ISP Redundancy
Make Internet connectivity more reliable with ISP Redundancy. This connects a Security Gateway or cluster member to the Internet through redundant Internet Service Provider (ISP) links.
ISP Redundancy Modes
ISP Redundancy monitors the ISP links and chooses the best current link. You can configure this choice to be for Load Sharing or Primary/Backup.
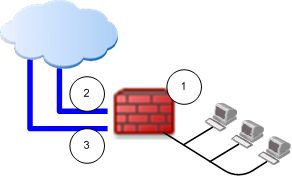
Item
|
Description
|
1
|
Security Gateway
|
2
|
Link A to the ISP
|
3
|
Link B to the ISP
|
ISP Redundancy monitors the links and directs the connection. You can configure this choice to be for Load Sharing or Primary/Backup.
- Load Sharing: Uses the two links with a distributed load of connections going out from the Security Gateway. Connections coming in are alternated. You can configure best relative loads for the links (set a faster link to handle more load). New connections are randomly assigned to a link. If one link fails, the other takes the load.
- Primary/Backup: Uses one link for connections going out from the Security Gateway and coming in. It switches to the backup if the primary link fails. When the primary link is restored, new connections are assigned to it. Existing connections continue on the backup link until they are complete.
SmartDashboard Toolbar
You can use the SmartDashboard toolbar to do these actions:
Icon
|
Description
|

|
Open the SmartDashboard menu. When instructed to select menu options, click this button to show the menu.
For example, if you are instructed to select > , click this button to open the Manage menu and then select the Users and Administrators option.
|

|
Save current policy and all system objects.
|

|
Open a policy package, which is a collection of policies saved together with the same name.
|

|
Refresh policy from the Security Management Server.
|

|
Open the Database Revision Control window.
|

|
Change global properties.
|

|
Verify rule base consistency.
|
|
Install the policy on Security Gateways or VSX Gateways.
|

|
Open SmartConsoles.
|
Configuring ISP Redundancy
If you configure VPN Link Selection settings on the Security Gateway, ISP Redundancy settings override them.
To enable ISP Redundancy:
- Open the network object properties of the Security Gateway or cluster.
- Click > .
- Select .
- Select or .
- Configure the links.
- Configure the Security Gateway to be the DNS server.
- Configure the policy for ISP Redundancy.
Configuring the ISP Links
Before you begin, make sure you have the ISP data - the speed of the link and next hop IP address. If the Security Gateway has only one external interface, configure two subnets on this interface. You will need routers and a switch.
If the Security Gateway has two external interfaces in the Topology page of the gateway object, you can configure the links automatically.
If the gateway is a ClusterXL cluster member, configure the two cluster members to the two ISPs. Use a LAN with two interfaces. Make sure the member interfaces are on the same subnet as the cluster external interfaces.
To configure ISP links automatically:
- In the ISP Redundancy page, click .
The ISP Links are added automatically.
- For , make sure the primary interface is first in the list. Use the arrows to change the order.
To configure ISP links manually:
- In the ISP Redundancy page, click .
- In the ISP Link window, give the link a name.
Note the names you give here. They are used in the ISP Redundancy script and commands.
- Select the of the Security Gateway for this ISP link.
- If the Security Gateway has two external interfaces, set each link to a different interface. If one of the ISP links is dialup connection to a backup ISP, configure the ISP Redundancy Script.
- If the Security Gateway has only one external interface, set each ISP link to connect to this interface.
- Configure the .
- If the Security Gateway has two external interfaces, leave this field empty and click . The next hop is the default gateway.
- If the Security Gateway has one external interface, set each ISP link to a different next hop router.
- For Load Sharing, enter the . For equal weight distribution, enter . If one link is faster, raise this value and lower it for the other link, so that the two equal 100.
- Define hosts to be monitored, to make sure the link is working. Open the tab of the window, and select hosts to add.
Configuring Security Gateway as DNS
The Security Gateway, or a DNS server behind it, must respond to DNS queries. It resolves IP addresses of servers in the DMZ (or another internal network).
Get a routable IP address from each ISP. If routable IP addresses are not available, register the domain to make the DNS server accessible from the Internet.
To enable DNS on the Security Gateway:
- Select .
The gateway intercepts Type A DNS queries for the web servers in its domain, that come from external hosts. If the Security Gateway recognizes the external host, it replies:
- In Load Sharing mode, the Security Gateway replies with two addresses, alternating their order.
- In Primary/Backup mode, the Security Gateway replies with the addresses of the active link.
If the Security Gateway does not recognize the host, it passes the DNS query on to the original destination or to the domain DNS server.
- Click .
- Add your DMZ or web servers. Give each two routable IP addresses, one for each ISP.
- Enter a number of seconds in .
This sets a Time To Live for each DNS reply. DNS servers in the Internet cannot cache your DNS data in the reply for longer than the TTL.
- Configure Static NAT to translate the routable addresses to the real server address. External clients use one of the two addresses.

|
Note - If the servers use different services (for example, HTTP and FTP), you can use NAT only for two routable IP addresses.
|
- Define a firewall rule: DNS traffic through the Security Gateway using the service.
To register the domain and get IP addresses:
- Register your domain with the two ISPs.
- Tell the ISPs the two addresses of the DNS server that respond to DNS queries for the domain.
- For each server in the DMZ, get two routable IP addresses, one from each ISP.
- In SmartDashboard, open Global Properties > and select - .
Configure the Firewall
The Firewall must allow connections through the ISP links, with Automatic Hide NAT on network objects that start outgoing connections.
To configure the firewall for ISP Redundancy:
- In the properties of the object for an internal network, select > .
- Select and .
- Click .
- Define rules for publicly reachable servers (web servers, DNS servers, DMZ servers).
If you have one routable IP address from each ISP for the Security Gateway, define Static NAT. Allow specific services for specific servers. For example, make rules so that incoming HTTP connections from the two ISPs reach a Web server, and DNS traffic from the ISPs reach the DNS server.
|
Original
|
|
|
Translated
|
|
Comment
|
Source
|
Destination
|
Service
|
Source
|
Destination
|
Serv.
|
|
Any
|
IP of web server
|
http
|
=
|
10.0.0.2 (Static)
|
=
|
Incoming Web - ISP A
|
Any
|
IP of web server
|
http
|
=
|
10.0.0.2 (Static)
|
=
|
Incoming Web - ISP B
|
Any
|
IP of DNS server
|
domain_udp
|
=
|
10.0.0.3 (Static)
|
=
|
Incoming DNS - ISP A
|
Any
|
IP of DNS server
|
domain_udp
|
=
|
10.0.0.3 (Static)
|
=
|
Incoming DNS - ISP B
|
If you have a routable address from each ISP for each publicly reachable server (in addition to the Security Gateway), define NAT rules:
- Give each server a non-routable address.
- Use the routable addresses in the Original Destination.
- Use the non-routable address in the Translated Destination.
- Select as the Original Service.

|
Note - If using Manual NAT, automatic arp does not work for the NATed addresses. On Linux and SecurePlatform use local.arp. On IPSO set up Proxy ARP.
|
When done, install the policy.
Configuring with VPN
When ISP Redundancy is enabled, VPN encrypted connections survive a failure of an ISP link. The settings in the ISP Redundancy page override settings in the Link Selection page.
To configure ISP Redundancy with VPN on one Security Gateway:
- In > , select .
- In > , see that shows the mode of the ISP Redundancy: or (for Primary/Backup).
Link Selection now only probes the ISPs configured in ISP Redundancy.
To configure for VPN with a third-party peer:
If the Security Gateway's peer is not a Check Point computer or appliance, the VPN may fail, or the third-party device may continue to encrypt traffic to a failed link.
- Make sure the device recognizes encrypted traffic from the secondary link as coming from the gateway.
- Change the configuration of ISP Redundancy to not use these Check Point technologies:
- - Make sure that uses another option.
- - Work only on Check Point Security Gateways. If used, the Security Gateway uses one link to connect to the third-party peer. The link with the highest prefix length and lowest metric is used.
Force ISP Link State
Use the fw isp_link command to force the ISP link state to Up or Down. Use this to test installation and deployment, or to force the Security Gateway to recognize the true link state if it cannot (the ISP link is down but the gateway sees it as up).
You can run this command on the Security Gateway or the Security Management Server: fw isp_link [target-gw] link-name up|down
The link_name is the name in the ISP Link window.
Editing the ISP Redundancy Script
When the Security Gateway starts, or an ISP link state changes, the $FWDIR/bin/cpisp_update script runs. It changes the default route of the Security Gateway. For example, you can force the Security Gateway to change the state of a dialup interface to match that state of its ISP link.
Edit this script to enable a dialup connection for one of the ISP links.
To configure dialup:
- In the script on the Security Gateway, enter the command to change the dialup interface state:
- If the link goes down:
fw isp_link link_name down - If the link goes up:
fw isp_link link_name up
- If you use PPPoE or PPTP xDSL modems, in the PPPoE or PPTP configuration of SecurePlatform, the Use Peer Gateway option must not be selected.
|
|

