

In This Section: |
This chapter includes configuration procedures and examples for network management.
Gaia supports these network interface types:
|
Note - When you add, delete or make changes to interface IP addresses, it is possible that when you use the Get Topology option in SmartDashboard, the incorrect topology is shown. If this occurs, run |
You can see the status of physical and logical interfaces by using the WebUI or the CLI.
To see interface status using the WebUI:
Link Status |
Description |
|---|---|
Grey (Down) |
The physical interface is disabled (Down). |
Red (no Link) |
The physical interface is enabled (up), but Gaia cannot find a network connection. |
Green (Up) |
The physical interface is enabled (up) and connected to the network. |
To see interface status using the CLI, run show interfaces all
This section has configuration procedures and examples for defining different types of interfaces on a Gaia platform.
Gaia automatically identifies physical interfaces (NICs) installed on the computer. You cannot add or delete a physical interface using the WebUI or the CLI. You cannot add, change or remove physical interface cards while the Gaia computer is running.
To add or remove an interface card:
Gaia automatically identifies the new or changed physical interfaces and assigns an interface name. The physical interfaces show in the list in the WebUI.
This section includes procedures for changing physical interface parameters using the WebUI.
To configure a physical interface:
Caution: Do not manually change the MAC address unless you are sure that it is incorrect or has changed. An incorrect MAC address can lead to a communication failure.
Description |
Configure physical interfaces |
||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
Syntax |
set interface <IF> ipv4-address <IP> subnet-mask <Mask> ipv6-address <IP> mask-length <Mask> ipv6-autoconfig <on | off> comments <Text> mac-addr <MAC> mtu <MTU setting> state <on | off> link-speed <Speed_Duplex> auto-negotiation <on | off> show interfaces all |
||||||||||||||||||||||||||
Parameters |
|
|
|||||||||||||||||||||||||
Parameter Values |
|
|
|||||||||||||||||||||||||
Examples |
set interface eth2 ipv4-address 40.40.40.1 subnet-mask 255.255.255.0 set interface eth2 mtu 1500 set interface eth2 link-speed
|
||||||||||||||||||||||||||
Comments |
There are some command options and parameters that you cannot do using the WebUI. |
||||||||||||||||||||||||||
|
Important - After you add, configure, or delete features, run the |
||||||||||||||||||||||||||
Interface aliases let you assign more than one IPv4 address to physical or virtual interfaces (bonds, bridges, VLANS and loopbacks). This section shows you how to configure an alias using the WebUI and the CLI.
To configure an interface alias using the WebUI:
The new alias interface name is automatically created by adding a sequence number to the interface name. For example, the name of first alias added to eth1 is eth1:0. She second alias added is eth1:1, and so on.
To delete an interface alias:
Description |
Configure an alias to a physical interface. |
|||||||||||
Syntax |
add interface <IF> alias <IP>/<Mask> delete interface <IF> alias <Alias IF> |
|||||||||||
Parameter Values |
|
|
||||||||||
Examples |
add interface eth1 alias 10.10.99.1/24 delete interface eth1 alias eth1:2 |
|||||||||||
Comments |
A new alias interface name is automatically created by adding a sequence number to the original interface name. For example, the name of first alias added to eth1 is eth1:0. She second alias added is eth1:1, and so on. |
|||||||||||
|
Important - After you add, configure, or delete features, run the |
|||||||||||
You can configure virtual LAN (VLAN) interfaces on Ethernet interfaces. VLAN interfaces let you configure subnets with a secure private link to gateways and management servers using your existing topology. With VLAN interfaces, you can multiplex Ethernet traffic into many channels using one cable.
This section shows you how to configure VLAN interfaces using the WebUI and the CLI.
To configure a VLAN interface using the WebUI:
|
Note - You cannot change the VLAN ID or physical interface for an existing VLAN interface. To change these parameters, delete the VLAN interface and then create a New VLAN interface. |
This section is a reference for the VLAN interface commands.
Description |
Use these commands to configure bridge interfaces. |
||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
Syntax |
add interface <IF> vlan <VLAN ID> set interface <IF> <VLAN ID> ipv4-address <IP> mask-length <Length>|subnet-mask<Mask> delete interface <IF> vlan <VLAN ID> |
||||||||||||||||
Parameters |
|
|
|||||||||||||||
Values |
|||||||||||||||||
Example |
add interface vlan eth1 set interface eth1.99 ipv4-address 99.99.99.1 subnet-mask 255.255.255.0 set interface eth1.99 ipv6-address 209:99:1 mask-length 64 delete interface eth1 vlan 99 |
||||||||||||||||
|
Important - After you add, configure, or delete features, run the |
||||||||||||||||
To add a new VLAN interface:
Run add interface <IF Name> vlan <VLAN ID>
<IF Name><VLAN ID>Example:
add interface eth1 vlan 10
To add IP addresses to a VLAN interface:
Run:set interface <IF Name>.<VLAN ID> ipv4-address <IPv4 Address> [ipv6-address <IPv6 Address>]
<IF Name><VLAN ID><IPv4 Address><IPv6-address>Examples:
set interface eth1.99 ipv4-address 99.99.99.1 subnet-mask 255.255.255.0
set interface eth1.99 ipv6-address 209:99:1 mask-length 64
To delete a VLAN Interface:
Run:delete interface <IF Name> vlan <VLAN ID>
Example:delete interface eth1 vlan 10
Check Point security devices support Link Aggregation, a technology that joins multiple physical interfaces into one virtual interface, known as a bond interface. The bond interface gives fault tolerance and increases throughput by sharing the load among many interfaces. Check Point devices support the IEEE 802.3ad Link Aggregation Control Protocol (LCAP) for dynamic link aggregation.
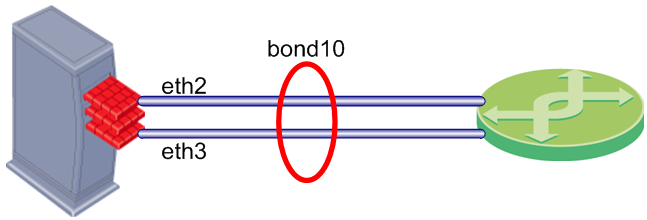
A bond interface (also known as a bonding group or bond) is identified by its Bond ID (for example: bond1) and is assigned an IP address. The physical interfaces included in the bond are called slaves and do not have IP addresses.
You can define bond interfaces using one of these functional strategies:
To configure a bond interface using the WebUI:
In the CLI, bond interfaces are known as bonding groups. Make sure the interfaces of the bond do not already have IP addresses.
Important: After you run a CLI command to add, configure, or delete an object, run the save config
To create a bond interface with the CLI:
This section is a quick reference for Link Aggregation commands. The next sections include procedures for different tasks, including explanations of the configuration options.
Use these commands to configure link aggregation.
Syntax:
{add | delete} bonding group <bondID> interface <IFName>
set bonding [group <bondID>] [primary <IFName>] [mii-interval <ms>] [up-delay <ms> | down-delay <ms>] [mode {round-robin | active-backup | xor [xmit-hash-policy {layer2 | layer3+4}]| 8023AD [lacp-rate {slow | fast}]}]
{<bondID> |show bonding group}groups
Parameters
Parameter |
Description |
|---|---|
bondID |
ID of bond, an integer between 1 and 1024 |
IFName |
Name of interface to add to the bond |
|
Name of primary interface in the bond |
|
Frequency that the system polls the Media Independent Interface (MII) to get status |
|
Waiting time to confirm the interface status before taking the specified action (0-5000 ms, default = 200 ms) |
|
|
|
Link Aggregation Control Protocol packet transmission rate:
|
|
Algorithm for interface selected by TCP/IP layer |
Example
set bonding group 666 20 eth2
show bonding groups
Output
Bonding Interface: 20
Bond Configuration
xmit_hash_policy Not configured
down-delay 200
primary Not configured
mode round-robin
up-delay 200
mii-interval 100
lacp_rate Not configured
Bond Interfaces
eth2
eth3
To add a new bond interface:
add bonding group >
Example:
add bonding group 777
To delete a bond interface:
delete bonding group <>A bond interface typically contains between two and eight slave interfaces. This section shows how to add and remove a slave interface. The slave interface must not have IP addresses assigned to it.
To add a slave interface to a bond:
add bonding group <bondID> interface <IFName>
Example:
add bonding group 777 interface eth4
|
Note - Do not change the bond state manually. This is done automatically by the bonding driver. |
To delete a slave interface from a bond:
delete bonding group <bondID> interface <IFName>
Example:
delete bonding group 777 interface eth4
|
Note - You must delete all non-primary slave interfaces before you remove the primary slave interface. |
Define how interfaces are activated in a bond:
round-robinactive-backupxor You can set the LACP packet transmission rate for xor mode or 8023AD mode. After you set one of these Load Sharing modes, enter this option: lacp-rate slowfast
where slow fast
8023AD xmit-hash-policylayer2 layer3+4To define the bond operating mode:
set bonding group <> mode <> []
Example:
set bonding group 777 mode xor xmit-hash-policy layer3+4
With the Active-Backup operating mode, the system automatically fails over to the primary slave interface, if available. If the primary interface is not available, the system fails over to a different slave interface. By default, the first slave interface that you define is the primary interface. You must define the slave interfaces and set the operating mode as Active-Backup before doing this procedure.
|
Note - You must delete all non-primary slave interfaces before you remove the primary slave interface. |
To define the primary slave interface:
set bonding group <bondID> mode active-backup primary <IFName>
Example
add bonding group 777 interface eth4
set bonding group 777 mode active-backup primary eth4
This sets the frequency of requests sent to the Media Independent Interface (MII) to confirm that a slave interface is up. The valid range is 1-5000 ms. The default is 100 ms.
To configure the monitoring interval:
set bonding group > mii-interval >
Example:
set bonding group 777 mii-interval 500
To disable monitoring:
set bonding group <> mii-interval 0
This parameter defines the waiting time, in milliseconds, to confirm the slave interface status before taking the specified action. Valid values are 0 to 5000 ms. The default is 200 ms.
To configure the UP and Down delay times:
set bonding group <bondID> down-delay <ms>
set bonding group <bondID> up-delay <ms>
Example:
set bonding group 777 down-delay 500
To make sure that a Link Aggregation is working for a bond interface, run this command in expert mode:
cat /proc/net/bonding/<bondID>
Example with output:
cat /proc/net/bonding/bond666 Ethernet Channel Bonding Driver: v3.2.4 (January 28, 2008) Bonding Mode: fault-tolerance (active-backup) Primary Slave: None Currently Active Slave: eth2 MII Status: up MII Polling Interval (ms): 100 Up Delay (ms): 100 Down Delay (ms): 200 Slave Interface: eth2 MII Status: up Link Failure Count: 2 Permanent HW addr: 00:50:56:94:11:de |
Check Point security devices support bridge interfaces that implement native, Layer-2 bridging. Configuration of an interface as a bridge lets network administrators deploy security devices in a topology without reconfiguration of the IP routing scheme. This is an important advantage for large-scale, complex environments. Gaia does not support Spanning Tree Protocol (STP) bridges.
You configure Ethernet interfaces (including aggregated interfaces) on your Check Point security device to work like ports on a physical bridge.
Note - You cannot configure as a bridge interface an interface that you configure as a bond slave.
The bridge interfaces send traffic with Layer-2 addressing. On the same device, you can configure some interfaces as bridge interfaces, while other interfaces work as layer-3 interfaces. Traffic between bridge interfaces is inspected at Layer-2. Traffic between two Layer-3 interfaces, or between a bridge interface and a Layer-3 interface is inspected at Layer-3.
This section shows you how to configure bridge interfaces using the WebUI and the CLI.
To configure a bridge interface in the WebUI:
The Add (or Edit) Bridge window opens.
Or click Obtain IP Address automatically.
This is a quick reference for bridge interface commands.
Description - Use these commands to configure bridge interfaces.
Syntax
add bridging group <Group ID> [interface <interface>]
delete bridging group <Group ID> interface <interface>
show bridging group <Group ID>
Parameters
Parameter |
Description |
|---|---|
<Group ID> |
ID of bridging group |
<interface> |
Interface name |
Example - add bridging group 56 interface eth1
|
Important - After you add, configure, or delete features, run the |
Bridge interfaces are known as Bridging Groups in Gaia clish commands. You can assign an IPv4 or IPv6 address to a bridge interface.
To see the interfaces of an existing bridge:
show bridging group
Where Group ID is the unique identifier of the bridge, an integer between 0 and 1024
To create a new bridging group:
add bridging group
To add an interface to the bridging group:
add bridging group interface
Run this command one time for each physical interface.
To remove an interface from the bridging group:
delete bridging group interface
Run this command one time for each physical interface.
To delete a bridging group:
delete bridging group
To add or change a bridge interface IP address:
set interface ipv4-address subnet-mask set interface ipv6-address mask-length Examples:
add bridging group 56 interface eth1set interface br1 ipv6-address 3000:40::1 mask-length 64
|
Important - After you add, configure, or delete features, run the |
You can define a virtual loopback interface by assigning an IPv4 or IPv6 address to the lo
To configure a loopback interface using the WebUI:
The new loopback interface name is automatically created with the addition of a sequence number to the string 'loop'. For example, the name of first loopback interface is loop00. The second loopback interface is loop01, and so on.
To delete an interface alias:
Description |
Configure loopback interfaces |
|||||||||||
Syntax |
add interface lo loopback <IP>/<Mask> delete interface lo loopback <IF> |
|||||||||||
Parameters and Values |
|
|
||||||||||
Examples |
add interface lo loopback 10.10.99.1/24 add interface lo loopback 2010:10:99::1/64 delete interface lo loopback loop01 |
|||||||||||
Comments |
When you create a new loopback interface, Gaia automatically assigns a name in the format Important: After using CLI commands to add, configure or delete features, you must run the save config command. This makes sure that the new configuration settings remain after reboot. |
Virtual Tunnel Interface. A virtual interface that is a member of an existing, Route-Based, VPN tunnel. Each peer Security Gateway has one VTI that connects to the tunnel.
The VPN tunnel and its properties are defined by the VPN community that contains the two gateways. You must define the VPN community and its member Security Gateways before you can create a VTI. To learn more about Route Based VPN, see Route Based VPN in the R77 VPN Administration Guide.
The procedure for configuring a VTI includes these steps:
You must define the VPN Community and add the member Security Gateways to it before you configure a VPN Tunnel Interface. This section includes the basic procedure for defining a Site to Site VPN Community. To learn more about VPN communities and their definition procedures, see the R77 VPN Administration Guide.
To define a VPN Community for Site to Site VPN:
This option automatically adds a rule to encrypt all traffic between gateways in a VPN community.
For star communities, use the Center Gateways and Satellite Gateways tabs to do this.
When Domain Based VPN and Route Based VPN are defined for a Security Gateway, Domain Based VPN is active by default. You must do two short procedures to make sure that Route Based VPN is always active.
The first procedure defines an empty encryption domain group for your peer gateways. You do this step one time for each Security Management Server. The second step is to make Route Based VPN the default option for all Security Gateways.
To Define an empty group:
To make Route Based VPN the default choice:
Do these steps for each Security Gateway.
You can configure the VPN Tunnel Interfaces using Gaia WebUI or CLI.
This section shows you how to configure a VPN Tunnel interface using the WebUI.
To configure a VPN Tunnel Interface:
vpntThis section shows the CLI commands used to add or delete VPN Tunnel Interfaces.
Description |
Add or delete a VPN Tunnel Interface (VTI) |
|||||||||||||
Syntax |
|
|||||||||||||
Parameters |
|
|
||||||||||||
Parameter |
|
|
||||||||||||
Example |
|
|
Important - After you add, configure, or delete features, run the |
To add a numbered VPN Tunnel Interface:
Run:
add vpn tunnel <Tunnel ID> type numbered local <Local IP> remote <Remote IP>
peer <Peer ID>
<Tunnel ID>vpnttype numberedlocal <Local IP>remote <Remote IP>peer <Peer ID>To add an unnumbered VPN Tunnel Interface:
Run:
add vpn tunnel <Tunnel ID> type unnumbered local peer <Peer ID>
<Tunnel ID>vpnttype unnumberedpeer <Peer ID>dev <IF>To Delete a VPN Tunnel Interface
Run:
delete vpn tunnel <Tunnel ID>
<Tunnel ID>vpntTo make sure that your security rules work correctly with Route Based VPN traffic, you must add directional matching conditions and allow OSPF traffic. This section includes procedures for configuring security rules to do this.
This section contains the procedure for defining directional matching rules. Directional matching is necessary for Route Based VPN when a VPN community is included in the VPN column in the rule. This is because without bi-directional matching, the rule only applies to connections between a community and an encryption domain (Domain Based Routing).
Name |
Source |
Destination |
VPN |
Service |
Action |
|---|---|---|---|---|---|
VPN Tunnel |
Any |
Any |
MyIntranet |
Any |
accept |
The directional rule must contain these directional matching conditions:
MyIntranet is the name of a VPN Community. Internal_Clear refers to all traffic from IP addresses to and from the specified VPN community.
Name |
Source |
Destination |
VPN |
Service |
Action |
|---|---|---|---|---|---|
VPN Tunnel |
Any |
Any |
MyIntranet > MyIntranet |
Any |
accept |
|
Note - It is not necessary to define bidirectional matching rules if the VPN column contains the Any value. |
To enable VPN directional matching:
To define a VPN directional matching rule:
Do this step for each set of matching conditions.
One advantage of Route Based VPN is the fact that you can use dynamic routing protocols to distribute routing information between Security Gateways. The OSPF (Open Shortest Path First) protocol is commonly used with VTIs. This section shows you how to allow OSPF traffic in a VPN community.
To learn about configuring OSPF, see the R77 Gaia Advanced Routing Administration Guide.
To Allow OSPF traffic for a VPN Community:
Name |
Source |
Destination |
VPN |
Service |
Action |
|---|---|---|---|---|---|
Allow OSPF |
Any |
Any |
MyIntranet |
ospf |
accept |
You must save your configuration to the database and install policies to the Security Gateways before the VPN can be fully functional.
To complete the VTI configuration:
This section summarizes the CLI interface
Description |
Add, delete and configure interface properties. |
|||||||||||||||||||||||||||||||||||||
Syntax |
|
|||||||||||||||||||||||||||||||||||||
Parameters |
|
|
||||||||||||||||||||||||||||||||||||
Parameter Values |
|
|
||||||||||||||||||||||||||||||||||||
Examples |
See the interface configuration section. |
|||||||||||||||||||||||||||||||||||||
Comments |
There are some command options and parameters that you cannot do using the WebUI. |
The Address Resolution Protocol (ARP) allows a host to find the physical address of a target host on the same physical network using only the target’s IP address. ARP is a low-level protocol that hides the underlying network physical addressing and permits assignment of an arbitrary IP address to every machine. ARP is considered part of the physical network system and not as part of the Internet protocols.
To show dynamic ARP entries
To show static ARP entries
To change Static and dynamic ARP parameters
Note – Make sure to configure a value large enough to accommodate at least 100 dynamic entries, in addition to the maximum number of static entries.
To add a static ARP entry
To delete a Static ARP entry
To flush all dynamic ARP entries
Description |
Commands to configure the Address Resolution Protocol (ARP) |
|||||||||||||
Syntax |
To add a static arp entry add arp static ipv4-address VALUE macaddress VALUE To delete static and dynamic arp entries delete arp dynamic all delete arp static ipv4-address VALUE To set arp parameters set arp table validity-timeout VALUE set arp table cache-size VALUE To show arp parameters show arp dynamic all show arp static all show arp table validity-timeout show arp table cache-size |
|||||||||||||
Parameters |
|
|
|
Important - After you add, configure, or delete features, run the |
You can configure the Gaia device to be a Dynamic Host Configuration Protocol (DHCP) server. The DHCP server give IP addresses and other network parameters to network hosts. DHCP makes it unnecessary to configure each host manually, and therefore reduces configuration errors.
You configure DHCP server subnets on the Gaia device interfaces. A DHCP subnet allocates these network parameters to hosts behind the Gaia interface:
This is the general workflow for allocating DHCP parameters to hosts (for the details, see the next section):
To allocate DHCP parameters to hosts
The Add DHCP window opens. You now define a DHCP subnet on an Ethernet interface of the Gaia device. Hosts behind the Gaia interface get IPv4 addresses from address pools in the subnet.
example.comThe DHCP server on Gaia is now configured and enabled.
You can now configure your network hosts to get their network parameters from the DHCP server on Gaia.
Description |
DHCP Server commands allow you to configure the Gaia device as DHCP server for network hosts. |
|||||||||||||||||||||||||||||||||||||
Syntax |
To create DHCP Server subnets: add dhcp server subnet VALUE netmask VALUE include-ip-pool start VALUE end VALUE exclude-ip-pool start VALUE end VALUE
To change DHCP Server subnet configurations: set dhcp server subnet VALUE enable disable include-ip-pool VALUE enable include-ip-pool VALUE disable exclude-ip-pool VALUE enable exclude-ip-pool VALUE disable default-lease VALUE max-lease VALUE default-gateway VALUE domain VALUE dns VALUE
To delete DHCP Server subnets: delete dhcp server subnet VALUE exclude-ip-pool VALUE include-ip-pool VALUE
To enable or disable the DHCP Server process: set dhcp server disable enable
To view DHCP Server configurations show dhcp server all status subnet VALUE ip-pools subnets |
|||||||||||||||||||||||||||||||||||||
Parameters |
|
|
||||||||||||||||||||||||||||||||||||
Example |
|
|||||||||||||||||||||||||||||||||||||
Output |
|
|
You set the host name (system name) during initial configuration. You can change the name.
To show the host name
The host name is in the header of the WebUI.
To change the host name
example.comDescription |
Use this group of commands to configure the host name of your platform. |
Syntax |
set hostname VALUE show hostname |
You should add host addresses for systems that will communicate frequently with the system. You can:
To add a static host entry
To edit a static host entry
To delete a static host entry
Description |
Add, edit, delete and show the name and addresses for hosts that will communicate frequently with the system |
|||||||||
Syntax |
To add a host name and address: add host name VALUE ipv4-address VALUE add host name VALUE ipv6-address VALUE To edit the name and IPv4 or IPv6 address of a host: set host name VALUE ipv4-address VALUE set host name VALUE ipv6-address VALUE To delete a host name and address: delete host name VALUE ipv4 delete host name VALUE ipv6 To show an IPv4 or IPv6 host address: show host name VALUE ipv4 show host name VALUE ipv6 To show all IPv4 or IPv6 hosts: show host names ipv4 show host names ipv6 |
|||||||||
Parameters |
|
|
Gaia uses the Domain Name Service (DNS) to translate host names into IP addresses. To enable DNS lookups, you must enter the primary DNS server for your system. You can also enter secondary and tertiary DNS servers. When the system resolves host names, it consults the primary name server. If a failure or time-out occurs, the system consults the secondary name server, and if necessary, the tertiary.
You can also define a DNS Suffix, which is a search for host-name lookup.
To configure the DNS Server for the Gaia computer:
example.comexample.comfooping foofoo.example.comDescription |
Configure, show and delete the DNS servers and the DNS suffix for the Gaia computer. |
|||||||||
Syntax |
To configure the DNS servers and the DNS suffix for the Gaia computer: set dns primary VALUE set dns secondary VALUE set dns tertiary VALUE set dns suffix VALUE To show the DNS servers and the DNS suffix for the Gaia computer: show dns primary show dns secondary show dns tertiary show dns suffix To delete the DNS servers and the DNS suffix for the Gaia computer: delete dns primary delete dns secondary delete dns tertiary delete dns suffix |
|||||||||
Parameters |
|
|
A static route defines the destination and one or more paths (next hops) to get to that destination. You define static routes manually using the WebUI or the set static-route
Static routes let you add paths to destinations that are unknown by dynamic routing protocols. You can define multiple paths (next hops) to a destination and define priorities for selecting a path. Static routes are also useful for defining the default route.
Static route definitions include these parameters:
You can configure static routes one at a time or use the Batch Mode to configure many routes simultaneously.
To configure one static route at a time:
This action makes sure that the connection is alive. If no answer is returned, the route is deleted from the routing table.
This a route priority value to use when there are many routes to a destination that use different routing protocols. The route with the lowest rank value is selected. Default = 0.
You can use the batch mode to configure multiple static routes in one step.
|
Note - You cannot configure a network (logical) interface using this option. |
To add many static routes at once:
<Destination IP>/<Mask length> <Next Hop IP> [<Comment>]
default - Use this as an alternative to the default route IP address
Destination IP - Destination IP address using dotted decimal notation
Mask length - Net mask using slash (/xx) notation
Next Hop IP - Next hop gateway IP address using dotted decimal notation
Comment - Optional free text comment
Examples:
default 192.0.2.100 192.0.2.1 "Default Route"
192.0.2.200 192.0.2.18
The newly configured more static routes show in the list of Static Routes in the Static Routes page.
|
Note - The text box shows entries that contain errors with messages at the top of the page. |
You only use the setstatic-route
Description |
Add, change or delete an IPv4 static route. |
|||||||||||||||||||||||
Syntax |
|
|||||||||||||||||||||||
Parameter |
|
|
||||||||||||||||||||||
Values |
|
|
||||||||||||||||||||||
Examples |
set static-route set static-route set static-route
set static-route
set static-route
|
|||||||||||||||||||||||
Comments |
There are no show route static |
This section includes some basic procedures for managing static routes using the CLI.
To show static routes, run
show route static
Codes: C - Connected, S - Static, R - RIP, B - BGP, O - OSPF IntraArea (IA - InterArea, E - External, N - NSSA) A - Aggregate, K - Kernel Remnant, H - Hidden, P - Suppressed S 0.0.0.0/0 via 192.168.3.1, eth0, cost 0, age 164115 S
S
|
To add a static route, run:
set static-route <Destination> nexthop gateway <GW IP> on
set static-route <Destination> nexthop gateway <GW IF> on
Destination GW IPGW IF
Example:
set static-route 192.0.2.100 nexthop gateway address 192.0.2.10 onset static-route 192.0.2.100 nexthop gateway logical 192.0.2.10 on
To add a static route with paths and priorities, run:
set static-route <Destination> nexthop gateway <GW ID> priority <P Value>
DestinationGW IPP Value
Run this command for each path, assigning a priority value to each. You can define two or more paths using the same priority to specify a backup path with equal priority.
Examples:
set static-route 192.0.2.100 nexthop gateway address 192.0.2.10 onpriority 1
set static-route 192.0.2.100 nexthop gateway address 192.0.2.10 onpriority 1
set static-route 192.0.2.0/24 nexthop gateway logical eth4 on priority 2
set static-route 192.0.2.0/24 nexthop gateway logical eth5 on priority 3
To add a static route where packets are dropped, run:
set static-route <Destination> nexthop reject
set static-route <Destination> nexthop blackhole
DestinationReject Blackhole
Examples:
set static-route 192.0.2.0/24 nexthop reject
or
set static-route 192.0.2.0/24 nexthop blackhole
To delete a route and all related paths, run:
set static-route <Destination> off
Destination
Example:
set static-route 192.0.2.0/24 off
To delete a path only, run:
set static-route <Destination> nexthop gateway <GW ID> off
Destination GW ID
Example:
set static-route 192.0.2.10 nexthop gateway address 192.0.2.100 off
You can configure IPv6 static routes one at a time.
To configure one static route at a time: