The Check Point VPN Solution
The IPsec VPN Software Blade lets the Security Gateway encrypt and decrypt traffic to and from other gateways and clients. Use SmartDashboard to easily configure VPN connections between Security Gateways and remote devices. You can configure Star and Mesh topologies for large-scale VPN networks that include third-party gateways. The VPN tunnel guarantees:
- Authenticity - Uses standard authentication methods
- Privacy - All VPN data is encrypted
- Integrity - Uses industry-standard integrity assurance methods
IKE and IPsec
The Check Point VPN solution uses these secure VPN protocols to manage encryption keys, and send encrypted packets. IKE (Internet Key Exchange) is a standard key management protocol that is used to create the VPN tunnels. IPsec is protocol that supports secure IP communications that are authenticated and encrypted on private or public networks.
VPN Components
VPN is composed of:
- VPN endpoints, such as Security Gateways, Security Gateway clusters, or remote clients (such as laptop computers or mobile phones) that communicate using a VPN.
- VPN trust entities, such as a Check Point Internal Certificate Authority (ICA). The ICA is part of the Check Point suite used for creating SIC trusted connection between Security Gateways, authenticating administrators and third party servers. The ICA provides certificates for internal Security Gateways and remote access clients which negotiate the VPN link.
- VPN Management tools. Security Management server and SmartDashboard. SmartDashboard is the SmartConsole used to access the Security Management server. The VPN Manager is part of SmartDashboard. SmartDashboard enables organizations to define and deploy Intranet, and remote Access VPNs.
Understanding the Terminology
A number of terms are used widely in Secure VPN implementation, namely:
- VPN - Virtual Private Network. A secure, encrypted connection between networks and remote clients on a public infrastructure, to give authenticated remote users and sites secured access to an organization's network and resources.
- Virtual Tunnel Interface - Virtual Tunnel Interface. A virtual interface that is a member of an existing, Route Based, VPN tunnel.
- VPN Peer - A gateway that connects to a different gateway using a Virtual Tunnel Interface.
- VPN Domain - A group of computers and networks connected to a VPN tunnel by one VPN gateway that handles encryption and protects the VPN Domain members.
- VPN Community - A named collection of VPN domains, each protected by a VPN gateway.
- VPN Security Gateway - The gateway that manages encryption and decryption of traffic between members of a VPN Domain, typically located at one (Remote Access VPN) or both (Site to Site VPN) ends of a VPN tunnel.
- Site to Site VPN - An encrypted tunnel between two gateways, typically of different geographical sites.
- Remote Access VPN - An encryption tunnel between a Security Gateway and remote access clients, such as Endpoint Security VPN, and communities.
- Remote Access Community - A group of computers, appliances, and devices that access, with authentication and encryption, the internal protected network from physically remote sites.
- Star Topology - A "hub and spoke" virtual private network community, with gateways defined as Satellites (spokes) that create tunnels only with the central gateway ("hub").
- Meshed topology - A VPN community with a VPN Domain that creates a tunnel to other VPN Domains.
- Domain-based VPN - A method to route encrypted traffic with parameters defined by Security Gateways.
- Route-Based VPN - A routing method for participants in a VPN community, defined by the Virtual Tunnel Interfaces (VTI).
- IKE (Internet Key Exchange) - An Encryption key management protocol that enhances IPSec by providing additional features, flexibility, and ease of configuration.
- IPSec - A set of secure VPN protocols that manage encryption keys and encrypted packet traffic, to create a standard for authentication and encryption services.
Site to Site VPN
The basis of Site to Site VPN is the encrypted VPN tunnel. Two Security Gateways negotiate a link and create a VPN tunnel and each tunnel can contain more than one VPN connection. One Security Gateway can maintain more than one VPN tunnel at the same time.
Sample Site to Site VPN Deployment
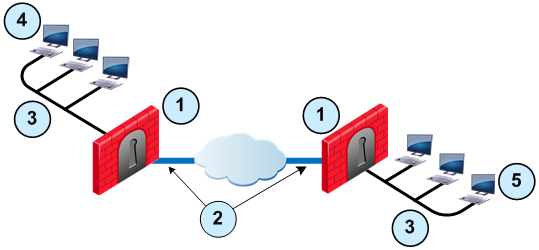
Item
|
Description
|
1
|
Security Gateway
|
2
|
VPN tunnel
|
3
|
Internal network in VPN domain
|
4
|
Host 1
|
5
|
Host 6
|
In this sample VPN deployment, Host 1 and Host 6 securely send data to each other. The Firewalls do IKE negotiation and create a VPN tunnel. They use the IPsec protocol to encrypt and decrypt data that is sent between Host 1 and Host 6.
VPN Workflow
Host 1 sends packet
to Host 6
|

|
Firewalls A & B create VPN tunnel
|

|
Firewall A encrypts data
|
|
|
|
|
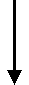
|
Host 6 receives unencrypted data
|

|
Firewall B decrypts data
|

|
Encrypted data is sent through VPN tunnel
|
VPN Communities
A VPN Domain is the internal networks that use Security Gateways to send and receive VPN traffic. Define the resources that are included in the VPN Domain for each Security Gateway. Then join the Security Gateways into a VPN community. Network resources of the different Security Gateways can securely communicate with each other through VPN tunnels.
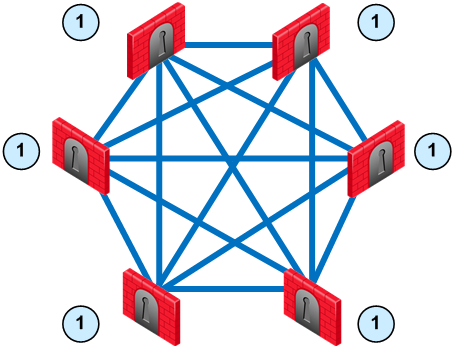
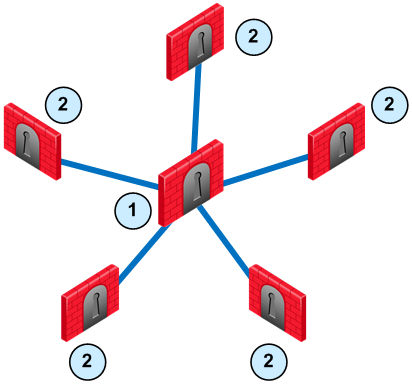
VPN communities are based on Star and Mesh topologies. In a Mesh community, there are VPN connections between each Security Gateway. In a Star community, satellites have a VPN connection with the center Security Gateway, but not to each other.
|
|
|
|
|
|
Item
|
Description
|
1
|
Security Gateway. For Star topology, the central Security Gateway.
|
2
|
For Star topology, satellite Security Gateways.
|
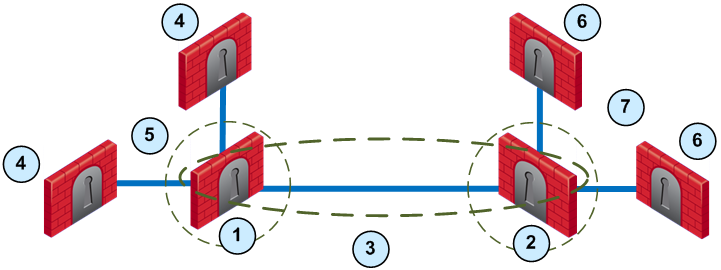
Sample Combination VPN Community
Item
|
Description
|
1
|
London Security Gateway
|
2
|
New York Security Gateway
|
3
|
London - New York Mesh community
|
4
|
London company partner (external network)
|
5
|
London Star community
|
6
|
New York company partner (external network)
|
7
|
New York Star community
|
This deployment is composed of a Mesh community for London and New York Security Gateways that share internal networks. The Security Gateways for external networks of company partners do not have access to the London and New York internal networks. The Star VPN communities let the company partners access the internal networks.
Routing VPN Traffic
Configure the Security Gateway to route VPN traffic based on VPN domains or based on the routing settings of the operating system.

|
Note - For each of the VPN gateways, you must configure an existing gateway as a default gateway.
|
Domain Based VPN
The VPN traffic is routed according to the VPN domains that are defined in SmartDashboard. Use domain based routing to let satellite Security Gateways send VPN traffic to each other. The center Security Gateway creates VPN tunnels to each satellite and the traffic is routed to the correct VPN domain.
Route Based VPN
VPN traffic is routed according to the routing settings (static or dynamic) of the Security Gateway operating system. The Security Gateway uses a VTI (VPN Tunnel Interface) to send the VPN traffic as if it were a physical interface. The VTIs of Security Gateways in a VPN community connect and can support dynamic routing protocols.
Granular Routing Control
The Link Selection feature gives you granular control of the VPN traffic in the network. Use this feature to enable the Security Gateway to:
- Find the best possible route for VPN traffic
- Select the interfaces that are used for VPN traffic to internal and external networks
- Configure the IP addresses that are used for VPN traffic
- Use route probing to select available VPN tunnels
- Use Load Sharing for Link Selection to equally distribute VPN traffic to VPN tunnels
Remote Access VPN
If employees remotely access sensitive information from different locations and devices, system administrators must make sure that this access does not become a security vulnerability. Check Point's Remote Access VPN solutions let you create a VPN tunnel between a remote user and the internal network. The Mobile Access Software Blade extends the functionality of Remote Access solutions to include many clients and deployments.
Client-Based vs. Clientless
Check Point remote access solutions use IPsec and SSL encryption protocols to create secure connections. All Check Point clients can work through NAT devices, hotspots, and proxies in situations with complex topologies, such as airports or hotels. These are the types of installations for remote access solutions:
- - Client application installed on endpoint computers and devices. Clients are usually installed on a managed device, such as a company-owned computer. The client supplies access to most types of corporate resources according to the access privileges of the user.
- - Users connect through a web browser and use HTTPS connections. Clientless solutions usually supply access to web-based corporate resources.
- - Users connect through a web browser and a client is installed when necessary. The client supplies access to most types of corporate resources according to the access privileges of the user.
Using Remote Access VPN
This section explains how to use a VPN tunnel to connect a client-based remote computer to an internal network. For more about using Mobile Access to connect remote devices to internal resources, see Remote Access to the Network.

|
Note - For each of the VPN gateways, you must configure an existing gateway as a default gateway.
|
VPN Connectivity Modes
The IPsec VPN Software Blade lets the Firewall overcome connectivity challenges for remote clients. Use VPN connectivity modes to make sure that remote users can connect to the VPN tunnels. These are some examples of connectivity challenges:
- The IP addresses of a remote access client might be unknown
- The remote access client can be connected to a hotel LAN with internal IP addresses
- It is necessary for the remote client to use protocols that are not supported
Office Mode
Remote users can be assigned the same or non-routable IP addresses from the local ISP. Office Mode solves these routing problems and encapsulates the IP packets with an available IP address from the internal network. Remote users can send traffic as if they are in the office and do not have VPN routing problems.
Visitor Mode
Remote users can be restricted to use HTTP and HTTPS traffic only. Visitor Mode lets these users tunnel all protocols with a regular TCP connection on port 443.
Sample Remote Access VPN Workflow
Use SmartDashboard to enable and configure the Security Gateway for remote access VPN connections. Then add the remote user information to the Security Management Server: create and configure an LDAP Account Unit or enter the information in the SmartDashboard user database. You can also configure the Firewall to authenticate the remote users. Define the Firewall access control and encryption rules. Create the LDAP group or user group object that is used for the Firewall rules. Then create and configure the encryption settings for the VPN community object. Add the access rules to the Firewall Rule Base to allow VPN traffic to the internal networks.
|
|
Enable remote access VPN
|
|
|
|
|
|
|
|
Configure LDAP
Account Unit
|
LDAP

|
Manage Users?
|
Smart
Dashboard

|
Configure users in SmartDashboard database
|
|
|
|
|
|
Configure user authentication
|
|
|
|
Configure user authentication
|
|
|
|
|
|
Create LDAP user
group object
|

|
Create VPN Community
|

|
Create user
group object
|
|
|
|
|
|
|
|
Configure rules for VPN access in Firewall Rule Base
|
|
|
|
|
|
|
|
|
|
Install policy
|
|
|
IPv6 Support and Limitations
This release includes limited IPv6 support for IPsec VPN communities:
- IPv6 is supported for Site to Site VPN only (Main IP to Main IP). The Main IP address for both Security Gateways must be defined as an IPv6 Address. You can define other IP addresses that are IPv4 or IPv6.
- IPv6 supports IKEv2 encryption only. IKEv2 is automatically always used for IPv6 traffic. The encryption method configuration applies to IPv4 traffic only.
These VPN features are not supported for IPv6:
- VSX
- Remote Access VPN
- CRL fetch for the internal Certificate Authority
- Multiple Entry Points (MEP)
- Route-based VPN (VTI)
- Wire Mode VPN
- Gateways with a dynamic IP address.
- Route Injection Mechanism (RIM)
- Traditional mode Firewall Policies
- IKE Denial of Service protection
- IKE Aggressive Mode
- Gateways with Dynamic IP addresses
- Traditional Mode VPN
- Migration from Traditional mode to Simplified mode
- Tunnel Management (permanent tunnels)
- Directional VPN Enforcement
- Link Selection
- GRE Tunnels
- Tunnel View in SmartView Monitor
- VPN Overview page
- vpn_route.conf configuration file
SmartDashboard Toolbar
You can use the SmartDashboard toolbar to do these actions:
Icon
|
Description
|

|
Open the SmartDashboard menu. When instructed to select menu options, click this button to show the menu.
For example, if you are instructed to select > , click this button to open the Manage menu and then select the option.
|

|
Save current policy and all system objects.
|

|
Open a policy package, which is a collection of Policies saved together with the same name.
|

|
Refresh policy from the Security Management Server.
|

|
Open the Database Revision Control window.
|

|
Change global properties.
|

|
Verify Rule Base consistency.
|
|
Install the policy on Security Gateways or VSX Gateways.
|

|
Open SmartConsoles.
|
|


