Deployment Options
There are different deployment scenarios for Check Point software products.
- - The Security Management Server and the Security Gateway are installed on the same computer or appliance.

|
Item
|
Description
|
1
|
Standalone computer
|

|
Security Gateway component
|

|
Security Management Server component
|
- - The Security Gateway and the Security Management Server are installed on different computers or appliances.
|
|
Item
|
Description
|
1
|
Security Management Server
|
2
|
Network connection
|
3
|
Security Gateway
|

|
Security Gateway component
|

|
Security Management Server component
|
- - Security Management server and Security Gateway are each installed on one appliance, and two appliances work in High Availability mode.

|
Item
|
Description
|
1
|
Primary appliance
|
2
|
Direct appliance to appliance connection
|
3
|
Backup appliance
|

|
Security Gateway component
|

|
Security Management Server component
|
- - Add a Security Gateway to an existing environment without changing IP Routing.
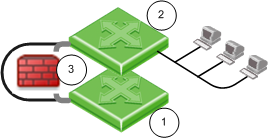
|
Item
|
Description
|
1 and 2
|
Switches
|

|
Security Gateway Firewall bridging Layer-2 traffic over the one IP address, with a subnet on each side using the same address.
|
- - A Primary and Secondary Security Management server are configured. The databases of the Security Management servers are synchronized, either manually or on a schedule, so they can back up one another. The administrator makes one Security Management server Active and the other(s) Standby. If the Active Security Management server is down, the administrator can make the Standby server Active.
|
|
|
|

|
Item
|
Description
|
1
|
Primary Security Management server
|
2
|
Direct or indirect Security Management server to Security Management server connection
|
3
|
Secondary Security Management server
|
|

|
Security Management Server component
|
|
|

