UserCheck Client
UserCheck Client Overview
The UserCheck client is installed on endpoint computers to communicate with the gateway and show UserCheck interaction notifications to users. It works with these Software Blades:
- Notifications of DLP incidents can be sent by email (for SMTP traffic) or shown in a popup from the UserCheck client in the system tray (for SMTP, HTTP and FTP).
- The UserCheck client adds the option to send notifications for applications that are not in a web browser, such as Skype, iTunes, or browser add-ons (such as radio toolbars). The UserCheck client can also work together with the UserCheck portal to show notifications on the computer itself when:
- The notification cannot be displayed in a browser, or
- The UserCheck engine determines that the notification will not be shown correctly in the browser and the for the UserCheck object is .
Users select an option in the notification message to respond in real-time.
For DLP, administrators with full permissions or the View/Release/Discard DLP messages permission can also send or discard incidents from SmartView Tracker.
Workflow for installing and configuring UserCheck clients:
- Configure how the clients communicate with the gateway and create trust with it.
- Enable UserCheck and the UserCheck client on the gateway.
- Download the UserCheck client MSI file.
- Install the UserCheck client on the endpoint computers.
- Make sure that the UserCheck clients can connect to the gateway and receive notifications.
UserCheck Requirements
See UserCheck Client Requirements in the R76 Release Notes.
Enabling UserCheck Client
Enable UserCheck and the UserCheck client on the gateway in the Properties window of the gateway object in SmartDashboard. This is necessary to let clients communicate with the gateway.
To enable UserCheck and the UserCheck client on the gateway:
- In SmartDashboard, open the window of the gateway object.
- If Data Loss Prevention is enabled on the gateway, select from the tree. In the area:
- Select . This enables UserCheck notifications from the client.
- Optional: Select . When selected, DLP email notifications also contain a link to download the UserCheck client directly from the email.
- If Application and URL Filtering is enabled on the gateway, select UserCheck from the tree:
- Select . This enables UserCheck notifications from the gateway.
- In the UserCheck Client area, select . This enables UserCheck notifications from the client.
- Click .
- Install the policy on the gateway.
Client and Gateway Communication
In an environment with UserCheck clients, the gateway acts as a server for the clients. Each client must be able to discover the server and create trust with it.
To create trust, the client makes sure that the server is the correct one. It compares the server fingerprint calculated during the SSL handshake with the expected fingerprint. If the server does not have the expected fingerprint, the client asks the user to manually confirm that the server is correct.
Here is a summary of the methods that you can use for clients to discover and trust the server. More details are described later in this section.
- File name based server configuration – If no other method is configured (default, out-of-the-box situation), all UserCheck clients downloaded from the portal are renamed to have the portal machine IP address in the filename. During installation, the client uses this IP address to connect to the gateway. Note that the user has to click to manually trust the server.
- AD based configuration – If client computers are members of an Active Directory domain, you can deploy the server addresses and trust data using a dedicated tool.
- DNS SRV record based server discovery – Configure the server addresses in the DNS server. Note that the user has to click to manually trust the server.
- Remote registry – All of the client configuration, including the server addresses and trust data reside in the registry. You can deploy the values before installing the client (by GPO, or any other system that lets you control the registry remotely). This lets you use the configuration when the client is first installed.
Option Comparison
|
Requires AD
|
Manual User Trust (one time) Required?
|
Multi-
Site
|
Client Remains Signed?
|
Still works after Gateway Changes
|
Level
|
Recommended for...
|
|
|
No
|
Yes
|
No
|
Yes
|
No
|
Very Simple
|
Single Security Gateway deployments
|
|
|
Yes
|
No
|
Yes
|
Yes
|
Yes
|
Simple
|
Deployments with AD that you can modify
|
|
|
No
|
Yes
|
Partially (per DNS server)
|
Yes
|
Yes
|
Simple
|
Deployments without AD
With an AD you cannot change, and a DNS that you can change
|
|
|
No
|
No
|
Yes
|
Yes
|
Yes
|
Moderate
|
Where remote registry is used for other purposes
|
File Name Based Server Discovery
This option is the easiest to deploy, and works out-of-the-box. It requires that users manually click to trust the server the first time they connect. You can use this option if your deployment has only one Security Gateway with the relevant Software Blades.
How does it work?
When a user downloads the UserCheck client from UserCheck notification, the address of the Security Gateway is inserted into the file name. During the installation sequence, the client checks if there is any other discovery method configured (AD based, DNS based, or local registry). If no method is configured and the gateway can be reached, it is used as the server. In the UserCheck Settings window, you can see that the server you connect to is the same as the Security Gateway in the UserCheck client filename.
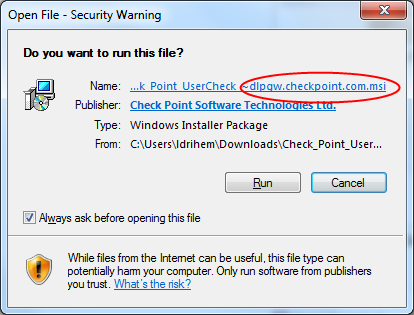
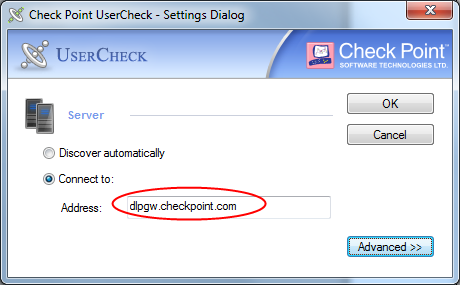
Users must manually make sure that the trust data is valid because the file name can easily be changed.
Renaming the MSI
You can manually change the name of the MSI file before it is installed on a computer so that it connects to different gateway.
To rename the MSI file:
- Make sure the gateway has a DNS name.
- Rename the MSI using this syntax: UserCheck_~GWname.msi
Where GWname - is the DNS name of the gateway.
Optional: Use UserCheck_~GWname-port.msi
Where port is the port number of notifications. For example, UserCheck_~mygw-18300.msi.

|
Notes - The prefix does not have to be "UserCheck". The important part of the syntax is underscore tilde (_~), which indicates that the next string is the DNS of the gateway.
If you want to add the port number for the notifications to the client from the gateway, the hyphen (-) indicates that the next string is the port number.
|
Active Directory Based Configuration
If your client computers are members of an Active Directory domain and you have administrative access to this domain, you can use the Distributed Configuration tool to configure connectivity and trust rules.
The Distributed Configuration tool has three windows:
- - Describes the tool and lets you enter different credentials that are used to access the AD.
- – Configure which Security Gateway the client connects to, based on its location.
- – View and change the list of fingerprints that the Security Gateways consider secure.
To enable Active Directory based configuration for clients:
- Download and install the UserCheck client MSI on a computer.
From the command line on that computer, run the client configuration tool with the AD utility.
For example, on a Windows 7 computer:
"C:\Users\<user name>\Local Settings\Application Data\Checkpoint\UserCheck\UserCheck.exe" -adtool
The Check Point UserCheck - Distributed Configuration tool opens.
- In the page, enter the credentials of an AD administrator.
By default, your AD username is shown. If you do not have administrator permissions, click and enter administrator credentials.
- In the page, click .
The window opens.
- Select and then click
- Enter the IP address or Fully Qualified Domain Name (FQDN) and the port for the AD Server.
- Click .
The identity of the AD Server for the UserCheck client is written in the Active Directory and given to all clients.

|
Note - The entire configuration is written under a hive named under the branch in the AD database that is added in the first run of the tool. Adding this hive does not affect other AD based applications or features.
|
Server Configuration Rules
If you use the Distributed Configuration tool and you configure the client to the server, the client fetches the rule lists. Each time it must connect to a server, it tries to match itself against a rule, from top to bottom.
When the tool matches a rule, it uses the servers shown in the rule, according to the priority specified.
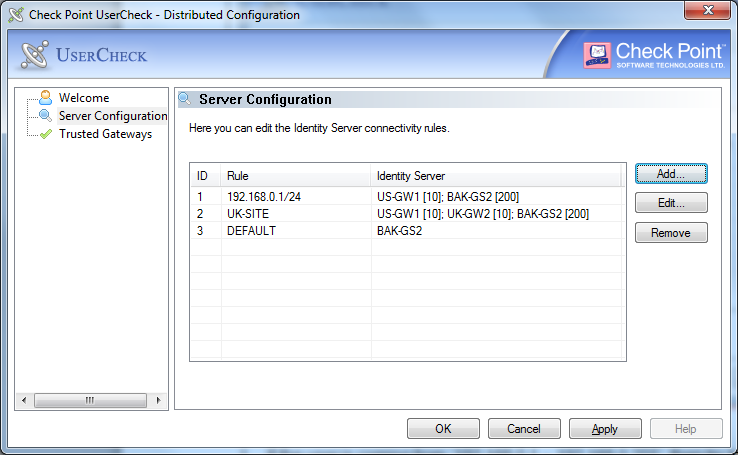
The configuration in this example means:
- If the user is coming from
‘192.168.0.1 – 192.168.0.255’US-GW1BAK-GS2US-GW1 - If the user is connected from the Active Directory site
‘UK-SITE’UK-GW1UK-GW2BAK-GS2 - If rules 1 and 2 do not apply, connect to
BAK-GS2
Use the , and buttons to change the server connectivity rules.
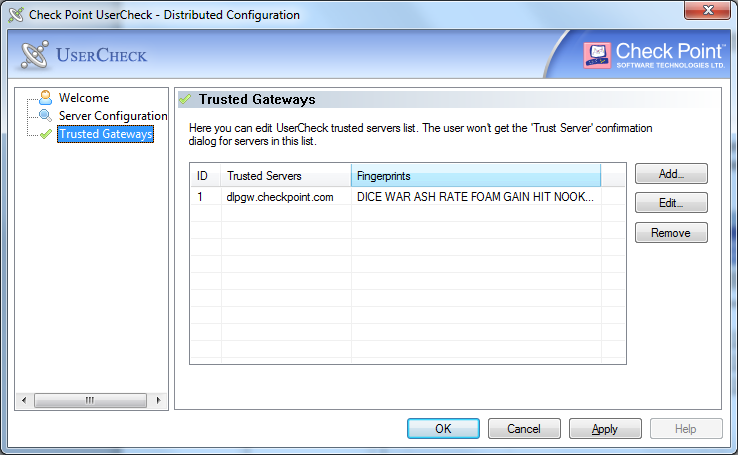
Trusted Gateways
The window shows the list of servers that are trusted - no messages open when users connect to them.
You can add, edit or delete a server. If you have connectivity to the server, you can get the name and fingerprint. Enter its IP address and click in the window. If you do not have connectivity to the server, enter the same name and fingerprint that is shown when you connect to that server.
DNS Based Configuration
If you configure the client to (the default), it looks for a server by issuing a DNS SRV query for the address of the gateway (the DNS suffix is added automatically). You can configure the address in your DNS server.
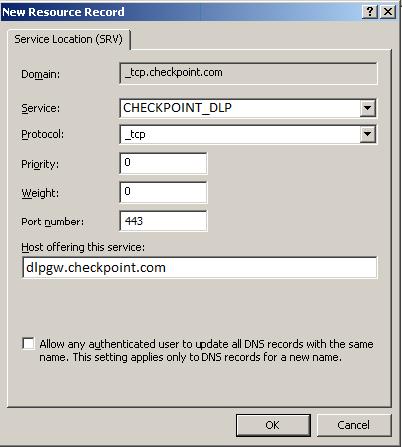
To configure DNS based configuration on the DNS server:
- Go to > > > .
- Go to and select the applicable domain.
- Go to the subdomain.
- Right click and select .
- Select , .
- In the field, enter .
- Set the to 443.
- In , enter the IP address of the Security Gateway.
- Click .

|
Note - To configure load sharing for the Security Gateway create multiple SRV records with the same priority. To configure High Availability, create multiple SRV records with different priorities.
|

|
Note - If you configure AD based and DNS based configuration, the results are combined according to the specified priority (from the lowest to highest).
|
Troubleshooting DNS Based Configuration
To troubleshoot issues in DNS based configuration, you can see the SRV records that are stored on the DNS server.
To see SRV records on the DNS server:
Run:
C:\> nslookup
> set type=srv
> checkpoint_dlp._tcp
The result is:
C:\> nslookup
> set type=srv
> checkpoint_dlp._tcp
Server: dns.company.com
Address: 192.168.0.17
checkpoint_dlp._tcp.ad.company.com SRV service location:
priority = 0
weight = 0
port = 443
svr hostname = dlpserver.company.com
dlpserver.company.com internet address = 192.168.1.212
>
|
Remote Registry
If you have a way to deploy registry entries to your client computers, for example, Active Directory or GPO updates, you can deploy the Security Gateway addresses and trust parameters before you install the clients. Clients can then use the deployed settings immediately after installation.
To configure the remote registry option:
- Install the client on one of your computers. The agent installs itself in the user directory, and saves its configuration to
HKEY_CURRENT_USER - Connect manually to all of the servers that are configured, verify their fingerprints, and click on the fingerprint verification dialog box.
- Configure the client to manually connect to the requested servers (use the window).
- Export these registry keys (from
HKEY_CURRENT_USER- SOFTWARE\CheckPoint\UserCheck\TrustedGateways (the entire tree)
- SOFTWARE\CheckPoint\UserCheck\
DefaultGatewayDefaultGatewayEnabled
- Import the exported keys to the endpoint computers before you install the UserCheck client.
Getting the MSI File
Use the Check_Point_UserCheck.MSI file to install the client on user computers. Each UserCheck client must be configured to connect to the gateway and to use the port needed for notifications. The default ports are 443 and 80. Download the MSI file from the Security Gateway through the Properties window of the gateway object in SmartDashboard. The MSI file is available after the first time that Policy is installed on the Security Gateway.
To get the MSI file:
- In SmartDashboard, open the window of the gateway object.
- If Data Loss Prevention is enabled on the gateway, select .
- If Application and URL Filtering is enabled on the gateway, select
If DLP and Application and URL Filtering are enabled on the Security Gateway, you can get the MSI file from the page or the page.

|
Important - Before you can download the client msi file, the UserCheck portal must be up. The portal is up only after a Policy installation.
|
Distributing and Connecting Clients
After configuring the clients to connect to the gateway, install the clients on the user machines. You can use any method of MSI or EXE mass deployment and installation that you choose. For example, you can send users an email with a link to install the client. When a user clicks the link, the MSI file automatically installs the client on the computer.
Alternatively, users can download the installation package from the regular DLP UserCheck notifications.
The installation is silent and generally, no reboot is required.
When the client is first installed, the tray icon indicates that it is not connected. When the client connects to the gateway, the tray icon shows that the client is active.
The first time that the client connects to the gateway, it asks for verification from the user and approval of the fingerprint.
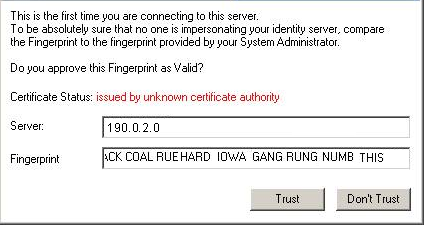
We recommend that you let the users know this will happen.
We recommend that you use a server certificate that is trusted by the certificate authority installed on users' computers. Then users do not see a message that says: .
If UserCheck for DLP is enabled on the gateway, users are required to enter their username and password after the client installs.
Example of message to users about the UserCheck client installation (for DLP:
Dear Users,
Our company has implemented a Data Loss Prevention automation to protect our confidential data from unintentional leakage. Soon you will be asked to verify the connection between a small client that we will install on your computer and the computer that will send you notifications.
This client will pop up notifications if you try to send a message that contains protected data. It might let you to send the data anyway, if you are sure that it does not violate our data-security guidelines.
When the client is installed, you will see a window that asks if you trust the DLP server. Check that the server is SERVER NAME and then click Trust.
In the next window, enter your username and password, and then click OK.

|
Note - If the UserCheck client is not connected to the gateway, the behavior is as if the client was never installed. Email notifications are sent for SMTP incidents and the Portal is used for HTTP incidents.
|
UserCheck and Check Point Password Authentication
You can configure UserCheck clients to authenticate with a Check Point user name and password. This is useful for non-Active Directory environments. It is also useful when it is necessary for a user, who is not logged in to the Active Directory domain, to log in manually.

|
Important - The UserCheck client is not supported for Load Sharing clusters. High Availability clusters and all other deployment types are supported.
|
You can see and edit Check Point users in the Data Loss Prevention tab, > page.
To enable Check Point password authentication. :
SmartDashboard Configuration
- Open SmartDashboard.
- For each user, edit the user object. You can do this in the Data Loss Prevention tab in the > page.
- In the page of the user, make sure that an email address is defined.
UserCheck Client Configuration
Ask your users to configure their UserCheck client:
- On the UserCheck client computer, right click the UserCheck icon in the Notification Area (next to the system clock).
- Select .
- Click .
- Select .
Helping Users
If users require assistance to troubleshoot issues with the UserCheck client, you can ask them to send you the logs.
To configure the client to generate logs:
- Right-click the UserCheck tray icon and select Settings.
The Settings window opens.
- Click Log to and browse to a pathname where the logs are saved.
- Click OK.
To send UserCheck logs from the client:
- Right-click the UserCheck tray icon and select Status.
The Status window opens.
- Click Advanced and then click the Collect information for technical support link.
The default email client opens, with an archive of the collected logs attached.
|


