Testing High Risk Activity Detection and Policy Enforcement
If the user’s device is determined to be at a High Risk state either due to a malicious app or malicious activity, the Harmony Mobile system notifies the user via in-app notifications as well as updates the High Risk state to the MaaS360 system for that device.
MaaS360 receives the state change, and upon recognizing the custom attribute being tied to a compliance policy, enacts the policy actions.
In the following example, the administrator blocks an app, for example HeyWhatsApp. As a result, the user’s device is identified to be at High Risk due to the blocked app, HeyWhatsApp being installed on the device. The Harmony Mobile dashboard notifies the user, and marks the device as High Risk to the MaaS360 system. The MaaS360 system then enforces policy actions specified in the compliance policy, in our example MP_Android_HighRisk based on the compliance rules specifying that the custom attribute set to yes groups this device in the device mitigation group, Devices_At_HighRisk. This mitigation process is the one created in section Creating a Mitigation Process.
Blocking a Test App
-
Log in to the Harmony Mobile dashboard.
-
Go to Forensics > Application and click
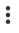 for the app you want to block.
for the app you want to block. -
Select Edit app exception and click the policy you want to modify.
The Application Exceptions section in the Application policy appears.
-
From the Action drop-down list, select Block.
-
Click Add.
-
To save the policy changes, click Save.
View of Non-Compliant Device
Harmony Mobile Protect App Notifications:
-
The user receives a Harmony Mobile Protect notification indicating that the blacklisted app is not allowed by Corporate Policy, in our example “Dropbox”.
-
The user will not be able to use the device’s camera, as specified in the compliance actions (policy) we created in section Creating Compliance Actions for iOS Devices (Policy), in our example “MP_iOS_HighRisk” until the user removes the blacklisted app.
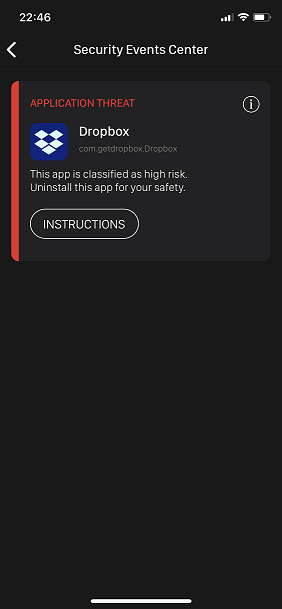
MaaS360 App Notifications
The user receives a MaaS360 notification as specified in the MP_HighRisk.
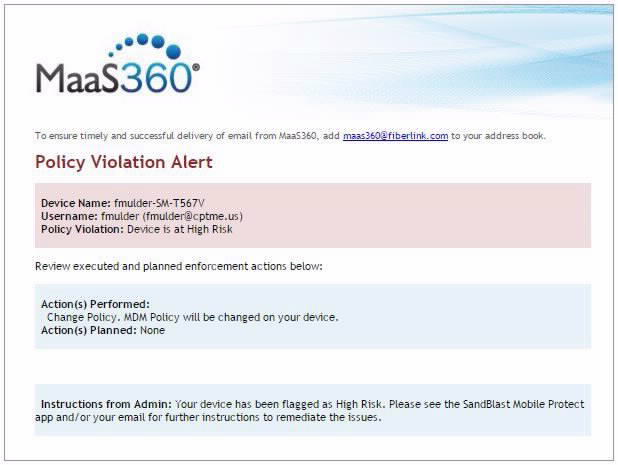
MaaS360 Email Notification
The user receives an email from the MaaS360 system, as specified in the MP_HighRisk_Rules.
Administrator View on the Harmony Mobile Dashboard
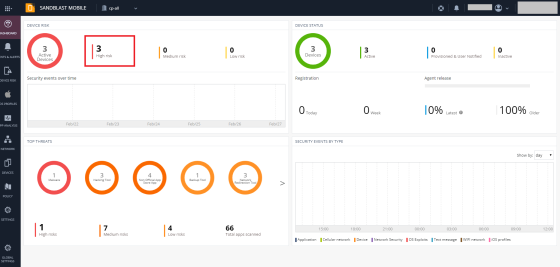
On the Harmony Mobile Dashboard the Administrator can see the devices at High Risk.
-
On the Infinity Portal, go to Device Risk > High Risk section.
A list of the Devices At Risk is displayed in the Device Risk section.
Example:
-
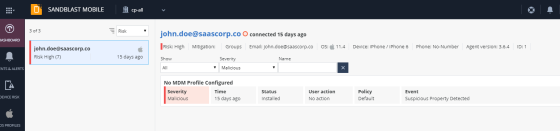
Click High Risk.
The list of devices at High Risk state is displayed.
-
Select the specified device on the left-side list.
You can see that the blacklisted app causes the High Risk state.
Example:
Administrator View on the MaaS360 Portal
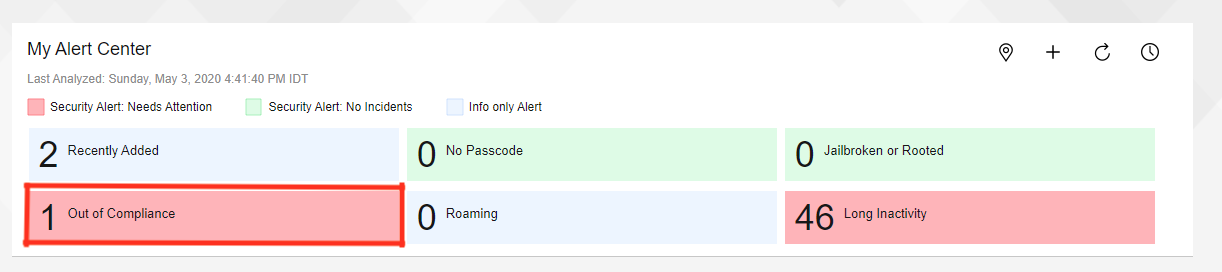
In the MaaS360 Portal from the Home tab, the Administrator can that one or more devices are Out of Compliance.
-
Clicking the Out of Compliance button, the Administrator is presented with a list of the devices currently Out of Compliance.
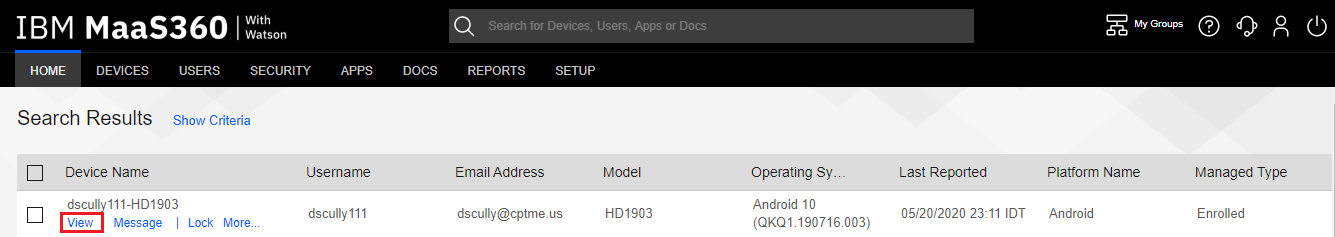
-
Clicking the View link under the device of interest will open the Device Details view displaying the Summary screen.
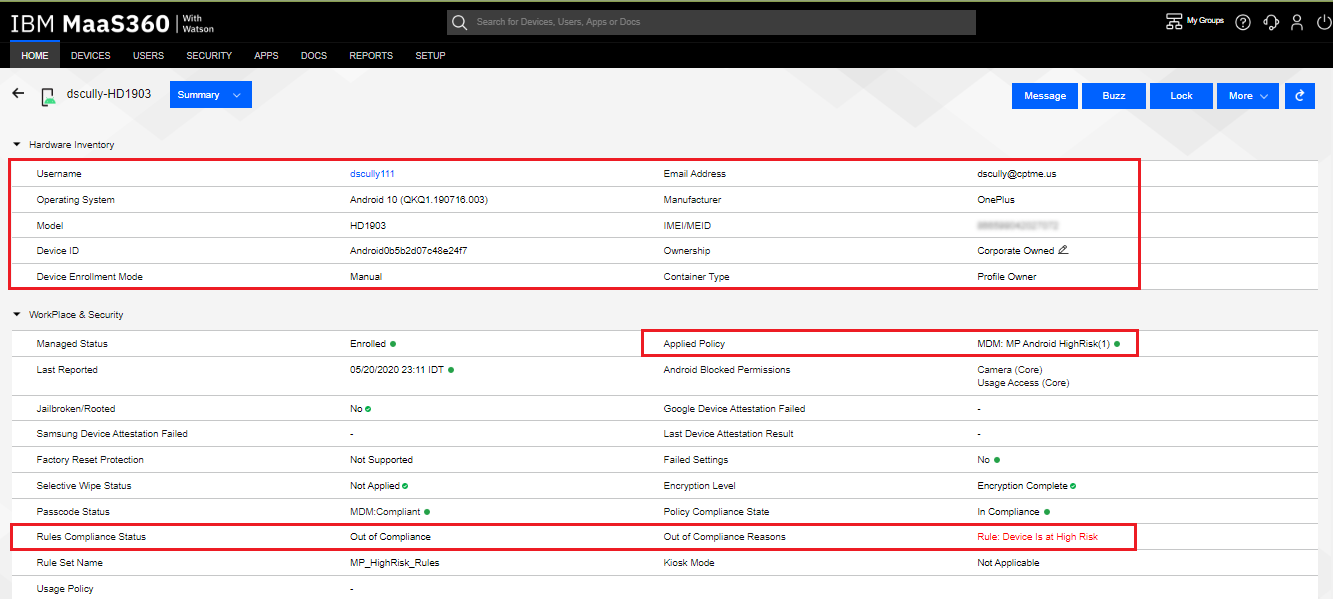
-
Clicking on the Summary drop-down menu, the Administrator can choose Security & Compliance details.
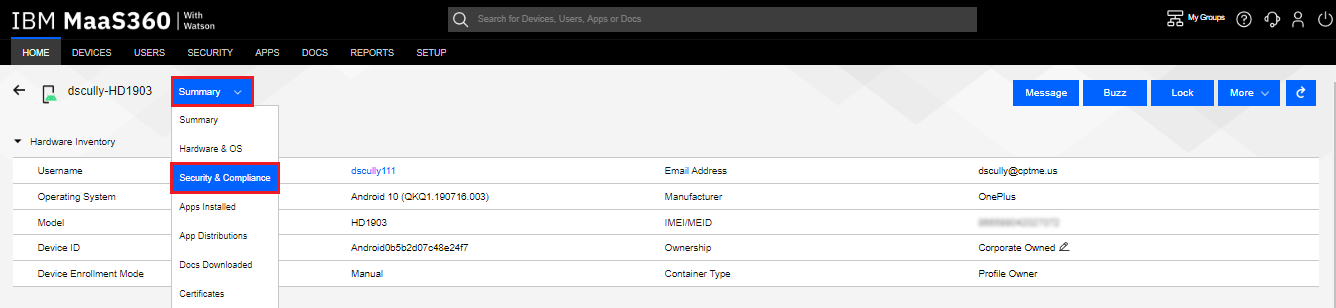
-
The Administrator can see that the device is Out of Compliance because of the device belongs to the MP_Android_HighRisk policy, with the compliance rule
 Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. of Device is at High Risk under the compliance rule set MP_HighRisk_Rules being applied.
Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. of Device is at High Risk under the compliance rule set MP_HighRisk_Rules being applied.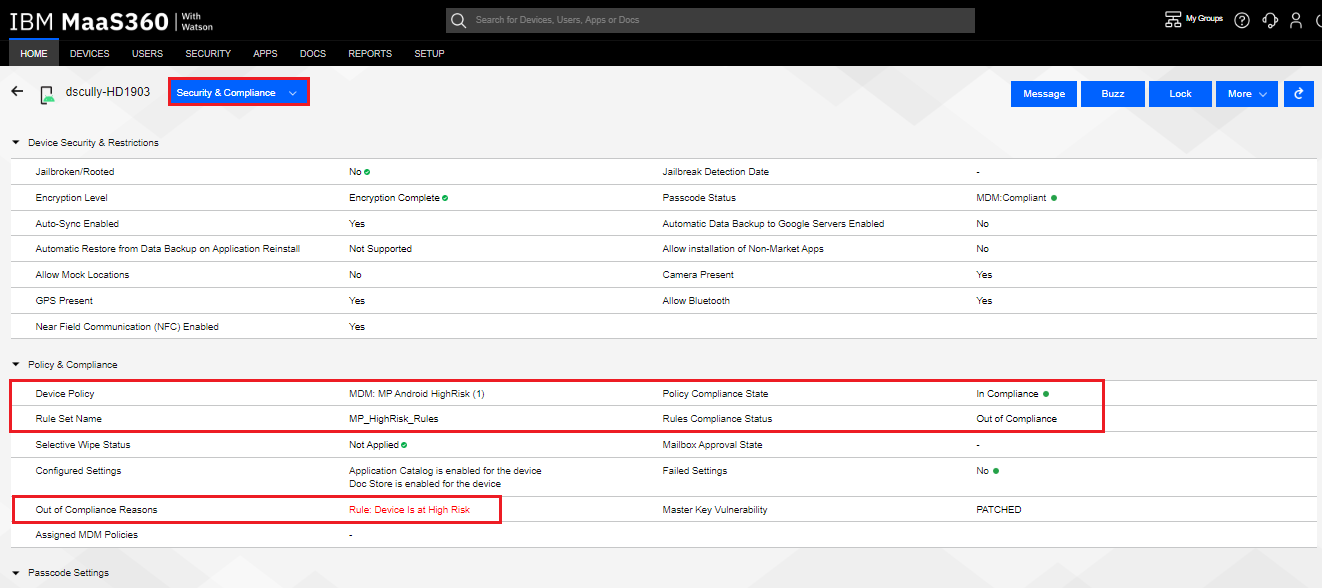
-
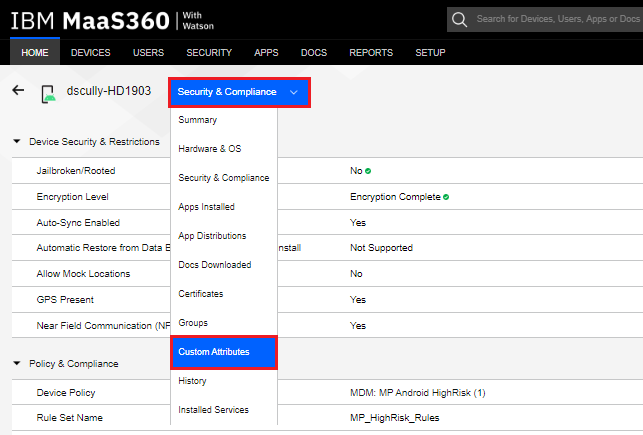
Clicking on the Security & Compliance drop-down menu, the Administrator can choose Custom Attributes details.
-
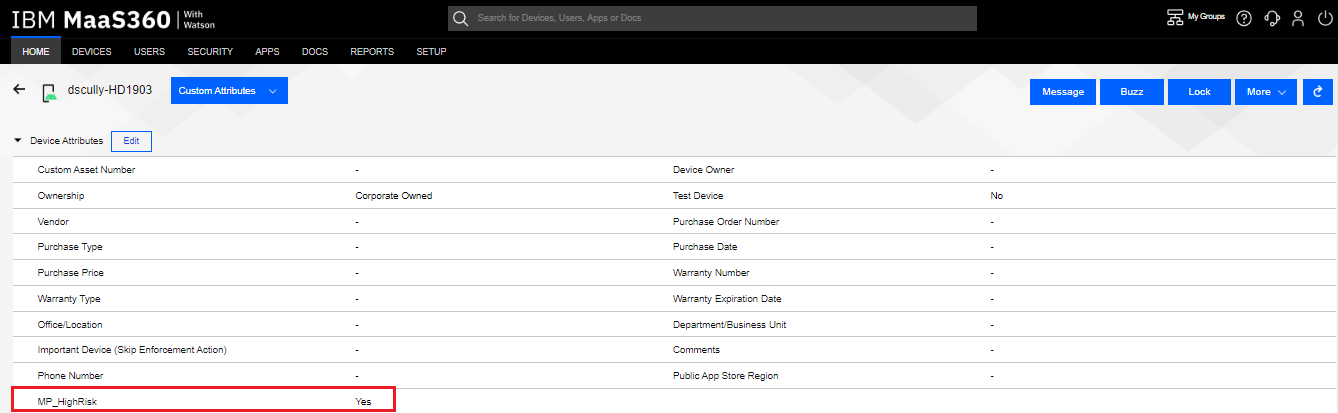
The Administrator can see which custom attributes are currently set. The device has the MP_HighRisk set to Yes.
-
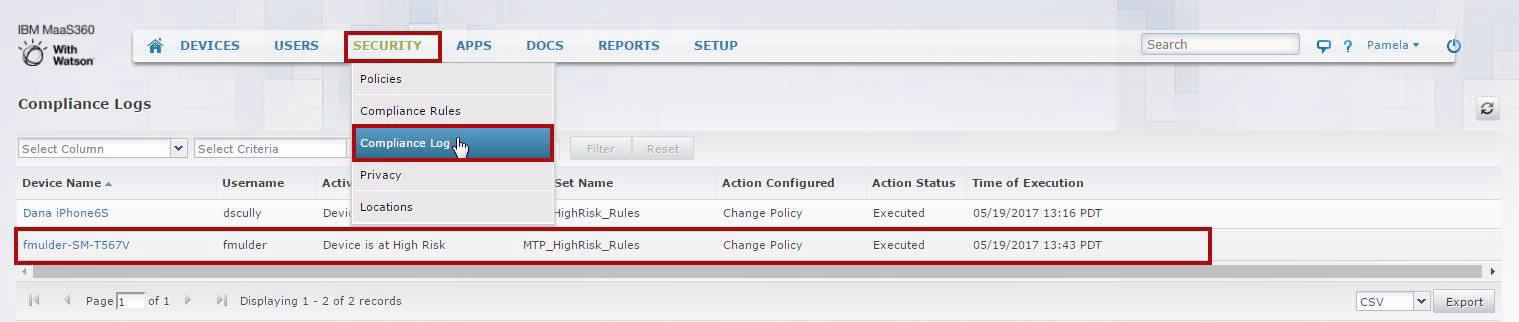
Navigating to Security > Compliance Logs, the Administrator can view the active Compliance Events.