Working with the Compliance Blade
The pane shows the overall compliance status of your organization. Select the different branches in the navigation tree to see more details.
To work with the Compliance Blade in SmartDashboard, go to the tab in SmartDashboard.
To work with the Compliance Blade in Multi-Domain Security Management, go to the tab in SmartDomain Manager (R77.20 and Higher).
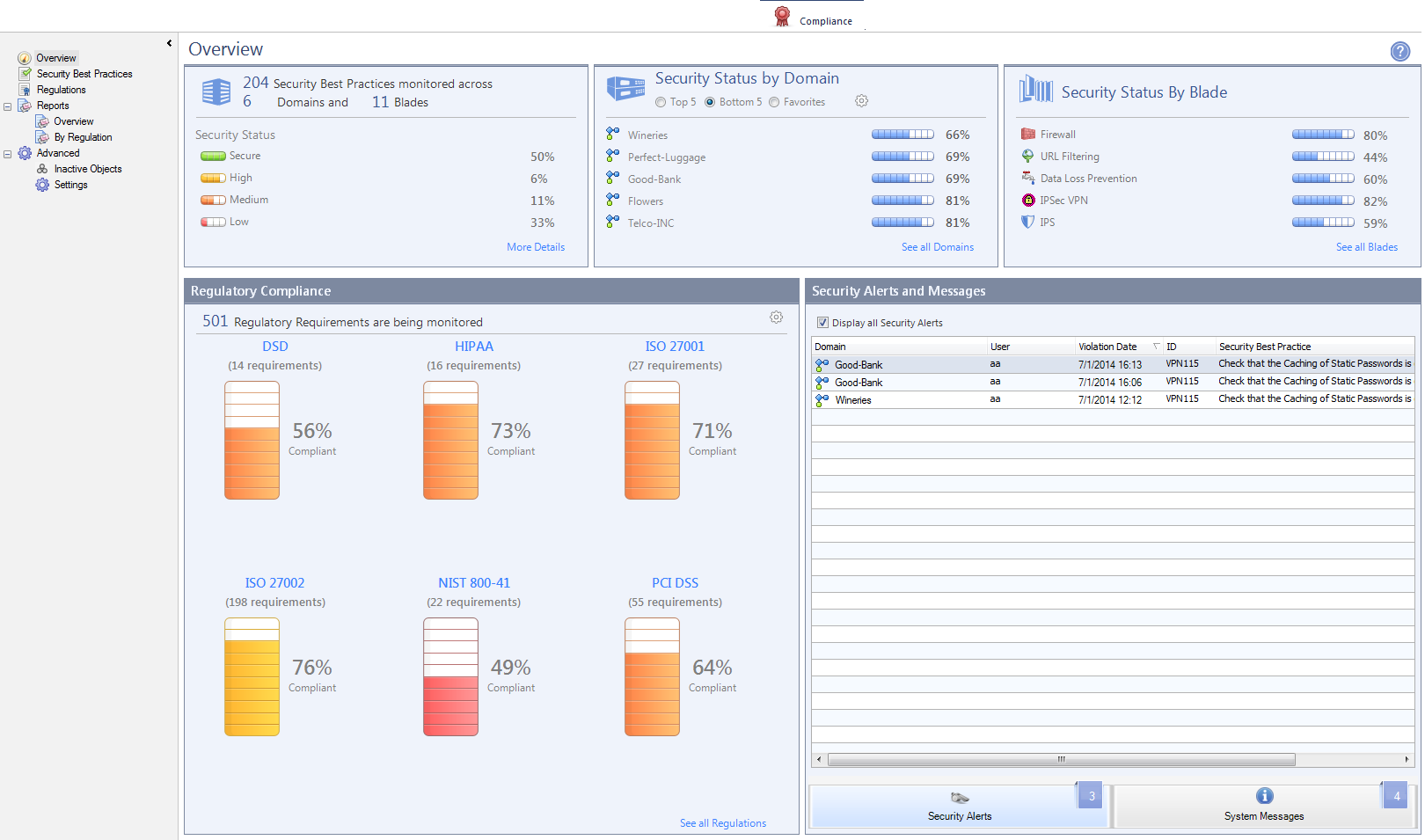
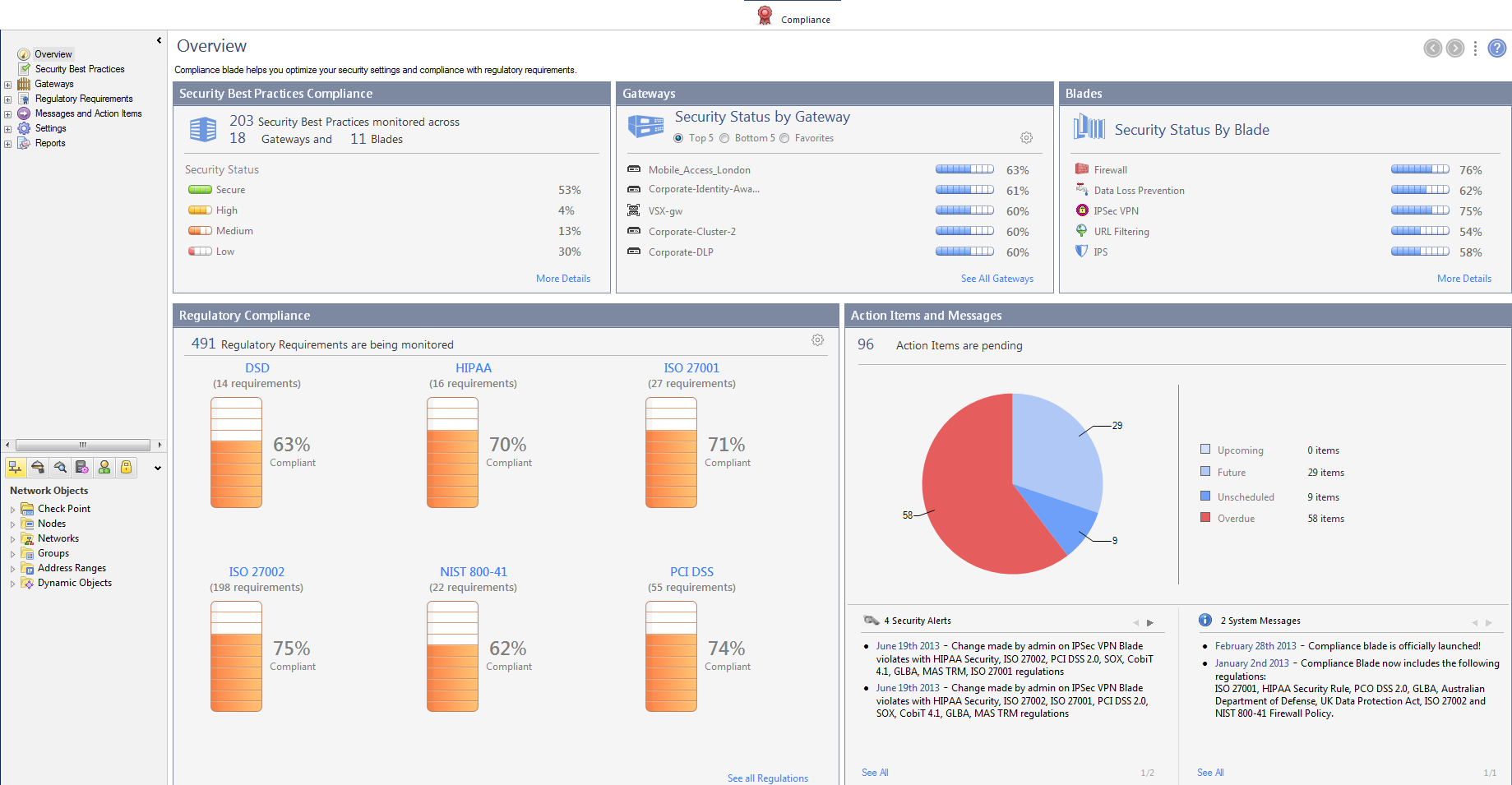
The Overview Pane
The pane shows:
Element
|
What can I do here?
|
|
|
See the compliance distribution by Security Best Practice status
|
|
|
See compliance scores for selected Security Gateways
|
|
|
See compliance scores and Security Best Practices by blade
|
|
|
See a summary of compliance with different regulations
|
|
|
See action items, compliance alerts, and system messages
|
Security Best Practices Compliance
The Compliance Blade uses Security Best Practices to make sure that Security Policy rules comply with Check Point configuration or policy recommendations. Each Security Best Practice contains criteria that match specified parameters in Security Policy rules or configuration settings.
The Compliance Blade includes many predefined Security Best Practices. In versions R77.20 and higher you can define your own custom Security Best Practices.
The Compliance Blade calculates a numeric score for each Security Best Practice, which is the average of the results for each object examined. Scores can show for the organization, Security Gateways, Software Blades, and regulations.
This is the Compliance Blade scoring system:
Category
|
Score
|
Low
|
0 - 50
|
Medium
|
51 - 75
|
High
|
76 - 99
|
Secure
|
100
|
N/A
|
Not Applicable
|
A category can show scores if:
- The Software Blade is not installed on the Security Management Server
- The Security Gateway does not support the examined feature
- You created a new Security Best Practice, but did not do a manual scan.
- A Security Best Practice is not activated for your organization
- A Security Best Practice cannot run because it is dependent on another Security Best Practice with a non-compliant status
Many Security Best Practices are binary: compliant or not.
Other Security Best Practices calculate a score based on the degree of security compliance.
Security Gateways
This SmartDashboard pane shows Security Gateways and Security Gateway Clusters with the highest compliance scores, lowest compliance scores, or a predefined set of .
- To see the Security Best Practice results for a Security Gateway, select it. The Gateways pane for the selected gateway opens.
- To see the results for all gateways, click. The window opens.
Domains

|
Note - This feature is supported in release R77.20 and higher.
|
This SmartDomain Manager pane shows Domains with the highest compliance scores, lowest compliance scores or a predefined set of .
Click See the security status for all Domains. Click .
Blades
This pane shows the average scores for the five Software Blades with the most Security Best Practices. The results show in descending order by the number of Security Best Practices. To see Security Best Practice results for one Software Blade, click that blade. The pane opens.
To see the results for all Software Blades, click . The pane opens. Group the results by .
Regulatory Compliance
The Compliance Blade includes many predefined governmental and industry standards right out of the box. From release 77.20 and higher, you can also define Regulations and Regulatory standards. This functionality is useful to manage organizational or local regulatory agency requirements.
The pane shows compliance statistics for selected regulatory standards, based on the Security Best Practice scan. This pane shows:
- The total number of Regulatory Requirements that are monitored
- The Number of Regulatory Requirements for each Regulation
- The Average compliance score for each regulation shown
The number of regulatory standards shown is based on your screen resolution.
To select the regulatory standards to show:
- Click the configuration icon in the top right corner of the pane.
- In the window, select the standards to show in the Overview.

|
Note - If a regulatory standard is not selected in the window, it is does not show in this widget.
|
To see the compliance score for all Regulatory Requirements, click . The window opens.
To see details of a standard, click the name of the standard in the pane or in the window. The pane for the selected standard opens.
Creating a User-Defined Security Best Practice

|
Note - This feature is supported in release R77.20 and higher.
|
You can define your own, custom Security Best Practices based on organizational security requirements. This release supports user-defined Security Best Practices only for Firewall rules. You define user-defined Security Best Practices in the SmartDashboard tab.
To define a new Security Best Practice:
- In the tab > pane, click .
- In the window, enter informational text in these fields:
- and for this Best Practice.
- and for the non-compliance Action Item generated by this best practice.
Note: In this version, you cannot change the option. It is automatically set to .
- In the table, enter rule matching criteria in the table cells. Each cell matches one related field or parameter in Security Policy rules. A Security Best Practice match occurs when all table cells match one or more rules in the Rule Base (Logical AND).
- Optional: Click to define these advanced scope parameters:
- - Define the part of the Rule Base to scan for matches. There are two parameters:
- or - Scan the top or bottom part of the Rule Base
- - The percentage of the Rule Base to scan.
For example, select to scan 30% of the Rule Base starting from the bottom (last rule in the Rule Base).
- - Select to include only rules that have at least one hit on or after the specified time period. Select the number of time periods and the type of period.
For example, select to include only rules that have at least one hit during the last two months.
- Define how Compliance Blade creates a violation (Action Item) when a Security Best Practice matches a rule.
- Define when the (Rule number) shows in the pane.
You can configure custom Security Best Practices to show the Rule in specified circumstances. This lets you easily see which rules cause or prevent violations.
- - Shows Rules that match the specified criteria in a Security Best Practice.
- - Shows Rules that do not match the specified criteria in a Security Best Practice.
- - Does not show the Rule.
- Click .
To see the status of your Security Best Practice, click . This feature runs the new Security Best Practice and shows the results in a window.
To change an existing, user-defined Security Best Practice:
- In the tab > pane, double click a user-defined Security Best Practice.
- In the Best Practice Definition window, change the parameters and settings as shown in the above procedure.
- Click .
Messages and Action Items (SmartDashboard)
This pane shows the updated status of pending action items for your organization.
- - Action items that are overdue.
- - Action items with due dates in the next 30 days.
- - Action items with due dates of more than 30 days.
- - Action items without defined due dates.
Note: We recommend that you resolve overdue action items immediately.
If you have a high resolution screen, the Alert and System messages show in the bottom section of the pane. Use the arrows to scroll through the messages.
If you have a low resolution screen, two buttons show in the bottom section of the pane.
- To see alert messages, click . They open in the pane.
- To see messages about the Compliance Blade, click . They open in the pane.
Using the Compliance Blade with Multi-Domain Security Management

|
Note - This feature is supported in release R77.20 and higher.
|
The Compliance Blade supports Multi-Domain Security Management Domains and is included as a tab in SmartDomain Manager. You can do these activities directly in SmartDomain Manager:
You must do these activities in the Domain SmartDashboard:
- Create, delete or change user-defined Security Best Practices.
- Work with messages and action items.
Searching, Grouping, Sorting
The Compliance Blade lets you search for text strings in many windows and panes. To search for a text string in enter a string in the search field at the top of the window or pane.
To search for values in a field, enter: field_namestring
To combine results into groups, select or in the field.
To sort the results by values in field, click that field header.
Working with Alerts and System Messages
You use the pane to see Security Alerts generated when a configuration change causes compliance status degradation. You can also see messages that are automatically generated by the Compliance Blade.
To see the details of a system message, double-click it. The window opens.
Working with Security Gateways
The Gatewayspane shows compliance details for each Security Gateway, VSX Virtual System or cluster in your environment. Here you can see the results of each Security Best Practice related to the selected Security Gateway.
To work with Security Gateways:
- Select the Gatewayspane from the tree.
- Select a Security Gateway or cluster.
The pane opens.
The top table shows the result of all Security Best Practices for the selected gateway:
- - Compliance Blade ID assigned to the Security Best Practice.
- - Security Best Practice name and brief description.
- Low, Medium, High, Secure, or N/A.
The bottom section shows one or more of these items:
- - What the Best Practice looks for.
- - Steps necessary to become secure.
- - The selected Security Best Practice is dependent on a different Security Best Practice. If the result of this other Security Best Practice is not secure, the selected Security Best Practice does not run.
- - Objects related to the selected Security Best Practice and their status. (Shows when the selected Security Best Practice applies to specified objects.)
- - List of all regulatory standards that include the Security Best Practice that generated the selected action item.
|



