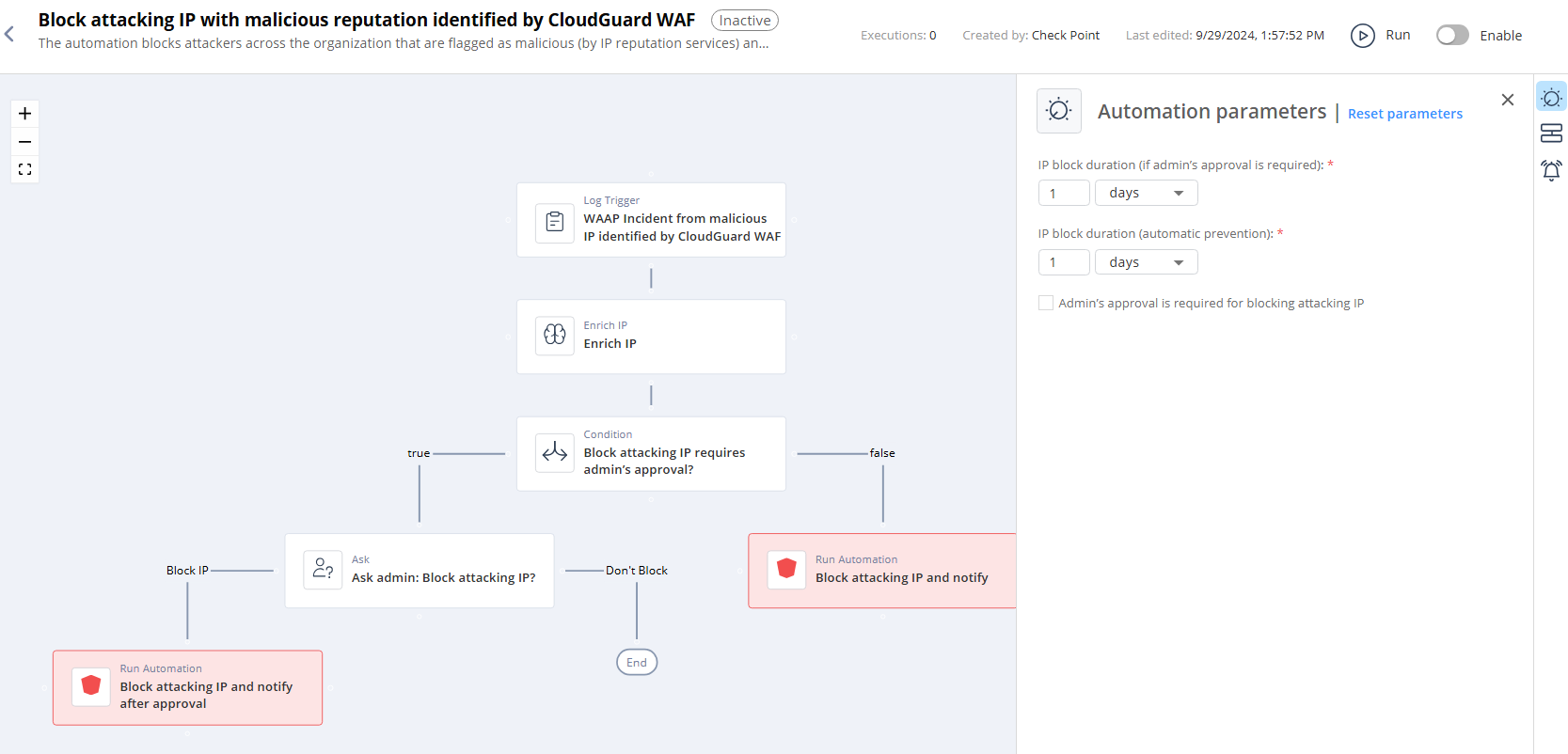
Block attacking IP with malicious reputation identified by CloudGuard WAF
The automation blocks attackers across the organization that are flagged as malicious (by IP reputation services) and is triggered by WAAP incidents that are detected by CloudGuard WAF. The notification includes information on the WAAP incident and the attacker. More parameters can be set using the automation parameters such as the block duration, whether the block is automatic or upon administrator's approval, and more.
Supported Products
-
CloudGuard WAF
-
Check Point Security Management Server (Quantum)
Parameters
|
IP block duration (if admin’s approval is required) |
Set the expiration period for the automation. This applies only if you have selected the Admin's approval is required for blocking attacking IP checkbox. After the expiration, Infinity Playblocks sends the notification for the administrator's approval. |
|
IP block duration (automatic prevention) |
Set the expiration period for the automations that are executed automatically (without the administrator's approval). The default duration is 1 day. |
|
Admin’s approval is required for blocking attacking IP |
Select the checkbox if you want administrator's approval to execute the automation. Check Point recommends that you leave Admin's approval is required for blocking attacking IP checkbox unselected. |
Trigger
Matching attacking IP with malicious reputation identified by CloudGuard WAF.
To view the example of this log, click Run.
Flow