Connecting the Harmony Mobile Protect app to your Device
To install the Harmony Mobile Protect app on your devices in your organization, you must first configure them to require the Harmony Mobile Protect app. For that, we need to link the Harmony Mobile App in our catalog to the User Provisioning![]() Check Point Software Blade on a Management Server that manages large-scale deployments of Check Point Security Gateways using configuration profiles. Synonyms: SmartProvisioning, SmartLSM, Large-Scale Management, LSM. Groups we created in Creating User Provisioning Groups.
Check Point Software Blade on a Management Server that manages large-scale deployments of Check Point Security Gateways using configuration profiles. Synonyms: SmartProvisioning, SmartLSM, Large-Scale Management, LSM. Groups we created in Creating User Provisioning Groups.
Optional: Create a mitigation process. See Creating a Mitigation Process.
General Workflow:
-
Assign the App Groups to the User Provisioning Group.
-
Create a compliance policy to uninstall / remove corporate apps from the device until the user installs the required apps on the device.
-
Create a Mitigation Process for devises-at-risk through the User Provisioning Group Risk.
Assign App to User Provisioning Group
-
On the BlackBerry UEM
 Unified Endpoint Management. An architecture and approach that controls different types of devices such as computers, smartphones and IoT devices from a centralized command point. console, go to Group > User.
Unified Endpoint Management. An architecture and approach that controls different types of devices such as computers, smartphones and IoT devices from a centralized command point. console, go to Group > User. -
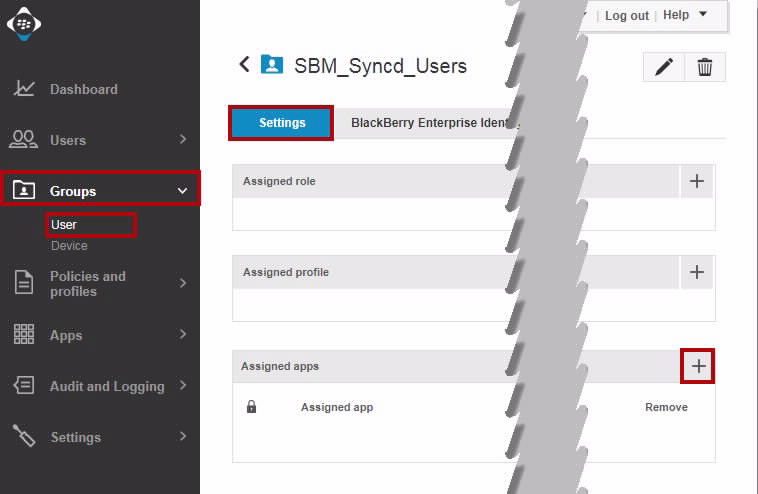
Search for the Provisioning Group SBM_Syncd_Users and Click it.
-
Click Settings tab.
-
In Assigned apps section, click +.
-
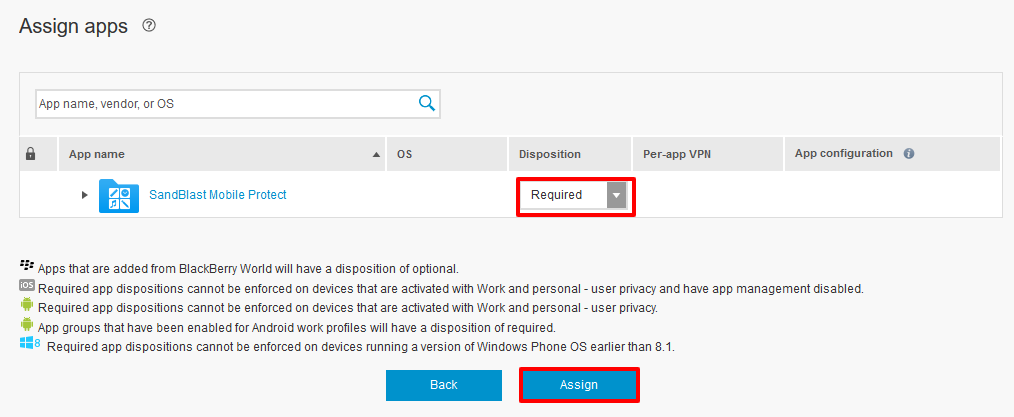
In the Assign apps window, select the App Group we created in Creating a Protect app Group.
-
Click Next.
-
In Disposition drop-down, select Required.
-
Click Assign.

|
Note - Repeat the steps in this section for "Users_At_Risk". This will prompt the users who belong to "SBM_Syncd_Users" to install the Harmony Mobile Protect app. Also, those users who are in the "Users_At_Risk" who uninstall the Harmony Mobile Protect app will be out of compliance |

|
Note - Repeat the steps in this section for "SBM_AD_Users" and "SBM_Local_Users", but change the "Disposition" to "Optional" instead of "Required". |
Creating a Compliance Policy for the Organization Devices
The Compliance![]() Check Point Software Blade on a Management Server to view and apply the Security Best Practices to the managed Security Gateways. This Software Blade includes a library of Check Point-defined Security Best Practices to use as a baseline for good Security Gateway and Policy configuration. Policies are activated on the devices that did not install the required apps.
Check Point Software Blade on a Management Server to view and apply the Security Best Practices to the managed Security Gateways. This Software Blade includes a library of Check Point-defined Security Best Practices to use as a baseline for good Security Gateway and Policy configuration. Policies are activated on the devices that did not install the required apps.

|
Note - In every organization, the customer configures the compliance policies according to the production environment, needs, and the internal security policy |
To create a Compliance Policy:
-
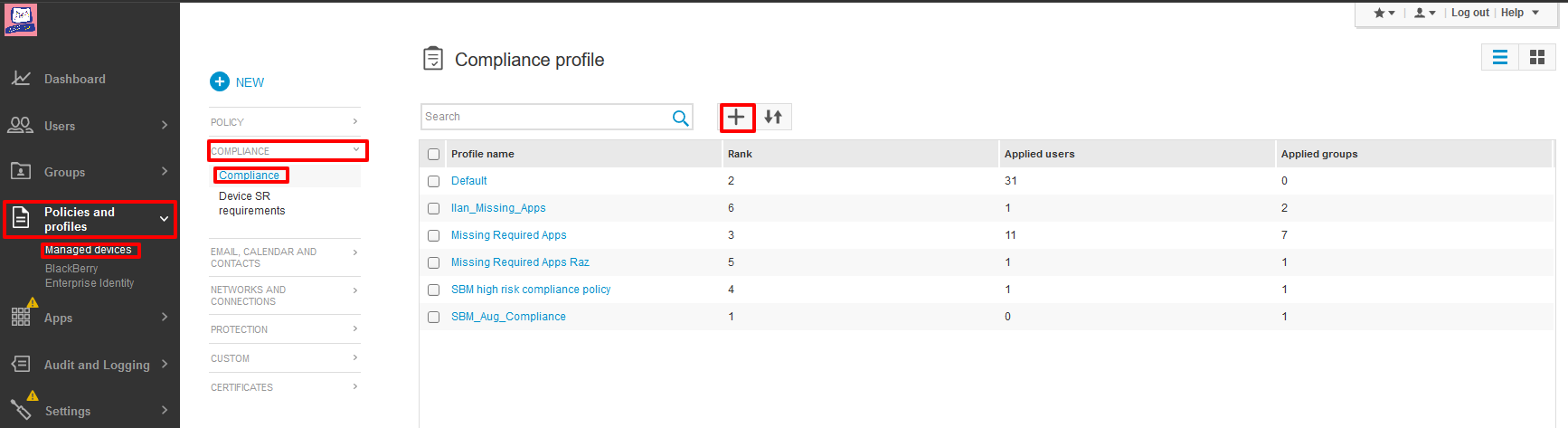
Go to Policies and profiles > Managed devices > Compliance > Compliance, and click +.
Example:
-
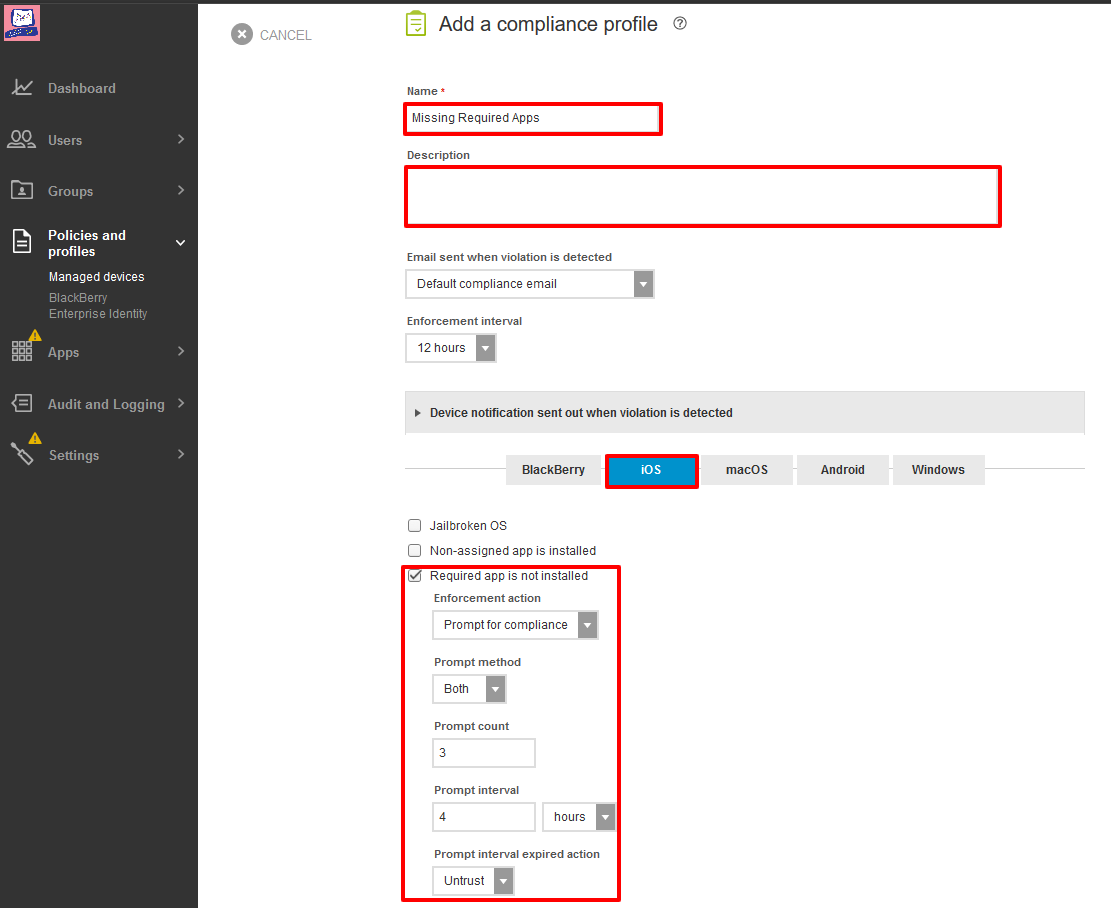
On the Add a compliance profile window, configure these settings:
-
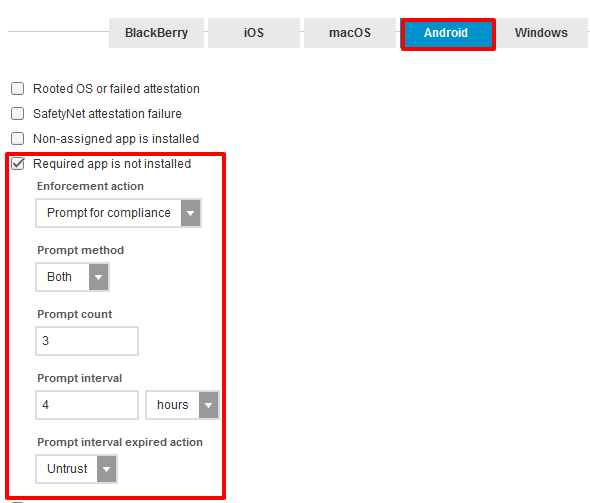
Select Android tab.
-
Select Required app is not installed and set appropriate actions to be taken if the user doesn't install the app.
Example:
-
Click Add.
Applying a Compliance Policy to User Provisioning Group
After creating a Compliance Policy, we need to assign it to User Provisioning Group.
-
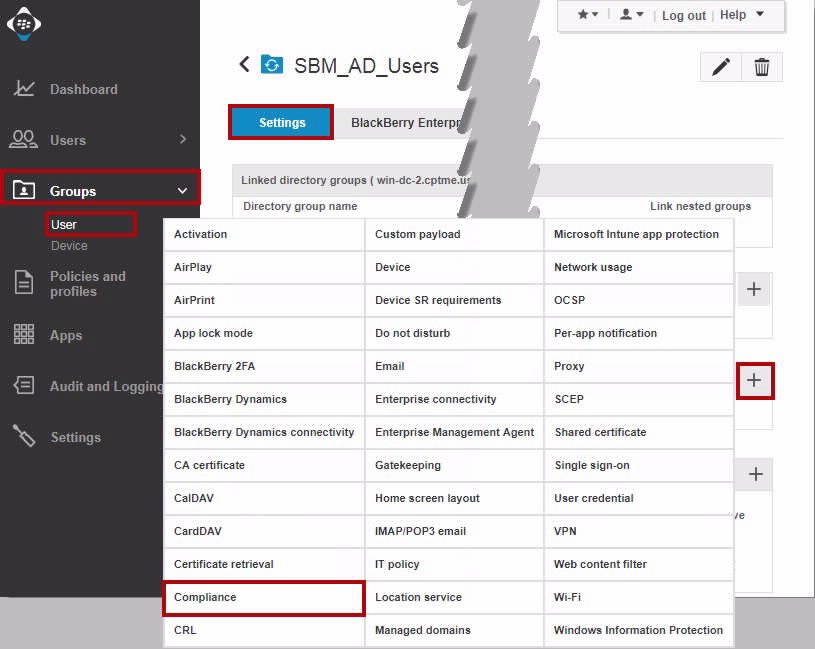
Go to Group > User.
-
Search for the Provisioning Group SBM_AD_Users we created in Creating User Provisioning Groups and click it.
-
Click Settings tab.

-
In Assigned profile, Click +.
-
Select Compliance from pop-up list
-
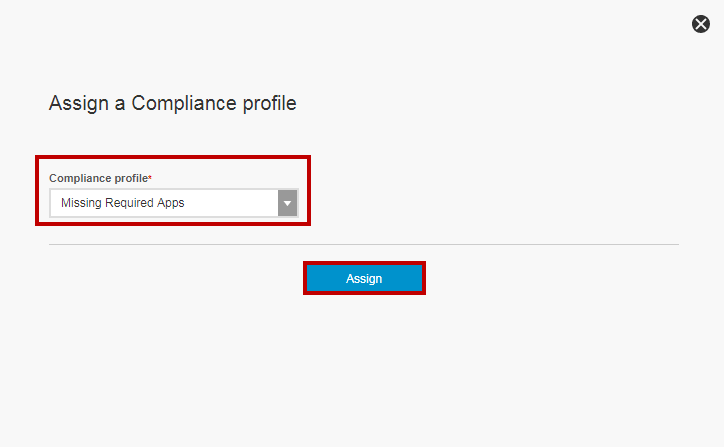
On the Assign a Compliance profile window, select the Compliance Policy we created in the previous section Missing Required Apps.
-
Click Assign.
Example:

|
Note Repeat these steps for "SBM_Local_Users", if you are using it. |
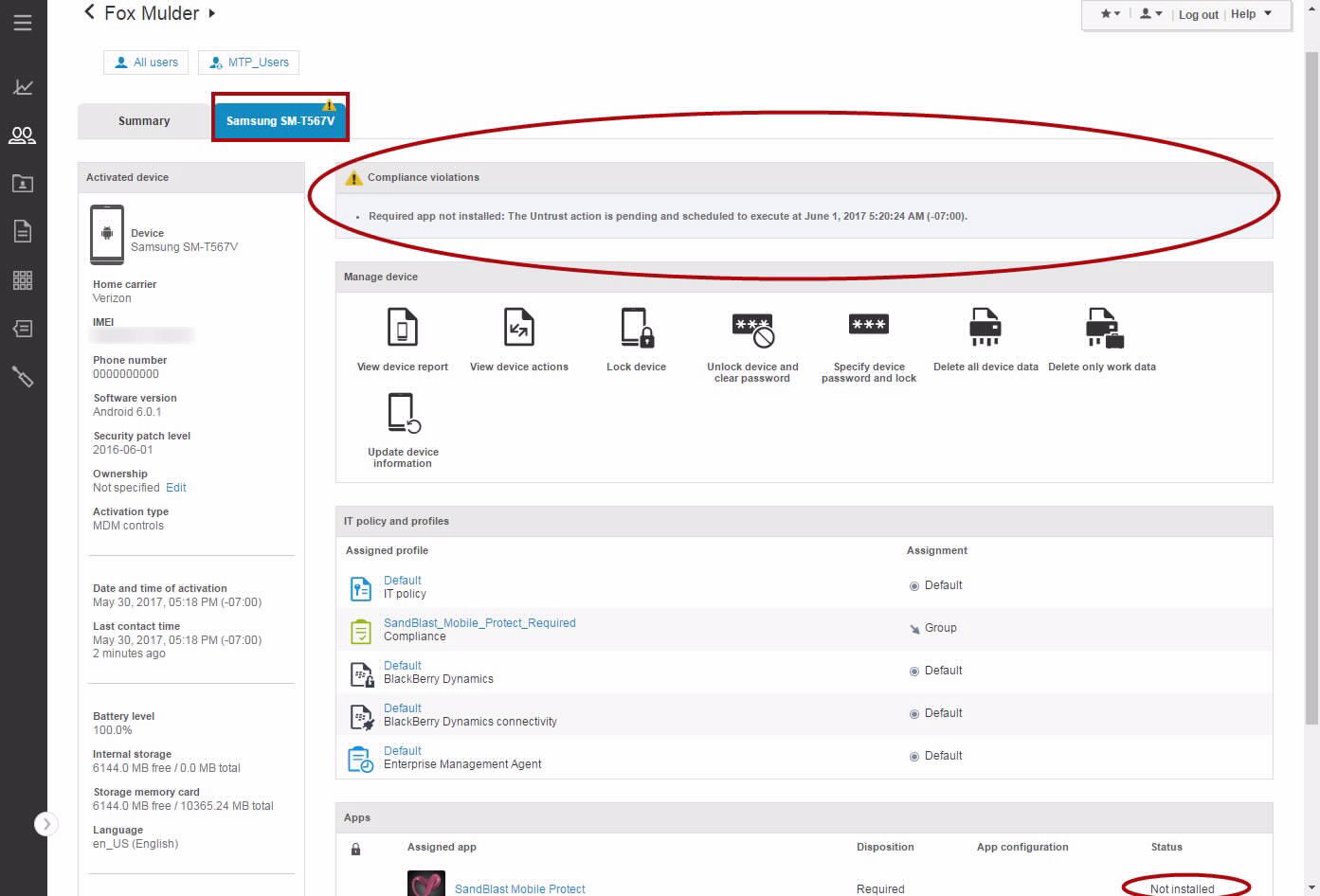
Device Out of Compliance - Missing Harmony Mobile Protect App

|
Note - Any device that belongs to the User Provisioning Group(s) which require the Harmony Mobile Protect apps to be installed ("SBM_Syncd_Users" and "Users_At_Risk") that hasn't installed the Harmony Mobile Protect app will be out of compliance. |
-
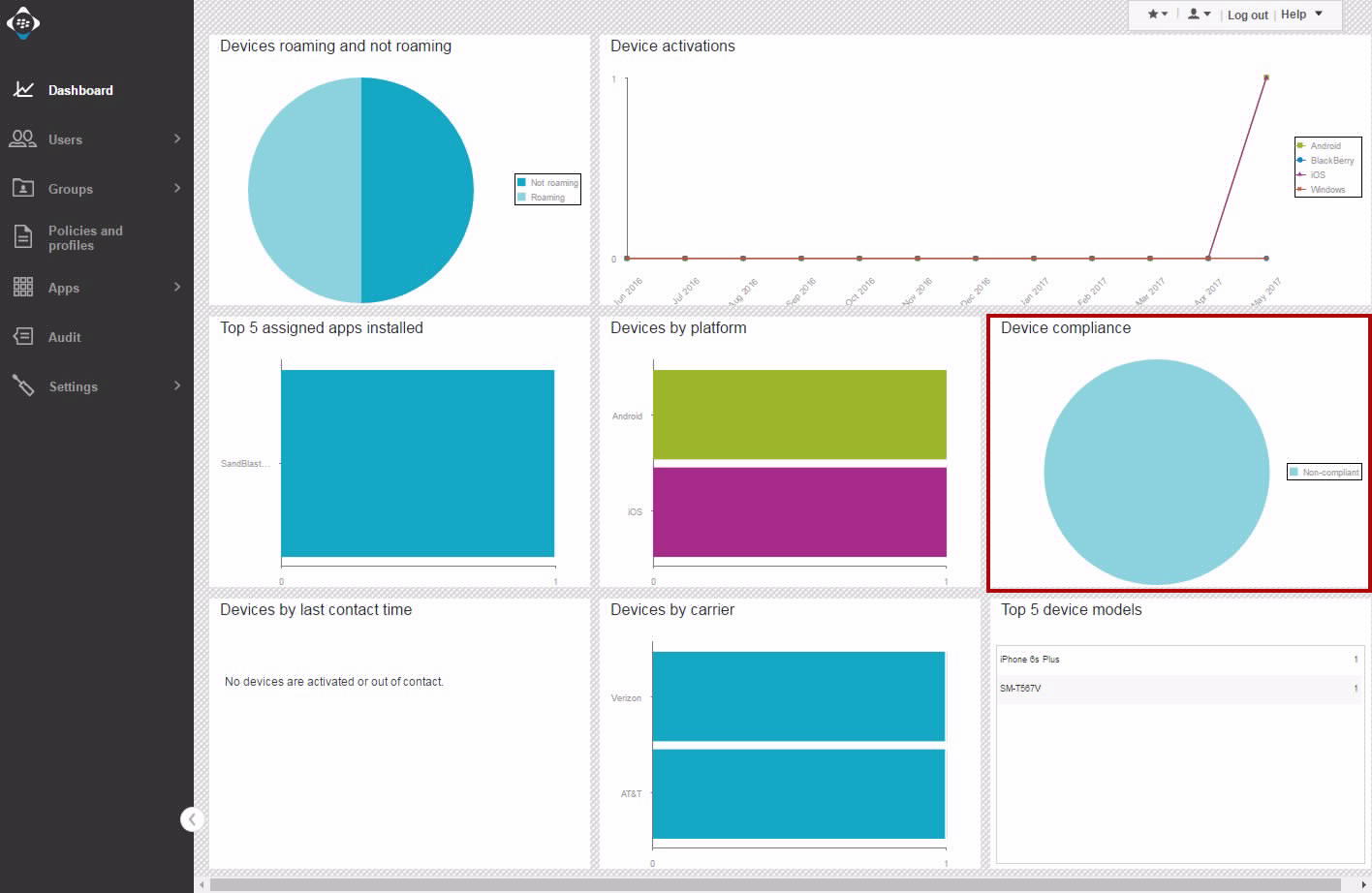
BlackBerry UEM Console Home Screen indicates an "Out of Compliance" issue.
Example:
-
Clicking on the "Non-compliant" pie piece, opens a reporting window.
-
Device Details View indicates an "Out of Compliance" issue.
-
The user receives an alert email as well as an in-app notification.
Creating a Mitigation Process
This procedure is optional.
To let the Blackberry UEM system identify the devices-at-risk and to enforce the configured compliance policies according to the risk level, you must apply the built-in Risk tags. The Harmony Mobile Dashboard uses these tags to label any device with the risk level that the Harmony Mobile analysis determines.
Creating IT Policies
We will create IT Policies that will be enforced on devices that are at risk. In this section, we will create an IT Policy that will be used to enforce restrict the At Risk device in some manner.

|
Note - We will show an example policy, but these enforcement policies are something that the customer should create for their environment and needs. In a production environment, the customer should configure the compliance and IT policies according to their internal security policy. |
The policy will specify the actions taken on At Risk devices. In our example, we will disable the camera, but you might create a policy that disables access to the corporate network or assets.
To add an IT policy:
-
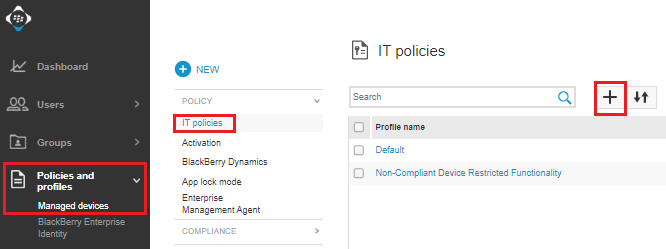
On the BlackBerry UEM console, go to Policies and profiles > Managed devices > Policy > IT policies and click +.
-
On the Add an IT Policy screen:
-
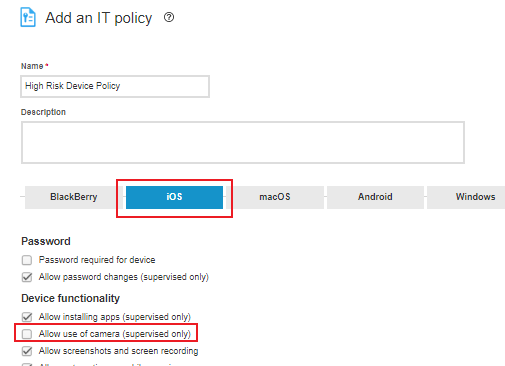
In the Name field - enter a name for the policy. (We recommend "High Risk Device Policy")
-
For iOS:
-
Select the iOS tab.
-
Under Device functionality, unselect Allow use of camera.
-
-
For Android:
-
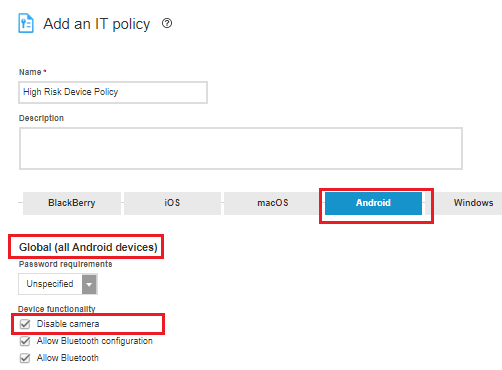
Select the Android tab.
-
Under Global (all Android devices) > Device functionality, select Disable camera.
-
Scroll to KNOX UEM > Device functionality, unselect Allow camera.
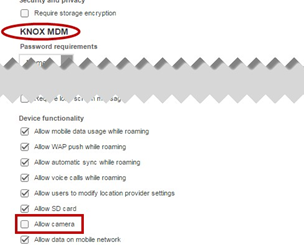
-
Scroll to KNOX Premium - Workspace > Device functionality unselect Allow camera.
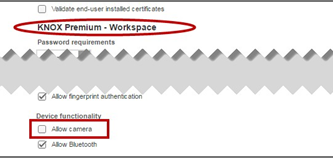
-
-
Scroll to the bottom of the screen and click Add.
-
Applying the Policy to the User Provisioning Group
Now that we have created the policy ("High Risk Device Policy") we want to enforce, we need to link this policy to our User Provisioning Group ("Users_At_Risk") we created in Creating User Provisioning Groups.
To assign an IT policy to group:
-
On the BlackBerry UEM console, go to Groups > User, find the user mitigation group you created. In our example "Users_At_Risk", and click the group name link.
-
On the group detailed view, select the Settings tab.
-
On the Settings tab, Click + on the Assigned Profiles section.
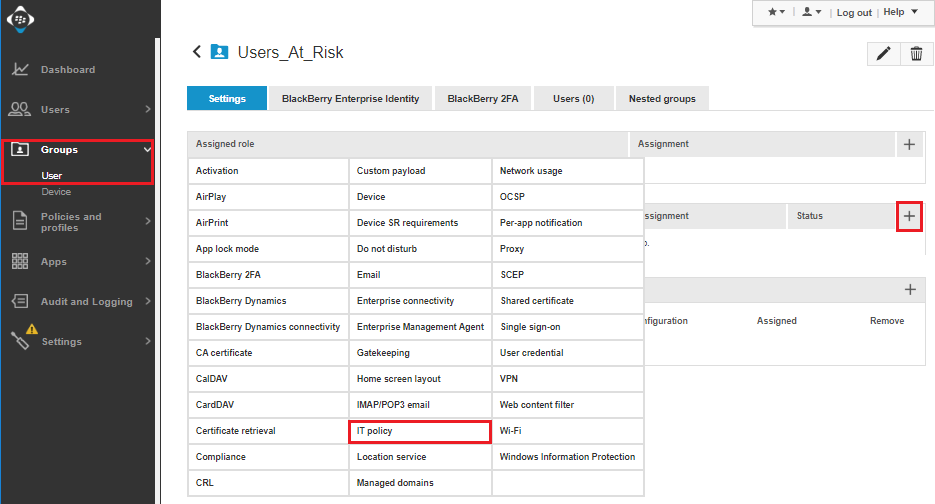
-
Select IT policy.
-
On the Assign an IT policy window, select the IT policy we created in Creating IT Policies, in our example "High Risk Device Policy".
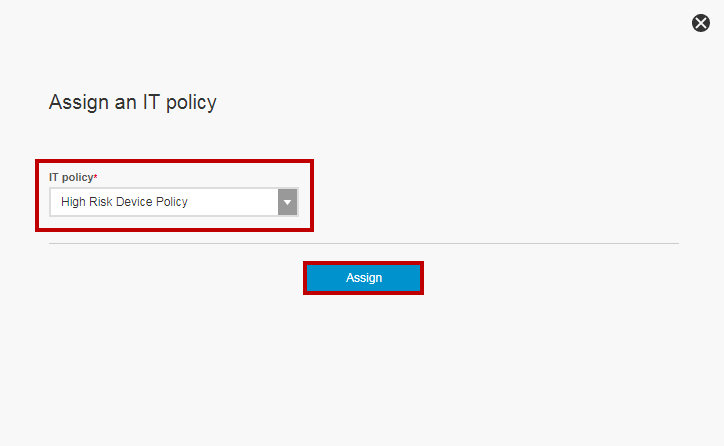
-
Click Assign.

|
Note - Now any device placed into the user groups, CHKP_Risk_High, CHKP_Risk_Medium or CHKP_Status_Inactive, which are nested under Users_At_Risk will have the policy actions in the IT Policy ("High Risk Device Policy") acted upon it. |