sort - To sort in ascending or descending order, click the column title in the Licenses or Packages tab.
Expand or Collapse - To expand or collapse the Check Point Security Gateways tree structure, right-click on the tree root and choose Expand/Collapse.
Change view - To change the Repository view, right-click on a blank row or column in the Repository window and select an option. For example, in the Licenses Repository you can select to see only the attached licenses.
Clear Repository of completed operations - To clear a single operation, select the line in the Operation Status window and press the Delete key, or right-click and select Clear. To clear all completed operations from the Operation Status window, select Status > Clear all completed operations.
See operation details - To view operation details, in the Operation Status window, double-click the operation entry. The Operation Details window shows the operation description, start and finish times, and progress history. The window is resizable. To copy the Status lines to the clipboard, select the line, right-click and choose Copy.
Print views - To print a view, select File > Print. The Choose Window is displayed. Select the window that you would like to print, e.g., Operation Status or License & Contract Repository. Optionally, you can adjust the print setup settings, or preview the output.
See logs -
$SUROOT\log\su.elg.The latest management version can be applied to a single Check Point Security Gateway, or to multiple Check Point Security Gateways simultaneously. Use the Upgrade all Packages operation to bring packages up to the most current management version.
When you perform Upgrade all Packages all products are upgraded to the latest Security Management Server version. This process upgrades both the software packages and its related HFA (that is, the most up to date HFA is installed). Once the process is over, the software packages and the latest HFA will exist in the Package Repository.
To upgrade Check Point packages to versions earlier than the latest available version, they must be upgraded one-by-one. Use the Distribute operation to upgrade packages to management versions other than the most current, or to apply specific HFAs.
In addition, SmartUpdate recognizes Gateways that do not have the latest HFA. When you right-click an HFA in the Package Repository and select Distribute for that specific HFA, you will receive a recommendation to install a new HFA on the Gateways that do not have it.
Secure Internal Communication (SIC) must be enabled between the Security Management Server and remote Check Point Security Gateways.
In order to know exactly what OS, vendor and management version is on each remote gateway, you can retrieve that data directly from the gateway.
To distribute (that is, install) or upgrade a package, you must first add it to the Package Repository. You can add packages to the Package Repository from the following three locations:
Ctrl and Shift keys to select multiple files. You can also use the Filter to show just the packages you need.Use this procedure for adding OPSEC packages and Hotfixes to the Package Repository.
.tgz file and click Open to add the packages to the Package Repository.A window opens, showing the available packages on the DVD.
Verify that the distribution (that is, installation) or upgrade is viable based upon the Check Point Security Gateway data retrieved. The verification process checks that:
To manually verify a distribution, select Packages > Pre-Install Verifier….
When you are ready to upgrade or distribute packages from the Package Repository, it is recommended to transfer the package files to the devices to be upgraded. Placing the file on the remote device shortens the overall installation time, frees Security Management Server for other operations, and reduces the chance of a communications error during the distribute/upgrade process. Once the package file is located on the remote device, you can activate the distribute/upgrade whenever it is convenient.
Transfer the package file(s) to the directory $SUROOT/tmp on the remote device. If this directory does not exist, do one of the following:
SYSTEMDRIVE\temp (SYSTEMDRIVE is usually C:\)/opt/.You can upgrade all packages on one remote gateway, or you can distribute specific packages one-by-one for all Gateways.
Ctrl and Shift keys to select multiple devices.Note - The Reboot if required option (selected by default) is required, to activate the newly distributed package.
The installation proceeds only if the upgrade packages for the selected packages are available in the Package Repository.
Use this procedure to select the specific package that you want to apply to a single package. The distribute function allows you to:
To update a single package on a remote gateway:
Use the Ctrl and Shift keys to select multiple packages, and click distribute.
The installation proceeds only if the upgrade packages selected are available in the Package Repository.
The UTM-1 Edge gateway firmware represents the software that is running on the appliance. The UTM-1 Edge gateway's firmware can be viewed and upgraded using SmartUpdate. This is a centralized management tool that is used to upgrade all Gateways in the system by downloading new versions from the download center. When installing new firmware, the firmware is prepared at the Security Management Server, downloaded and subsequently installed when the UTM-1 Edge gateway fetches for updates. Since the UTM-1 Edge gateway fetches at periodic intervals, you will notice the upgraded version on the gateway only after the periodic interval has passed.
If you do not want to wait for the fetch to occur you can download the updates with the Push Packages Now (UTM-1 Edge only) option in the Packages menu. With this option it is possible to create a connection with UTM-1 Edge in order to access new (that is, the latest) software package(s). The distribution is immediate and avoids the need to wait for the fetch to get the package.
You can stop a Distributed installation or upgrade while in progress.
To stop a Distributed installation or upgrade:
From the SmartUpdate Menu, select Operation > Stop Operation.
To uninstall a package:
From the SmartUpdate Menu, select Packages > Uninstall.
Note - Uninstallation restores the gateway to the last management version distributed.
After you distribute an upgrade or uninstall, reboot the gateway.
To restart the gateway:
If an upgrade fails on SecurePlatform, SmartUpdate restores the previously distributed version.
If an upgrade or distribution operation fails on a SecurePlatform device, the device will reboot itself and automatically revert to the last version distributed.
Before performing an upgrade, you can use the command line to create a Snapshot image of the SecurePlatform OS, or of the packages distributed. If the upgrade or distribution operation fails, you can use the command line to revert the disk to the saved image.
cprinstall snapshot <object name> <filename>
cprinstall show <object name>
cprinstall revert <object name> <filename>
Note - Snapshot files are stored at /var/CPsnapshot on the gateway.
To clear the Package Repository of extraneous or outdated packages, select a package, or Ctrl-select multiple packages and select Packages > Delete Package. This operation cannot be undone.
With SmartUpdate, you can manage all licenses for Check Point packages throughout the organization from the Security Management Server. SmartUpdate provides a global view of all available and installed licenses, allowing you to perform such operations as adding new licenses, attaching licenses and upgrading licenses to Check Point Security Gateways, and deleting expired licenses. Check Point licenses come in two forms, Central and Local.
When you add a license to the system using SmartUpdate, it is stored in the License & Contract Repository. Once there, it must be installed to the gateway and registered with the Security Management Server. Installing and registering a license is accomplished through an operation known as attaching a license. Central licenses require an administrator to designate a gateway for attachment, while Local licenses are automatically attached to their respective Check Point Security Gateways.
Licenses received from the User Center should first be added to the License & Contract Repository. Adding a local license to the License & Contract Repository also attaches it to the gateway.
Licenses can be conveniently imported to the License & Contract Repository via a file and they can be added manually by pasting or typing the license details.
Licenses are attached to a gateway via SmartUpdate. Attaching a license to a gateway involves installing the license on the remote gateway, and associating the license with the specific gateway in the License & Contract Repository.
A Central License is a license attached to the Security Management Server IP address, rather than the gateway IP address. The benefits of a Central License are:
The Certificate Key is a string of 12 alphanumeric characters. The number is unique to each package. For an evaluation license your certificate key can be found inside the mini pack. For a permanent license you should receive your certificate key from your reseller.
A command line for managing local licenses and local license operations. For additional information, refer to the R77 Command Line Interface Reference Guide.
Detaching a license from a gateway involves uninstalling the license from the remote gateway and making the license in the License & Contract Repository available to any gateway.
Licenses can be in one of the following states:
The license state depends on whether the license is associated with the gateway in the License & Contract Repository, and whether the license is installed on the remote gateway. The license state definitions are as follows:
Locally installed licenses can be placed in the License & Contract Repository, in order to update the repository with all licenses across the installation. The Get operation is a two-way process that places all locally installed licenses in the License & Contract Repository and removes all locally deleted licenses from the License & Contract Repository.
Licenses expire on a particular date, or never. After a license has expired, the functionality of the Check Point package may be impaired.
A Local License is tied to the IP address of the specific gateway and can only be used with a gateway or a Security Management Server with the same address.
Licenses can be conveniently added to a gateway or a Security Management Server via a file, rather than by typing long text strings. Multi-license files contain more than one license, and can be downloaded from the Check Point User Center.
Multi-license files are supported by the cplic put, and cplic add command-line commands.
A character string that identifies the features of a package.
One of the many SmartUpdate features is to upgrade licenses that reside in the License & Contract Repository. SmartUpdate will take all licenses in the License & Contract Repository, and will attempt to upgrade them with the use of the Upgrade tool.
When a Central license is placed in the License & Contract Repository, SmartUpdate allows you to attach it to Check Point packages. Attaching a license installs it to the remote gateway and registers it with the Security Management Server.
New licenses need to be attached when:
Attaching a license is a three step process.
The following explains the process in detail.
To know exactly what type of license is on each remote gateway, you can retrieve that data directly from the gateway.
To install a license, you must first add it to the License & Contract Repository. You can add licenses to the License & Contract Repository in the following ways:
A license file can contain multiple licenses. Unattached Central licenses appear in the License & Contract Repository, and Local licenses are automatically attached to their Check Point Security Gateway. All licenses are assigned a default name in the format SKU@ time date, which you can modify at a later time.
You may add licenses that you have received from the Licensing Center by email. The email contains the license installation instructions.
cplic putlic... and ends with the last SKU/Feature. cplic putlic 1.1.1.1 06Dec2002 dw59Ufa2-eLLQ9NB-gPuyHzvQ-WKreSo4Zx CPSUITE-EVAL-3DES-NGX CK-1234567890After licenses have been added to the License & Contract Repository, select one or more licenses to attach to a Check Point Security Gateway.
If the attach operation fails, the Local licenses are deleted from the Repository.
Detaching a license involves deleting a single Central license from a remote Check Point Security Gateway and marking it as unattached in the License & Contract Repository. This license is then available to be used by any Check Point Security Gateway.
To detach a license, select Network Objects License & Contract tab > Detach and select the licenses to be detached from the displayed window.
Licenses that are not attached to any Check Point Security Gateway and are no longer needed can be deleted from the License & Contract Repository.
To delete a license:
The overall view of the License & Contract Repository displays general information on each license such as the name of the license and the IP address of the machine to which it is attached. You can view other properties as well, such as expiration date, SKU, license type, certificate key and signature key.
To view license properties, double-click on the license in the Licenses tab.
After a license has expired, the functionality of the Check Point package will be impaired; therefore, it is advisable to be aware of the pending expiration dates of all licenses.
To check for expired licenses, select Licenses > Show Expired Licenses.
To check for licenses nearing their dates of expiration:
x days property.To delete expired licenses from the License Expiration window, select the detached license(s) and click Delete.
Licenses can be exported to a file. The file can later be imported to the License & Contract Repository. This can be useful for administrative or support purposes.
To export a license to a file:
All selected licenses are exported. If the file already exists, the new licenses are added to the file.
To manage licenses using SmartUpdate, select the SmartUpdate view in the SmartDomain Manager Selection Bar. If you loaded SmartUpdate, you can also right-click a Multi-Domain Server object and select Applications > SmartUpdate from the Options menu. Licenses for components and blades are stored in a central repository.
To view repository contents:
To add new licenses to the repository:
You can now see the license in the repository.
To attach a license to a component:
You can manage other license tasks with SmartUpdate. See the R77 Security Management Administration Guide.
A gateway or gateway cluster requires a Web Security license if it enforces one or more of the following protections:
Before upgrading a gateway or Security Management Server, you need to have a valid support contract that includes software upgrade and major releases registered to your Check Point User Center account. The contract file is stored on Security Management Server and downloaded to Check Point Security Gateways during the upgrade process. By verifying your status with the User Center, the contract file enables you to easily remain compliant with current Check Point licensing standards.
For more on service contracts, see the Service Contract Files Web page.
CPInfo is a support tool that gathers into one text file a wide range of data concerning the Check Point packages in your system. When speaking with a Check Point Technical Support Engineer, you may be asked to run CPInfo and transmit the data to the Support Center. Download the tool from the Support Center.
To launch CPInfo, select Tools > Generate CPInfo.
SmartUpdate lets you automatically generate and send CPinfo to Check Point Technical support.
To automatically generate and send CPinfo:
The Upload CPinfo from... window opens.
Click Add to enter the full path to the remote file on the remote gateway or Security Management Server.
The Operation Status window opens.
All management operations that are performed via the SmartUpdate GUI can also be executed via the command line. There are three main commands:
cppkg to work with the Packages Repository.cprinstall to perform remote installations of packages.cplic for license management.For details on how to use these commands, see the R77 Command Line Interface Reference Guide.