Disabling BPDU Forwarding
Bridge Protocol Data Unit (BPDU) is a data message that is sent between switches in an extended LAN that uses a Spanning Tree Protocol (STP) topology. When VLAN translation is configured, BPDU frames can send the incorrect VLAN number to switch ports through the bridge. This mismatch can cause the switch port to block traffic.
To resolve this issue, it is necessary to disable BPDU forwarding in a manner that survives reboot. This solution also works well for layer 2 Virtual Systems.
To permanently disable BPDU forwarding:
- Open
/etc/rc.d/init.d/network in a text editor. - Search for:
/etc/init.d/functions
- Add this new line after the above line:
/sbin/sysctl -w net.bridge.bpdu_forwarding=0
- Exit the editor and save the file.
- Copy the file to all SGMs:
> asg_cp2blades /etc/rc.d/init.d/network
- Reboot the system.
If you are using a dual Chassis 61000/41000 Security System, reboot the Standby Chassis first and then reboot the Active Chassis.
To learn more, see sk98927.
IPv6 Neighbor Discovery
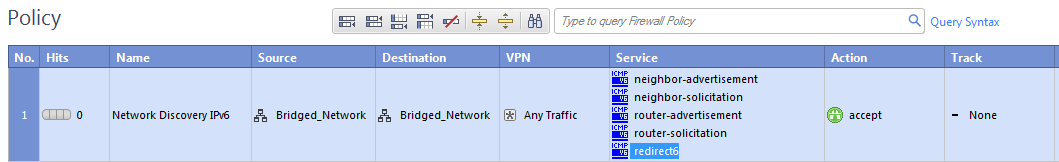
Neighbor discovery works over the ICMPv6 Neighbor Discovery protocol, which is the functional equivalent of the IPv4 ARP protocol. ICMPv6 Neighbor Discovery Protocol must be explicitly allowed for all bridged networks in your Firewall rules. This is different from ARP, for which traffic is always allowed regardless of the Rule Base.
This is an example of a rule that allows ICMPv6 Neighbor Discovery protocol:
|



