

In This Section: |
The Security Management server consists of several databases with information on different aspects of the system, such as objects, users and policy information. This data changes each time the system administrator makes modifications to the system. It is important to maintain a backup for this data, so that crucial information is not permanently lost in the event of Security Management server failure.
Moreover, if the Security Management server fails or is down for administrative purposes, a backup server needs to be in place in order to take over its activities. In the absence of the Security Management server, essential operations performed by the gateways, such as the fetching of the Security Policy and the retrieval of the CRL, cannot take place.
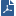
In Management High Availability, the Active Security Management server always has one or more backup Standby Security Management server which are ready to take over from the Active one. These Security Management servers must all be of the same operating system and version. The existence of the Standby Security Management server lets crucial backups be in place:
In a Management High Availability deployment, the first installed Security Management server is specified as the Primary Security Management server. This is a regular Security Management server used by the system administrator to manage the Security Policy. When any subsequent Security Management server is installed, these must be specified as Secondary Security Management servers. Once the Secondary Security Management server has been installed and manually synchronized, the distinctions between Primary versus Secondary are no longer significant. These servers are now referred to according to their role in the Management High Availability scenario as Active or Standby, where any Security Management server can function as the Active SMS.
The Management High Availability environment requires an Active SMS and at least one Standby SMS.
The Secondary SMS is created with empty databases. These databases are filled with information that the newly created Secondary SMS gleans from the Active SMS. The Secondary SMS is ready once:
It is possible to install a gateway on any of the Security Management servers. The role of these gateways is to protect the Security Management servers. Although the Security Management servers backup one another, High Availability is not implemented between the gateways installed on Security Management servers.
All management operations such as editing and installing the Security Policy and modifying users and objects, are done by the Active SMS. If the Active SMS is down, and any of the aforementioned operations need to be performed, one of the Standby SMSs should be made active by the system administrator. This transition from Standby to Active should be initiated manually.
The Standby SMSs are synchronized to the Active SMS, and therefore, are kept up to date with all changes in the databases and Security Policy. Thus Security Gateways can fetch the Security Policy and retrieve a CRL from both the Active SMS and the Standby SMS.
The frequency of the synchronization between the Standby SMS and the Active SMS is set by the System Administrator. This process can be configured to take place automatically, or it can be set to occur manually.
In order for Management High Availability to function properly, the following data must be synchronized and backed up:
|
Note - Previous versions of the Database, SmartMap data, as well as View Installed Policy data are not synchronized. |
There are two ways to perform synchronization:
The former option synchronizes quicker than the latter option. It should be the preferred mode of synchronization provided that the system administrator has edited the objects or the Security Policy, but has not installed the newly edited Security Policy since the previous synchronization.
Even when automatic synchronization has been selected as the synchronization mode, it is possible to perform a manual synchronization.
The synchronization status indicates the status of the peer SMSs in relation to that of the selected Security Management server. This status can be viewed in the Management High Availability Servers window or in SmartView Monitor, whether you are connected to the Active or Standby SMS.
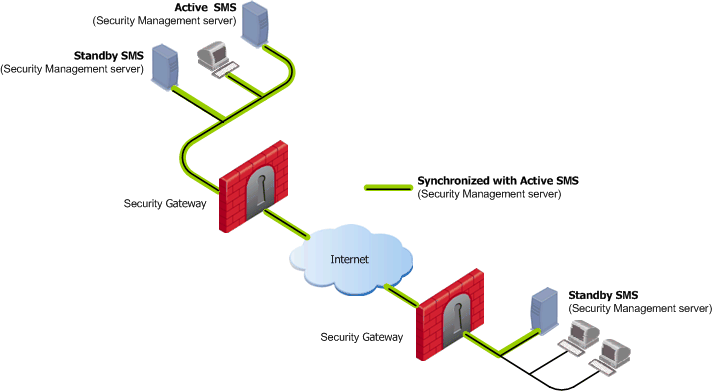
The possible synchronization statuses are:
For instance, on account of the fact that the Active SMS has undergone changes since the previous synchronization (objects have been edited, or the Security Policy has been newly installed), the information on the Standby SMS is lagging.
For instance, in the above figure, if a system administrators logs into Security Management server B before it has been synchronized with the Security Management server A, the status of the Security Management server A is Advanced, since it contains more up-to-date information which the former does not have.
In this case, manual synchronization must be initiated by the system administrator by changing the Active SMS to a Standby SMS. Perform a synch me operation from the more advanced server to the Standby SMS. Change the Standby SMS to the Active SMS.
For instance, in the above figure, when Security Management server A fails before a synchronization takes place, the changes made (to databases or to the Security Policy) cannot be synchronized with Security Management server B. When Security Management server B takes over from Security Management server A, the system administrator may decide to modify the Security Policy.
In this case, both Security Management server A and B have some information which is not synchronized with its peer. In order to remedy the collision state, one of the Security Management servers will need to be overwritten. The Security Management server which is found to have the dominant or significant changes should be the Security Management server on which manual synchronization is initiated.
At this point the system administrator needs to decide which of the Security Management server's should become the Standby SMS, and change its status, if necessary.
|
Note - Changes made by the CA, such as the issuance of certificates, could lead to breaches of security if they are overwritten; therefore, any CA changes that are made are merged in order to eliminate security issues. |
Although Security Gateways can use the Standby Security Management server to fetch a Security Policy or a fresh CRL, in the event that the Active one fails, the Standby Security Management server must become the Active one for two predominant reasons:
If the Active Security Management server is going down for administrative purposes, the system administrator should login to the Standby one and manually set it as the Active Security Management server.
Thereafter manual synchronization should be initiated. Once the Standby Security Management server has become Active, we recommend that you install the policy to make sure that this server is the Active Security Management server.
If the Active Security Management server is in failover, it is likely that the synchronization status of the Active Security Management server and its peer will be collision. In this case the system administrator will need to decide which information will be overwritten.
The status of all Security Management servers can be viewed in the Management High Availability Servers window in SmartDashboard or via SmartView Monitor.
Audit Logs can be used to view and track management operations as well as Synchronization operations in the SmartView Tracker.
There are several instances in which the synchronization process might fail:
When a collision occurs and one of the Security Management servers is overwritten, it is very useful to follow management operations performed on the overwritten Security Management server in the audit logs of the SmartView Tracker. In this manner it is possible to track and redo these operations, where necessary, on the dominant Security Management server.
In the Management High Availability deployment the Secondary Security Management server is often installed locally on the LAN. The system administrator should consider the usefulness of maintaining a remote Standby Security Management server. This remote Security Management server will not be affected in the case of networking problems on the LAN. This Standby Security Management server can be made into the Active Security Management server by the remote system administrator.
Automatic synchronization keeps the peer SMSs updated. However the synchronization may take some time and affect the system performance. It may be useful to schedule a synchronization event that automatically synchronizes the Security Management servers after working hours when the system performance cannot affect the regular work of the employees.
Manual synchronization can be initiated at any stage by the system administrator. Manual synchronization is recommended when changing the Standby SMS to Active (if the Active SMS is about to go down for administrative purposes). It is essential when the synchronization status is collision.
The data saved during the synchronization process is very heavy. Synchronization is optimized if the connectivity between the Security Management server is fast and efficient.
The Host General Properties window opens.
The Secondary and Active Security Management servers are synchronized.
If you suspect that the status of the Security Management server has changed, you may decide to do a refresh operation.
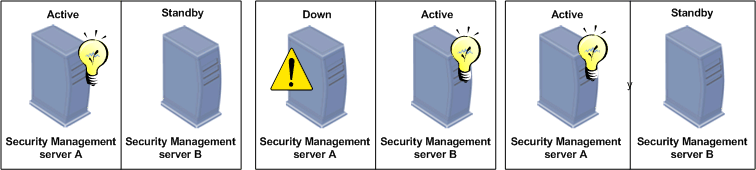
The manner in which the Standby Security Management server synchronizes with the Active Security Management server is defined in the Global Properties - Management High Availability window. This window is displayed by selecting Policy > Global Properties > Management High Availability. The Standby Security Management server can be synchronized automatically when the policy is installed, saved or on a specified scheduled event. Alternatively, the Standby Security Management server can be synchronized manually. If manual synchronization is the method of choice, the system administrator will need to initiate the manual synchronization in the Management High Availability Servers window. For more information, see Synchronization Modes.
The statuses of all the Security Management servers in the system are displayed in the Management High Availability window. This window is displayed by selecting Policy > Management High Availability. Details about the Security Management server and its peers that are displayed include the name, status and type of Security Management server.
All Management High Availability management operations can be viewed in the SmartView Tracker in Audit mode.