Configuring UEM to Deploy the Harmony Mobile Protect app
|
|
Notes:
|
General workflow:
-
Add the Harmony Mobile Protect app to your App Catalog. See Adding the Harmony Mobile Protect app to your App Catalog
-
Prompt the Harmony Mobile Protect app installation on your devices. See Automatic Activation of Harmony Mobile: Prompt the Protect app installation
-
Connect the app to your devices. See Connecting the Harmony Mobile Protect app to your Device
-
Configure the Mitigation Process for the app (optional). See Connecting the Harmony Mobile Protect app to your Device
Adding the Harmony Mobile Protect app to your App Catalog
The Harmony Mobile Protect app can be automatically configured and deployed. The user only needs to accept the installation and then launch the app to finish activation and registration. You assign configuration parameters for configuring the app per user.
|
|
Note - The data fields are similar for both iOS and Android users. The examples below are applicable for both platforms. |
Use the CHKP Status Tags to deploy the Harmony Mobile Protect app from the public stores to the devices that are protected by Check Point Harmony Mobile. See Creating a Device Provisioning Group for Harmony Mobile
You must add the Protect app for both iOS and Android operating systems.
|
|
Notes -
|
To import the Harmony Mobile Protect app:
-
Go to Apps > App Catalog > Add.
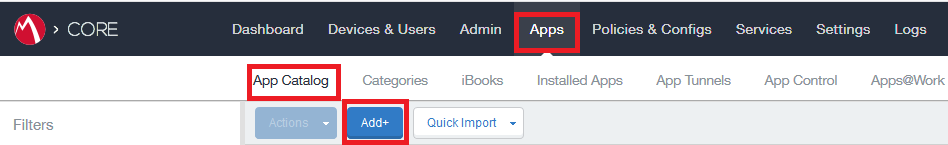
-
Select and configure the Harmony Mobile Protect app.
-
From the app list, select the Harmony Mobile Protect app.
-
Click Next.
The Describe pane opens. No changes are required.
-
Click Next.
-
On the App Store pane go to Apps@Work catalog checkbox and select only the Feature this App option.
-
Select these options:
-
Install the app for Android Enterprise
-
Auto Update this App
-
Silent Install for Mandatory Apps
Example:
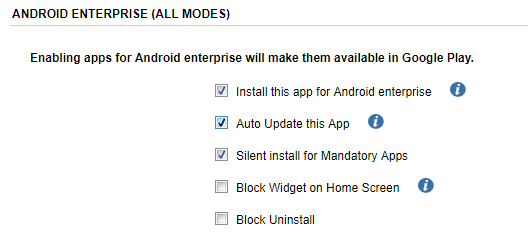
-
-
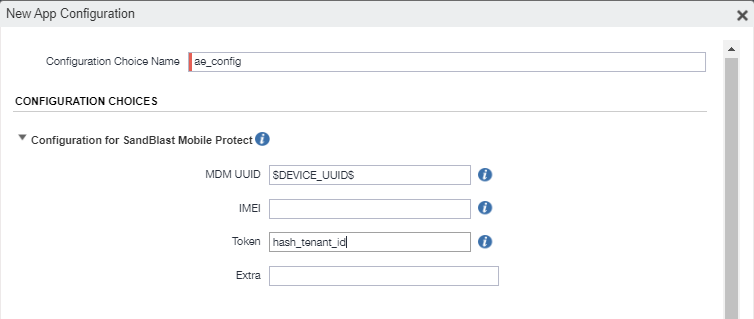
Go to Configuration Choices and click Add.
-
In the Configuration Choices section configure these settings and assign to the label:
Item
Description
Configuration Value
mdm_uuid
String
gwAddress
String
Enter the Security Gateway
 Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. server for your region:
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. server for your region:Region
Server
US
gw.locsec.net
Ireland (EU region)
eu-gw.locsec.net
Australia (Asia region)
au-gw.locsec.net
Canada (Canada)
ca-gw.locsec.net
UK region (UK)
uk-gw.locsec.net
India
in-gw.locsec.net
token
String
hash_tenant_id**
(The SHA-256 value of the Dashboard Management ID. You must use the token configured in the Deployment section. For more information see Configuring the Integration Settings)
portalAccountId
String
Account ID of the application in the Infinity Portal.
-
Click Finish
-
For iOS Devices
-
Go to Store List and select iTunes.
-
In the Application Name field enter Harmony Mobile Protect > App Store and click Search.
-
Select the Harmony Mobile Protect app
Example:
-
Click Next.
The Describe pane opens. No changes are required.
-
On the App Store pane go to Apps@Work catalog and select these options:
-
This is a Free App
-
Allow conversion of apps from unmanaged to managed in Apps@Work (iOS 9 or later)
-
Feature this App in the Apps@Work catalog
-
-
Click Next.
-
On the App Configuration pane select these options:
-
Send installation request on device registration or sign-in
-
Remove app when UEM profile is removed
-
-
Click Finish.
Enable the automatic configuration and deployment of the app. See iOS App Deployment Configuration
-
iOS App Deployment Configuration
To enable the automatic configuration and deployment of the iOS Harmony Mobile Protect app on your devices you must assign configuration parameters for configuring the app per user. Create the ManagedAppConfig.plist File and then use it for auto-deploy of the Harmony Mobile Protect app on your devices.
To create the ManagedAppConfig.plist File:
-
Copy this text to a text editor (for example, Notepad).
Copy<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>DEVICE_UDID</key>
<string>$DEVICE_UDID$</string>
<key>DEVICE_MAC</key>
<string>$DEVICE_MAC$</string>
<key>DISPLAY_NAME</key>
<string>$DISPLAY_NAME$</string>
<key>EMAIL</key>
<string>$EMAIL$</string>
<key>FIRST_NAME</key>
<string>$FIRST_NAME$</string>
<key>LAST_NAME</key>
<string>$LAST_NAME$</string>
<key>USERID</key>
<string>$USERID$</string>
<key>Lacoon Server Address</key>
<string>gw.locsec.net</string>
<key>token</key>
<string>hash_tenant_id</string>
<key>UEM_device_id</key>
<string>$DEVICE_UUID$</string>
</dict>
</plist>In line number 20, replace the gateway server (gw.locsec.net) with the local gateway based on your region:
Enter the Security Gateway server for your region:
Region
Server
US
gw.locsec.net
Ireland (EU region)
eu-gw.locsec.net
Australia (Asia region)
au-gw.locsec.net
Canada (Canada)
ca-gw.locsec.net
UK region (UK)
uk-gw.locsec.net
India
in-gw.locsec.net
-
Change the
<string>hash_tenant_id</string>content (i.e. instead of “hash_tenant_id” text) to the Token you saved from Deployment section in Configuring the Integration Settings -
Click Save As… and save the file as ManagedAppConfig.plist
-
Exit the file.
-
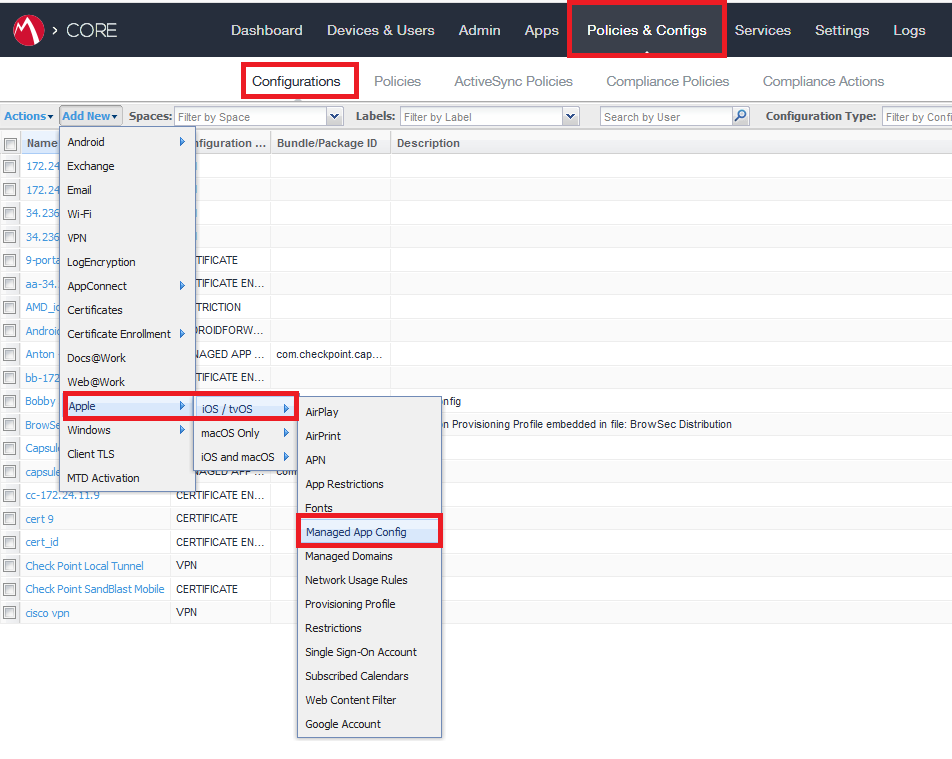
Go to Policies & Configs > Configurations and click Add New.
-
From the drop-down list select Apple > iOS / tvOS > Managed App Config.
The New Managed App Config Setting window opens.
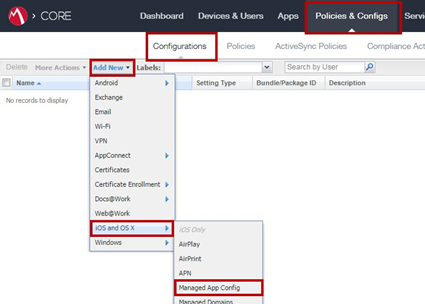
-
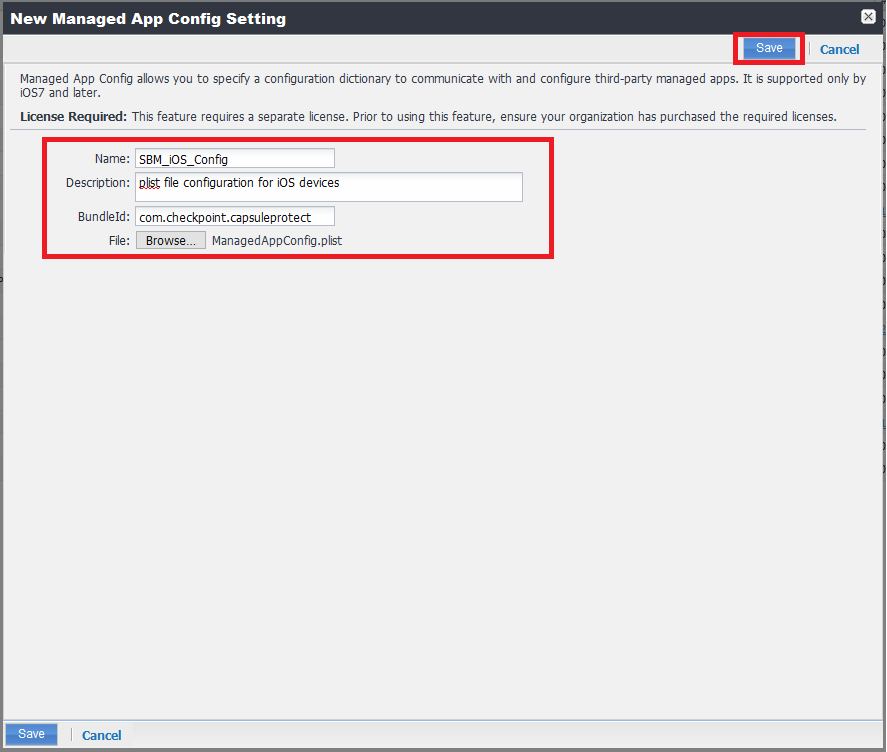
Enter these parameters:
-
Name
-
Description
-
BundleId - Enter com.checkpoint.capsuleprotect
-
-
Click Choose File and select the ManagedAppConfig.plist file.
-
Click Save.
-
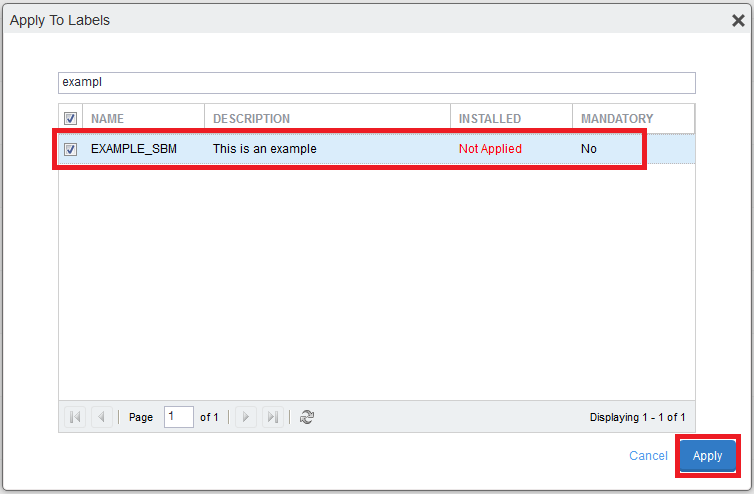
Select this new Managed App Config and click More Actions drop-down menu.
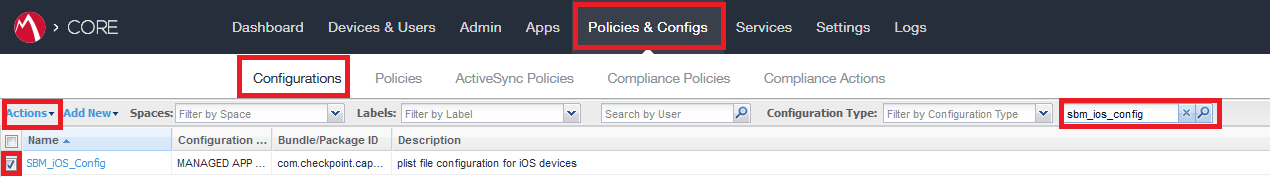
-
Select Apply To Label.
-
In the Apply To Labels window select the primary or secondary Device Provisioning group (label).
-
Click Apply.
Automatic Activation of Harmony Mobile: Prompt the Protect app installation
If Harmony Mobile Protect app is not installed or removed from device, then the device is marked as not protected.
To prompt the Harmony Mobile Protect app installation on your devices
-
Create a Protect app Application Group for both iOS and Android apps.
-
Assign this group to your organization.
-
Create a compliance policy that uninstalls and, or removes all corporate apps from the device until the user installs the Harmony Mobile Protect app on the device.
Connecting the Harmony Mobile Protect app to your Device
To install the Harmony Mobile Protect app on your devices in your organization, you must first configure them to require the Harmony Mobile Protect app. This is a dynamic group assignment according to the associated tag. MobileIron UEM calls these dynamic Assignment Groups “Smart Groups”.
Add all the devices marked with the Status tags to a group that indicates that the devices are registered in Harmony Mobile Dashboard.
Optional: Create a mitigation process. See Creating a Mitigation Process
General Workflow:
-
Add Harmony Mobile Protect apps to the Device Provisioning Group to create a Protect app group.
-
Create App Control Rule
 Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. that prompts installation of the Harmony Mobile Protect app on both the iOS and Android apps.
Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. that prompts installation of the Harmony Mobile Protect app on both the iOS and Android apps. -
Assign the groups of the protected devices to the organization through the Status tags.
-
Create a Compliance policy to uninstall / remove corporate apps from the device until the user installs the required apps on the device.
-
Create a Mitigation Process for devises-at-risk through the Risk tags.
Creating a Protect app Group
Add the Harmony Mobile Protect app group to your devices in the Device Provisioning group.
|
|
Note - The data fields are similar for both iOS and Android users. The examples below are applicable for both platforms. |
To add Harmony Mobile Protect apps to the Device Provisioning Group:
-
On the MobileIron Core Portal go to Apps > App Catalog, select Harmony Mobile Protect app both the iOS and Android devices.
-
In the Actions drop-down menu select Apply To Labels.
Example:
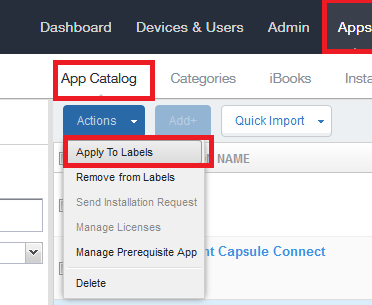
-
In the Apply to Labels window select the provisioning label you created for the Device Provisioning group. See Creating a Device Provisioning Group for Harmony Mobile
-
Click Apply.
Example:
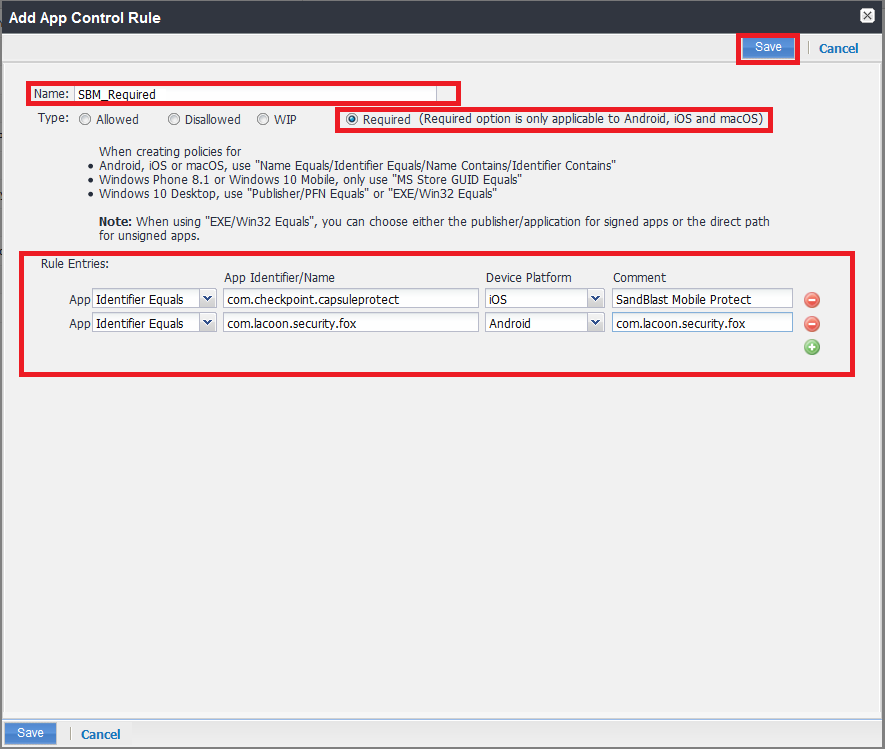
Creating an App Control Rule
Procedure:
-
Go to Apps > App Control click Add.
App Control Rule prompts the iOS and Android devices to install the Harmony Mobile Protect app.
Example:
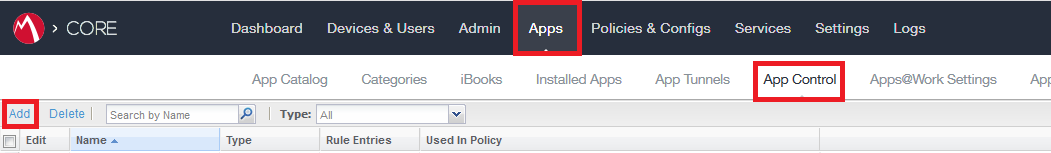
-
In the Add App Control Rule window configure these parameters:
-
Click Save.
Creating a Compliance Actions Policy for the Organization Devices
The Compliance Policies are activated on the devices that did not install the required apps.
You must create separate compliance policies for specific OS types, such as iOS and Android.
|
|
Note - In every organization, the customer configures the compliance policies according to the production environment, needs, and the internal security policy |
To create a Compliance Policy:
-
Go to Policies & Configs > Compliance Action > and click + Add.
Example:
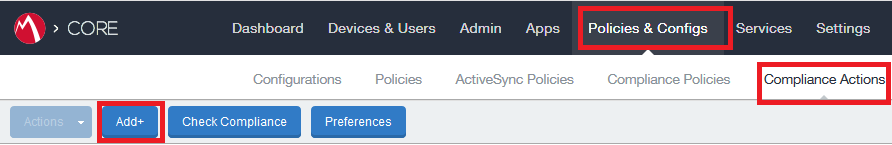
-
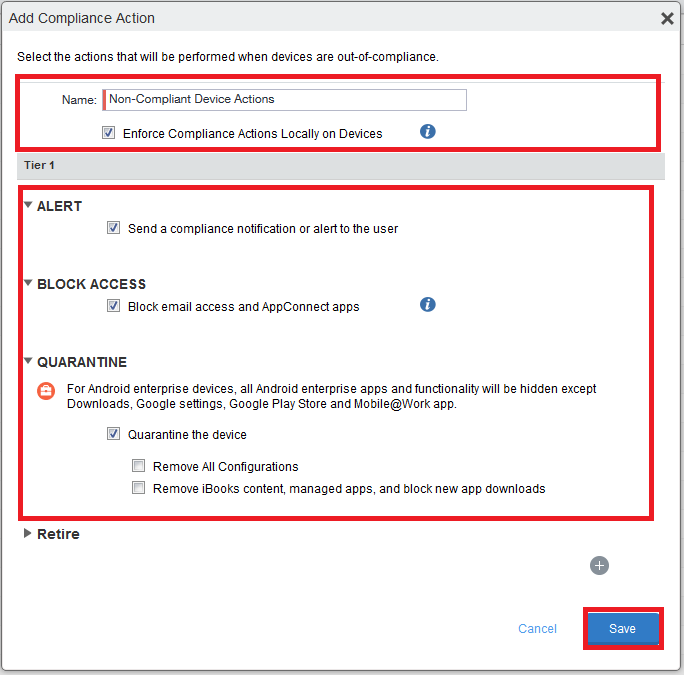
In the Add Compliance Action window configure these parameters:
-
Name - Enter Non- Compliant Device Actions (recommended)
-
Select these options:
-
Enforce Compliance Actions Locally on Devices
-
ALERT - Select Send a compliance notification or alert to the user
-
BLOCK ACCESS - Select Block email access and AppConnect apps
-
QUARANTINE - Select Quarantine the device
-
-
-
Click Save.
Example:
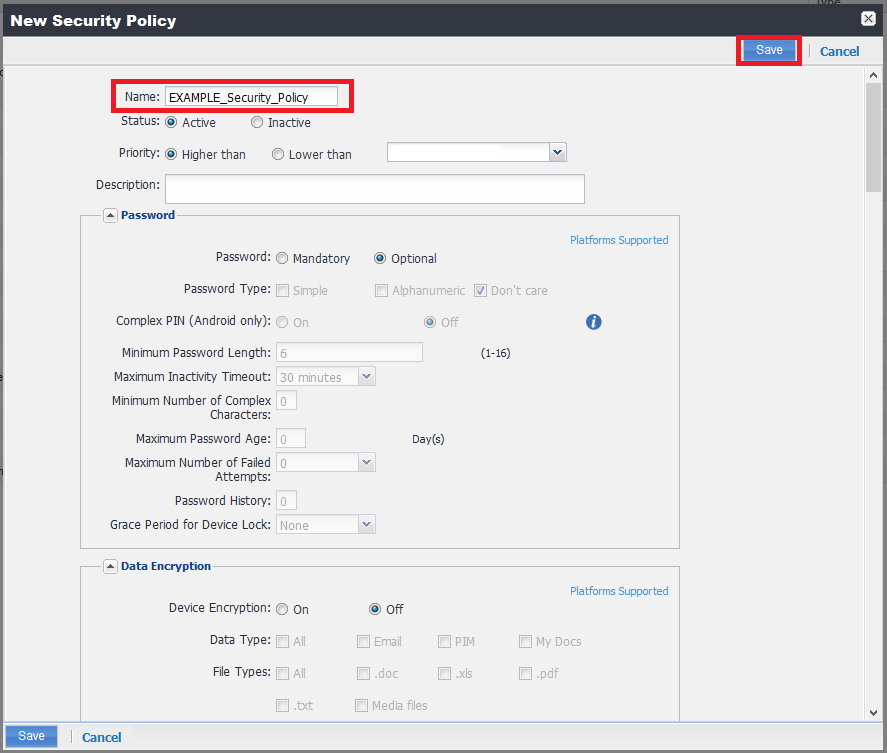
Creating a Security Compliance Rule (Enforcement)
Link the App Control Rule and Compliance Actions Policy to create the new Security Policy.
Procedure:
-
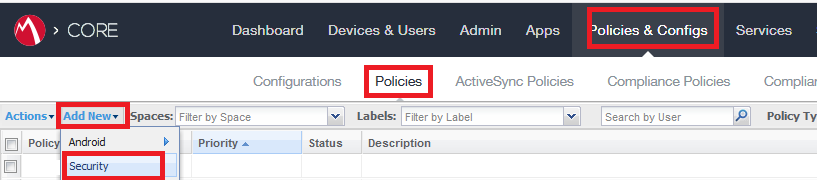
Go to Policies & Configs > Policies > Add New menu and select Security.
Example:
-
In the New Security Policy window enter a policy name.
Example:
-
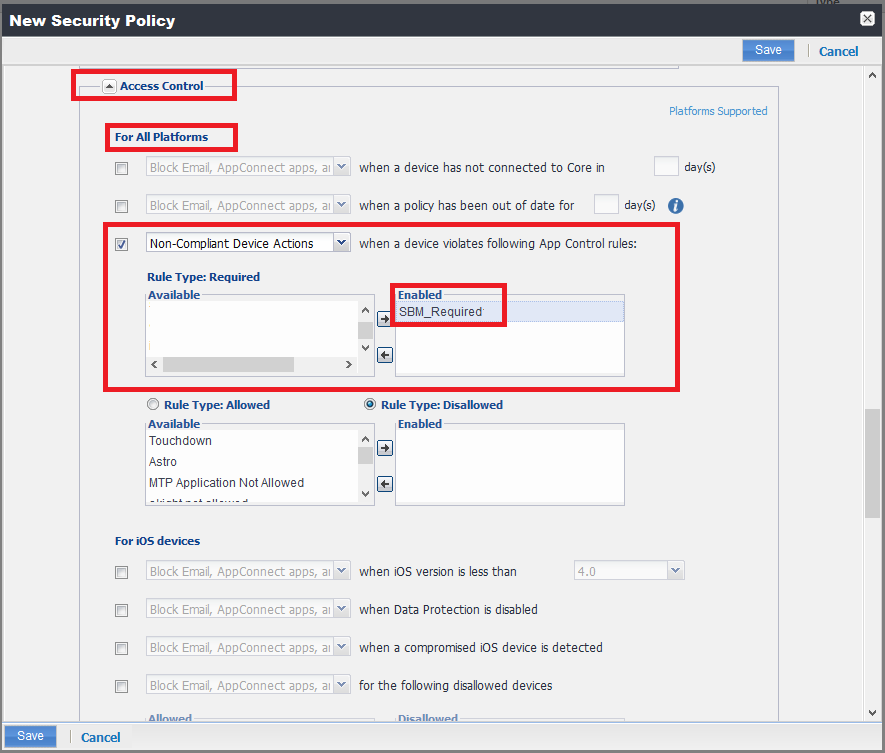
Scroll down to Access Control > For All Platforms section and select these options:
-
Option Non-Compliant Device Actions compliance action policy (see Creating a Compliance Actions Policy for the Organization Devices .
-
Option when a device violates following App Control rules (see Creating an App Control Rule).
-
Rule Type - Select Enabled > SBM_Required
-
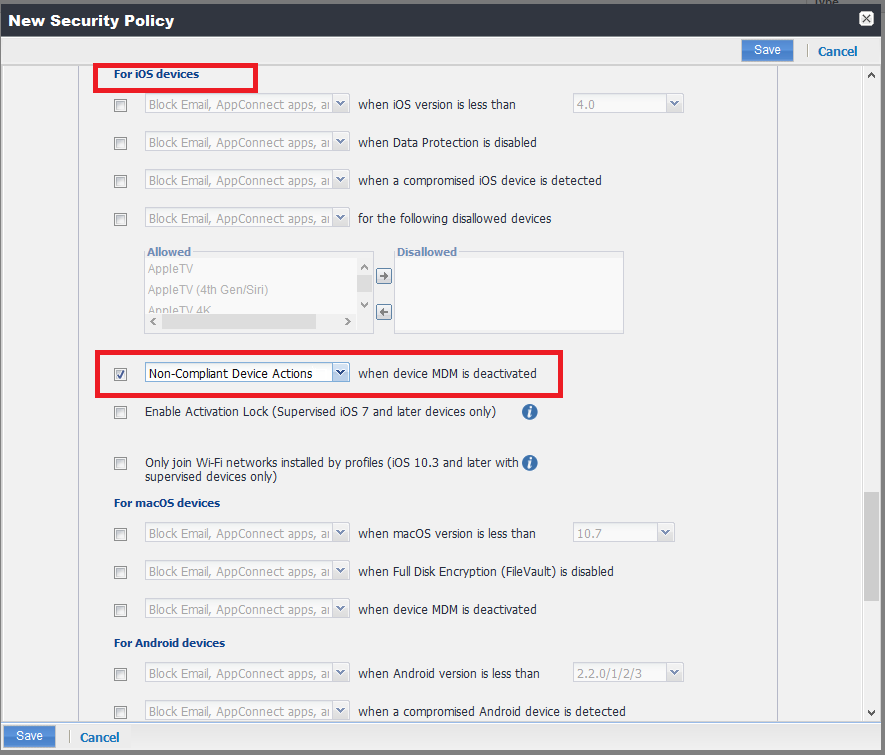
For iOS Devices:
Scroll down to For iOS devices section and select these options:
-
Non-Compliant Device Actions Policy
-
when device UEM is deactivated
Example:
-
-
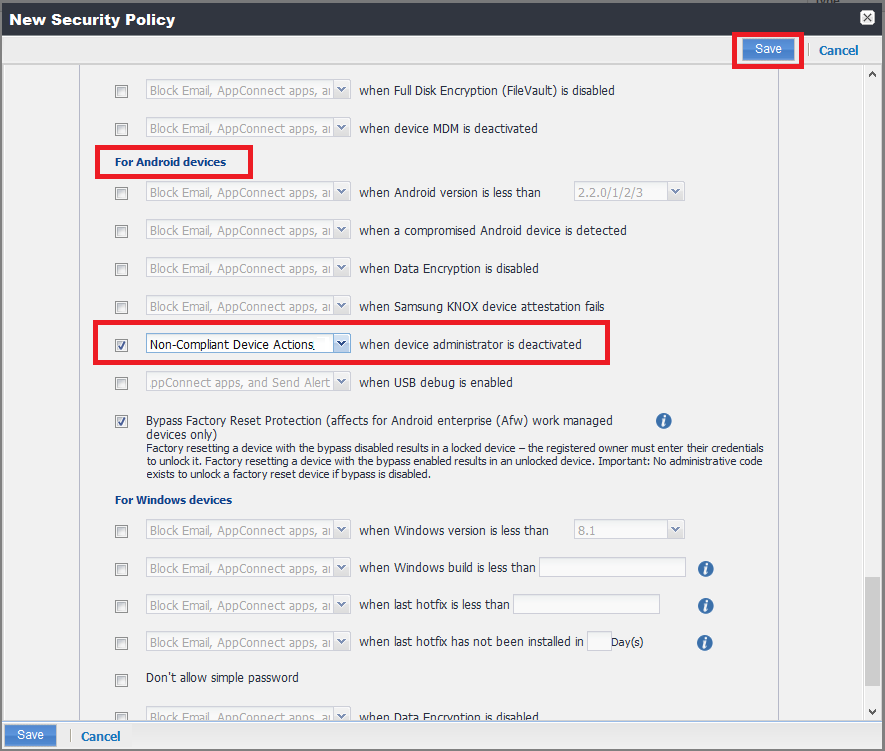
For Android Devices
Scroll down to the For Android devices section and select these options:
-
Non-Compliant Device Actions Policy
-
when device administrator is deactivated
Example:
-
-
-
Click Save.
Applying the UEM Security Policy to the Device Provisioning Group
Procedure:
-
Go to Policies & Configs > Policies and select the Security Policy.
-
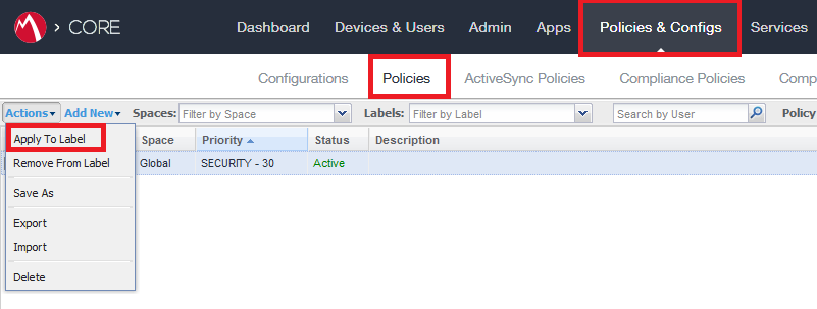
Click More Actions drop-down menu and select Apply To Label.
Example:
Make sure the checkbox is checked:
And after that apply it to label:
-
In the Apply To Labels window select one of these options:
-
If you created only a Primary Device Provisioning Group

Note - Perform this step if you created a Primary Device Provisioning Group only.
Select the Device Provisioning Label.
Example:
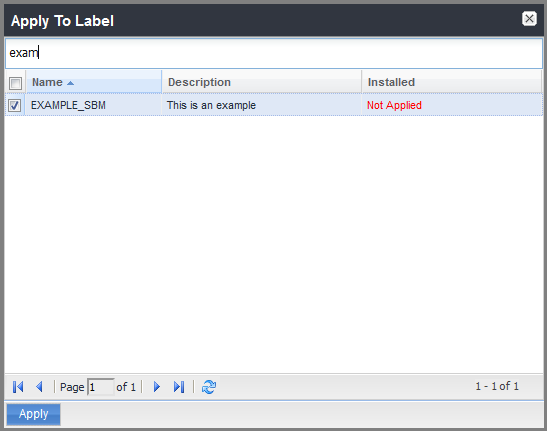
-
If you created both a Device Provisioning Group and a Secondary Device Provisioning Group

Note - Perform this step only if you created a Secondary Device Provisioning Group.
Select the Secondary Device Provisioning Label.
Example:
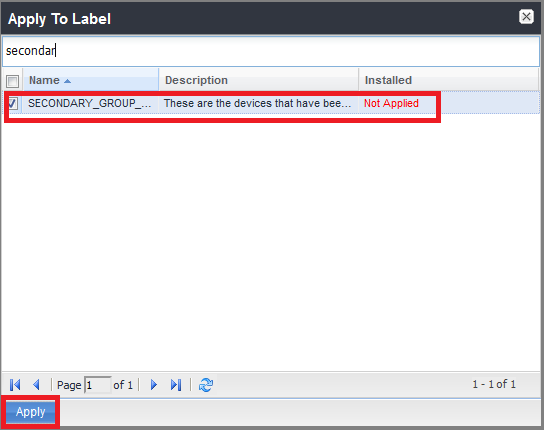
-
-
Click Apply.
Creating a Mitigation Process
To let the MobileIron Core system identify the devices-at-risk and to enforce the configured compliance policies according to the risk level, you must apply the built-in Risk tags. The Harmony Mobile Dashboard uses these tags (CHKP_Risk) to identify any device with the risk level that the Harmony Mobile analysis determines.
For more information, see Configuring the Integration Settings
To accomplish the policy enforcement on the devices, you must create Device Profiles and the Compliance Policy to apply these profiles to the devices. Create a Compliance Policy Rule, Compliance Policy Group and apply the Compliance Policy Group to the Device Provisioning Label.
Check Point recommends these names for the Harmony Mobile Protect app attributes:
-
Device Provisioning Group - CPTME_SBM
-
Custom Attribute - CHKP_ Risk (set to High or Medium)
-
Compliance Policy Group - CPTME_SBM_AT_RISK_DEVICES
Creating a Compliance Policy for the Devices at Risk
The Compliance Policies are activated on the devices that are at high risk.
You must create separate compliance policies for specific OS types, such as iOS and Android.
|
|
Note - In every organization, the customer configures the compliance policies according to the production environment, needs, and the internal security policy. |
To create a Compliance Policy for the Devices at Risk:
-
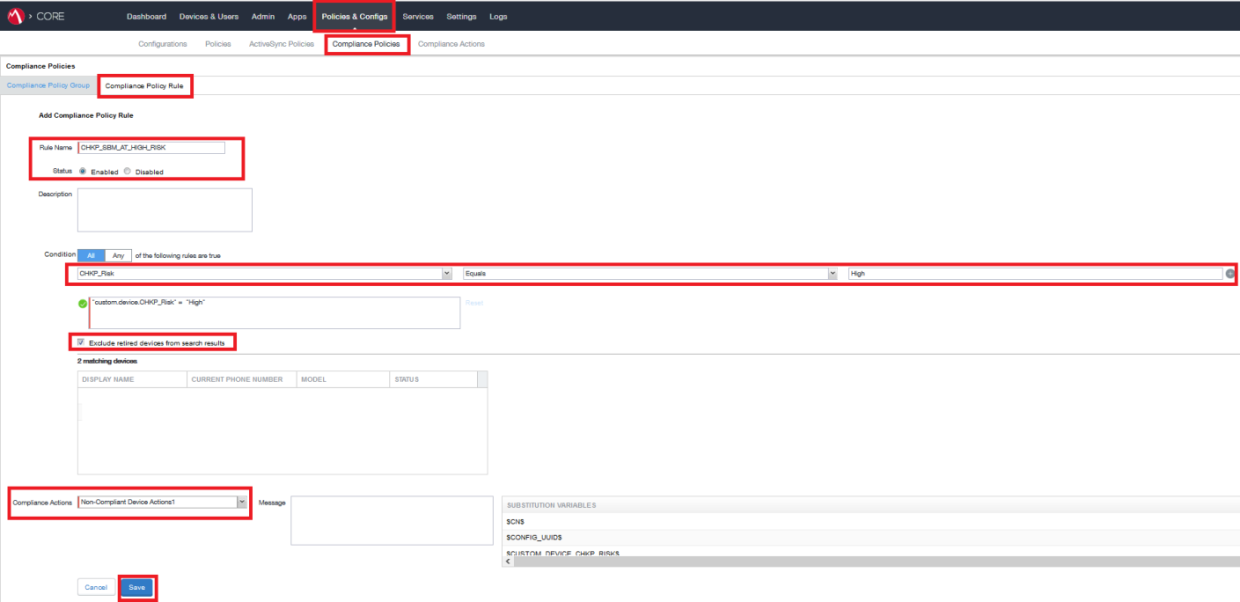
Go to Policies & Configs > Compliance Policies > Compliance Policy Rule and click Add.
Example:
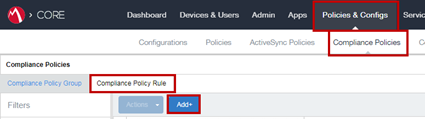
-
On the Compliance Policy Rule tab configure these parameters:
-
Rule Name - Enter the Rule Name.
-
Description - Enter a description.
-
Status - Check Enabled option.
-
Make sure Exclude retired devices from search results is selected.
-
-
From the Field menu select Custom Attributes > Device Attributes > CHKP_Risk.
-
From the Operator menu select Equals.
-
In the Value field enter High.
-
(Optional) To apply the Compliance Action to devices with High or Medium Risk level, click [+] icon to add another line and enter Medium in the Value field.
-
From the Compliance Action menu select the Non-Compliant Device Action. See Creating a Compliance Actions Policy for the Organization Devices
-
Click Save.
Example:
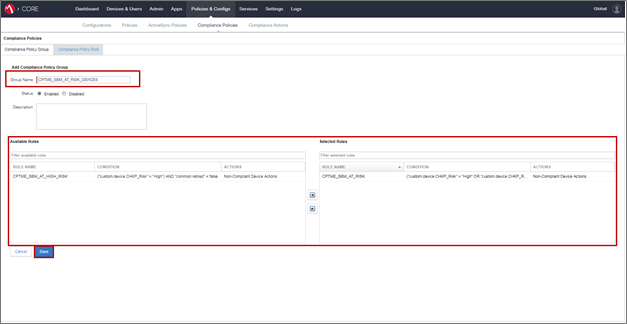
Creating a Compliance Policy Group
Compliance Policy Group uses the Compliance Policy Rules and applies to the Device Provisioning Group to enforce on devices that are at High or Medium Risk.
Procedure:
-
Go to Policies & Configs > Compliance Policies > Compliance Policy Group and click Add.
Example:
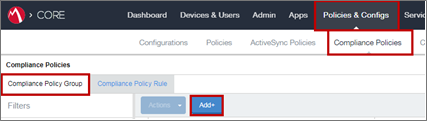
-
On the Compliance Policy Group tab configure these parameters:
-
Group Name - Enter the Group Name.
-
Status - Check Enabled option.
-
Make sure Exclude retired devices from search results is selected.
-
-
In the Available Rules section, select the created Compliance Rule.
-
Click Save.
Example:
Applying the Compliance Policy Group to the Device Provisioning Group
The Compliance Policy applies to the Device Provisioning Group (see Creating a Device Provisioning Group for Harmony Mobile).
Procedure:
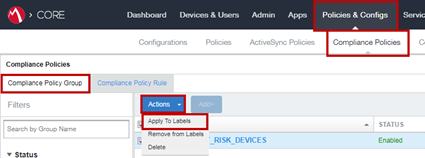
-
Go to Policies & Configs > Compliance Policies > Compliance Policy Group and select the Compliance Policy Group (seeCreating a Compliance Policy Group).
-
Click Actions menu and select Apply to Labels.
Example:
-
In the Apply to Label window select the Device Provisioning Group label (for example, CPTME_SBM).
-
Click Apply.