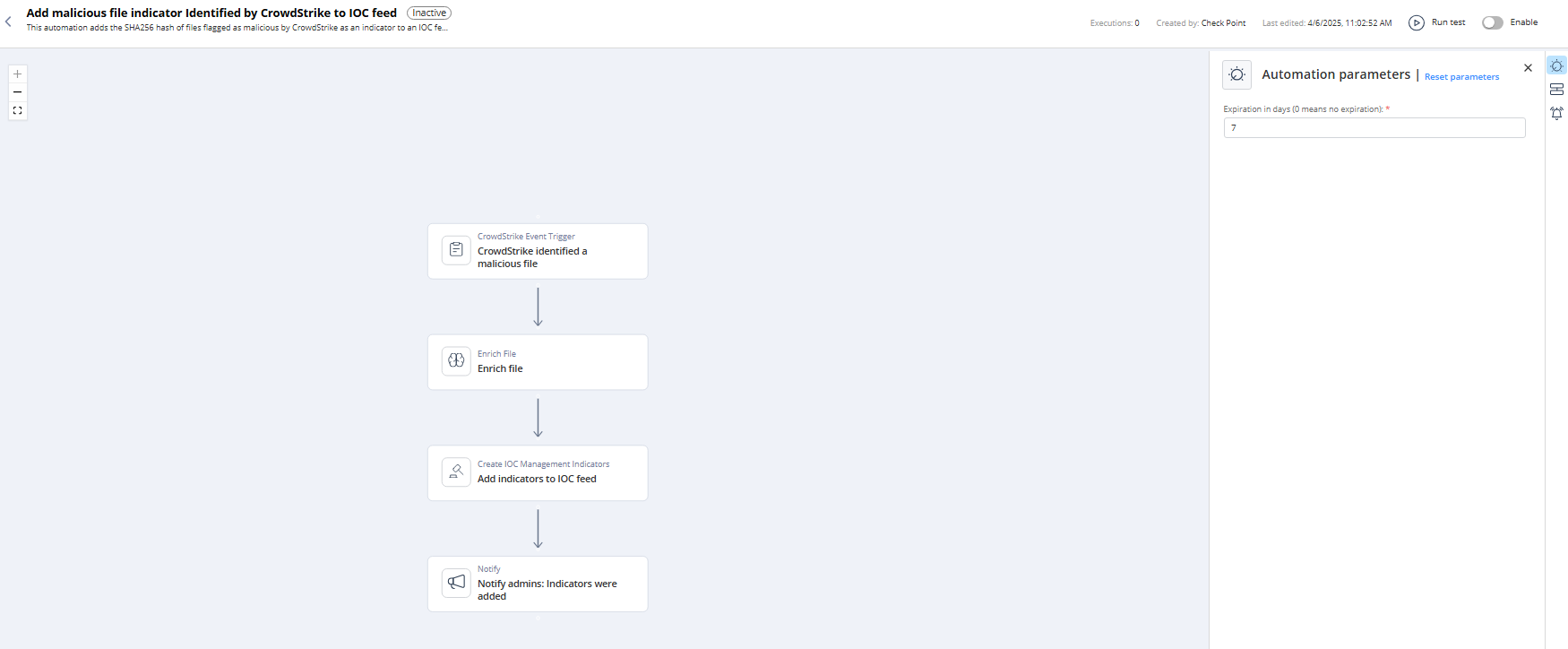
Add malicious file indicator Identified by CrowdStrike to IOC feed
This automation adds the SHA256 hash of files flagged as malicious by CrowdStrike as an indicator to an IOC feed, updating threat intelligence and enhancing security response. It could potentially help other products prevent the file from being downloaded or executed on all your machines if IOC Enforcement is enabled.
Supported Product
-
CrowdStrike
-
Infinity IoC Management
Parameters
|
Expiration in days (0 means no expiration) |
Set the expiration period for the automation. |
Trigger
Malicious file identified by CrowdStrike.
To view the example of this log, click Run.
Flow