Introduction
SmartView Tracker Overview
You need different levels of tracking, depending on the data's importance. For example, while you may choose to track standard network patterns (e.g., your users' surfing patterns), this information is not urgent and you can inspect it at your convenience. If your network is being attacked, you must be alerted immediately.
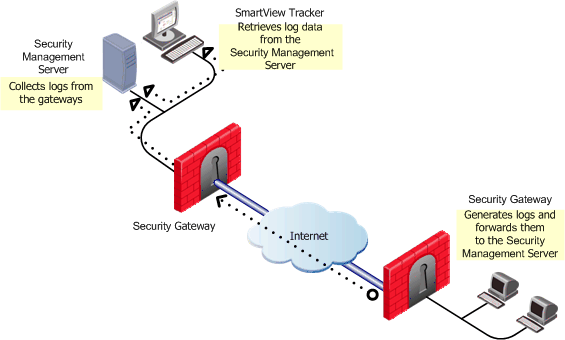
Check Point products provide you with the ability to collect comprehensive information on your network activity in the form of logs. You can then audit these logs at any given time, analyze your traffic patterns and troubleshoot networking and security issues. The figure below illustrates the log collection and tracking process:
The SmartDashboard allows you to customize your tracking settings for each Rule Base, by specifying per-rule whether or not to track the events that match it.
If you decide to track the events that match a certain rule, you can choose from a variety of tracking options, based on the information's urgency. For example, you can choose a standard Log for allowed http connections; opt for an Account log when you wish to save byte data; or issue an Alert (in addition to the log) when a connection's destination is your gateway. For a list of the available tracking options, right-click the relevant rule's Track column.
The gateways on which this Policy is installed collect data as specified in the Policy, and forward the logs to the Security Management server (and/or to Log Servers, depending on their settings). The logs are organized in files according to the order in which they arrived to the Security Management server. All new logs are saved to the fw.log file, except for audit (management-related) logs, which are saved to the fw.adtlog file.
The Security Management server makes these logs available for inspection via SmartView Tracker - a comprehensive auditing solution, enabling central management of both active and old logs of all Check Point products. You can conveniently customize searches to address your specific tracking needs; integrate the logs with the Check Point SmartReporter; or export them to text files or to an external Oracle database.
The Security Management server also performs the operations specified in the Policy for events matching certain rules (e.g., issuing an alert, sending email, running a user-defined script etc.).
In addition to the above solutions, you can benefit from the tracking and auditing capabilities of the following Check Point SmartConsole:
- SmartView Monitor allows you to manage, view and test the status of various Check Point components throughout the system, as well as to generate reports on traffic on interfaces, specific Check Point products, and other Check Point system counters.
- SmartReporter allows you to save consolidated records (as opposed to "raw" logs) and conveniently focus on events of interest.
Tracking Network Traffic
The SmartView Tracker can be used to track all daily network traffic and activity logged by any Check Point and OPSEC Partners log-generating product. It can also be used to give an indication of certain problems. Network administrators can use the log information for:
- Detecting and monitoring security-related events.
For example, alerts, repeated rejected connections or failed authentication attempts, might point to possible intrusion attempts.
- Collection information about problematic issues.
For example, a client has been authorized to establish a connection but the attempts to connect have failed. The SmartView Tracker might indicate that the Rule Base has been erroneously defined to block the client's connection attempts.
- Statistical purposes such as analyzing network traffic patterns.
For example, how many HTTP services were used during peak activity as opposed to Telnet services.
Log Suppression
The SmartView Tracker is designed to efficiently present the logs that are generated from Check Point products. To avoid displaying log entries for a frequently repeating event, SmartView Tracker displays the first instance of the event and then counts subsequent instances which occur in the next two minutes.
For as long as the event continues to occur, every two minutes SmartView Tracker shows a Log Suppression Report which contains the details of the event as well as the number of times the event occurred.
SmartView Tracker GUI
In the main window of SmartView Tracker, an entry in the Records pane is a record of an event that was logged according to a specific rule in the Rule Base. New records that are added to the fw.log file are automatically added to the Records pane as well.
To understand the figure, refer to the numbers in the figure and the following list.
- The Network & Endpoint, Active and Management modes display different types of logs.
- The Query Tree pane displays the Predefined and Custom queries.
- The Query Properties pane displays the properties of the fields in the Records pane.
- The Records pane displays the fields of each record in the log file.
The log fields displayed are a function of the following factors:
- The software blade that generated the log, such as Firewall, VPN or IPS.
- The type of operation performed, such as installation or opening a connection.
For example, when NAT is used, the address translation fields (with the 'Xlate' prefix, e.g., XlateSrc, XlateDst etc.) are displayed. When Firewall is used, IKE-related fields (e.g., IKE Cookiel, IKE CookieR etc.) are displayed.
SmartView Tracker Toolbar
Icon
|
Menu Command
|
Description
|

|
>
|
Open an existing Log File.
|

|
>
|
Save the Log File under a new name in a new location.
|

|
>
|
Open a new active Log File.
|

|
> t
|
Remote log files management
|

|
>
|
Hide or show the Files Fetch Progress Window.
|

|
>
|
Hide or show the Query Tree on the left side of the window.
|

|
>
|
Hide or show user identities. Only users with relevant permissions can view identities.
|

|
Select a query > >
|
Open an existing Query.
|

|
>
|
Save the modifications you made to the custom Query.
|

|
>
|
Save the Query under a new name in the Custom folder.
|

|
|
Online Help
|
SmartView Tracker Query Toolbar

|
Note - Some of the toolbar buttons are shortcuts for menu commands. Some toolbar buttons do not have corresponding menu commands.
|
The following table describes the toolbar buttons for the Query Properties pane.
Icon
|
Description
|

|
Show or hide query properties.
|

|
Apply all filtering criteria.
|

|
Display the name of the host and the domain.
|

|
Display the type of service the port uses.
|

|
Show all null matches.
|

|
The Autoscroll button enables you to update the Log File to display all new log entries and place them at the end of the Log File.
|

|
Delete all filtering criteria in the Log File.
|

|
Find the specified text string in all fields.
|

|
Go to the top of the Log File.
|

|
Go to the bottom of the Log File.
|

|
Shows the total number of filtered records.
|

|
The Abort button enables you to stop loading Log data from the server or abort any action which is in progress or on queue to begin.
|
SmartView Tracker Actions
The following table gives a description of the different types of actions recorded by SmartView Tracker.
Action Filter
|
Description
|
Accept
|
The connection was allowed to proceed.
|
Reject
|
The connection was blocked.
|
Drop
|
The connection was dropped without notifying the source.
|
Detect
|
The connection was monitored without enforcing IPS protections.
|
Encrypt
|
The connection was encrypted.
|
Authcrypt
|
SecuRemote user logon.
|
Bypass
|
The connection passed transparently through InterSpect.
|
Flag
|
Flags the connection.
|
Login
|
A user logged into the system.
|
Reject
|
The connection was rejected.
|
VPN routing
|
The connection was routed through the gateway acting as a central hub.
|
Decrypt
|
The connection was decrypted.
|
Key Install
|
Encryption keys were created.
|
Authorize
|
Client Authentication logon.
|
Deauthorize
|
Client Authentication logoff.
|
Block
|
Connection blocked by Interspect.
|
Detect
|
Connection was detected by Interspect.
|
Inspect
|
Connection was subject to InterSpect configured protections.
|
Quarantine
|
The IP source address of the connection was quarantined by InterSpect.
|
Replace Malicious code
|
Malicious code in the connection was replaced.
|
DLP Actions
Specific actions for DLP incidents include:
DLP Action
|
Description
|
Ask User
|
DLP incident captured and put in Quarantine, user asked to decide what to do.
|
Do not Send
|
User decided to drop transmission that was captured by DLP.
|
Send
|
User decided to continue transmission after DLP notified that it may contain sensitive data.
|
Quarantine Expired
|
DLP captured data transmission cannot be sent because the user did not make a decision in time. Expired incidents may still be viewed, until they are deleted (routine cleanup process).
|
Prevent
|
DLP transmission was blocked.
|
Allow
|
DLP transmission was allowed; usually by exception to rule.
|
Inform User
|
DLP transmission was detected and allowed, and user notified.
|
Deleted Due To Quota
|
DLP incidents are deleted from gateway for disk space.
|
DLP General Columns
DLP incidents may show any of these columns and are available to all administrators.
DLP Columns
|
Description
|
Incident UID
|
Unique ID of the incident.
|
DLP Action Reason
|
Reason for the action. Possible values: Rulebase, Internal Error, Prior User Decision
|
Related Incident
|
Internal incident ID related to the current log.
|
DLP Transport
|
Protocol of the traffic of the incident: HTTP, FTP, SMTP.
|
Using the Incident UID as a key between multiple logs:
Each DLP incident has a unique ID included in the log and sent to the user as part of an email notification. User actions (Send, Do not Send) are assigned the same Incident UID that was assigned to the original DLP incident log.
If a user sends an email with a DLP violation and then decides to discard it, two logs are generated. The first log is a DLP incident log with Ask User action and is assigned an Incident UID. On the user action, the second log is generated with the same UID, with the Do not Send action.
Each matched data type generates its own log. The gateway makes sure that all the data type logs of one incident indicate the same unique Incident UID and rule action (Prevent, Ask, Inform, or Detect), even if data types were matched on different rules. The common action for an incident is the most restrictive.
For example, assume a transmission matches two data types. Each data type is used in a different rule. The action of one rule is Prevent. The action of another rule is Detect. The two logs that are generated will indicate Prevent as the action. (The action implemented will be Prevent.) The log of the Detect rule will show Rule Base (Action set by different rule) in the DLP Action Reason column.
DLP Restricted Columns
These columns are restricted to administrators with permissions.
Restricted Filters
|
Description
|
DLP Rule Name
|
Name of the DLP rule on which the incident was matched.
|
DLP Rule UID
|
Internal rule ID of the DLP rule on which the incident was matched.
|
Data Type UID
|
Internal ID of the data type on which the incident was matched.
|
Data Type Name
|
Name of the matched data type.
|
User Action Comment
|
Comment given by user when releasing the incident from the Portal.
|
DLP Recipients
|
For SMTP traffic, list of recipients of captured email.
|
Scanned Data Fragment
|
Captured data itself: email and attachment of SMTP, file of FTP, or HTTP traffic.
|
Message to User
|
Message sent, as configured by administrator, for the rule on which the incident was matched.
|
DLP Categories
|
Category of data type on which the incident was matched.
|
DLP Words List
|
If the data type on which the incident was matched included a word list (keywords, dictionary, and so on), the list of matched words.
|
Mail Subject
|
For SMTP traffic, the subject of captured email.
|
Identity Awareness Columns
Incidents for Identity Awareness show information about the AD name and IP address associations.
Identity Awareness Column
|
Description
|
Destination Machine Name
|
Resolved AD name of a machine associated with destination IP of a logged traffic.
|
Destination User Name
|
Resolved AD name of a user associated with destination IP of a logged traffic.
|
Source Machine Name
|
Resolved AD name of a machine associated with source IP of a logged traffic.
|
Source User Name
|
Resolved AD name of a user associated with source IP of a logged traffic.
|
IPS Columns
The Protection Type column is relevant to IPS protection incidents. You can filter for any of these types:
- Application Control
- Engine Settings
- Geo Protection
- Protocol Anomaly
- Signature
Other columns specific to the IPS Software Blade:
- Protected Server
- Source Reputation
- Destination Reputation
- Client Type
- Server Type
IPS-1 Columns
These columns are relevant for IPS-1 appliances.
IPS-1 Product Column
|
Description
|
RPC Service Number
|
Protocol detail.
|
VLAN ID
|
Internal ID of the VLAN.
|
MAC Destination Address
MAC Source Address
|
MAC address associated with destination or source machine.
|
Command
|
Used in protocol context and is name or identifier of the command used in the traffic of the attack.
|
Destination DHCP Hostname
Destination DNS Hostname
NetBIOS Destination Hostname
NetBIOS Source Hostname
Source DHCP Hostname
Source DNS Hostname
|
Name of the host associated with source or destination of the logged traffic according to the relevant resolving service. Not all those fields are filled in the same time.
|
Source OS
Destination OS
|
OS type of source or destination machine.
|
Email Address
|
Email address fetched from attack traffic.
|
Email Subject
|
Subject of the email caught in attack traffic.
|
Hostname
|
If in attack traffic we find host name that is unrelated to the either source or destination, it is given here.
|
HTTP Referer
HTTP Modifier
Cookie
URI
Payload
|
HTTP protocol elements.
|
Attack Assessment
|
Possible values: Failed, Successful, Unknown.
|
Attack Impact
|
Possible values: Admin Access, Code Execution, Data Access, Denial of Service, Information Gathering, Security Violation, Unknown, User Access.
|
Sensor Mode
|
Possible values: Invalid, Passive, Inline - Fail-open, Inline - Fail-closed, Inline - Monitor only.
|
Activated Quarantine
|
Whether attack caused quarantine.
|
SmartView Tracker Modes
SmartView Tracker consists of three different modes:
- Log, the default mode, displays all logs in the current
fw.log file. These include entries for security-related events logged by different Check Point software blades, as well as Check Point's OPSEC partners. New logs that are added to the fw.log file are added to the bottom of the Records pane. - Active allows you to focus on connections that are currently open through the Security Gateways that are logging to the active Log file.
- Audit allows you to focus on management-related records, such as records of changes made to objects in the Rule Base and general SmartDashboard usage. This mode displays audit-specific data, such as the record's Administrator, Application or Operation details, which is read from the
fw.adtlog file.
You can toggle between modes by clicking the desired tab.
|
|

