Layer Two Tunneling Protocol (L2TP) Clients
The Need for Supporting L2TP Clients
For some organizations there are clear benefits to be gained by using the Microsoft IPSec client for remote access to internal network, rather than the more feature rich and secure Check Point SecuRemote/SecureClient.
Reasons for using the Microsoft L2TP IPSec client include the fact that is an inherent part of many Windows operating systems, does not require an additional client to be installed, and is free.
Solution - Working with L2TP Clients
Introduction to L2TP Clients
Check Point Security Gateways can create VPNs with a number of third party IPSec clients. This explanation focuses on the Microsoft IPSec/L2TP client.
You can access a private network through the Internet by using a virtual private network (VPN) connection with the Layer Two Tunneling Protocol (L2TP). L2TP is an industry-standard Internet tunneling protocol.
Creating a Remote Access environment for users with Microsoft IPSec/L2TP clients is based on the same principles as those used for setting up Check Point Remote Access Clients. It is highly recommended to read and understand Introduction to Remote Access VPN before attempting to configure Remote Access for Microsoft IPSec/L2TP clients.
Establishing a VPN between a IPSec/L2TP Client and a Gateway
To allow the user at the Microsoft IPSec/L2TP client to access a network resource protected by a Security Gateway, a VPN tunnel is established between the Microsoft IPSec/L2TP client and the Security Gateway, as shown below.
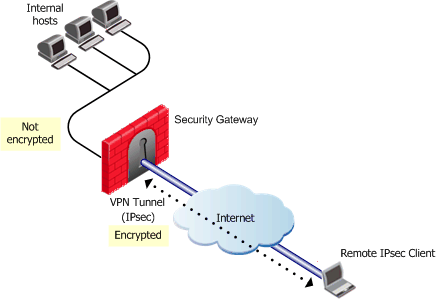
The process of the VPN establishment is transparent to the user, and works as follows:
- A user at an Microsoft IPSec/L2TP client initiates a connection to a Security Gateway.
- The Microsoft IPSec/L2TP client starts an IKE (Internet Key Exchange) negotiation with the peer Security Gateway in order to initiate construction of an encrypted tunnel.
- During IKE negotiation, the identities of the remote client machine and the Security Gateway are authenticated. This authentication is performed by means of certificates. Both sides send their certificates to each other as means of proving their identity. This ensures that a connection can be made only from the authenticated machine.
- Both peers exchange encryption keys, and the IKE negotiation ends.
- Encryption is now established between the client and the Security Gateway. All connections between the client and the Security Gateway are encrypted inside this VPN tunnel, using the IPSec standard.
- The Client starts a short L2TP negotiation, at the end of which the client can pass to the Security Gateway L2TP frames that are IPSec encrypted and encapsulated.
- The Security Gateway now authenticates the user at the Microsoft IPSec/L2TP client. This authentication is in addition to the client machine authentication in step 3. This identification can happen via two methods.
- A Certificate
- An MD5 challenge, whereby the user is asked to enter a username and a password (pre-shared secret)
- The Security Gateway allocates to the remote client an Office Mode IP address to make the client routable to the internal network. The address can be allocated from all of the Office Mode methods.
- The Microsoft IPSec/L2TP client connects to the Security Gateway, and can browse and connect to locations in the internal network.
Behavior of an L2TP Connection
When using an IPSec/L2TP client, it is not possible to connect to organization and to the outside world at the same time.
This is because when the client is connected to the Security Gateway, all traffic that leaves the client is sent to the Security Gateway, and is encrypted, whether or not it is intended to reach the protected network behind the Security Gateway. The Security Gateway then drops all encrypted traffic that is not destined for the encryption domain of the Security Gateway.
Security Gateway Requirements for IPSec/L2TP
In order to use Microsoft IPSec/L2TP clients, the Security Gateway must be set up for remote access. The setup is very similar to that required for remote access using Check Point Remote Access Clients, and involves creating a Remote Access community that includes the Security Gateway(s) and the user groups.
An additional requirement is to configure the Security Gateway to supply addresses to the clients by means of the Office Mode feature.
L2TP Global Configuration
Certain settings related to L2TP authentication can be configured globally for Security Gateways of version R71 and higher. These setting are configured using GuiDBedit, the Check Point Database Tool.
All L2TP clients can be configured to use a Pre-shared key for IKE in addition to the standard user authentication.

|
Note - IKE Security Authority created for L2TP cannot be used for regular IPSec traffic.
|
Authentication of Users and Client Machines
There are two methods used to authenticate an L2TP connection:
- Using Legacy Authentication
- Using certificates
Authentication Methods
L2TP clients can use any of the following Authentication schemes to establish a connection:
- Check Point password
- OS password
- RADIUS
- LDAP
- TACACS
Using a username and password verifies that a user is who they claim to be. All users must be part of the Remote Access community and be configured for Office Mode.
Certificates
During the process of establishing the L2TP connection, two sets of authentication are performed. First, the client machine and the Security Gateway authenticate each other's identity using certificates. Then, the user at the client machine and the Security Gateway authenticate each other using either certificates or a pre-shared secret.
The Microsoft IPSec/L2TP client keeps separate certificates for IKE authentication of the client machine, and for user authentication.
On the Security Gateway, if certificates are used for user authentication, then the Security Gateway can use the same certificate or different certificates for user authentication and for the IKE authentication.
Certificates for both clients and users can be issued by the same CA or a different CA. The users and the client machines are defined separately as users in SmartDashboard.
Certificates can be issued by:
- The Internal Certificate Authority (ICA) on the Security Management server, or
- An OPSEC certified Certificate Authority.
The certificates must use the PKCS#12 format, which is a portable format for storing or transporting private keys and certificates. The certificates are transferred to and stored on the client machine.
Authenticating the Client Machine During IKE
The Microsoft IPSec/L2TP client machine needs a certificate to authenticate itself to the Security Gateway during IKE negotiation.
It is possible to have only one certificate for all client machines, but you will then not be able to identify the machine that the user logged on from. For example, SmartView Tracker would show "user=bob, machine=generic_laptop" rather than "user=bob, machine=bob_laptop".
The computer account (we call it the machine account) must use PKI and must be in the Remote Access community. It is not affected by the authentication scheme in the Remote Access tab in the GUI. It may or may not be a good idea to use the same certificate (and "machine" user) for all clients. You can use an internal CA certificate with no problem for this user. It makes no difference if the authentication tab is defined or not.
The user account is more important, because that is the basis for rule matches and logs. This may use either MD5-challenge (passwords) or certificates. If you choose MD5-challenge, the certificate selection in the remote access tab is irrelevant. As for the user definition, it makes no difference how, if at all, the authentication tab is defined. The password is always the shared secret defined in the encryption tab. Note that this behavior differs from that of Secure Client, where passwords in the authentication tab override shared secrets from the encryption tab.
The client machine administrator must install the certificate in the machine certificate store.
Authenticating the User
Connecting with Microsoft IPSec/L2TP clients requires that every user be authenticated. Users can be authenticated with:
- Certificates, or
- Using an MD5 challenge, whereby the user is asked to enter a username and a password (pre-shared secret). The user must be informed of the password "out-of-band"
The user certificate can be easily added to the user certificate store. If the user certificate is on a Smart Card, plugging it into the client machine will automatically place the certificate into the certificate store.
User Certificate Purposes
It is possible to make sure that PKI certificates are used only for a defined purpose. A certificate can have one or more purposes, such as "client authentication", "server authentication", "IPSec" and "email signing". Purposes appear in the Extended Key Usage extension in the certificate.
The certificates used for IKE authentication do not need any purposes. For the user authentication, the Microsoft IPSec/L2TP client requires that
- The user certificate must have the "client authentication" purpose.
- The Security Gateway certificate must have the "server authentication" purpose.
Most CAs (including the ICA) do not specify such purposes by default. This means that the CA that issues certificates for IPSec/L2TP clients must be configured to issue certificates with the appropriate purposes (in the Extended Key Usage extension).
It is possible to configure the ICA on the Security Management server so that the certificates it issues will have these purposes. For OPSEC certified CAs, it is possible to configure the Security Management server to create a certificate request that includes purposes (in the Extended Key Usage extension).
It is also possible to configure the Microsoft IPSec/L2TP clients so that they do not validate the Security Gateway's certificate during the L2TP negotiation. This is not a security problem because the client has already verified the Security Gateway certificate during IKE negotiation.
Considerations for Choosing Microsoft IPSec/L2TP Clients
Check Point Endpoint Security VPN is much more than a personal firewall. It is a complete desktop security solution that allows the administrator to define a full desktop security policy for the client.IPSec/L2TP clients are more basic remote clients, and for some organizations may provide an adequate set of capabilities.
When using an IPSec/L2TP client, it is not possible to connect to organization and to the outside world at the same time. For some organizations, this may be an appropriate connection policy as it effectively dedicates the machine to being connected to the organization. Check Point Remote Access Clients on the other hand, make it possible to be connected to the organization and to the Internet at the same time.
Configuring Remote Access for Microsoft IPSec/L2TP Clients
Establishing a Remote Access VPN for Microsoft IPSec/L2TP clients requires configuration to be performed both on the Security Gateway and on the client machine. The configuration is the same as setting up Check Point Remote Access Clients, with a few additional steps. It is highly recommended to read and understand Introduction to Remote Access VPN before configuring Remote Access for Microsoft IPSec/L2TP clients.
The general procedure is as follows:
- Using SmartDashboard, configure a Remote Access environment, including generating authentication credentials (normally certificates) for the users.
- Generate certificates to authenticate the client machines.
- Configure support for Office Mode and L2TP on the Security Gateway.
- On the client machine, place the user certificate in the User Certificate Store, and the client machine certificate in the Machine Certificate Store.
- On the client machine, set up the Microsoft IPSec/L2TP client connection profile.
Configuration details are described in the following sections.
General Configuration Procedure
Configuring a Remote Access Environment
Follow the instructions in VPN for Remote Access Configuration.
Defining the Client Machines and their Certificates
- Define a user that corresponds to each client machine, or one user for all machines, and generate a certificate for each client machine user. The steps are the same as those required to define users and their certificate.
- Add users that correspond to the client machines to a user group, and add the user group to the Remote Access VPN community.
Configuring Office Mode and L2TP Support
- Configure Office Mode. For detailed instructions, see Configuring Office Mode.
- On the Security Gateway object, IPSec VPN > Remote Access page, check Support L2TP.
- Select the Authentication Method for the users:
- To use certificates, choose Smart Card or other Certificates (encryption enabled).
- To use a username and a shared secret (password), choose MD5-challenge.
- For Use this certificate, select the certificate that the Security Gateway presents in order to authenticate itself to users. This certificate is used if certificates are the chosen Authentication Method for users, in step 3.
Preparing the Client Machines
- In the Windows Services window of the client machine, make sure that the IPSec Policy Agent is running. It should preferably be set to Automatic.
- Make sure that no other IPSec Client is installed on the machine.
Placing the Client Certificate in the Machine Certificate Store
- Log in to the client machine with administrator permissions.
- Run the Microsoft Management Console. Click Start > Run
- Type: MMC, and press Enter.
- Select Console > Add/Remove Snap-In.
- In the Standalone tab, click Add.
- In the Add Standalone Snap-in window, select Certificates.
- In the Certificates snap-in window, select Computer account.
- In the Select Computer window select the computer (whether local or not) where the new certificates have been saved.
- Click Finish to complete the process and click Close to close the Add/Remove Snap- in window.
- The MMC Console window is displayed, where a new certificates branch has been added to the Console root.
- Right-click on the Personal entry of the Certificates branch and select All Tasks > Import. A Certificate Import Wizard is displayed.
- In the Certificate Import Wizard, browse to the location of the certificate.
- Enter the certificate file password.
- In the Certificate Store window make sure that the certificate store is selected automatically based on the certificate type.
- Select Finish to complete the Import operation.
Using the MMC, the certificate can be seen in the certificate store for the "Local Computer".
Placing the User Certificate in the User Certificate Store
- On the client machine, double-click on the user's certificate icon (the .p12 file) in the location where it is saved. A Certificate Import Wizard is displayed
- Enter the password.
- In the Certificate Store window make sure that the certificate store is selected automatically based on the certificate type.
- Select Finish to complete the Import operation.
Using the MMC, the certificate can be seen in the certificate store for the "current user".
Setting up the Microsoft IPSec/L2TP Client Connection Profile
Once the Client machine's certificate and the user's certificate have been properly distributed, set up the L2TP connection profile.
- In the client machine, right-click on the My Network Places icon on the desktop and select Properties.
- In the Network and Dial-up Connections window, select Make New Connection. The Network Connection Wizard is displayed.
- In the Network Connection Type window: On Windows 2000 machines select Connect to a private network through the Internet. On Windows XP machines select VPN or dial-up, and in the next window select VPN.
- In the Destination Address window, enter the IP address or the resolvable host name of the Security Gateway.
- In the Connection Availability window, make the new connection available For all users or Only for myself.
- In the closing window, provide a name for the new connection, for example, L2TP_connection.
- The Connect window for the new connection type is displayed.
To complete the L2TP connection configuration, proceed as follows. Note that the order is important:
- In the Connect window, click Properties.
- In the Networking tab, select the L2TP server.
- In the Security tab, choose Advanced > Settings, and select Use extensible Authentication protocols or Allow these protocols.
If you select Use extensible Authentication protocols: Choose either MD5-challenge, or Smart Card or other Certificates (encryption enabled). Make the same choice as made on the Security Gateway.
If you select Allow these protocols: Choose Unencrypted password (PAP).
For more information, see Configuring Office Mode and L2TP Support.
- Click OK to save the configured settings and to return to the Connect window.
- In the Connect window, enter the user name and password or select a certificate.
Configuring User Certificate Purposes
A CA that issues certificates for IPSec/L2TP clients must be configured to issue certificates with the appropriate purposes.
Alternatively, the Microsoft IPSec/L2TP Client can be set to not require the "Server Authentication" purpose on the Security Gateway certificate.
To configure the CA to Issue Certificates with Purposes
- If using the ICA, run the ICA Management Tool.
- Change the property IKE Certificate Extended Key Usage property to the value 1, to issue Security Gateway certificates with the "server authentication" purpose.
- Change the property IKE Certificate Extended Key Usage to the value 2 to issue user certificates with the "client authentication" purpose.
If using an OPSEC certified CA to issue certificates, use the DBedit command line or GuiDBedit, the graphical Database Tool to change the value of the global property cert_req_ext_key_usage to 1. This will cause the Security Management server to request a certificate that has purposes (Extended Key Usage extension) in the certificate.
- Using SmartDashboard, issue a new certificate for the Security Gateway. (In the VPN page, in the Certificate List section click Add. A new Certificate Properties window opens.) Look at the certificate properties and check that the Extended Key Usage Extension appears in the certificate.
- In the Remote Access page of the Security Gateway object, in the L2TP Support section, select the new certificate.
To Configure the Microsoft IPSec/L2TP Clients so they do not Check for the "Server Authentication" Purpose
The following procedure tells the Microsoft IPSec/L2TP Client not to require the "Server Authentication" purpose on the Security Gateway certificate.
- In the client machine, right-click on the My Network Places icon on the desktop and select Properties.
- In the Network and Dial-up Connections window, double click the L2TP connection profile.
- Click Properties, and select the Security tab.
- Select Advanced (custom settings), and click Settings.
- In the Advanced Security Settings window, under Logon security, select Use Extensible Authentication Protocol (EAP), and click Properties.
- In the Smart Card or other Certificate Properties window, uncheck Validate server certificate, and click OK.

|
Note - The client validates all aspects of the Security Gateway certificate, during IKE authentication, other than the "Server Authentication" purpose.
|
Making the L2TP Connection
- Click on Connect to make the L2TP connection.
- To view the IP address assigned to the connection, either view the Details tab in the connection Status window, or use the ipconfig /all command.
For More Information
For more information about how to configure advanced capabilities for Microsoft IPSec/L2TP clients, see
The L2TP protocol is defined in RFC 2661. Encryption of L2TP using IPSec is described in RFC 3193. For information about the L2TP protocol and the Microsoft IPSec/L2TP client, see the Network and Dial Up Connections Help in Windows 2000 and XP.
|
|


