Monitoring Gateway Status
Gateway Status Solution
Check Point enables information about the status of all gateways in the system to be collected from these gateways. This information is gathered by the Security Management server and can be viewed in SmartView Monitor. The information gathered includes status information about:
- Check Point gateways
- OPSEC gateways
- Check Point Software Blades
Gateways Status is the SmartView Monitor view which displays all component status information. A Gateways Status view displays a snapshot of all Check Point Software Blades, such as VPN and ClusterXL, as well as third party products (for example, OPSEC-partner gateways).
Gateways Status is very similar in operation to the SNMP daemon that also provides a mechanism to ascertain information about gateways in the system.
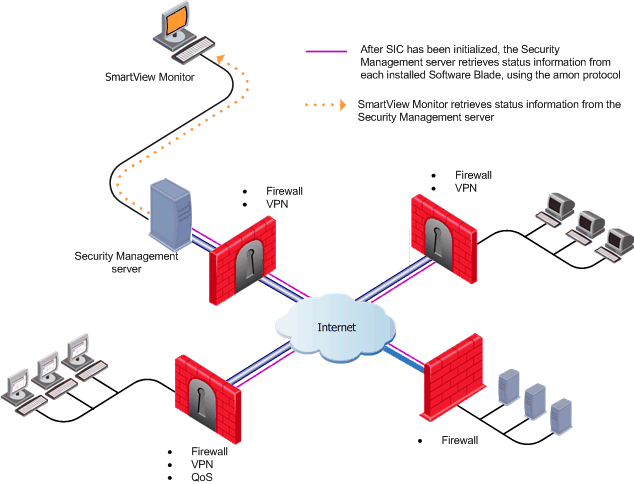
In the figure above information is retrieved by the Security Management server from all of the available Software Blades, using the AMON protocol, after SIC has been initialized.
How Does it Work?
The Security Management server acts as an AMON (Application Monitoring) client. It collects information about specific Check Point Software Blades installed, using the AMON protocol. Each Check Point gateway, or any other OPSEC gateway which runs an AMON server, acts as the AMON server itself. Each gateway makes a status update request, via APIs, from various other components such as:
- The "kernel"
- Security Servers
An alternate source for status collection may be any AMON client, such as an OPSEC partner, which uses the AMON protocol.
The information is fetched at a subscribed interval which is defined by the system administrator. The AMON protocol is SIC- based so information can be retrieved once SIC has been initialized.
Gateway Status
General statuses can occur on the Security Gateway or on the server on which a Check Point Software Blade is installed.
Overall Status
An Overall status is the result of the blades' statuses. The most serious Software Blades status determines the Overall status. For example, if all the Software Blades statuses are OK except for the SmartReporter blade, which has a Problem status, then the Overall status will be Problem.
Software Blade Status
Software Blades include components such as VPN, SmartReporter, Endpoint Security, and QoS.
 OK - indicates that the blade (for example, SmartReporter, VPN, Firewall, etc.) is working properly. OK - indicates that the blade (for example, SmartReporter, VPN, Firewall, etc.) is working properly. Attention - the blade indicates that there is a minor problem but it can still continue to work. Attention - the blade indicates that there is a minor problem but it can still continue to work. Problem - indicates that the blade reported a specific malfunction. To see details of this malfunction open the gateways status window associated with the blade by double-clicking it in the Gateways Status view Problem - indicates that the blade reported a specific malfunction. To see details of this malfunction open the gateways status window associated with the blade by double-clicking it in the Gateways Status view Waiting - displayed from the time that the view starts to run until the time that the first status message is received. This takes no more than thirty seconds. Waiting - displayed from the time that the view starts to run until the time that the first status message is received. This takes no more than thirty seconds. Disconnected - the gateway cannot be reached. Disconnected - the gateway cannot be reached. Untrusted - Secure Internal Communication failed. The gateway is connected, but the Security Management server is not the master of the gateway. Untrusted - Secure Internal Communication failed. The gateway is connected, but the Security Management server is not the master of the gateway.
Displaying Gateway Information
Gateways Status, information is displayed per Check Point or OPSEC gateway.
To display information about the gateway, click the specific gateway in the Gateway Results view. Details about the gateway will be displayed in the Gateway Details pane.
This information includes general information such as the name, IP Address, version, operating system, and the status of the specified gateway, as well as gateway specific information, such as:
System Information
- Unified Package - the version number.
- SO Information - the name, the version name/number, the build number, the service pack and any additional information about the Operating System in use.
- CPU - the specific CPU parameters (for example, Idle, User, Kernel and Total) for each CPU.
Note: In the Gateways Results view the Average CPU indicates the average total CPU usage of all existing CPOS. - Memory - the total amount of virtual memory, what percentage of this total is being used. The total amount of real memory, what percentage of this total is being used and the amount of real memory available for use.
- Disk - displays all the disk partitions and their specific details (for example, capacity, used and free).
Note: In the Gateways Results view the percentage/total of free space in the hard disk on which the firewall is installed. For example, if there are 2 hard drives C and D and the firewall is on C, the Disk Free percentage represents the free space in C and not D.
Firewall
- Policy information - the name of the Security Policy installed on the gateway and the date and time that this policy was installed.
- Packets - the number of packets accepted, dropped and logged by the gateway.
- UFP Cache performance - the hit ratio percentage as well as the total number of hits handled by the cache, the number of connections inspected by the UFP Server.
- Hash Kernel Memory (the memory status) and ystem Kernel Memory (the OS memory) - the total amount of memory allocated and used. The total amount of memory blocks used. The number of memory allocations, as well as those allocation operations which failed. The number of times that the memory allocation has freed up, or has failed to free up. The NAT Cache, including the total amount of hits and misses.
Virtual Private Networks
VPN is divided into three main statuses:
- Current represents the current number of active output.
- High Watermark represents the maximum number of current output
- Accumulative data which represents the total number of the output.
This includes:
- Active Tunnels - this includes all types of active VPN peers to which there is currently an open IPsec tunnel. This is useful for tracking the proximity to a VPN Net license and the activity level of the VPN gateway. High Watermark includes the maximum number of VPN peers for which there was an open IPsec tunnel since the gateway was restarted.
- RemoteAccess - this includes all types of RemoteAccess VPN users with which there is currently an open IPsec tunnel. This is useful for tracking the activity level and load patterns of VPN gateways serving as a remote access server. High Watermark includes the maximum number of RemoteAccess VPN users with which there was an open IPsec tunnel since the gateway was restarted.
- Tunnels Establishment Negotiation - The current rate of successful Phase I IKE Negotiations (measured in Negotiations per second). This is useful for tracking the activity level and load patterns of a VPN gateway serving as a remote access server. High Watermark includes the highest rate of successful Phase I IKE Negotiations since the Policy was installed (measured in Negotiations per second). In addition, accumulative data includes the total number of successful Phase I IKE negotiations since the Policy was installed.
- Failed - the current failure rate of Phase I IKE Negotiations can be used for troubleshooting, for instance, denial of service, or for a heavy load of VPN remote access connections. High Watermark includes the highest rate of failed Phase I IKE negotiations since the Policy was installed. And finally, Accumulative is the total number of failed Phase I IKE negotiations since the Policy was installed.
- Concurrent - the current number of concurrent IKE negotiations. This is useful for tracking the behavior of VPN connection initiation, especially in large deployments of remote access VPN scenarios. High Watermark includes the maximum number of concurrent IKE negotiations since the Policy was installed.
- Encrypted and Decrypted throughput - the current rate of encrypted/decrypted traffic (measured in Mbps). Encrypted/decrypted throughput is useful (in conjunction with encrypted/decrypted packet rate) for tracking VPN usage and VPN performance of the gateway. High Watermark includes the maximum rate of encrypted/decrypted traffic (measured in Mbps) since the gateway was restarted. And finally, Accumulative includes the total encrypted/decrypted traffic since the gateway was restarted (measured in Mbps).
- Encrypted and Decrypted packets - the current rate of encrypted/decrypted packets (measured in packets per second). Encrypted/decrypted packet rate is useful (in conjunction with encrypted/decrypted throughput) for tracking VPN usage and VPN performance of the gateway. High Watermark includes the maximum rate of encrypted/decrypted packets since the gateway was restarted. And finally, Accumulative, the total number of encrypted packets since the gateway was restarted.
- Encryption and Decryption errors - the current rate at which errors are encountered by the gateway (measured in errors per second). This is useful for troubleshooting VPN connectivity issues. High Watermark includes the maximum rate at which errors are encountered by the gateway (measured in errors per second) since the gateway was restarted. And finally, the total number of errors encountered by the gateway since the gateway was restarted.
- Hardware - the name of the VPN Accelerator Vendor, and the status of the Accelerator. General errors such as the current rate at which VPN Accelerator general errors are encountered by the gateway (measured in errors per second). The High Watermark includes the maximum rate at which VPN Accelerator general errors are encountered by the gateway (measured in errors per second) since the gateway was restarted. And finally the total number of VPN Accelerator general errors encountered by the gateway since it was restarted.
- IP Compression - Compressed/Decompressed packets statistics and errors.
QoS
- Policy information - the name of the QoS Policy and the date and time that it was installed.
- Number of interfaces - the number of interfaces on the Check Point QoS gateway. Information about the interfaces applies to both inbound and outbound traffic. This includes the maximum and average amount of bytes that pass per second, as well as, the total number of conversations, where conversations are active connections and connections that are anticipated as a result of prior inspection. Examples are data connections in FTP, and the "second half" of UDP connections.
- Packet and Byte information, the number of packets and bytes in Check Point QoS queues.
ClusterXL
- The gateway's working mode, whether or not it is active, and its place in the priority sequence. There are three possible working modes (ClusterXL/Load Sharing or Sync only). There are 4 types of running modes, (Active, standby, ready and down).
- Interfaces include the interface(s) recognized by the gateway. The interface information includes the IP Address and status of the specified interface. Whether or not the connection passing through the interface is verified, trusted or shared.
- Problem Notes contains descriptions of the problem notification device such as its status, priority and when the status was last verified.
OPSEC
- The version name/number and build number of the Check Point OPSEC SDK and OPSEC product. The amount of time (in seconds) since the OPSEC gateway has been up and running.
- The OPSEC vendor may add additional fields to their OPSEC Application gateway's details.
Check Point Security Management
- The synchronization status indicates the status of the peer Security Management servers in relation to that of the selected Security Management server. This status can be viewed in the Management High Availability Servers window, whether you are connected to the Active or Standby Security Management server. The possible synchronization statuses are:
- Never been synchronized - immediately after the Secondary Security Management server has been installed, it has not yet undergone the first manual synchronization that brings it up to date with the Primary Management.
- Synchronized - the peer is properly synchronized and has the same database information and installed Security Policy.
- Advanced - the Security Management server is more advanced than the standby server, it is more up-to-date.
- Lagging - the Security Management server has not been synchronized properly.
- Collision - the active Security Management server and its peer have different installed policies and databases. The administrator must perform manual synchronization and decide which of the Security Management servers to overwrite.
- Clients - the number of connected clients on the Security Management server, the name of the SmartConsole, the administrator responsible for administering the SmartConsole, the name of the SmartConsole host, the name of the locked database and the type of SmartConsole application, such as SmartDashboard, User Monitor etc.
UserAuthority WebAccess
- Plug-in Performance - the number of http requests accepted and rejected.
- Policy info - the name of the WebAccess policy and the last time that the policy was updated.
- UAS info - the name of the UA Server host, the IP Address and port number of the UAG Server. The number of requests sent to the UA Server and the time it took for the request to be handled.
- Global UA WebAccess - the number of currently open sessions and the time passed since the last session was opened.
SmartConsole Server
The number of licensed users who are currently connected.
Log Server
Indicates whether or not the Security Management server is active and the number of licensed users who are currently connected. The Log Server includes elaborate details about the named connected client, including, then name of the administrator, managing the selected Log Server, the host of the Log Server and the name of the database if it is locked. The Log Server also indicates the type of application that can be tracked by the Log Server.
Correlation Unit and SmartEvent
SmartView Monitor reads statuses from the SmartEvent Correlation Unit and SmartEvent server.
Correlation Unit status examples:
- is the SmartEvent Correlation Unit active or inactive
- is the SmartEvent Correlation Unit connected to the SmartEvent server
- is the SmartEvent Correlation Unit connected to the log server
- SmartEvent Correlation Unit and log server connection status
- offline job status
- lack of disk space status
SmartEvent Server status examples:
- last handle event time
- is the SmartEvent Server active or inactive
- a list of correlation units the SmartEvent Server is connected to
- how many events arrived in a specific time period.
The SmartEvent Correlation Unit should be connected to the log server(s) so that it can read logs. It also needs to be connected to the SmartEvent Server so that it can send events to it. If problems occur in the SmartEvent Correlation Unit Unit's connection to other components (for example, SIC problems) the problems are reported in the SmartEvent Correlation Unit Unit's status.
For the same reasons, the SmartEvent server contains statuses that provide information about its connect to all the SmartEvent Correlation Unit Unit(s) that it is currently connected to.
Anti-Virus and URL Filtering
SmartView Monitor can now provide statuses and counters for gateways with Anti-Virus and URL Filtering.
The statuses are divided into the following two categories:
- Current Status
- Update Status (for example, when was the signature update last checked)
Anti-Virus statuses are associated with signature checks and URL Filtering statuses are associated with URLs and categories.
In addition, SmartView Monitor can now run Anti-Virus and URL Filtering counters.
For example:
- Top five attacks in the last hour
- Top 10 attacks since last reset
- Top 10 http attacks in the last hour
- HTTP attacks general info
Multi-Domain Security Management
SmartView Monitor can now be used to monitor Multi-Domain Servers. This information can be viewed in the Gateway Status view. In this view it is now possible to view Multi-Domain Security Management counter information (for example CPU or Overall Status).
Views of a Specified Gateway
Gateways Status allows you to define views for specific gateways. From within a Gateway Status view it is possible to access information about the following:
- Monitor Tunnels - provides a list of Tunnels associated with the selected gateway. Tunnels are secure links between gateways that allow secure connections between gateways and remote access clients.
The option of viewing a list of tunnels associated with a specific gateway enable you to keep track of the tunnels normal function, so that possible malfunctions and connectivity problems can be accessed and solved as soon as possible.
For additional information about Tunnels refer to the Monitoring Tunnels chapter.
- Monitor Users - provides a list of Mobile Access users currently logged on to the specific Security Management servers. On the SmartView Monitor Gateways interface you will be able to view all the remote users currently logged on to specific Security Management servers.
- Monitor Traffic or System Counters - provides information about monitored and analyzed network traffic and network usage associated with the selected gateway. You can generate fully detailed or summarized graphs and charts for all connections intercepted and logged when monitoring traffic and for numerous rates and figures when counting usage throughout the network.
For additional information about Traffic or Counter refer to the Monitoring Traffic or System Counters chapter.
Interfering Actions
After reviewing the status of certain Clients, in SmartView Monitor, you may decide to take decisive action for a particular Client or Cluster Member, for instance:
- Disconnect client - if you have the correct permissions, you can choose to disconnect one or more of the connected SmartConsole clients.
- Start/Stop Cluster member - All Cluster Members of a given Gateway Cluster can be viewed via Gateways Status. You can start or stop a selected Cluster Member.
Thresholds
For each kind of Check Point Software Blade there is a set of status parameters that can be monitored. When the status of a blade is changed or when an event has occurred, predefined actions can be triggered. This is done by defining Thresholds (that is, limits) and actions to be taken if these Thresholds are reached or exceeded. To Define a Threshold refer to Defining a Threshold.
Alert Dialog
Alerts provide real-time information about vulnerabilities to computing systems and how they can be eliminated.
Check Point alerts users to potential threats to the security of their systems and provides information about how to avoid, minimize, or recover from the damage.
Alerts are sent by the gateways to the Security Management server. The Security Management server then forwards these alerts to SmartView Monitor, which is actively connected to the Security Management server.
Alerts are sent in order to draw the administrator's attention to problematic gateways, and are displayed in SmartView Monitor. These alerts are sent:
- If certain rules or attributes, which are set to be tracked as alerts, are matched by a passing connection,
- If system events, also called System Alerts, are configured to trigger an alert when various predefined thresholds are surpassed.
The administrator can define alerts to be sent for different gateways. These alerts are sent under certain conditions, for example, if they have been defined for certain policies, or if they have been set for different properties. By default an alert is sent as a pop-up message to the administrator's desktop when a new alert arrives to SmartView Monitor.
Alerts can also be sent for certain predefined system events. If certain predefined conditions are set, you can get an alert for certain critical situation updates. These are called System Alerts. For example, if free disk space is less than 10%, or if a security policy has been changed. System Alerts are characterized as follows:
- Defined per product: For instance, you may define certain System Alerts for Unified Package and other System Alerts for Check Point QoS.
- Global or per gateway: This means that you can set global alert parameters for all gateways in the system, or you can specify a particular action to be taken on alert on the level of every Check Point gateway.
- Displayed and viewed via the same user-friendly window.
SNMP Monitoring Thresholds
This release lets you configure a variety of SNMP Thresholds that generate SNMP traps, or alerts. You can use the thresholds to monitor many system components automatically without requesting information from each object or device. The categories of thresholds that you can configure include:
- Hardware
- High Availability
- Networking
- Resources
- Log Server Connectivity
Some categories apply only to some machines or deployments.
In each category are many individual thresholds that you can set. For example, the hardware category includes alerts for the state of the RAID disk, the state of the temperature sensor, the state of the fan speed sensor, and others. For each individual threshold, you can configure:
- If it is enabled or disabled
- How frequently alerts are sent
- The severity of the alert
- The threshold point (if necessary)
- Where the alerts are sent to
You can also configure some settings globally, such as how often alerts are send and where they are sent to.
Types of Alerts
There are two different types of alerts:
- Active alerts are sent when a threshold point is passed or the status of a monitored component is problematic.
- Clear alerts are sent when the problem is resolved and the component has returned to its normal value. Clear alerts look like active alerts but the severity is set to 0.
Configuring SNMP Monitoring
Configure the SNMP monitoring thresholds in the command line of the Security Management server. When you install the policy on the gateways the SNMP monitoring thresholds are applied globally to all gateways.
Configuring in Multi-Domain Security Management
In a Multi-Domain Security Management environment, you can configure thresholds on the Multi-Domain Server and on each individual Domain Management Server. Thresholds that you configure on the Multi-Domain Server are for the Multi-Domain Server only. Thresholds that you configure for a Domain Management Server are for that Domain Management Server and its gateways. If a threshold applies to the Multi-Domain Server and the Domain Management Server gateways, set it on the Multi-Domain Server and Domain Management Server. However, in this situation you might only get alerts from the Multi-Domain Server if the threshold is passed.
For example, because the Multi-Domain Server and Domain Management Server are on the same machine, if the CPU threshold is passed, it applies to both of them. However, only the Multi-Domain Server generates alerts.
You can see the for each threshold with the threshold_config utility.
- If the Multi-Domain Security Management level for a threshold is , alerts are generated for the Multi-Domain Server when the threshold point is passed.
- If the Multi-Domain Security Management level for a threshold is , alerts are generated for the Multi-Domain Server and Domain Management Servers separately when the threshold point is passed.
Configuring a Local Gateway Policy
You can configure SNMP thresholds locally on a gateway with the same procedure that you do on a Security Management server. However, each time you install a policy on the gateway, the local settings are erased and it reverts to the global SNMP threshold settings.
You can use the threshold_config utility to save the configuration file and load it again later. Or you can manually back up the configuration file so that you can copy the configuration to the gateway again after you install the policy.
On SecurePlatform and Linux, the configuration file that you can back up is: $FWDIR/conf/thresholds.conf
On Windows the configuration file that you can back up is: %FWDIR%\conf\thresholds.conf
Configuration Procedures
There is one primary command to configure the thresholds in the command line, threshold_config. You must be in expert mode to run it. After you run threshold_config, follow the on-screen instructions to make selections and configure the global settings and each threshold.
When you run threshold_config, you get these options:
- - Shows you the name configured for the threshold policy.
- - Lets you set a name for the threshold policy.
- - Lets you save the policy.
- - Lets you export the policy to a file.
- - Lets you import a threshold policy from a file.
- - Lets you configure global settings for how frequently alerts are sent and how many alerts are sent.
- - Lets you configure a location or locations where the SNMP alerts are sent.
- - Shows a list of all thresholds that you can set including: The category of the threshold, if it is active or disabled, the threshold point (if relevant), and a short description of what it monitors.
- - Open the list of threshold categories to let you select thresholds to configure.
Configure Global Alert Settings
If you select , you can configure global settings for how frequently alerts are sent and how many alerts are sent. You can also configure these settings for each threshold. If a threshold does not have its own alert settings, it uses the global settings by default.
You can configure these options:
- - How many alerts will be sent when an active alert is triggered. If you enter 0, alerts will be sent until the problem is fixed.
- - How long the system waits between sending active alerts.
- - How many clear alerts will be sent after a threshold returns to a normal value.
- - How long the system waits between sending clear alerts.
Configure Alert Destinations
If you select Configure Alert Destinations, you can add and remove destinations for where the alerts are sent. You can also see a list of the configured destinations. A destination is usually an NMS (Network Management System) or a Check Point log server.
After entering the details for a destination, the CLI asks if the destination should apply to all thresholds.
- If you enter , alerts for all thresholds are sent to that destination, unless you remove the destination from an individual threshold.
- If you enter , no alerts are sent to that destination by default. However, for each individual threshold, you can configure the destinations and you can add destinations that were not applied to all thresholds.
For each threshold, you can choose to which of the alert destinations its alerts are sent. If you do not define alert destination settings for a threshold, it sends alerts to all of the destinations that you applied to all thresholds.
For each alert destination enter:
- - An identifying name.
- - The IP address of the destination.
- - Through which port it is accessed
- - the version on SNMP that it uses
- - Some versions of SNMP require more data. Enter the data that is supplied for that SNMP version.
Configure Thresholds
If you select Configure thresholds, you see a list of the categories of thresholds, including:
- Hardware
- High Availability
- Networking
- Resources
- Log Server Connectivity
Some categories apply only to some machines or deployments. For example, Hardware applies only to Check Point appliances and High Availability applies only to clusters or high availability deployments.
Select a category to see the thresholds in it. Each threshold can have these options:
- - If the threshold is enabled, the system sends alerts when there is a problem. If it is disabled it does not generate alerts.
- - You can give each threshold a severity setting. The options are: Low, Medium, High, and Critical. The severity level shows in the alerts and in SmartView Monitor and lets you know quickly how important the alert is.
- - Set how frequently and how many alerts will be sent when the threshold is passed. If you do not configure this, it uses the global alert settings.
- - Enter the value that will cause active alerts when it is passed. Enter the number only, without a unit of measurement.
- - See all of the configured alert destinations. By default, active alerts and clear alerts are sent to the destinations. You can change this for each destination. Select the destination and you see these options:
- - If you select this, alerts for this threshold are not sent to the selected destination.
- - If you configured a destination in the global alert destinations but did not apply it to all thresholds, you can add it to the threshold.
- - If you select this, clear alerts for this threshold are not sent to the selected destination. Active alerts are sent.
Completing the Configuration
To complete threshold configuration and activate the settings:
- On the Security Management server, install the policy on all gateways.
- For a local gateway threshold policy or a Multi-Domain Security Management Multi-Domain Server environment, restart the CPD process using the
cpwd_admin utility:- Run: cpwd_admin stop -name CPD -path "$CPDIR/bin/cpd_admin" -command "cpd_admin stop"
- Run: cpwd_admin start -name CPD -path "$CPDIR/bin/cpd" -command "cpd"
Monitoring SNMP Thresholds
You can see an overview of the SNMP thresholds that you configure in SmartView Monitor.
To see an overview of the SNMP thresholds:
- Open SmartView Monitor and select a gateway.
- In the summary of the gateway data that open in the bottom pane, click .
- In the new pane that opens, click .
- In the pane that opens, you can see these details:
- - A summary of the total SNMP Threshold policy.
- - The name that you set for the policy in the CLI.
- - If the policy is enabled or disabled.
- - How many thresholds are enabled.
- - How many thresholds are currently sending alerts.
- - How many thresholds went from not active to active since the policy was installed.
- - Details for the thresholds that are currently sending alerts.
- - The name of the alert (given in the CLI)
- - The category of the alert (given in the CLI), for example, Hardware or Resources.
- - The name of the object as recorded in the MIB file.
- - The value of the object when the threshold became active, as recorded in the MIB file.
- - The current state of the object, either active or clearing (passed the threshold but is returning to normal value.
- - The severity of that threshold, as you configured for it in the CLI.
- - When the alert was first sent.
- - A list of the destinations that alerts are sent to.
- - The name of the location.
- - The type of location, for example, a log server or NMS.
- - If logs are being sent from the gateway or Security Management server to the destination machine.
- - How many alerts were sent to the destination from when the policy was started.
- - Shows thresholds that cannot be monitored. For example, the gateway cannot monitor RAID sensors on a machine that does not have RAID sensors. Therefore it will show an error for the RAID Sensor Threshold.
- - The name of the threshold with an error.
- - A description of the error.
- - When the error first occurred.
Configuring Gateway Views
The following pages contain a number of different sets of steps that will instruct you on how to work with SmartView Monitor Gateway Status views.
To obtain an explicit understanding about the fields, text boxes, drop-down lists, etc., in each window refer to SmartView Monitor Online Help.
Defining Status Fetch Frequency
Define the frequency at which status information will be gathered by the Security Management server from the Check Point gateways and sent to SmartView Monitor. This is referred to as the Status Fetching Interval, and it is defined in SmartDashboard > Global Properties > Log and Alert > Time Settings window. By default a status check takes place every 60 seconds.
Start/Stop Cluster Member
Select a specific Cluster Member of a given Gateway Cluster in the Gateways Status view. Right-click the Cluster Member and select Cluster Member > Start Member or Stop Member respectively.
Select and Run a Gateways View
When a Gateways Status view is run the results appear in the SmartView Monitor client. A Gateways Status view can be run:
- from an existing view
- by creating a new view
- by changing an existing view
In the SmartView Monitor client, click on an existing Gateways Status view. The view results (that is, a list of all the available gateways) appears in the Results View.
Refresh a Gateways Status View
The Gateways Status view is automatically refreshed every 60 seconds. To refresh the view earlier select the specific view in the Tree View, right-click and select Run.
To refresh information about a specific gateway in the currently running Gateways Status view, right-click the specific gateway line and select Refresh.
Run a Specific View at Startup
With SmartView Monitor you can select the view that will first appear when you launch SmartView Monitor.
- Right-click the view that should be run as soon as SmartView Monitor is launched.
- Select Run at Startup.
|
|

