Applying the Harmony Mobile Protect app Configuration and Policy Enforcement
Deploying the Harmony Mobile Protect app on the Devices
|
|
Notes:
|
If you used the Zero Touch deployment you can skip this section. The devices will be automatically activated and your users will have to approve a few permissions, according to the policy defined for the user group in Harmony Mobile dashboard, for example Location permission or Notification access.
Note that for Android devices, Android Enterprise is mandatory for the Zero Touch deployment process.
Registration of an iOS Device
After the device is enrolled to the Citrix Endpoint Management and the device is synchronized to Harmony Mobile, the CHKP_Status device property will be set to "Provisioned".
Procedure for the User:
-
Register your device.
-
Tap INSTALL on the Harmony Mobile Protect app.
The Protect app is deployed on the iOS Device.
-
-
Launch the Protect app to finish the registration.
Citrix Endpoint Management system automatically configures the registration server and the key in the Protect app.
-
Follow the on-screen instructions to enable Notifications, Location, and Network Security.
Example:
-
Tap Allow to allow Harmony Mobile Protect app to add the needed VPN Configuration profile, when On-device Network protection is enabled.
Registration of an Android Device
-
Harmony Mobile Protect app is pushed and installed to the device by Citrix Endpoint Management
-
Launch the App to finish its deployment and registration to Check Point Harmony Mobile.
The Harmony Mobile Protect app is automatically registered.
Example:
-
Tap Continue
-
Enable security settings Allow all required permissions
-
Tap Enable
-
The Harmony Mobile Protect app scans the system. See the state of the device on the display.
Example:
iOS Devices
Android Devices

Testing High Risk Activity Detection and Policy Enforcement
If the user’s device is determined to be at risk either due to a malicious app or malicious activity, the Harmony Mobile system notifies the User via in-app notifications as well as updates the risk state by setting the appropriate CHKP_Risk tag to the Citrix Endpoint Management system for that device.
Citrix Endpoint Management receives the state change, and upon recognizing the set Device Property being tied to Policies/Actions, enacts those policies/actions.
In the following example, the Administrator will blacklist an app, such as in our example "Dropbox". As a result, all devices with " Dropbox " installed will be identified to be at High Risk (CHKP_Risk = High) due to the blacklisted app being installed on the device. The Harmony Mobile Dashboard will notify the user, and mark the device with CHKP_Risk to High to the Citrix Endpoint Management system. The Citrix Endpoint Management system will then enforce policy actions specified in the policies/actions. This mitigation process was the one we created in Creating a Mitigation Process.
Blacklisting a Test App
|
|
Note - When you blacklist an app, all release versions and OS types of this app are blacklisted. Select Apply only to this version option to blacklist the specified version only. |
-
Log into the Harmony Mobile Dashboard.
-
Go to Forensics > App Risk tab and select for the app you wish to blacklist.
Example:
-
Go to Global Policy and click Edit.
A Changing application policy-Global window pops up.
-
From the New Policy drop-down menu, select Black Listed.
-
In the Audit Trail note field, enter a reason for this change.
-
Click OK.
The user receives a Harmony Mobile Protect app notification to indicate that the blacklisted app (for example, Box) is not allowed by the Corporate Policy.
View of Device at Risk
Harmony Mobile Protect App Notifications
The user receives a Harmony Mobile Protect notification indicating that the blacklisted app is not allowed by Corporate Policy, in our example "Dropbox".
Citrix Endpoint Management In-App Notification
The user will not be to open the Citrix Mail app as specified in the AppLock device policy.

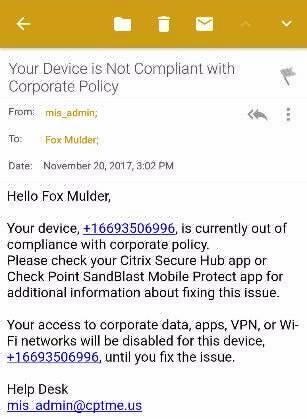
Citrix Endpoint Management Email Notification
The user receives an email from the Citrix Endpoint Management system, as specified in the "SBM_HighRisk" Actions policy.
Administrator View on the Harmony Mobile Dashboard
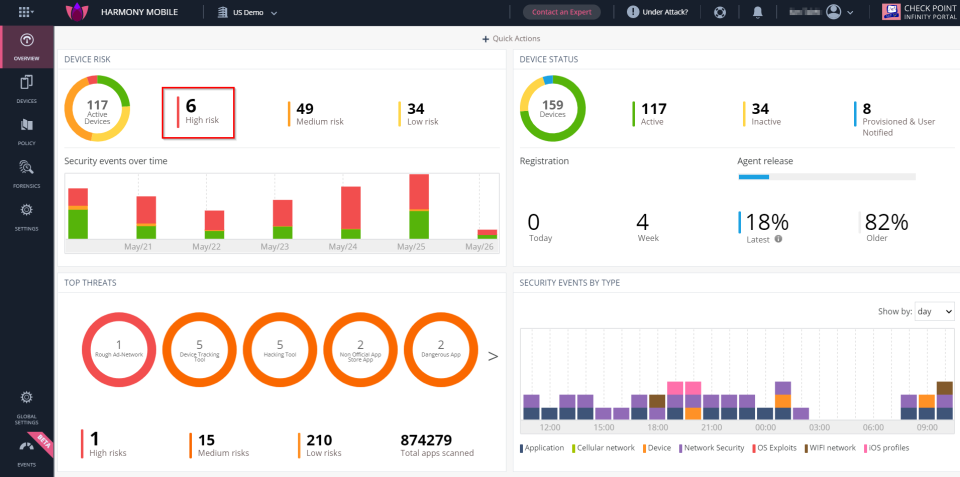
On the Harmony Mobile Dashboard the Administrator can see the devices at High Risk.
-
On the Infinity Portal, go to Device Risk > High Risk section.
A list of the Devices At Risk is displayed in the Device Risk section.
Example:
-
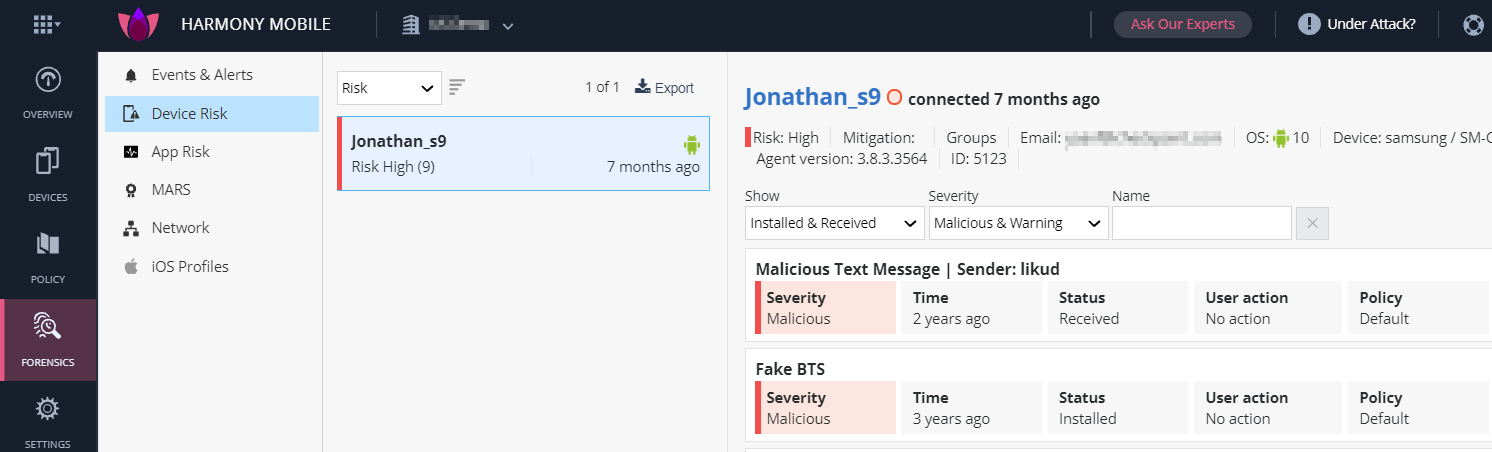
Click High Risk.
The list of devices at High Risk state is displayed.
-
Select the specified device on the left-side list.
You can see that the blacklisted app causes the High Risk state.
Example:
Administrator View on the Citrix Endpoint Management Console
-
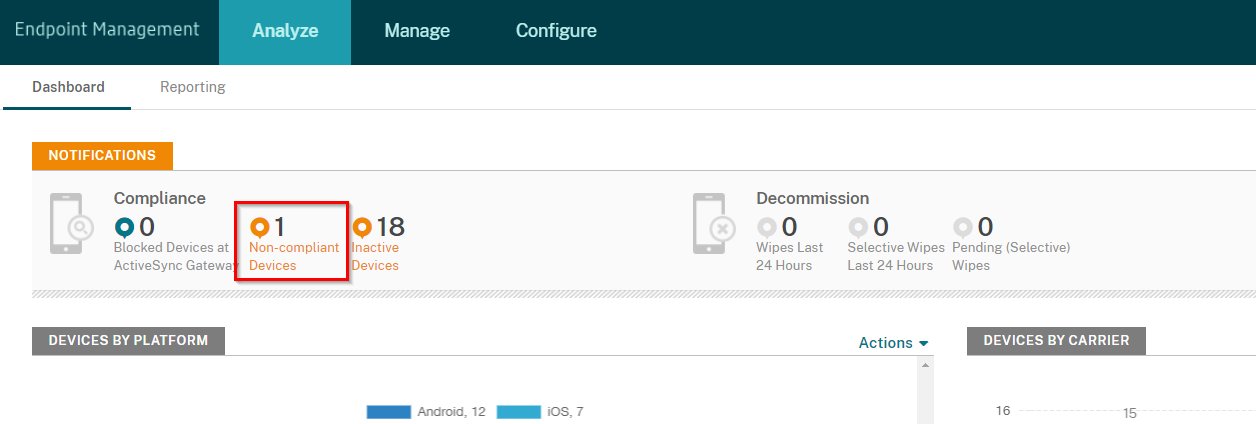
In the Citrix Endpoint Management Console on the Analyze view, the Administrator can see that one or more devices are Non-compliant or Inactive.
-
In the Citrix Endpoint Management Console from the Devices View, the Administrator can see that Fox’s device is Out of Compliance
 Check Point Software Blade on a Management Server to view and apply the Security Best Practices to the managed Security Gateways. This Software Blade includes a library of Check Point-defined Security Best Practices to use as a baseline for good Security Gateway and Policy configuration. and that the CHKP_Risk device property is equal to High.
Check Point Software Blade on a Management Server to view and apply the Security Best Practices to the managed Security Gateways. This Software Blade includes a library of Check Point-defined Security Best Practices to use as a baseline for good Security Gateway and Policy configuration. and that the CHKP_Risk device property is equal to High. -
Clicking the device’s name and selecting "Show more", the Administrator is presented with the device details view.
-
On the Properties tab, the Administrator can see that the device has a CHKP_Risk value of High.