Creating a Mitigation Process
To let Workspace ONE UEM![]() Unified Endpoint Management. An architecture and approach that controls different types of devices such as computers, smartphones and IoT devices from a centralized command point. identify the devices-at-risk and enforce compliance policies according to the risk level determined by Harmony Mobile analysis, you can apply the built-in Risk tags. The Harmony Mobile Dashboard uses tags to label the device with the risk level that the Harmony Mobile analysis determines.
Unified Endpoint Management. An architecture and approach that controls different types of devices such as computers, smartphones and IoT devices from a centralized command point. identify the devices-at-risk and enforce compliance policies according to the risk level determined by Harmony Mobile analysis, you can apply the built-in Risk tags. The Harmony Mobile Dashboard uses tags to label the device with the risk level that the Harmony Mobile analysis determines.
For creating a mitigation process for devices at risk:
-
Create a dynamic assignment group for devices at risk.
-
Assign this group to your organization.
-
Create a compliance policy for devices at risk.
Creating a Dynamic Assignment Group for Risk Tags
Create the Smart Group for the devices-at-risk.
Procedure:
-
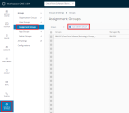
Go to Groups & Settings > Groups > Assignment Groups.
-
Click +Add Smart Group.
Example
-
Under Tags section select these tags:
-
CHKP_Risk_High
-
CHKP_Risk_Medium
-
CHKP_Risk_Low

Note - Check Point recommends to create a separate Smart Group for each risk level and for each device status (active, inactive, and more).
-
-
Click Save
|
|
Note - You can create a smart group for each risk level – High/Medium/Low and assign later the relevant policy for each level |
Creating a Compliance Policy for the Devices at Risk
The Compliance![]() Check Point Software Blade on a Management Server to view and apply the Security Best Practices to the managed Security Gateways. This Software Blade includes a library of Check Point-defined Security Best Practices to use as a baseline for good Security Gateway and Policy configuration. Policies are activated on the devices that are at high risk.
Check Point Software Blade on a Management Server to view and apply the Security Best Practices to the managed Security Gateways. This Software Blade includes a library of Check Point-defined Security Best Practices to use as a baseline for good Security Gateway and Policy configuration. Policies are activated on the devices that are at high risk.
To accomplish the policy enforcement on the devices, you must create Device Profiles and the Compliance Policy to apply these profiles to the devices.
You must create separate compliance policies for specific OS types, such as iOS and Android.
|
|
Note - In every organization, the customer configures the compliance policies according to their production environment, needs, and internal security policy |
To create a Compliance Policy for the Devices at Risk:
-
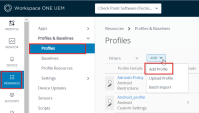
Go to Resources > Profiles & Baselines > Profiles, click Add > Add Profile.
Example:
-
In the Add Profile window, select a platform to start.
Example:
The Add Profile window opens

Note - The data fields are different for iOS and Android users. The examples below are applicable for iOS. For Android it is the same idea with different fields.
-
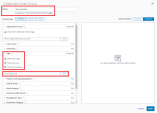
Configure the profile for Non-Compliant Devices Policy.
-
Configure setting in the Add a Profile window:
-
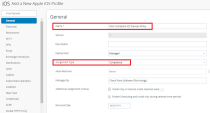
General Tab
-
Name - Enter a unique Profile name (for example, Non-Compliant iOS Devices Policy).
-
Description - Enter short description (for example, Non-Compliant iOS Devices Policy).
-
Assignment Type - Select Compliance.
-
Managed By - Select the relevant Organization Group under which the profile is managed.
-
-
Click Restrictions > Configure.
By default, all the device functions are activated in Device Functionality section (for iOS devices), or in Work Managed Device (for Android devices). When you remove the check mark, you completely disable the function once the profile is applied.
-
Click Save and Publish.
-
-
Configure the compliance policy for the non-compliant devices.
The Compliance Policy is activated on the devices with risk.

Note - In every organization, the customer configures the compliance policies according to the production environment needs, and the internal security policy.
Follow steps 1-10 in Creating a Compliance Policy for Required Apps (This time create a Compliance Policy for Devices at Risk) with these changes:
-
In the Rules tab:
-
For iOS devices - Select OS Version, Greater Than or Equal To, Apple - iOS 12.0.0.
-
For Android devices - Select OS Version, Greater Than or Equal To, Android - Android 5.0.0.
-
-
On the Assignment tab, add the Assignment Group you created in Creating a Dynamic Assignment Group for Risk Tags.
-
On the Summary tab, enter a unique name for the Compliance Policy, and add the description of the policy, while both contain the words Devices At Risk.
Examples:
-
For iOS - Name this policy “iOS Devices At Risk”.
-
For Android - Name this policy “Android Devices At Risk”.
-
-