
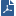

After you complete policy installation on the Check Point Appliance gateway and the gateway works as a cluster member, you can view cluster status in the WebUI application (Device > High Availability).
A security zone object is a logical object that represents the network behind a specified interface. For example, an InternalZone object represents the internal network IPs behind all of the internal gateway interfaces.
You can use security zone objects to create a generic Security Policy and reduce the amount of rules necessary in the Rule Base. This Security Policy can be applied to numerous Check Point Appliance gateways. Resolution of the security zone is done by the actual association on the Check Point Appliance gateway object in SmartDashboard.
Workflow
To associate a security zone object with an interface on the gateway object:
The Interface Properties window opens.
The Check Point Appliance Gateway General Properties is shown.
To create a rule with a security zone:
After you associated a security zone object to the applicable interface on the gateway, you can use it in a rule. To create a rule with a security zone, just add the security zone object to the Source or Destination cell.
For example, to create a rule that allows internal users access to any external network, create a rule with these fields:
Policy Field |
Value |
|---|---|
Source |
InternalZone |
Destination |
ExternalZone |
Action |
accept |
Install On |
gateway object or SmartLSM profile |
Use this procedure to prepare the policy for automatic installation when the gateway connects.
Note - If the Check Point Appliance is physically set up and configured, when you successfully complete this step, the policy is pushed to the gateway. For a list of possible statuses, see Viewing the Policy Installation Status.
At the end of the Install Policy process, the policy status for a Check Point Appliance that is not yet set up is "waiting for first connection." This implies that trusted communication is not yet established between the Security Management Server and the Check Point Appliance. When the gateway connects it establishes trust and attempts to install the policy automatically.
To install a security policy:
The Install Policy window opens.
By default, all gateways that are managed by the Security Management Server are available for selection.
The Installation Process window shows the status of the Network Security Policy for the selected target.
|
Important - If the Check Point Appliance object is defined by the appliance is not set up and it is in the "Waiting for first connection status", you see a message that says "Installation completed successfully". This means that the policy is successfully prepared for installation. |
Continue tracking the status of the Security Policy installation with the Policy Installation and the status bar.
You can see the installation status of managed gateways with the status bar that shows at the bottom of the SmartDashboard window. The status bar shows how many gateways are in Pending or Failed mode.
The status bar is updated dynamically each time a gateway tries to install a policy or tries to connect to the Security Management Server. The results of these actions are also shown in SmartDashboard popup notification balloons when such events occur. You can configure these notifications.
To monitor the status of the last policy installed on each gateway, you can use the Policy Installation Status window.
The window has two sections. The top section shows a list of gateways and status details regarding the installed policy. You can use the filter fields to see only policies of interest and hide other details by defining the applicable criteria for each field. After you apply the filtering criteria, only entries that match the selected criteria are shown. If the system logs trusted communication (SIC) attempts from unknown gateways, a yellow status bar opens below the filter fields.
The bottom section shows details of a row you select in the gateway list (errors that occurred, the date the policy was prepared, verification warnings). If there is a yellow status bar, click Show details to show the details of unknown gateways that try to connect to the Security Management Server.
These are the different statuses in this window:
Icon |
Policy status |
Description |
|---|---|---|
|
Succeeded |
Policy installation succeeded. |
|
Succeeded |
Policy installation succeeded but there are verification warnings. |
|
Waiting for first connection |
A Check Point Appliance object is configured, but the gateway is not connected to the Security Management Server (initial trust is not established).
|
|
Waiting for first connection |
Same as above, with warnings that attempts to establish trust failed or there are verification warnings. |
|
Pending |
The policy remains in the pending status until the gateway successfully connects to the Security Management Server and retrieves the policy. This status is shown only if there was at least one successful policy installation. For example, when the Security Management Server has problems connecting to the Gateway (the Gateway is unavailable for receiving communication, as in behind NAT). |
|
Pending |
Same as above but there are verification warnings. |
|
Warning |
Warning. |
|
Information |
Information. |
|
Failed |
Policy not installed due to a verification error. |
|
Failed |
Policy installation failed. |
You can access the Policy Installation Status window in these ways:
When you use the Management First deployment scenario, the policy is prepared to be fetched by appliances when they are configured.
During each appliance’s first time configuration, the routeable IP address of the Security Management Server is manually configured to create a first connection.
When SIC is established between the appliance and Security Management Server, the policy is fetched for the first time. Then, an automatic mechanism calculates the routeable IP address of the Security Management Server for the periodic policy fetch attempts. However, if the Security Management Server is located behind a 3rd party NAT device, the automatic mechanism fails.
In such cases, you can manually determine the routeable IP address of the Security Management Server, not only for the first connection. You can request that the appliance always attempt a connection with a manually configured IP address. You can configure this from the First Time Configuration Wizard - Security Management Server Connection page (select Always use this IP address and enter the IP address) or from the WebUI Home > Security Management page.