Creating VPN Policies
Overview
The IPsec VPN Software Blade lets the Firewall encrypt and decrypt traffic to and from external networks and clients. Use SmartDashboard to easily configure VPN connections between Security Gateways and remote devices. You can configure Star and Mesh topologies for large-scale VPN networks that include third-party gateways. The VPN tunnel guarantees:
- Authenticity - Uses standard authentication methods
- Privacy - All VPN data is encrypted
- Integrity - Uses industry-standard integrity assurance methods
IKE and IPsec
The Check Point VPN solution uses these secure VPN protocols to manage encryption keys, and send encrypted packets. IKE (Internet Key Exchange) is a standard key management protocol that is used to create the VPN tunnels. IPsec is protocol that supports secure IP communications that are authenticated and encrypted on private or public networks.
For more about using IPsec VPN, see the R77 VPN Administration Guide.
Site to Site VPN
The basis of Site to Site VPN is the encrypted VPN tunnel. Two Security Gateways negotiate a link and create a VPN tunnel and each tunnel can contain more than one VPN connection. One Security Gateway can maintain more than one VPN tunnel at the same time.
Sample Site to Site VPN Deployment
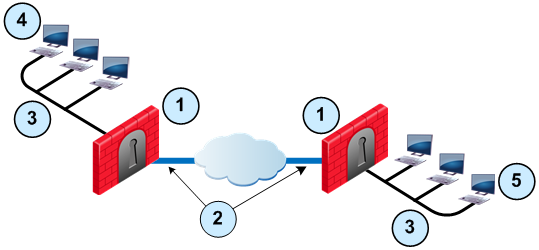
Item
|
Description
|
1
|
Security Gateway
|
2
|
VPN tunnel
|
3
|
Internal network in VPN domain
|
4
|
Host 1
|
5
|
Host 6
|
In this sample VPN deployment, Host 1 and Host 6 securely send data to each other. The Firewalls do IKE negotiation and create a VPN tunnel. They use the IPsec protocol to encrypt and decrypt data that is sent between Host 1 and Host 6.
VPN Workflow
Host 1 sends packet
to Host 6
|

|
Firewalls A & B create VPN tunnel
|

|
Firewall A encrypts data
|
|
|
|
|
|
Host 6 receives unencrypted data
|

|
Firewall B decrypts data
|

|
Encrypted data is sent through VPN tunnel
|
VPN Communities
A VPN Domain is a collection of internal networks that use Security Gateways to send and receive VPN traffic. Define the resources that are included in the VPN Domain for each Security Gateway. Then join the Security Gateways into a VPN community - collection of VPN tunnels and their attributes. Network resources of different VPN Domains can securely communicate with each other through VPN tunnels that terminate at the Security Gateways in the VPN communities.
VPN communities are based on Star and Mesh topologies. In a Mesh community, there are VPN tunnels between each pair of Security Gateway. In a Star community, each satellite Security Gateway has a VPN tunnel to the central Security Gateway, but not to other Security Gateways in the community.
Item
|
Description
|
1
|
Security Gateway. For Star topology, the central Security Gateway.
|
2
|
For Star topology, satellite Security Gateways.
|
Sample Combination VPN Community

Item
|
Description
|
1
|
London Security Gateway
|
2
|
New York Security Gateway
|
3
|
London - New York Mesh community
|
4
|
London company partner (external network)
|
5
|
London Star community
|
6
|
New York company partner (external network)
|
7
|
New York Star community
|
This deployment is composed of a Mesh community for London and New York Security Gateways that share internal networks. The Security Gateways for external networks of company partners do not have access to the London and New York internal networks. The Star VPN communities let the company partners access the internal networks.
Routing VPN Traffic
Configure the Security Gateway to route VPN traffic based on VPN domains or based on the routing settings of the operating system.

|
Note - For each VPN gateway, you must configure an existing gateway as a default gateway.
|
Domain Based VPN
The VPN traffic is routed according to the VPN domains that are defined in SmartDashboard. Use domain based routing to let satellite Security Gateways send VPN traffic to each other. The center Security Gateway creates VPN tunnels to each satellite and the traffic is routed to the correct VPN domain.
Route Based VPN
VPN traffic is routed according to the routing settings (static or dynamic) of the Security Gateway operating system. The Security Gateway uses a VTI (VPN Tunnel Interface) to send the VPN traffic as if it were a physical interface. The VTIs of Security Gateways in a VPN community connect and can support dynamic routing protocols.
Granular Routing Control
The Link Selection feature gives you granular control of the VPN traffic in the network. Use this feature to enable the Security Gateway to:
- Find the best possible route for VPN traffic
- Select the interfaces that are used for VPN traffic to internal and external networks
- Configure the IP addresses that are used for VPN traffic
- Use route probing to select available VPN tunnels
- Use Load Sharing for Link Selection to equally distribute VPN traffic to VPN tunnels
Remote Access VPN
If employees remotely access sensitive information from different locations and devices, system administrators must make sure that this access does not become a security vulnerability. Check Point's Remote Access VPN solutions let you create a VPN tunnel between a remote user and the internal network. The Mobile Access Software Blade extends the functionality of Remote Access solutions to include many clients and deployments.
Using Site to Site VPN
Sample Star Deployment
This section explains how to configure a VPN star community. This deployment lets the satellite Security Gateways connect to the internal network of the central Security Gateway. The internal network object is named: .
To create a new VPN Star Community:
- In the tab, select .
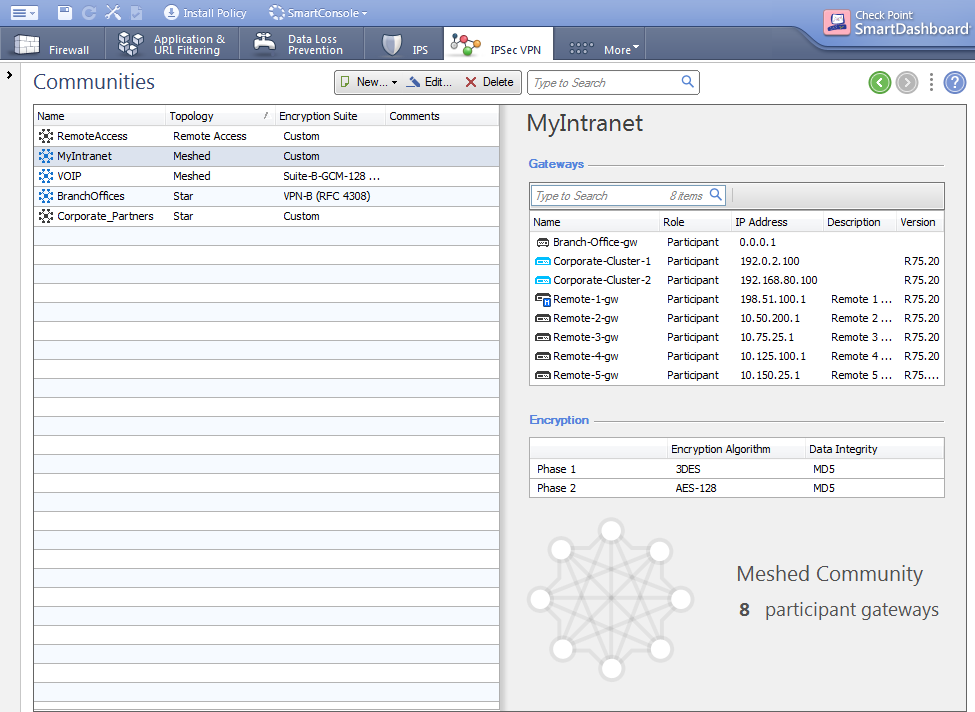
- Click .
The page of the window opens.
- Enter the name for the community.
- From the navigation tree, select .
- Configure the VPN encryption methods and algorithms for the VPN community.
- Click .
To configure star VPN for the Security Gateways:
- Double-click the Security Gateway.
The window opens.
- In , select .
- From the navigation tree, click .
- In the section:
- For the central Security Gateway, click and select the object.
- For a satellite Security Gateway, select
- From the navigation tree, click .
- Configure the Security Gateway as a member of a VPN star community.
- In the section, click .
The window opens.
- Select the VPN Community and click .
- Configure the Security Gateway as a hub or a spoke.
- For the center, select .
- For the satellites, select .
- Click .
- Click .
- Do these steps for all the Security Gateways for the VPN community.
Allowing VPN Connections
When you create a VPN connection between Security Gateways, add Firewall rules to allow the VPN traffic. Use the VPN Community objects in the VPN column of the Firewall Rule Base to define access control for VPN connections in the network.
Allowing All VPN Traffic
Use the feature to configure the Firewall to allow all VPN traffic to the internal networks for the VPN communities. It is not necessary to add rules to the Firewall Rule Base that allow the VPN traffic for the specified VPN communities.
SmartDashboard adds this automatic rule to the top of the Rule Base:
Source
|
Destination
|
VPN
|
Service
|
Action
|
Track
|
Install On
|
Any
|
Member Gateways
|
<VPN community>
|
Encrypted Services
|
Accept
|
Log
|
<VPN gateways>
|
This automatic rule allows all encrypted packets that are sent between hosts or clients in the specified VPN community. Traffic that is sent to the Security Gateways in the VPN community is dropped. The rule is installed on all Security Gateways in the VPN communities.

|
Note - This automatic rule can apply to more than one VPN community.
|
Sample VPN Firewall Rules
This table shows sample VPN rules for a Firewall Rule Base. (The , and columns are not shown. is set to , is set to , and is set to .)
No.
|
Name
|
Source
|
Destination
|
VPN
|
Service
|
Install On
|
-
|
-
|
Any
|
Member Gateways
|
BranchOffices
LondonOffices
|
Encrypted Services
|
BranchOffices
LondonOffices
|
2
|
Site to site VPN
|
Any
|
Any
|
All_GwToGw
|
FTP-port
HTTP
HTTPS
SMTP
|
Policy Targets
|
3
|
Remote access
|
Any
|
Any
|
RemoteAccess
|
HTTP
HTTPS
IMAP
|
Policy Targets
|
The first rule is the automatic rule for the feature. The Firewalls for the Security Gateways in the BranchOffices and LondonOffices VPN communities allow all VPN traffic from hosts in clients in these communities. Traffic to the Security Gateways is dropped. This rule is installed on all Security Gateways in these communities.
2. - Connections between hosts in the VPN domains of all Site to Site VPN communities are allowed. These are the only protocols that are allowed: FTP, HTTP, HTTPS and SMTP.
3. - Connections between hosts in the VPN domains of RemoteAccess VPN community are allowed. These are the only protocols that are allowed: HTTP, HTTPS, and IMAP.
Using Remote Access VPN
This section explains how to use a VPN tunnel to connect a client-based remote computer to an internal network. For more about using Mobile Access to connect remote devices to internal resources, see Remote Access to the Network.

|
Note - For each VPN gateway, you must configure an existing gateway as a default gateway.
|
VPN Connectivity Modes
The IPsec VPN Software Blade lets the Firewall overcome connectivity challenges for remote clients. Use VPN connectivity modes to make sure that remote users can connect to the VPN tunnels. These are some examples of connectivity challenges:
- The IP addresses of a remote access client might be unknown
- The remote access client can be connected to a hotel LAN with internal IP addresses
- It is necessary for the remote client to use protocols that are not supported
Office Mode
Remote users can be assigned the same or non-routable IP addresses from the local ISP. Office Mode solves these routing problems and encapsulates the IP packets with an available IP address from the internal network. Remote users can send traffic as if they are in the office and do not have VPN routing problems.
Visitor Mode
Remote users can be restricted to use HTTP and HTTPS traffic only. Visitor Mode lets these users tunnel all protocols with a regular TCP connection on port 443.
Sample Remote Access VPN Workflow
Use SmartDashboard to enable and configure the Security Gateway for remote access VPN connections. Then add the remote user information to the Security Management Server: create and configure an LDAP Account Unit or enter the information in the SmartDashboard user database. You can also configure the Firewall to authenticate the remote users. Define the Firewall access control and encryption rules. Create the LDAP group or user group object that is used for the Firewall rules. Then create and configure the encryption settings for the VPN community object. Add the access rules to the Firewall Rule Base to allow VPN traffic to the internal networks.
|
|
Enable remote access VPN
|
|
|
|
|
|
|
|
Configure LDAP
Account Unit
|
LDAP

|
Manage Users?
|
Smart
Dashboard

|
Configure users in SmartDashboard database
|
|
|
|
|
|
Configure user authentication
|
|
|
|
Configure user authentication
|
|
|
|
|
|
Create LDAP user
group object
|

|
Create VPN Community
|

|
Create user
group object
|
|
|
|
|
|
|
|
Configure rules for VPN access in Firewall Rule Base
|
|
|
|
|
|
|
|
|
|
Install policy
|
|
|
|



