

In This Section: |
Security Gateways and VPN connections are business critical devices. The failure of a Security Gateway or VPN connection can result in the loss of active connections and access to critical data. The Security Gateway between the organization and the world must remain open under all circumstances.
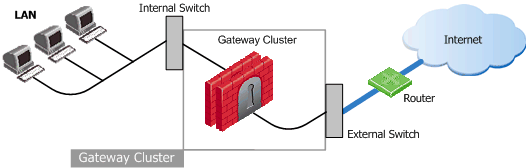
ClusterXL is a Check Point software-based cluster solution for Security Gateway redundancy and Load Sharing. A ClusterXL Security Cluster contains identical Check Point Security Gateways.
R77 ClusterXL supports High Availability clusters for IPv6. IPv6 status information is synchronized and the IPv6 clustering mechanism is activated during failover.
You can define IPv6 addresses for:
Limitations
During failover, a cluster sends gratuitous ARP request packets to update hosts and routers connected to cluster interfaces. It does this by advertising the new MAC address for the virtual cluster IPv4 addresses.
ClusterXL updates the IPv6 network during failovers. ClusterXL sends Neighbor Advertisement messages to update the neighbor cache (which is equivalent to the ARP cache in IPv4) by advertising the new MAC address for the virtual cluster IPv6 address. In addition, ClusterXL will reply to any Neighbor Solicitation with a target address equal to the Virtual Cluster IPv6 address.
Note - ClusterXL failover event detection is based on IPv4 probing. During state transition the IPv4 driver instructs the IPv6 driver to reestablish IPv6 network connectivity to the HA cluster.
ClusterXL uses State Synchronization to keep active connections alive and prevent data loss when a member fails. With State Synchronization, each member "knows" about connections that go through other members.
ClusterXL uses virtual IP addresses for the cluster itself and unique physical IP and MAC addresses for the members. Virtual IP addresses do not belong to physical interfaces.
ClusterXL can work with OPSEC certified High Availability and Load Sharing products, which use the same State Synchronization infrastructure as Check Point ClusterXL.
|
Note - The ClusterXL Administration Guide contains information only for Security Gateway clusters. For information about the use of ClusterXL with VSX, see the R77 VSX Administration Guide. |
The Cluster Control Protocol (CCP) is the glue that links together the members in the Security Cluster. CCP traffic is distinct from ordinary network traffic and can be viewed using any network sniffer.
CCP runs on UDP port 8116, and has the following roles:
The Check Point CCP is used by all ClusterXL modes as well as by OPSEC clusters. However, the tasks performed by this protocol and the manner in which they are implemented may differ between cluster types.
|
Note - There is no need to add a rule to the Security Policy Rule Base that accepts CCP |
ClusterXL must be installed in a distributed configuration in which the Security Management Server and the Security Cluster members are on different computers. ClusterXL is part of the standard Security Gateway installation.
For more detailed installation instructions, see the R77 Installation and Upgrade Guide.
See the applicable R77.x Release Notes to see the ClusterXL supported platforms.
To use ClusterXL for High Availability, each Security Gateway in the configuration must have a regular gateway license and the management server must have a license for each cluster defined.
To use ClusterXL for Load Sharing, each Security Gateway in the configuration must have a regular gateway license, an Acceleration and Clustering Blade (CPSB-ACCL or CPSB-ADNC) license, and the management server must have a license for each cluster defined.
If the proper licenses are not installed, the install policy operation will fail.
To learn more about licenses, go to the Check Point Support Center.
When using ClusterXL, make sure to synchronize the clocks of all of the cluster members. You can synchronize the clocks manually, or using a protocol such as NTP. Features, such as VPN, only function properly when the clocks of all of the cluster members are synchronized.
You can use the SmartDashboard toolbar to do these actions:
Icon |
Description |
|---|---|
Open the SmartDashboard menu. When instructed to select menu options, click this button to show the menu. For example, if you are instructed to select Manage > Users and Administrators, click this button to open the Manage menu and then select the Users and Administrators option. |
|
|
Save current policy and all system objects. |
|
Open a policy package, which is a collection of Policies saved together with the same name. |
|
Refresh policy from the Security Management Server. |
|
Open the Database Revision Control window. |
|
Change global properties. |
Verify Rule Base consistency. |
|
Install the policy on Security Gateways or VSX Gateways. |
|
Open SmartConsole. |