Introduction to Harmony Mobile Connector
|
|
Important Update - This documentation is deprecated as Gaia R80.40 has reached its end of support. For the latest information, refer to the Harmony Mobile Connector Installation Guide R81.20. |
Harmony Mobile Connector is a web-based application that integrates your Harmony Mobile dashboard with your on-premises corporate ecosystem (UEM, syslog or SIEM solution, SMTP server for sending emails and so on).
To protect users' Personally Identifiable Information (PII), the Connector encrypts device/user names, email addresses, and phone numbers when accessing the Harmony Mobile dashboard from the cloud. When accessed locally, within a secure on-premise environment, the dashboard displays decrypted PII, with the Connector decrypting the data in real-time.
Key features:
-
Harmony Mobile Connector serves as a local proxy that allows organizations to get rid of any incoming communications to their corporate network.
-
Integrates and supports all on-premises Mobile Device Management (MDM) and Unified Endpoint Management (UEM) solutions.
-
Advanced architecture that provides High Availability.
-
Secured browsing with support for multi-user and secure login to the Harmony Mobile dashboard from anywhere within the customer’s internal network.
This document describes how to install the Harmony Mobile Connector and provides the configuration instructions for different deployment scenarios.
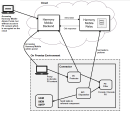
Solution Architecture
|
Component |
Description |
|---|---|
|
Cloud Components |
|
|
Harmony Mobile Backend |
|
|
Harmony Mobile Relay |
|
|
On-Premise Components |
|
|
Harmony Mobile Connector |
Harmony Mobile Connector is a proxy application that resides within the organization’s data center that provides an integration interface between your Harmony Mobile dashboard and your on-prem services. |
|
PII Protector |
|
|
API Dispatcher |
Routes incoming API tasks to the appropriate component (UEM, SIEM, SMTP). |
|
PII Filter |
Handles encoding and decoding of PII data. |
|
WWW (Remote Access) |
|
|
On-Premise Client (Local Access) |
|
|
UEM / SIEM / SMTP |
|