Testing High Risk Activity Detection and Policy Enforcement
If the user’s device is determined to be at risk either due to a malicious app or malicious activity, the Harmony Mobile system notifies the user through in-app notifications, and also updates the risk level custom attribute value to the MobileIron Cloud system for that device. MobileIron Cloud receives the risk state change, and upon recognizing the risk level value tied to a Configuration Profile, enacts that policy.
In this example, the administrator blocks an app, for example, HeyWhatsApp. As a result, the user device is identified to be at High Risk (CHKP_Risk = High) due to the blocked app HeyWhatsApp installed on the device. The Harmony Mobile dashboard notifies the user, and marks the device as High Risk (CHKP_Risk = High) to the MobileIron Cloud system. The MobileIron Cloud system then enforces policy actions specified in the Compliance![]() Check Point Software Blade on a Management Server to view and apply the Security Best Practices to the managed Security Gateways. This Software Blade includes a library of Check Point-defined Security Best Practices to use as a baseline for good Security Gateway and Policy configuration. Policy Profile.
Check Point Software Blade on a Management Server to view and apply the Security Best Practices to the managed Security Gateways. This Software Blade includes a library of Check Point-defined Security Best Practices to use as a baseline for good Security Gateway and Policy configuration. Policy Profile.
Blocking a Test App
-
Log in to the Harmony Mobile dashboard.
-
Go to Forensics > Application and click
 for the app you want to block.
for the app you want to block. -
Select Edit app exception and click the policy you want to modify.
The Application Exceptions section in the Application policy appears.
-
From the Action drop-down list, select Block.
-
Click Add.
-
To save the policy changes, click Save.
View of a Non-Compliant Device
The device with the blacklisted app must be in one of the Smart Groups that you created for the devices at risk. See Connecting the Harmony Mobile Protect app to your Device
|
|
Note - The data fields are similar for both iOS and Android users. The examples below are applicable for both platforms |
Harmony Mobile Protect app Notifications
You receive a Harmony Mobile Protect notification that the blacklisted app is not allowed by Corporate Policy.
If you configured an email notification, you receive an email from MobileIron Cloud.
Example:
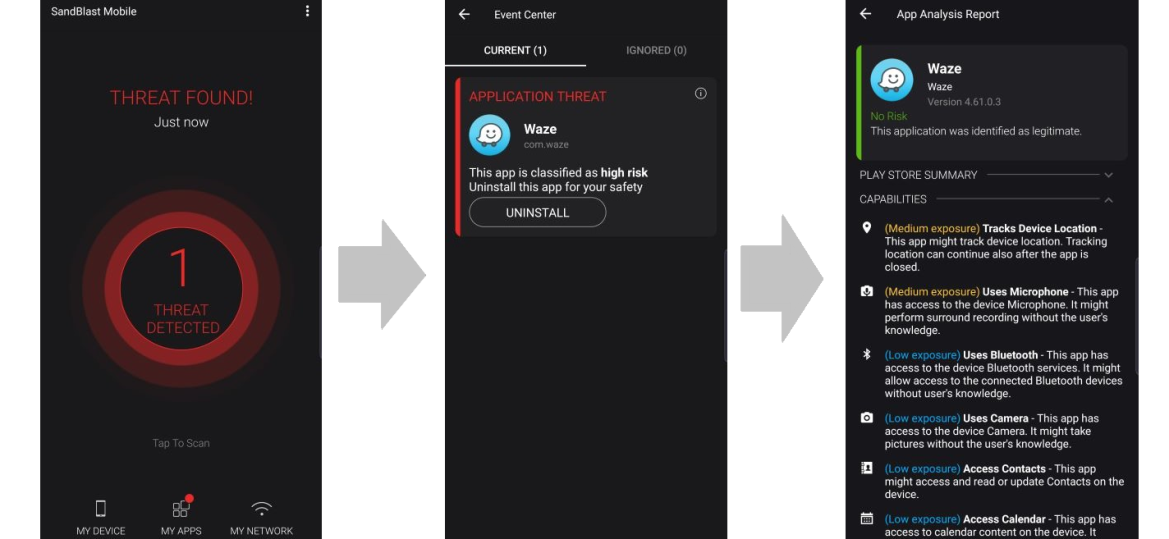
You are not allowed to use the app until you remove the blacklisted app or change the compliance policy settings. See Creating a Mitigation Process.
Mobile@Work app Notifications
You receive Harmony Mobile Protect app notifications in the Mobile@Work app.
You can see that the device is out of compliance and that it cannot access corporate resources.
Example:
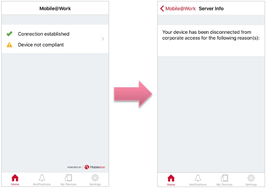
You are not allowed to access your corporate data or network from this device until you uninstall this app to reduce the risk level.
Administrator View on the Harmony Mobile Dashboard
To view the devices at high risk on the Harmony Mobile dashboard:
-
Go to Overview.
The list of devices at risk is displayed in the Device Risk section.
-
Click High Risk.
The list of devices at High Risk state is displayed.
-
Select the specific device.
You can see that the blacklisted app causes the high risk state.
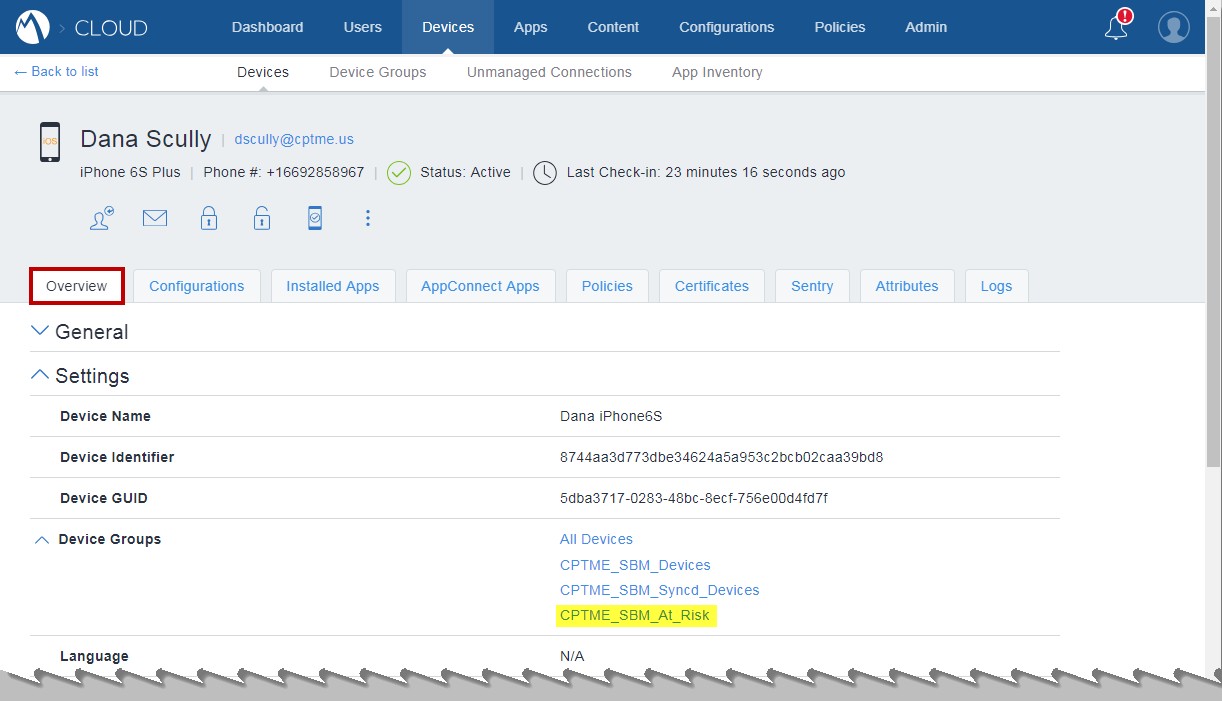
Administrator View on the MobileIron Cloud Console
In the MobileIron Cloud Portal, the Administrator can see that this device belongs to the "at risk" device group, in our example "CPTME_SBM_At_Risk ".
-
Devices > Overview tab:
Example:
-
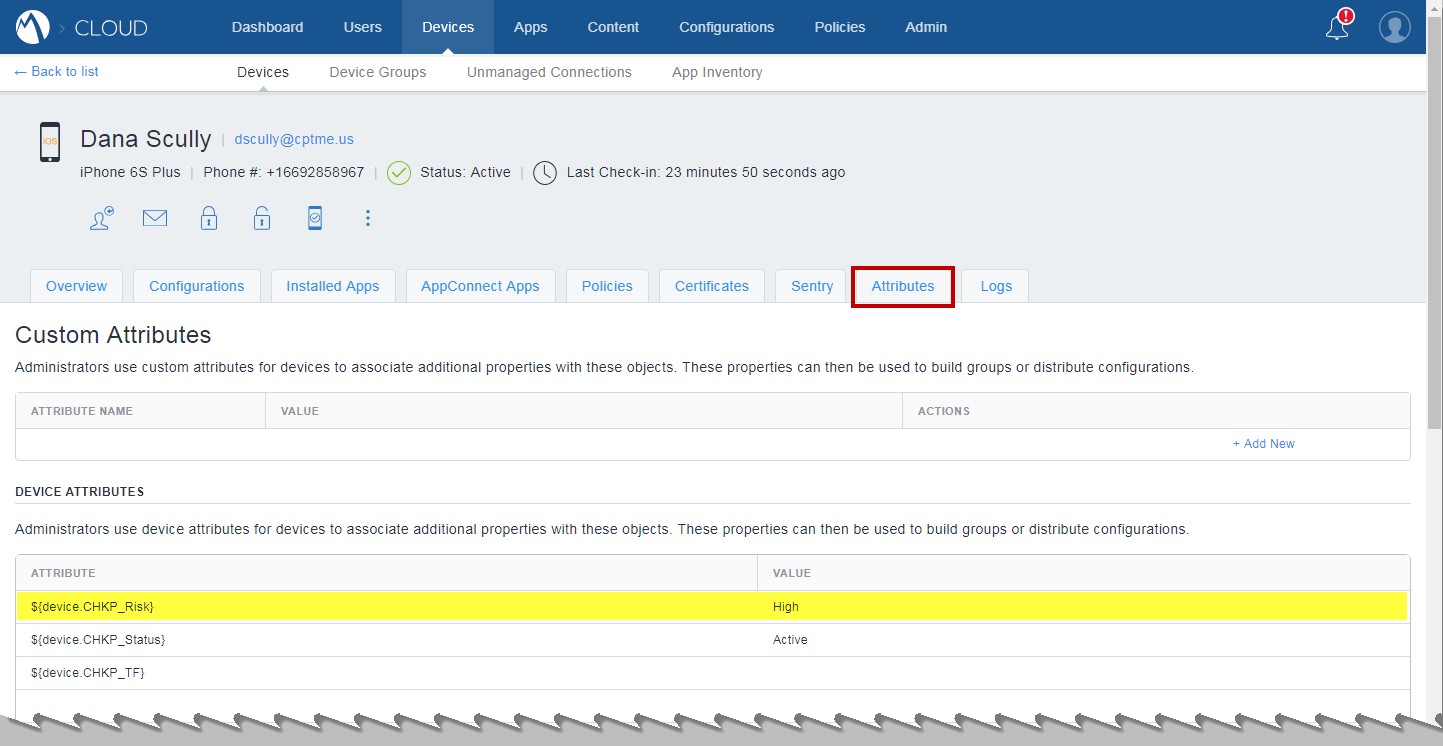
Devices > Attributes tab:
The MobileIron Cloud Portal shows that the device has its custom device attribute "CHKP_Risk" set to "High".
Example:
-
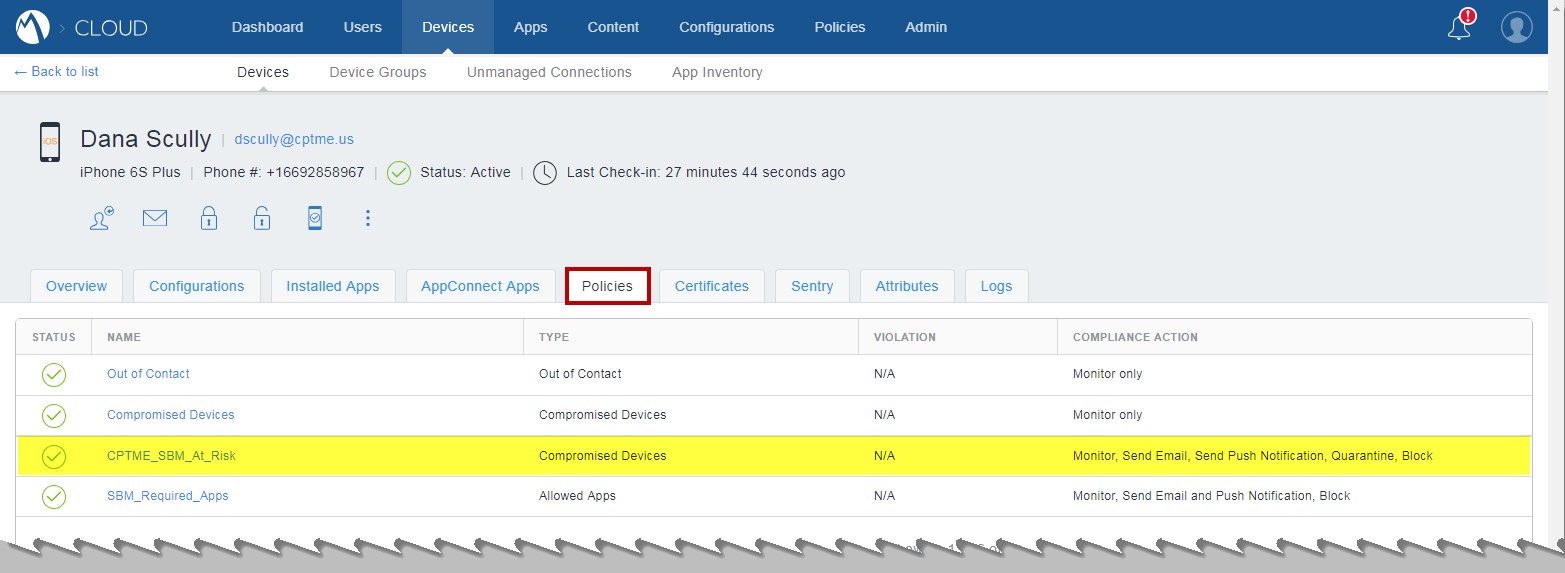
Devices > Policies tab:
The Administrator can see what Compliance Policy were applied, and we can see that the ''at risk'' policy was applied to this user's device.
Example:
The user cannot access their corporate data or networks from this device until they uninstall the blacklisted app and lower the risk.





