Global Policy Management
The Need for Global Policies
Besides security policies for a specific set of Security Gateways, administrators need to create policies that apply to all or to a group of Domains. This separation between different levels of policies, and different types of policies, means that Domain-level security rules do not need to be reproduced throughout the entire Multi-Domain Security Management environment.
Security policies can be created and privately maintained for each Domain. Global policies enforce security for the entire Multi-Domain Security Management system or for a group of Domains.
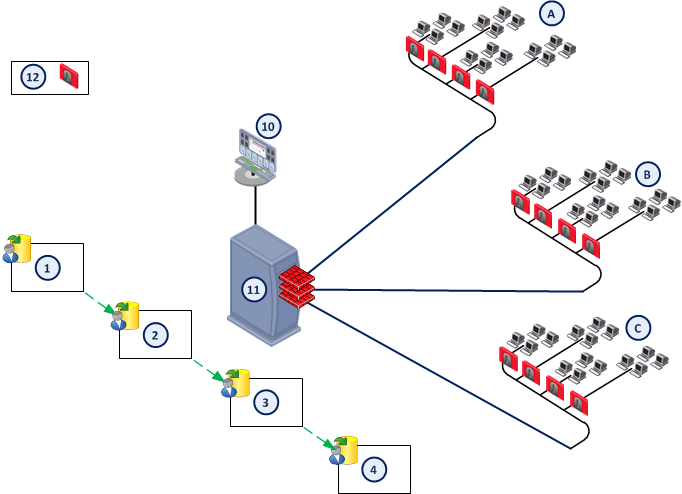
Item
|
Description
|
Step 1
|
Administrator creates or changes global policy
|
Step 2
|
Administrator assigns global policy to Domain
|
Step 3
|
Domain Management Server rule base inherits global policy rules
|
Step 4
|
Domain Management Server installs policy to Security Gateways
|
10
|
Network Operations Center
|
11
|
Multi-Domain Server
|
12
|
Security Gateway
|
A, B, C
|
Domain networks
|
The Global Policy as a Template
Security policies can be created and privately maintained per Domain. Some security rules need to be enforced for all Domains. Global policies can serve as security templates with rules that are applied to many Domains, and their individualized security policies.
Types of Global Policies can be designed for groups of Domains with similar security needs. This eliminates the need to recreate identical policies for each Domain. This feature greatly improves management efficiency. A service provider may use Global Policy rules to provide Domains with access to common MSP services but does not allow Domains to access private information about each other.
An MSP may provide several basic types of security policies. Rather than recreate the rule base for each new Domain, they can create a Global Policy for banks, a different Global Policy for independent dentists and therapists, and a Global Policy for small businesses, such as grocery stores, florists, gas stations or tax accountants.
An enterprise may use a Global Policy to set corporate wide policies. For example, an airline company with many branches and sales-offices, sales points and Domain check-in facilities may want to set rules for many different types of standard access needs. Rather than painstakingly recreating the same rule or set of rules for each branch, a global security policy can secure access across the board.
Global Policies and the Global Rule Base
Global policies are created using the global rule base, which contains a hierarchy of rules. In a Global Policy, you define common (global) rules, which are given priority in the rule base. These rules can be distributed (or assigned) to whichever Domains you choose. The Global Policy rule base is similar to the management rule base, except that it includes a demarcation or a "place holder" for Domain-specific rules.
The placeholder signifies that all the rules before and after it are global rules. The rule base layout is hierarchical: the most important global rules are highest up in the rule base. They take precedence over the Domain rules. Global rules that are designated as being of lower priority than Domain rules appear below the place holder.
The rules of the Global Policy are not specific to a single policy of single Domain, but apply to all Domains assigned the Global Policy.
Global rules can serve many uses. They can be used to rapidly implement defense against new cyber-attacks or viruses. They can be used to prevent logging for specific types of traffic in order to reduce the amount of information in log files. They can be used to set up rules for Domain Management Server communication management, such as allowing additional GUI Clients to be implemented at Domain sites.
Only one set of objects is used for all the Global Policies. The Global Policies database contains this set of objects, which can be used in any global rule in any Global Policy. The administrator creates these objects using Global SmartDashboard. Global Object icons are displayed with a purple G.
Global policies can be assigned to one or more Domains. Once Global Policies are assigned to a Domain Management Server, they become part of the Domain Management Server rule base. The entire Domain Management Server rule base, including assigned global rules, can then be installed onto selected Security Gateways.
Global SmartDashboard
Introduction to Global SmartDashboard
The Global SmartDashboard is used to maintain the Global Policy Rule Base. You use it to configure rules and network objects at the Multi-Domain Security Management system level.
SmartDashboard differs from Global SmartDashboard in that it operates only at the Domain level and below. After a Global Policy is assigned to a Domain, SmartDashboard for the Domain Management Server will show global rules automatically inserted either above or below editable Domain rules. The Domain administrator can create or edit Domain rules using SmartDashboard, and then install the Policy onto the Security Gateway.
When a Global Policy is assigned to a Domain, the global rules are read-only in the Domain SmartDashboard. Domain administrators cannot edit global rules or Global Objects from SmartDashboard.
Global Services
Default services defined by a Security Gateway are available for global use. Other services need to be defined. To avoid conflicts, make sure that you define services with unique names, which should not be the same as in the Domain Management Server databases.
Dynamic Objects and Dynamic Global Objects
Dynamic objects are generic network items such as a host or server object that has no IP specified. The administrator creates them in SmartDashboard, and uses them to create generic rules for Domain Security Gateways. At each Security Gateway, the dynamic object can be translated into a specific local computer, host or other network object, with an IP address.
Global rules may similarly use dynamic Global Objects, which are generic items (such as a web server) that can be applied to any network. Global objects are defined through the Global SmartDashboard and SmartDashboard are downloaded to the Domain Management Servers.
At the global level, an administrator defines dynamic Global Objects in addition to standard Global Objects which are available in the Global SmartDashboard. Once a Global Policy is assigned to a Domain, the dynamic global object is replaced by a corresponding Domain object. This makes it possible to create global rules without requiring that the rule use specific network objects. This allows the administrator to create rules that are "templates."
A dynamic global object serves as virtual place holder for a network element. The network element type can be anything that the administrator designates, including Security Gateways, hosts, or services, or even groups. A dynamic global object is created in the Global SmartDashboard with the suffix _global FTPserver_global
To "translate" the dynamic global object, the administrator creates an object in SmartDashboard with the same name, but with an IP address and other details. The Domain database substitutes the dynamic global object in the global rule with the local object from the Domain Management Server database. Alternatively, the dynamic global object is replaced with a Domain Management Server dynamic object, and the object is assigned an IP at the Security Gateway level.
To understand how the dynamic global object is used, let us consider an example. An administrator creates a global rule applying to a dynamic global object representing a generic ftp server. But instead of specifying exactly which ftp servers and their IP addresses will be affected by the rule, the servers are represented by a dynamic global object (FTPserver_global
In each Domain Management Server, the Domain administrator will define a host object with the same name. During the assignment of the Global Policy, the references to the global dynamic object in different rules will be replaced by the reference to the local host object with the same name. The _global syntax triggers the reference replacement mechanism.
Applying Global Rules to Security Gateways by Function
It is possible to create Security Rules in Global SmartDashboard that are installed on certain Security Gateways or groups of Security Gateways and not others. Thus Security Gateways with different functions on a single Domain Management Server can receive different security rules designed for a specific function or environment. When installing global policy to a number of similarly configured Domain Management Servers, the relevant global rules are installed to all of the relevant Security Gateways on each Domain Management Server.
This feature is particularly useful for enterprise deployments of Multi-Domain Security Management, where Domain Management Servers typically represent geographic subdivisions of an enterprise. For example, an enterprise deployment may have Domain Management Servers for business units in New York, Boston, and London, and each Domain Management Server will be similarly configured, with a Security Gateway (or Security Gateways) to protect a DMZ, and others to protect the perimeter. This capability allows an administrator to configure the global policy so that certain global security rules are installed to DMZ Security Gateways, wherever they exist, and different rules are installed to the perimeter Security Gateways.

|
Note - Global security rules can be installed on Security Gateways, Edge Security Gateways, SmartProvisioning Profiles, and Open Security Extension (OSE) devices.
|
To install a specific security rule on a certain Security Gateway or types of Security Gateways:
- Launch Global SmartDashboard for the relevant Global Policy.
- In the Objects Tree, right-click Dynamic Objects and select New Dynamic Object.
- Name the dynamic object, and add the suffix
_global - On the Firewall tab, create rules to be installed on Security Gateways with this function, and drag the dynamic object you created into the Install On column for each rule.
- Launch the SmartDashboard for each relevant Domain Management Server.
- Create a group object with the name of the dynamic object you created, including the suffix
_globalNote - While you can name a Security Gateway with the name of the global Dynamic Object, it is recommended to create a group to preserve future scalability (for instance, to include another Security Gateway with this function). It is not recommended to change the name of an existing Security Gateway to the dynamic object name.
- Add all Security Gateways on the Domain Management Server that you want to receive global security rules with this target to the group.
- Select File > Save.
- From the SmartDomain Manager, re-assign the global policy to the relevant Domains.
Synchronizing the Global Policy Database
The Global Policy database is synchronized on all Multi-Domain Servers automatically, or manually, depending on the settings. Global policies must be synchronized for the entire system, since they are system-wide security templates, and the entire system uses the same Global Objects. Synchronization is performed when the Global Policy is saved, or at a configurable interval.
Creating a Global Policy Using Global SmartDashboard
Global policies are created using the Global SmartDashboard. Domain policies are made using SmartDashboard launched using the Domain Management Server. Let us consider an MSP that wants to implement a rule which blocks unwanted services at Domain sites. The Multi-Domain Security Management Superuser, Carol, wants to set up a rule which will allows Domain administrators discretion to decide which computers are allowed to access the Internet.
Source
|
Destination
|
VPN
|
Service
|
Action
|
gInternetAccessAllowed_Global
|
Any
|
Any Traffic
|
Any
|
accept
|
Once she has created a Global Policy including this rule, she assigns/installs it for specific Domains and their Security Gateways. Each Domain administrator must create a group object with the same name as in the Domain Management Server database. This is done through SmartDashboard. In this way, local administrators translate the dynamic global object into sets of network object from the local database.
For details about using SmartDashboard, see the R76 Security Management Administration Guide. The differences between the SmartDashboard and the Global SmartDashboard are as follows:
|
|
|
|
Feature
|
Domain SmartDashboard
|
Global SmartDashboard
|
Rule Base
|
Local, applying to the Domain network only.
|
Global, applying to multiple networks of all Domains assigned this Global Policy.
|
|
Domain Security Rules and Global Rules (in Read Only mode) if the Global Policy is assigned to the Domain.
|
Global Rules and a place holder for Domain rules.
|
|
Not associated with the Domain other security policies.
|
Automatically added to all of the assigned security policies of Domains.
|
|
Each Domain policy is independent, with its own rules.
|
All the assigned Domain policies share the global rules.
|
Network Objects
|
Local to this network only.
|
Global to multiple networks of all Domains assigned this Global Policy.
|
Global Properties
|
Enabled.
|
Disabled (manipulations is through the Domain SmartDashboard).
|
Saving a Security Policy
|
Adds the security policy to the list of Domain security policies.
|
Adds the Global Policy to the Global Policies database (and displays it in the Global Policies Tree of the SmartDomain Manager).
|

|
Note - Global SmartDashboard cannot be used to create Connectra or Security Gateway objects. Instead, use a SmartDashboard connected to a specific Domain Management Server to create these objects.
|
Global IPS
Introduction to Global IPS
You can manage IPS protections for multiple Domains by including IPS profiles in Global Policies. You then assign a global policy to each Domain Management Server. You can include multiple IPS Profiles in a global policy. Administrators can assign any of the IPS profiles included in the global policy to specified Security Gateways managed by a Domain Management Server. Administrators can also make some limited changes to IPS profiles using the Domain Management Server SmartDashboard.

|
Important - If you manage an IPS Sensor using a global policy, you must activate sensor management in the Global SmartDashboard.
To activate sensor management in Global SmartDashboard:
- Select Policy > Global Properties > IPS.
- In the Global Properties pane, enable the Manage IPS-1 Sensors and IPS Software Blade option.
|
The global nature of Global IPS refers to the ability to set IPS Profiles for all subscribed Domains from the Global SmartDashboard. However, the Domain Management Server administrator for each Domain can assign different profiles to each Security Gateway and modify the IPS protections in certain ways once they have been installed. So in this case, the term global does not imply read only, as it does in the case of the Global Security Policy.
IPS in Global SmartDashboard
The Global IPS Policy is configured on the IPS tab in the Global SmartDashboard.
IPS protections available in the Global SmartDashboard are identical to the default settings and protections for a Domain Management Server. Any changes made to the Global Profiles apply to all Domain Management Servers subscribed to the IPS service.

|
Note - You must have an Enterprise Software Subscription to update IPS protections. Enterprise Software Subscriptions are available for purchase at the User Center.
|
IPS Profiles
An IPS Profile is a complete set of configured IPS protections that can be applied to multiple Security Gateways. On the Domain Management Server, multiple IPS Profiles can be assigned to suit Security Gateways that are exposed to different types of threats.
Global SmartDashboard supports multiple IPS Profiles. Changes made to IPS protections for a Global Profile are replicated when the Global Policy is assigned to Domain Management Servers that are subscribed to the IPS Service.
To learn more, see the R76 IPS Administration Guide.
Managing IPS Profiles
You manage IPS Profiles using the IPS tab in the Global SmartDashboard. Select Profiles from the Navigation Tree to view all Profiles and make changes.
Creating a New IPS Profile
To create a new IPS Profile:
- In SmartDashboard (Global or Domain Management Server), select the IPS tab.
- Select Profiles.
- Select New and either Create New Profile or Clone Selected Profile (to clone a profile, one must be selected).
- Enter a Profile Name and Comment. Select the IPS mode (Prevent or Detect) and a Protection Activation method.
Editing an IPS Profile
To edit an IPS Profile:
- In SmartDashboard (Global or Domain Management Server), select the IPS tab.
- Select Profiles.
- Double-click a profile.
- Edit parameters as required on any of the pages.
- On the Networks Exceptions page, add and edit exception rules by clicking New or Edit.
Subscribing Domains to IPS Service
Any Domain that you want to include in the global IPS policy must be subscribed to the IPS service.
To subscribe an existing Domain to the IPS Service:
- In the SmartDomain Manager, enable the Domain Contents Mode.
- On the Selection Bar, select General.
- Double-click a Domain name in the list.
- In the Domain Configuration window, select the Assign Global Policy tab.
- Enable the Subscribe Domain to IPS Service option.
Domains who subscribe to the IPS Service are automatically assigned to an Exclusive subscription. Once Domains are subscribed to the IPS service using the global policy, any changes made to the Global IPS Profiles are forwarded to the Domain Management Servers whenever Global Policy is assigned. See Assigning Global Policy for details.

|
Note - Merge and Override IPS subscriptions are no longer supported in Multi-Domain Security Management.
|
Managing IPS from a Domain Management Server
After Domains are assigned Global Policy, the IPS Profiles configured on the Global Dashboard are augmented to the local profiles list on the Domain Management Server. Domain administrators can assign IPS Profiles to Security Gateways and change these profiles in limited ways.
Protection settings for Global Profiles cannot be edited from the Domain Management Server. However, exceptions can be defined for specific traffic in the IPS tab of SmartDashboard.
Once a Profile has been downloaded to a Domain Management Server, there will be a 'G' prefix at the beginning of the Profile name and 'Global' appears in the activation column in the local SmartDashboard.
Any exceptions set globally for a specific Global Profile are indicated with a 'G' icon and cannot be changed from the Domain Management Server.
Assigning IPS Profiles to Security Gateways
IPS policy will not be activated on any Security Gateways until the Security Gateway is assigned a Profile.
To assign an IPS Profile to a Security Gateway:
- Navigate to the Profile Assignment page in one of two ways:
- From the Security Gateway object:
- In the SmartDashboard of the Domain Management Server on which the Security Gateway is managed, right-click the Security Gateway and select Edit.
- Select IPS from the navigation tree in the Security Gateway dialog box.
- From the IPS tab:
- In the SmartDashboard of the Domain Management Server on which the Security Gateway is managed, select the IPS tab and Enforcing Gateways from the navigation tree.
- Select a Security Gateway from the list and click Edit.
- Select Assign Profile and select a profile from the list, then click OK.
- If you do not want to apply IPS on the Security Gateway, select Do not apply IPS on this gateway.
- Select Policy > Install, and make sure the Security Gateway is selected in the Advanced Security column.
- Click OK to install policy and activate the assigned IPS Profile
Removing Global IPS from a Domain Management Server
To remove Global IPS from a Domain Management Server:
- In the IPS tab of the Domain Management Server SmartDashboard, make sure that Security Gateways on the Domain Management Server are not using Global Profiles.
- In the Global Policy page of the SmartDomain Manager, select a Domain, right-click, and select Configure Domain.
- In the tab, clear Subscribe to Domain IPS Service and click OK.
- In the Global Policy page, select the Domain again, right-click, and select Reassign Global Policy. Click OK to confirm.

|
Note - If you select Remove Global Policy, Global IPS will be removed from the Domain Management Server regardless of the check box setting.
|
Making Changes to an IPS Profile
Domain administrators can make exceptions to protections in a Profile and can override actions of a protection. These changes are made from the IPS tab of the Domain Management Server SmartDashboard by clicking Edit. See the R76 IPS Administration Guide to learn more.
If a Domain administrator makes changes to a profile, changes are saved in the Domain Management Server local policy. If the Profile is later altered in the Global SmartDashboard, the Domain administrator's changes will not be affected when Global Policy is reinstalled on the Domain Management Server.
Managing Global IPS Sensors
You can manage IPS sensors globally in a Multi-Domain Security Management deployment.
Assigning Global Policy
Global Policy, which includes the Global Security Policy and Global IPS, should be assigned to Domains when it is first configured, and whenever you want to implement a change. All Global Policy assign operations are performed from the Global Policies - Security Policies and IPS v global policy cannot be assignediew.
Assigning the First Global Policy
To assign a global policy for the first time:
- From the SmartDomain Manager view, select a Domain.
- To select local policies that use the global policy, click .
The window opens.
To assign the global policy to a local policy:
- Select the local policy in the list.
- Click .
The local policy moves to the list.To remove the global policy from a local policy:
- Select the local policy in the list.
- Click .
The local policy moves to the list.
Assigning Global Policies to VPN Communities
When assigning and/or reassigning global polices to VPN Communities, you should perform the following procedure to ensure that all participating Security Gateway domains update each other correctly.
To assign global policies to VPN Communities:
- Assign global policies to Domains.
- Using the Domain Management Server SmartDashboard for active Domains, install policies and/or databases as required.
- Reassign the global policy and install the most recent policy on all Security Gateways.
Re-assigning Global Policies
Whenever you make changes to a global policy, you must re-assign it to the appropriate Domain Management Servers. This ensures that global policy changes are reflected in individual Domain networks.
Automatic Security Gateway Policy Installation
When reassigning a global policy to Domain Management Servers, you can automatically re-install the last policy installed on individual Domain Management Server Security Gateways. This option ensures that changes made to the global policy are correctly updated at the Security Gateway level.
The term 'last policy installed' on a Security Gateway refers to the most recent version of the last policy installed on that Security Gateway using SmartDashboard.

|
Important - You cannot reassign global policies to any Security Gateway on which a policy was never installed (such as a new Security Gateway). Automatic policy installation will fail if no policy was previously installed on that Security Gateway.
To ensure that policy installation on a Security Gateway succeeds when re-assigning a global policy, you must first install a policy on that Security Gateway using the Domain Management Server SmartDashboard.
|
Re-assigning Global Policy to one Domain
To re-assign a Global Policy to an individual Domain Management Server:

|
Important Exception - If you reassign a global policy to a Domain that has one or more Security Gateways with no policy installed, global policy installation succeeds on those Security Gateways with an installed policy. The new global policy does not install on Security Gateways with no installed policy. This behavior occurs even when the Install Security Policy if it can be installed on all Security Gateways option is enabled.
This can result in some Security Gateways in a Domain enforcing the new global policy, while others continue to enforce the old (or no) global policy.
|
- From the Global Policy page in the SmartDomain Manager, right-click a Domain and select Reassign/Install Global Policy.
- In the Reassign/Install Global Policy window, enable the Reassign Global Policy option.
- To automatically install policies on Domain Security Gateways, select one or more Security Gateways from the list.
- Click OK to finish.
Re-assigning Global Policies to Many Different Domains
You can also reassign Global Policies to multiple Domains at the same time.

|
Important Exception - If you reassign a global policy to a Domain containing one or more Security Gateways with no installed policy, global policy installation succeeds on those Security Gateways with an installed policy. The new global policy does not install on Security Gateways with no installed policy. This occurs even when the Install Security Policy if it can be installed on all Security Gateways option is enabled.
This can result in some Security Gateways in a Domain enforcing the new global policy, while others continue to enforce the old (or no) global policy.
|
To reassign a policy to multiple Domains,
- From the Manage menu, select Reassign Global Policy and IPS to Domains.
- Select the Domains to receive this global policy.
- Enable the Install last Policy on all gateways of assigned Domains option, if you wish to automatically re-install the last policy installed on all Security Gateways belonging to the selected Domains.
Considerations for Global Policy Assignment
Introduction to Considerations for Global Policy Assignment
When assigning a Global Policy to one or more Domains, Global Objects are copied to the database of the Domain Management Server. Whether all the Global Objects in the database are copied, or only those related to the Global Policy, can be configured for each Domain in the Domain Configuration window, (which can be accessed by selecting Manage > Configure when selecting a Domain in the General-Domain Contents view).
Rules belonging to the Global Policy package being assigned are added above and below the rules inside ALL local policies defined in that Domain Management Server database.
When issuing the "install policy" command for Domain Management Server Security Gateways, the Security Gateways will receive the most updated Domain Management Server policy containing the latest updates from the Global Policy. Changes may be made to a Global Policy, after which the Global Policy is reassigned to one of more Domains. When a Domain Management Server then installs the updated policy to the Domain Security Gateways, any modifications to global and local objects/ rules are updated on the selected Security Gateways.
The assign and install procedure are two different processes. The administrator can re-assign a Global Policy without installing a local policy to Domain Security Gateways.
Assigning Policy for the First Time
Once you create a Domain internal network, you will want to create a policy for the Domain. The first step may be creating a Global Policy template for general use by different types of Domain. This allows you a certain amount of flexibility in how you manage security policy assignment.
Global policies are designed in Global SmartDashboard, but the assign/install procedure is handled through the SmartDomain Manager. The SmartDomain Manager provides a Global Policy Mode which gives you a few options to handle the procedure of assigning Global Policies. The Global Policy is assigned to the Domain Management Server.
When You Change a Global Policy
If you change the Global Policy, you must reassign it to all Domains using this policy, and reinstall it onto the Domain Security Gateways.
Re-install a Domain policy to Security Gateways when:
- You have made changes to a Global Policy and reassigned it to the Domain Management Server, without installing the updated policy to the Domain Security Gateways or,
- When you have made changes to the Domain network policy.
If you have network load considerations, rather than install the Security Gateways all at once, it can be better to do the procedure in stages. You can re-install a current policy to Domain Security Gateways using the Install Last Policy command. You can also install on selected Security Gateways by right clicking a Domain and selecting Reassign/Install Global Policy.
Assigning a Different Global Policy
To assign a different Global Policy to a Domain, use the same procedure as for initially assigning a Global Policy to a Domain. The Global Policy is overwritten when a new one is assigned.
Global Object Transfer Method
During Domain configuration, you define for each Domain how the Global Policy database will transfer objects during global security policy assignment (this is located in the Add Domain Wizard — Assign Global Policy tab). When Global Policies are assigned to Domain Management Servers, two methods can be used to transfer all the information to the Domain Management Server database from the Global Policy database.
It is possible to assign all Global Objects when assigning the Global Policy to a Domain Management Server. Or it is possible to assign only objects required by the rule base of the Global Policy assigned to the Domain Management Server. This includes objects directly or indirectly referenced by rules, such as network objects contained in groups. Indirectly references objects will also be copied to the Domain Management Server database, and the administrator will see them in both group and individually.
You can decide to change settings later, but be careful when changing settings. Consider the following scenario: a Domain assigns a Global Policy and transfers all the Global Objects. All objects are copied to the global database. When a Global Policy is re-assigned with just those objects relevant to the Global Policy assigned, extraneous objects not used by the Global Policy will be removed from the Domain configuration database. However, if these objects are used by a Domain network security rules or objects, the assignment operation will terminate (an error message lists the objects that prevented the operation from proceeding).
Viewing the Status of Global Policy Assignments
You can view global policy assignments from the SmartDomain Manager while in the Security Policies and IPS mode in the Global Policies view.
In this window, each Domain is displayed under the Global Security Policy to which it is assigned, or under the category No Global Policy. The time and date at which the Global Policy was assigned to each Domain is reported, and a status indicator shows whether that assignment is the most up-to-date version of the Global Policy.
When a change is made in Global SmartDashboard, either to a Global Security Policy or to the Global IPS, the change will be reflected in the Global Policy state of each Domain assigned the relevant Policy. (A green check mark indicates that the Policy is up-to-date, while a red exclamation mark indicates that since the Policy was assigned, it has changed, and should be reassigned.)
Global Policy History File
Each Domain log directory includes a history file (named gpolicy.log
Configuration
Assigning or Installing a Global Policy
To assign, reassign, install or remove policies for Domains, you must be a Superuser (either a Domain Superuser or a Multi-Domain Security Management Superuser. All these actions are performed in the SmartDomain Manager, using the Global Policies view.
You cannot assign a Global Policy to a Domain if a Read/Write SmartDashboard is logged in to the Domain Management Server. First, close SmartDashboard and then assign the Global Policy. You can, however, assign a Global Policy to a Domain if there is a Read Only SmartDashboard logged in to the Domain Management Server. The changes won't be displayed in SmartDashboard until it is disconnected from and then reconnected to the Domain Management Server.
Assign to Many Domains: How to Assign/Install from a Global Policy Object
To Assign/Install from a Global Policy Object
Use the following method to create a Global Policy, then assign it to several Domains at once. You can also install a policy to all Domain Security Gateways at the same time. If a Domain already has a different Global Policy, it is overwritten.
- Select the desired Global Policy. Right-click the Global Policy and choose Assign/Install Global Policy from the options menu. Select the Global Policy Name of the Global Policy you want to install (for example, Standard_Global_Policy).
- Select the Domains to which you want to assign this Global Policy from the Unassigned to selected Policy list. To install the policy on all the Security Gateways of the Domains to which the policy is assigned, check Install Policy on assigned Domains.
To install a policy on specific Security Gateways, perform the assign/install operation using the Domain object and select the specific Security Gateways on which to install the policy.
- Click OK. A Global Policy Assignment progress window lets you follow each step of the procedure, as the Global Policy is enforced on the selected Domain Management Servers. You can track installation attempts using the History file.
Assign to One Domain: Assign/Install from a Domain Object
To Assign/Install from a Domain Object:
Select a Domain that does not have a Global Policy, and assign one of the Global Policies you have created. This method gives you more control over the installation procedure for particular Domain Security Gateways.
For Domains that already have a Global Policy, the option will be to Reassign/Install Global Policy.
- Select a Domain, then choose Manage > Assign/Install Global Policy, or right-click the Domain and select Assign/Install Global Policy.
The Assign/Install Global Policy window lets you select a policy to be installed.
- Select one or more Security Gateways. A policy must already have been installed on the Security Gateways, or the operation will not work.
- Click OK.
The Global Policy is assigned to the Domain Management Server and the Domain policy is re-installed on the selected Security Gateways.
Reassigning/Installing a Global Policy on Domains
Once a Domain has been assigned a Global Policy, it is possible to update the policy by re-assigning it.
Reassigning/Installing a Global Policy to a Specified Domain
When performing a Reassign/Install the user does not choose the Policy. The Policy is already selected. You can also re-install the Domain Policy to the Security Gateways at the same time, but note that this is for all the Security Gateways at once and will only work if there is already a Domain Policy resident on the Security Gateway.
To reassign or install a global Policy to a specified Domain:
- Select a Domain, then choose Manage > Reassign/Install Global Policy, or right-click the Domain and select Reassign/Install Global Policy.
The Reassign/Install Global Policy window will display the Policy currently installed.
- Select the specific Security Gateways for which to re-install the Policy.
- Click OK.
The Global Policy is assigned to the Domain Management Server and the resident Domain Policy is re-installed on the selected Security Gateways.
Reassigning/Installing a Global Policy to Multiple Domains
reassign or install a global policy to multiple Domains:
- Right-click a Global Policy and select Reassign/Install Global Policy from the options menu.
- In the Reassign/Install Global Policy window, select on or more Domains.
- Enable the Install last Policy on all Gateways of assigned Domains option, if you wish to automatically reinstall the last policy installed on all Security Gateways belonging to the selected Domains.
- Enable the Install last IPS Sensor Policy on all IPS-1 Sensors of assigned Domains option, if you wish to automatically re-install the last policy on all IPS-1 sensors belonging to the selected Domain.
Reinstalling a Domain Policy on Domain Gateways
The Install Last Policy window allows you to select a group of Domains and re-install policies onto their Security Gateways. You can use this method only if the selected Security Gateways already have a policy installed.
To Reinstall a Domain Policy on Domain gateways:
- From the Manage menu, click Reassign Global Policy and IPS to Domains.
(Or click the Reassign Global Policy toolbar icon.) - In the Install Last Policy window, select the Domains to re-assign this global policy.
- Click Install last Policy on all gateways of assigned Domains, to automatically re-install the last policy installed on all Security Gateways belonging to the selected Domains.
- Click Install last IPS Sensor Policy on all IPS-1 Sensors of assigned Domains, to automatically re-install the last policy on all IPS-1 sensors belonging to the selected Domain.
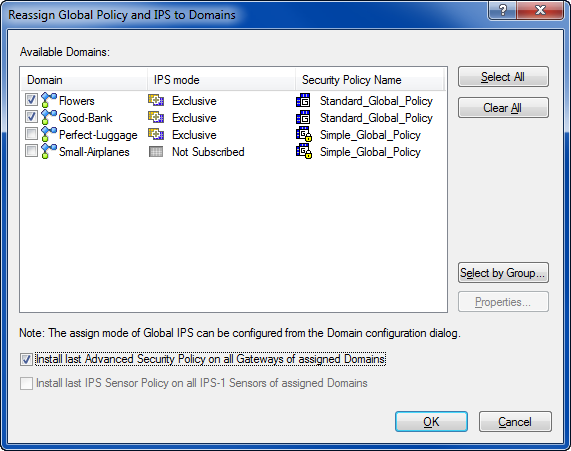
The policy is installed on all Security Gateways for selected Domains.
Remove a Global Policy from Multiple Domains
- Select the Global Policy and choose Manage > Remove Global Policy from Domains..., or right-click the policy and select Remove Global Policy from Domains... from the right-click menu.
- Check Domains in the Assigned to selected Policy list. To remove the policy from all Domains, click Select All. Domains from which the Global Policy has been removed are automatically assigned to the No Global Policy group.
Remove a Global Policy from a Single Domain
To remove a Global Policy from only single Domain:
- Select the Domain and right-click and choose Manage > Remove Global Policy, or choose Remove Global Policy from the Manage.
- You are asked whether you are sure you want to remove this Domain from the Global Policy. Click Yes to confirm. The Domain is automatically assigned to No_Global_Policy.
Viewing the Domain Global Policy History File
To view the Domain history file, select a Domain, right-click and choose View History File..., or from the Manage, select View History File.
Setting Policy Management Options
These options control system behavior when assigning global policies to Domain Management Servers and installing local policies on Domain network objects.
You can limit the number of Domains on which you do policy operations at the same time. This limit helps you prevent network congestion and excessive resource consumption during these operations. For example, if there are 5 Domains in your deployment and the defined maximum is 2, policy operations run in this sequence:
- The policy operation runs on the first two Domain Management Servers.
- The policy operation runs on the third and fourth Domain Management Servers.
- The policy operation runs on the last Domain Management Server.
You can also define what occurs if policy installation is not successful on some network objects or Security Cluster members, but is successful on others. These options can make sure that all network objects and Security Cluster members enforce the correct policy.

|
Important Exception - If you assign a global policy to a Domain Management Server where one or more Security Gateways do not have an installed policy:
- The local policy installation succeeds on those Security Gateways with an installed policy.
- The global policy does not install on Security Gateways with no installed policy.
- Some Security Gateways in this Domain will enforce the new local policy, while others enforce the old (or no) local policy.
This problem occurs if you select the option.
|
To configure policy management options:
- From the menu, select .
- In the window, select .
- Set the maximum number of domains on which you can do policy operations at the same time.
- Define what behavior occurs when policy installation fails on some Security Gateways and is successful on others:
Selected - Policy does not install on Security Gateways unless it successfully installs on all Security Gateways.
Cleared (Default) - Policy installs successfully on some Security Gateways, but not on others.
- Define what behavior occurs when policy installation fails on some Security Cluster members but is successful on others:
Selected (Default) - The policy does not install on members unless it successfully installs on all members.
Cleared - The policy installs successfully on some members, but not on others.
Global Names Format
The > menu > window lets users define a template for . This template is comprised of the original Security Gateway name, Domain name and other details. When defining Security Gateways for Global Use, the system gives you an automatic suggestion for a name, based on this template.
The properties are:
|



