Forensics
In the Forensics tab, you can view all the security forensic data collected across the Enterprise.
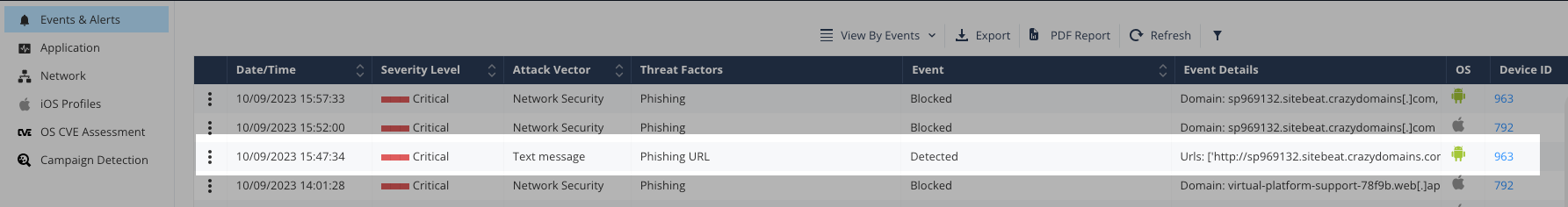
Events and Alerts
The Events & Alerts tab shows an audit trail of incidents and actions that occurred on the devices, for example, Application installation and Profiles detected on devices.
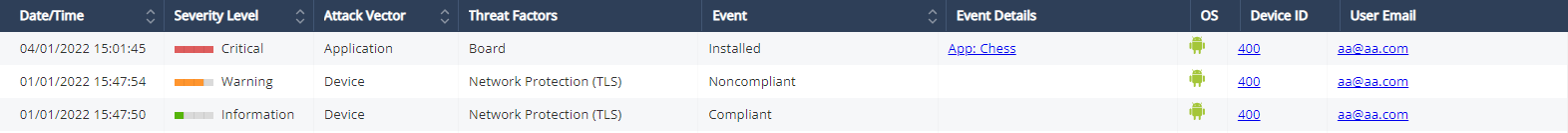
Events & Alerts table:
|
Item |
Description |
||
|---|---|---|---|
|
Date/Time |
Displays the date and time when the event occurred. |
||
|
Severity level |
|
||
|
Attack Vector |
Specifies the nature of the Event/Alert:
|
||
|
Threat Factors |
Specifies the threat factor for the event that occurred. Explains the reason for the severity level. |
||
|
Event |
Specifies the user or the action taken by the Harmony Mobile solution.
|
||
|
Event Details |
Additional details about the Event, such as name of application installed or removed Wi-Fi SSID |
||
|
OS |
Operating System of the device (iOS/Android). It is determined by the information received from the device when the application is installed. |
||
|
Device ID |
The device ID in the Harmony Mobile dashboard. |
||
|
User email |
Device user's email address. It is manually set by the Admin or automatically by UEM |
|
|
Note - For Android devices, you get a Phishing alert on the dashboard when Harmony Mobile detects and blocks a SMS phishing attempt on the mobile device. This feature works only if the end-user has granted access to Harmony Mobile Protect App to scan the SMS received on the device.
For more information on how to grant the access on the device:
|
Filtering the Events & Alerts Table
-
Click the
 icon above the Events & Alerts table.
icon above the Events & Alerts table.
The Filters pane appears on the right side.
-
Expand the required category and select the filter.
Exporting Events Data to CSV File
To export Events data to a CSV file, click Export above the Events & Alerts table.
The system creates a comma separated values file that can be opened in spreadsheet applications such as Microsoft Excel. Use filter to select the required information for the file.
If the number of events exceeds 10,000, processing the data may take time. So the export is performed offline and an email is sent to the registered address with the link to download the CSV file. The link is valid for 7 days. For privacy reasons, PII data is obfuscated in the CSV file.
Generating the Mobile Security Report
The Mobile Security Report provides an overview of the security status of all the mobile devices associated with your account. You can generate and download this report in PDF format whenever you need it, or set up a schedule to automatically generate and receive it on a weekly or monthly basis.
There are two types of security reports:
-
Operational report - Contains the Operational Overview details such as Device Status, Licensing Information, Mobile Models and so on.
-
Full report - Contains both the operational overview and the detailed security status of all mobile devices in your account. It provides full visibility to the Harmony Mobile usage.
To generate the report, click PDF Report above the Events & Alerts table.

The system generates and downloads the report in this format:
mobile-security-report-yyyy-mm-dd-hh-mm
To select the report type and schedule the Mobile Security Report, go to Settings > Administrators > Notifications. See Scheduling Mobile Security Report.
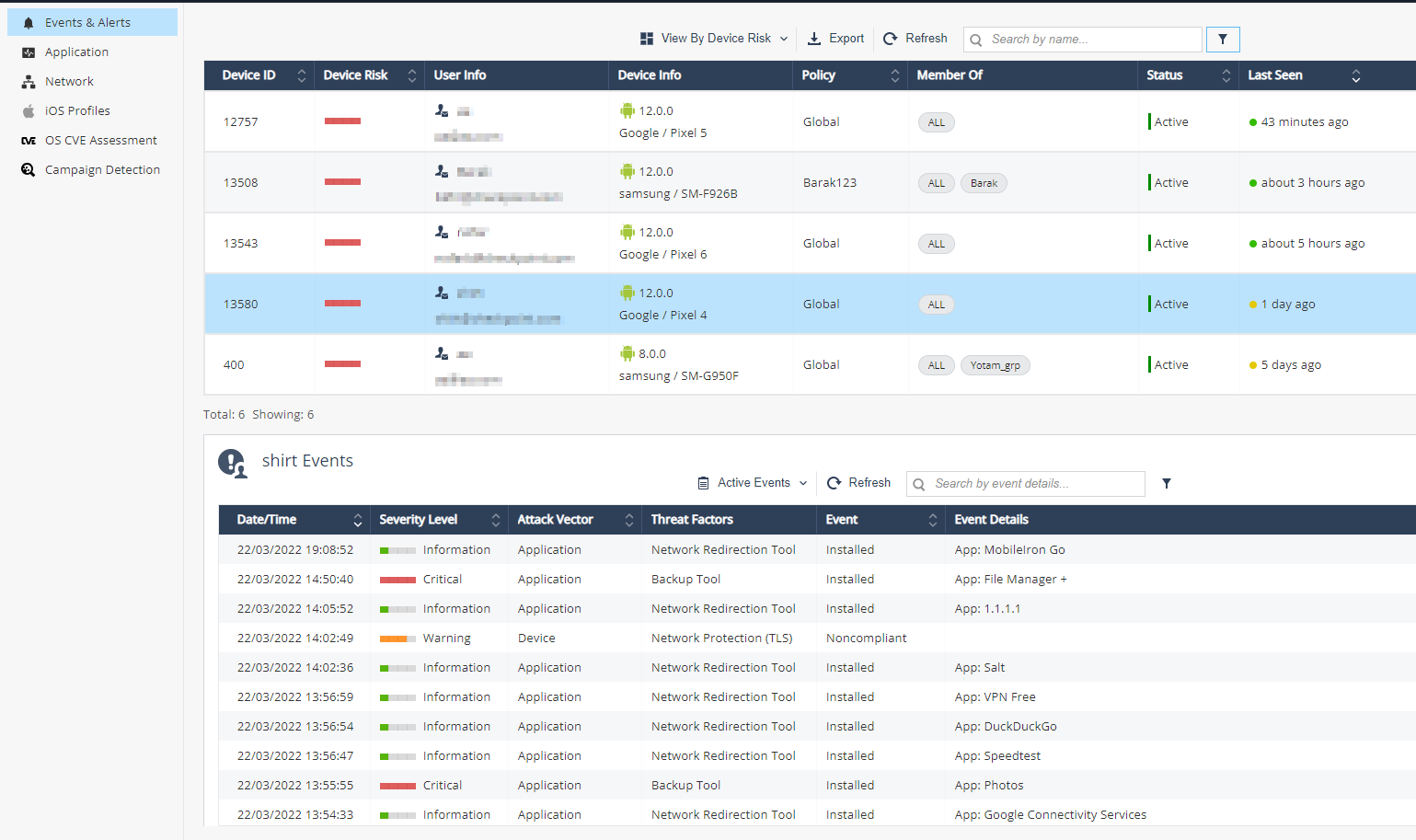
Viewing Events by Device Risk
In addition to Events view, you can view the events according to device risk (not available when privacy mode is enabled):
This view shows all the necessary risk information per device in the system, and the number of the devices with a specific risk level.
The top table shows the list of devices with their risk levels and the number of devices.
|
Item |
Description |
|---|---|
|
Device Risk |
Device risk is determined by both the accumulative threats risk levels found on it and different settings present on the device. (Debugging tools, Jailbreak, Developer Tools, and so on). Risk levels:
|
|
User Info |
User name and email as configured in the devices screen. |
|
Device Info |
Device Info determined by the information received from the device post the Protect installation:
|
|
Policy |
The device policy, determined according to the device group. Can be Global or custom. |
|
Member Of |
The device groups. |
|
Status |
Indicates the device current state:
|
|
Last Seen |
Last seen field indicates the last time the device communicated with Harmony Mobile Servers. |
You can filter every column in the table:
-
Click Filter
 above the table.
above the table. -
On the Filters pane on the right side, select the information you want to view.
-
You can also export
 the mobile devices information from the table to CSV file, which creates a comma separated values file that can be opened in spreadsheet applications such as Microsoft Excel. Use filter to select the required information for the file. Later you can use those details to approach end-users and instruct them how to remove the risk off their mobile devices, or other related actions.
the mobile devices information from the table to CSV file, which creates a comma separated values file that can be opened in spreadsheet applications such as Microsoft Excel. Use filter to select the required information for the file. Later you can use those details to approach end-users and instruct them how to remove the risk off their mobile devices, or other related actions.
The lower table on the screen shows the chosen device row events details.
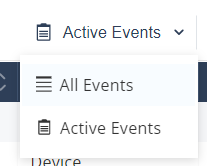
This table has two modes:
-
Active Events (default): Shows only the active events on the device.
-
All Events: Shows active and historic events.
You can filter every column in the table:
-
Click Filter
 above the table.
above the table. -
On the Filters pane on the right side, adjust information you want to view.
Application
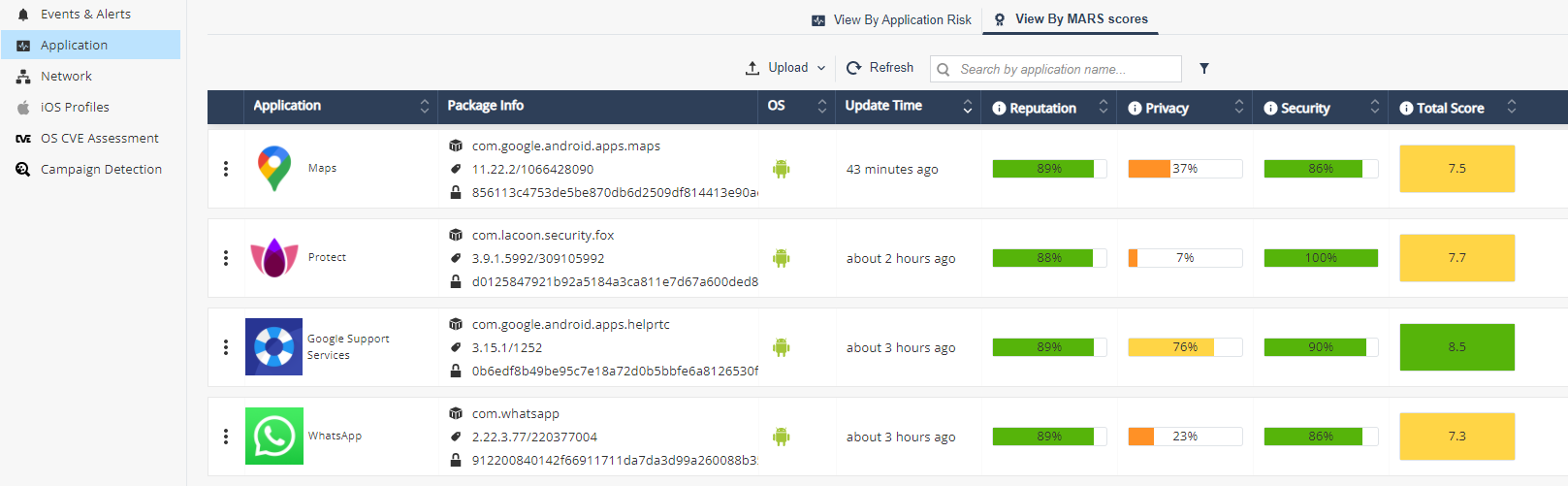
You can view an application by Application risk or by MARS score.

View By Application Risk
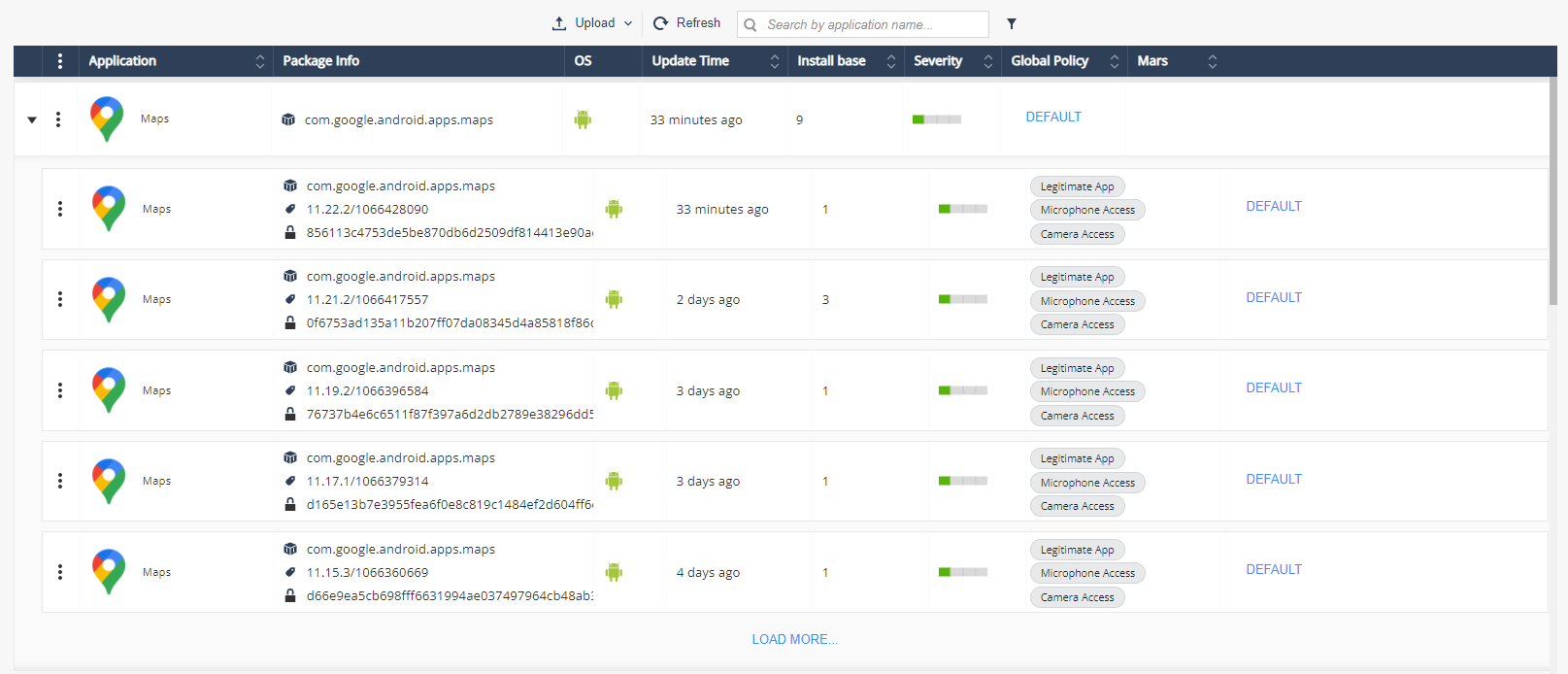
Applications Risk view is the main screen for risk analysis of different applications installed on the corporate devices. The applications are categorized to help the administrators understand the risk level. Click on each category to find the corresponding risk level.

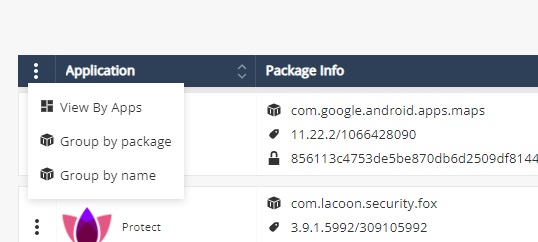
You can arrange the application list according to package and name:
Application data:
|
Item |
Description |
|---|---|
|
Application |
Name of the application. |
|
Package Info |
|
|
OS |
Application platform:
|
|
Update Time |
Indicates the last time the application was updated. |
|
Install Base |
The install base tells the administrators the current count of this app version that is currently installed within their environment. |
|
Global risk level |
Risk level of the application in the Global policy. |
|
Risk level by policy |
Risk level of the application in all other policies. |
|
Severity |
Highest risk level specified for the application in Application Exceptions across all the policies. For example, if the risk level of an application is High in policy 1, Medium in policy 2 and Low in policy 3, then the Severity is High.
|
|
Global Policy |
The Global policy of the application:
Click on the policy will direct to Application Policy section with the chosen application details. |
-
You can filter every column in the table:
-
Click Filter
 above the table.
above the table. -
On the Filters pane on the right side of the window, adjust information you want to view.

Note - If you filter for a Severity Level, the Severity column may not match the specified filtered risk level. This is because the Severity column always shows the highest risk level specified for the application in Application Exceptions across all policies and at least one policy has the filtered risk level for the application.
For example, if you filter for None and if the Severity column shows High for some applications, then it indicates that these applications' risk level is set to None in at least one of the policies.
-
-
Click
 .
. -
App Report: Generates application report
-
Reanalyze: Send application to reanalyzed
-
App view: Opens an extended application details view
-
Policy:Directs to the application policy section.
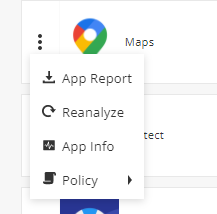
-
Application Overview
Click on the application row or on the App View option to open the application overview:
Severity
Severity indicates the risk level of the analyzed application. The possible values are:
-
High – Indicates that the app is malicious or contradicts company policy.
-
Medium – Indicates a potential threat by a legitimate application or configuration which contradicts the company policy.
-
Low – Indicates the app might perform potentially risky behavior. This might be caused by a legitimate app which uses an unusual ad network or an app which has access to the device contacts with no reasonable explanation, but no potential risk is applied.
-
No Risk – Indicates an app is legitimate or complies with company policy.
Install Base
The install base tells the administrators the current count of this particular version of the app that is currently installed within their environment.
At the bottom of the page you can locate information of where this app is installed in the environment (only if the app presents a risk to your organization). See Installations for a list of devices on which the app is installed.
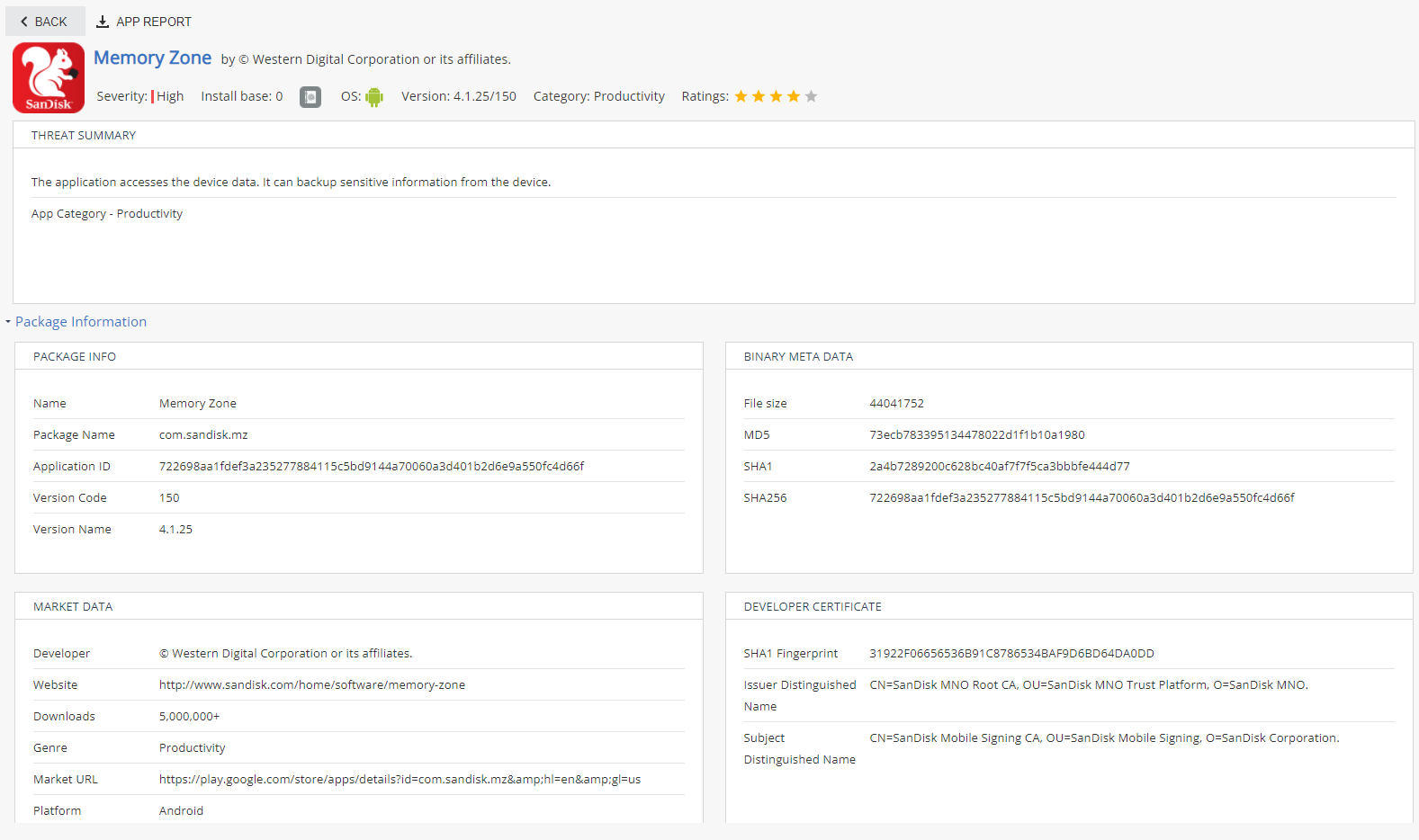
Package Information
Package Information includes detailed information about these:
-
Package Info
-
Binary Meta-Data
-
Market Data
-
Developer Certificate Data

Capabilities Summary
This panel provides an overview of what this application can do.

Capabilities Details
This panel provides additional details about the capabilities of this application.
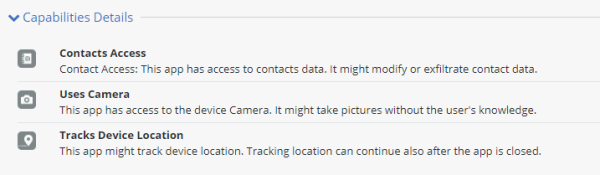
Exploits
Exploits panel appears only on malicious apps which use and exploit the OS vulnerability. It displays detailed information about the exploit and shows the risk level on a 1 to 10 scale.
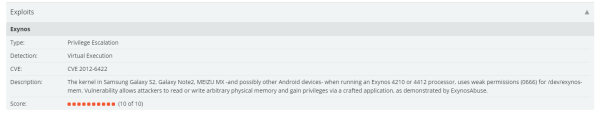
Cloud Hosting Services
This section displays a listing of any cloud services used by the app.

Behaviors
This section displays a collection of characteristics of the app called identifiers. Identifiers are used to declare the current risk level of the app.
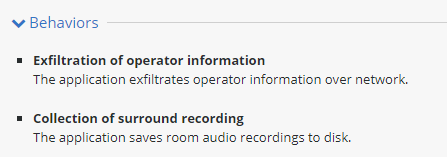
Installations
The Installations table displays the list of devices where the selected application is currently installed.
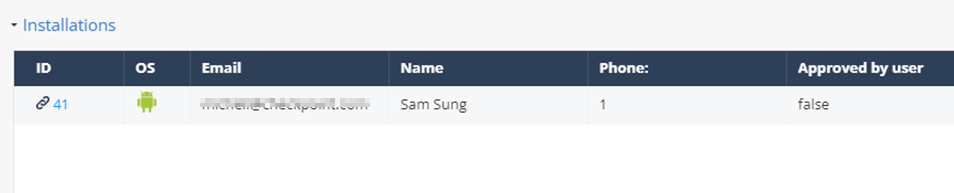
|
|
Notes -
|
Network
If the app is designed to use the network for specific reason such as send information to a specific URL, this address will be shown in this section.

Application Permissions
The Application permissions panel displays the app permissions and the risk level it implies.

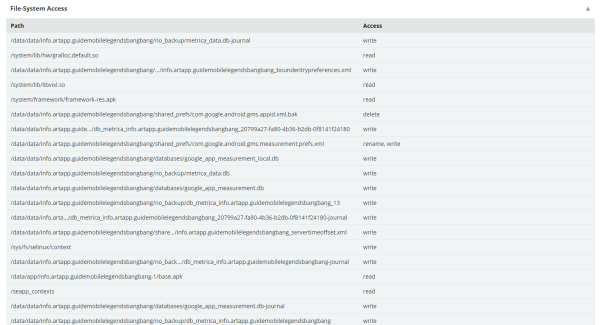
File System Access
This section displays all of the access permissions this app has to the device file system.
MITRE ATT&CK Matrix
MITRE ATT&CK is a globally accessible knowledge base of adversary tactics and techniques based on real-world observations. When Harmony Mobile detects a malicious application, it uses the MITRE ATT&CK tactics and techniques to categorize and represent the risks and damages that this application may cause.
For more information about the MITRE ATT&CK Matrix, see https://attack.mitre.org/techniques/mobile/
|
|
Note - The MITRE ATT&CK Matrix is available only if the application contains malware. |
To view the MITRE ATT&CK Matrix for an application:
-
Go to Forensics > Application.
-
Do one of these:
-
If the application was installed on the tenant device, click View Application Risk.
-
If the application file or URL was uploaded for analysis, click View MARS scores.
-
-
Click the application in the table to view its details.
 Note - If you selected View MARS scores in step 2, click the application and then click App Info to view the application details.
Note - If you selected View MARS scores in step 2, click the application and then click App Info to view the application details. -
To view the attack technique description, click any of the MITRE ATT&CK Tactics (for example, T1532: Data Encrypted).
The system opens a web page on the MITRE ATT&CK website that shows the description of the specific attack technique. -
To view the complete MITRE ATT&CK Matrix for the application, click Open MITRE ATT&CK full table.
This matrix highlights the tactics and techniques used for the application.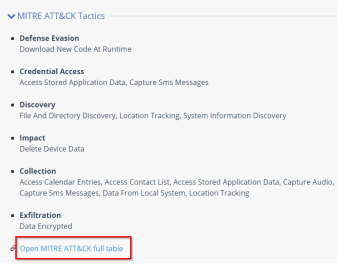
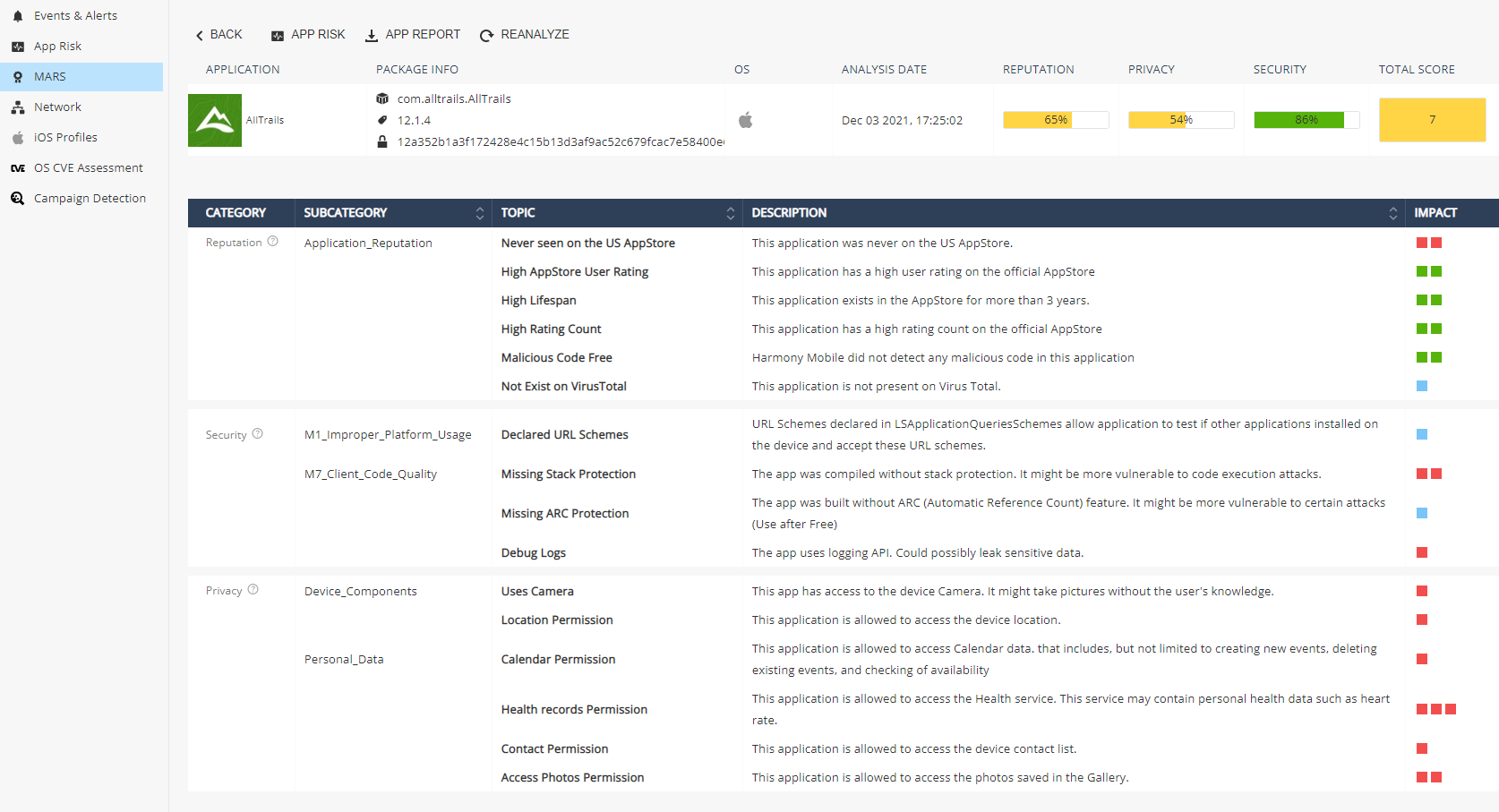
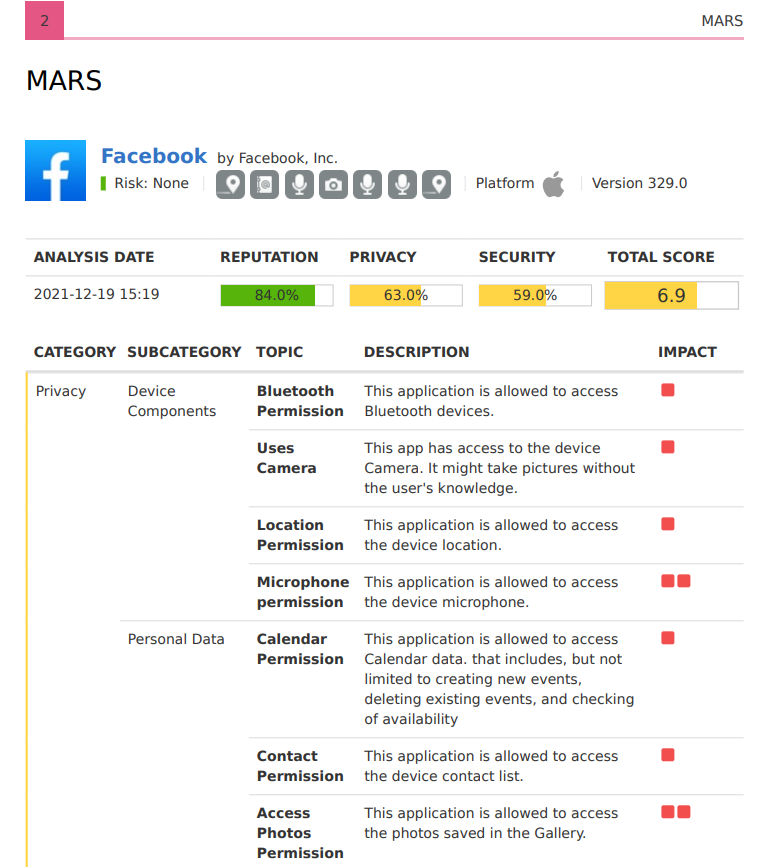
MARS – Mobile Application Reputation Service
Under Application tab move to View MARS scores tab. MARS provides analysis of any mobile application that is uploaded to the service either as a binary file or a link to the official Apple App Store and Google Play.
With MARS administrators can upload an application either as a binary file (APK - Android App format or IPA - iOS App format) or a direct link to an application in the official store (Apple App Store or Google Play Store), once uploaded into Harmony Mobile Dashboard, administrator receives a full app analysis report after few minutes.
-
To learn about an application, administrator should upload the APK/IPA file, iOS App Store link or Google Play Store link into Harmony Mobile Dashboard (under Forensics > MARS tab).
-
If the App is analyzed for the first time, it may take few minutes for Harmony Mobile to analyze the App, when done - administrator receives an email with a link to MARS full App analysis report, at the same time MARS dashboard is updated with new report.
-
MARS generates a report which analyses the application according to 3 categories: security (vulnerabilities), reputation and privacy. Each category consists of a list of findings, split into sub-categories and topics, with their associated impact on the category score.
-
For each category a score is calculated according to MARS analysis findings, then, a weighted summary score is given to the application.
-
If the App was already analyzed by Harmony Mobile, administrator can immediately view or download the full App analysis.
-
After reading the App analysis report, administrators can make educated decisions based on full App analysis before they distribute an App into their organization’s Mobile devices.
-
The App analysis report consists of the data as described in ‘App Analysis Overview’ (p.62) plus the MARS analysis for the 3 categories – security, reputation and privacy.
-
MARS detailed app report is linked to its App Risk analysis, clicking on ‘App Risk’ icon will take you directly to the App Risk analysis page.
-
Administrator can also export a full app report (MARS + Risk Analysis) and ask to reanalyze the app if a new version is available on the Apple app store or Google Play.
App report (MARS and Risk Analysis):
Network
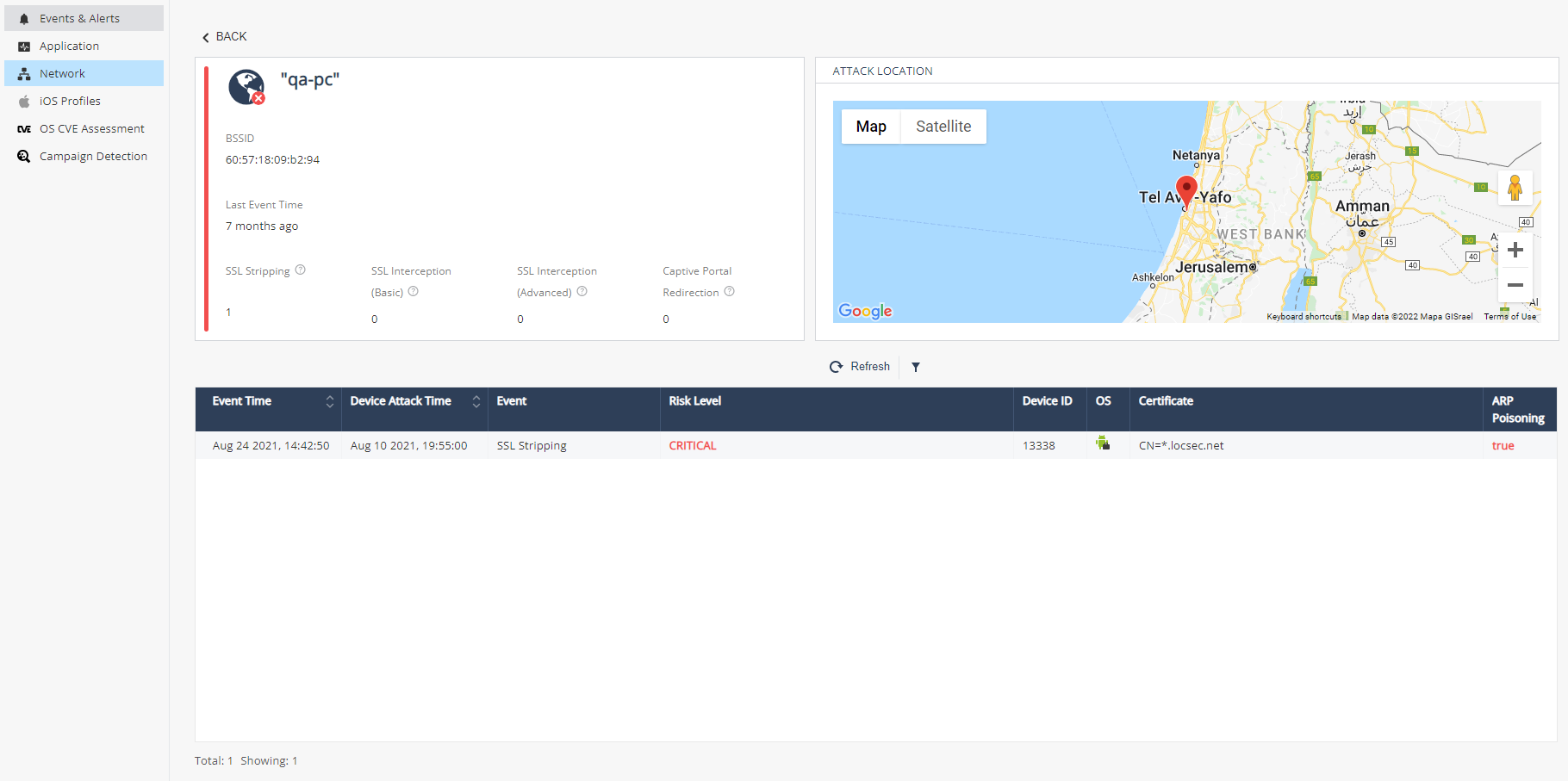
The Network tab shows any network event reported. This tab provides a more granular view of network events in the context of the network in which they occurred. These network events are reported:
-
SSL Stripping – A third-party intercepted the traffic and downgraded it from HTTPS to HTTP
-
SSL Interception (Basic) – A third-party intercepted the traffic and posed as the original requester to the target server while controlling the responses back to the requester.
-
SSL Interception (Advanced) – Similar to basic SSL
 Secure Sockets Layer. The standard security technology for establishing an encrypted link between a web server and a browser. Interception, however, in this case the perpetrator responses were encrypted with an SSL certificate that was issued by a certificate authority that is listed as trusted on the victim’s device. This can be gained by either deceiving the certificate authority to issue an SSL certificate to the perpetrator or by injecting the perpetrator’s certificate to the victim device’s trusted list. This attack requires advanced skills and a higher level of sophistication.
Secure Sockets Layer. The standard security technology for establishing an encrypted link between a web server and a browser. Interception, however, in this case the perpetrator responses were encrypted with an SSL certificate that was issued by a certificate authority that is listed as trusted on the victim’s device. This can be gained by either deceiving the certificate authority to issue an SSL certificate to the perpetrator or by injecting the perpetrator’s certificate to the victim device’s trusted list. This attack requires advanced skills and a higher level of sophistication. -
Captive Portal Redirection – The traffic from the device is redirected to the network portal for registration to the network. This is common with public networks, especially free networks, such as those in airports, hotels, and cafes.
Click Filter  button to filter the list of networks based on Network Name (SSID), BSSID, Device ID (affected device), and Network Status.
button to filter the list of networks based on Network Name (SSID), BSSID, Device ID (affected device), and Network Status.
Clicking on one of the network card opens the network overview:
Information about reported events in the Network:
|
Item |
Description |
|---|---|
|
Network Details |
|
|
Network Name (SSID) |
The name assigned in the access point as the wireless network name. |
|
Occurrences |
Number of times a network event was reported for a device in this organization’s wireless network. |
|
BSSID |
The MAC address of the access point. It is used to identify the network, no matter if the Network Name was changed. |
|
Previous Network Names (SSIDs) |
If network name was changed, they are listed in this field. |
|
Attack location |
To receive Location, the user is required to enable location collection in the Dashboard Settings and to grant location collection permissions on their device. If the device has geo-location enabled for the Harmony MobileProtect App, the location of the device is recorded when the device is connected to this network. |
|
Event Summary |
What type of Events were identified with this BSSID, such as SSL Stripping, SSL Interception, Captive Portal, etc. |
|
Network Event Details |
For each network event reported on this wireless network these details are provided:
|
|
|
Note - The networks in the list are identified by their BSSID, which is the unique network identifier. However, for readability purposes, the pronounced identifier is the network name (SSID). As a result, several networks of the same name may appear in the list next to each other. In such a case, please make sure to refer to the network of the desired BSSID. |
iOS Profiles
iOS Profiles are unique to Apple iOS devices. To assist the mobile device admins, Apple developed a tool called Profiles, which includes Network Configuration Profiles, Provisioning![]() Check Point Software Blade on a Management Server that manages large-scale deployments of Check Point Security Gateways using configuration profiles. Synonyms: SmartProvisioning, SmartLSM, Large-Scale Management, LSM. Profiles, and Certificates. Network profiles are also used by the legitimate VPN applications. The shortcoming of iOS Profiles is that it opens a security hole where an attacker can create and install a malicious network configuration profile. It makes them act as a Man-In-The-Middle and collect all the information flowing from the device.
Check Point Software Blade on a Management Server that manages large-scale deployments of Check Point Security Gateways using configuration profiles. Synonyms: SmartProvisioning, SmartLSM, Large-Scale Management, LSM. Profiles, and Certificates. Network profiles are also used by the legitimate VPN applications. The shortcoming of iOS Profiles is that it opens a security hole where an attacker can create and install a malicious network configuration profile. It makes them act as a Man-In-The-Middle and collect all the information flowing from the device.

Information about iOS Profiles:
iOS Profiles window shows the Network Configuration Profiles. It allows the administrator to get a clear view on the profiles installed on the devices in the organization.
|
Item |
Description |
|---|---|
|
Type |
Displays the type of profile – Wi-Fi configuration, VPN, etc. |
|
Name |
Profile name as it appears on the iOS device. |
|
Profile Details |
Profile details indicated the information (properties) of the profile. Including remote address, IP and servers. |
|
Install Base |
Number of devices currently installed with this specific profile. |
|
Policy |
Policy drop down menu allows the Administrator to set the alert level of a specific profile in the dashboard. |
The iOS Profiles tab also shows the Provisioning Profiles that are installed on the organization’s iOS devices.
On the right side of the window, you can use a filter to select information that is presented in the table. Filtering options include Device ID, Device Type, Device Name, Install Base, and Policy.
OS CVE Assessment
OS CVE![]() Common Vulnerabilities and Exposures. A list of publicly disclosed computer security flaws. When someone refers to a CVE, they mean a security flaw assigned with a CVE ID number. window shows the vulnerability status of the OS devices in the dashboard.
Common Vulnerabilities and Exposures. A list of publicly disclosed computer security flaws. When someone refers to a CVE, they mean a security flaw assigned with a CVE ID number. window shows the vulnerability status of the OS devices in the dashboard.
|
|
Note - The CVE information is derived from National Vulnerability Database. When the CVE information is updated in the National Vulnerability Database, Harmony Mobile automatically updates the dashboard. |
View by CVEs
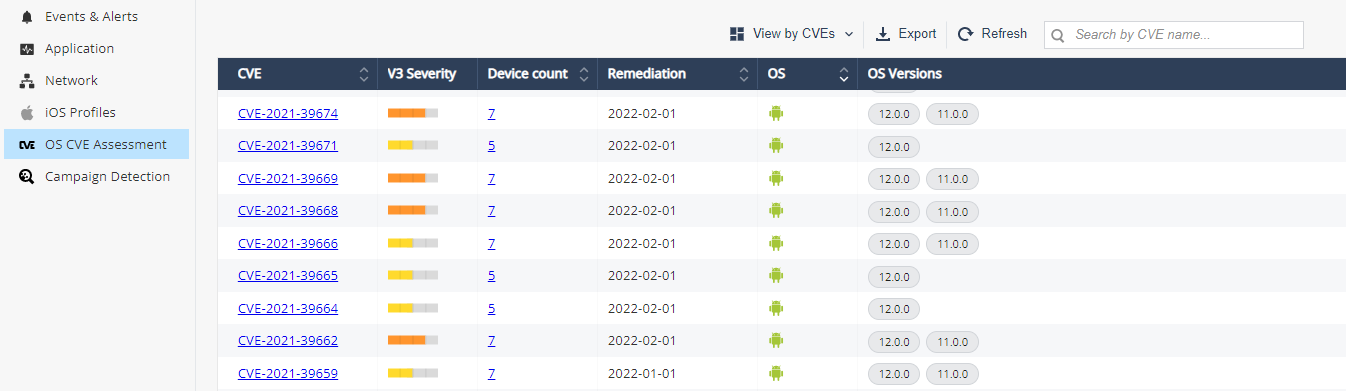
| Item | Description |
|---|---|
|
CVE |
OS CVE name. Click on the name will direct to NVD for full description |
|
V3 Severity |
The Common Vulnerability Scoring System (CVSS
|
|
Device Count |
Number of devices that are exposed to the displayed CVE. Click on the number will direct you to the devices tab |
|
Remediation |
The release date of the security patch to the CVE |
|
OS |
Operating System (Android/iOS) |
|
OS Version |
List of OS Versions that contain the CVE |
To export the CVEs information from the table to CSV file, click Export. It creates a comma separated values file that can be opened in spreadsheet applications such as Microsoft Excel. Use a filter to select the required information for the file.
If the number of CVEs exceeds 10,000, processing the data may take time. So the export is performed offline and an email is sent to the registered address with the link to download the CSV file. The link is valid for 7 days.
View by OS Versions
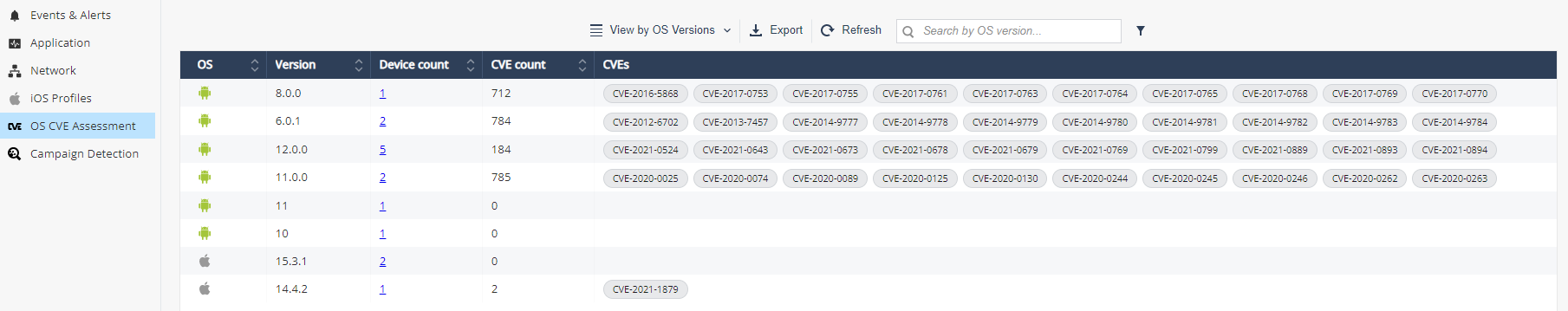
| Item | Description |
|---|---|
|
OS |
Operating System (Android/iOS) |
|
Version |
OS Version |
|
Device Count |
Number of devices with the OS version |
|
CVE Count |
Number of CVEs that the OS version contains |
|
CVEs |
The first 10 CVEs the OS version contains |
-
You can filter by OS, OS version and CVE name in the table:
-
Click Filter
 above the table.
above the table. -
On the Filters pane on the right side of the window, adjust information you want to view.
-
-
You can also export
 the information from the table to CSV file, which creates a comma separated values file that can be opened in spreadsheet applications such as Microsoft Excel. Use filter to select the required information for the file.
the information from the table to CSV file, which creates a comma separated values file that can be opened in spreadsheet applications such as Microsoft Excel. Use filter to select the required information for the file.If the number of CVEs exceeds 10,000, processing the data may take time. So the export is performed offline and an email is sent to the registered address with the link to download the CSV file. The link is valid for 7 days.
-
You can set policy according to the OS CVE under Policy > Device > OS Vulnerabilities.
View by Devices
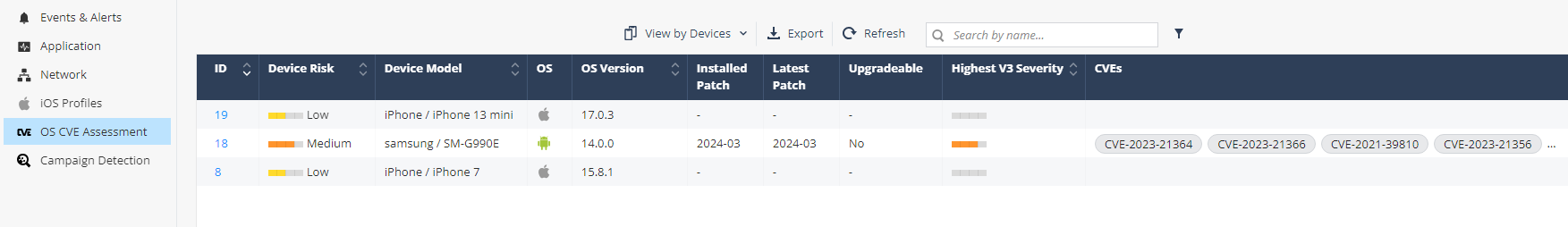
| Item | Description |
|---|---|
|
ID |
Device ID. To view the device details, click the ID link. |
|
Device Risk |
Risk level of the device |
|
Device Model |
Model of the device. For example, iPhone 13 Pro, Samsung SM-G998B |
|
OS |
Device Operating System
|
|
OS Version |
Device OS version |
|
Installed Patch |
The security patch version installed on the Android device. |
|
Latest Patch |
The latest security patch version available for the Android device OS version. |
|
Upgradeable |
Indicates whether the Android device can be upgraded to the latest security patch version:
|
|
Highest V3 Severity |
Highest CVSS score of the device. The Common Vulnerability Scoring System (CVSS) is a free and open industry standard to assess the severity of computer system security vulnerabilities. The scores displayed are as per CVSS version 3.x:
|
|
CVEs |
The CVEs detected on the device |
-
To filter the table, click
 . You can filter by:
. You can filter by:-
OS
-
Device Risk
-
Highest CVSS greater than - Shows the devices with Highest V3 Severity greater than the selected value.
-
Not Connected Since - Shows the devices not connected with the Harmony Mobile server since the selected date.
-
-
To export the table to a CSV file, click Export.
If the number of devices exceeds 10,000, processing the data may take time. So the export is performed offline and an email is sent to the registered address with the link to download the CSV file. The link is valid for 7 days.
Campaign Detection
Using the Campaign Detection tab you can define attack campaigns you will be notified about.
A campaign is an attack using the same attack vector several times. For example, Network Security.
There are three pre-configured campaigns for Applications, Wifi and Network security:
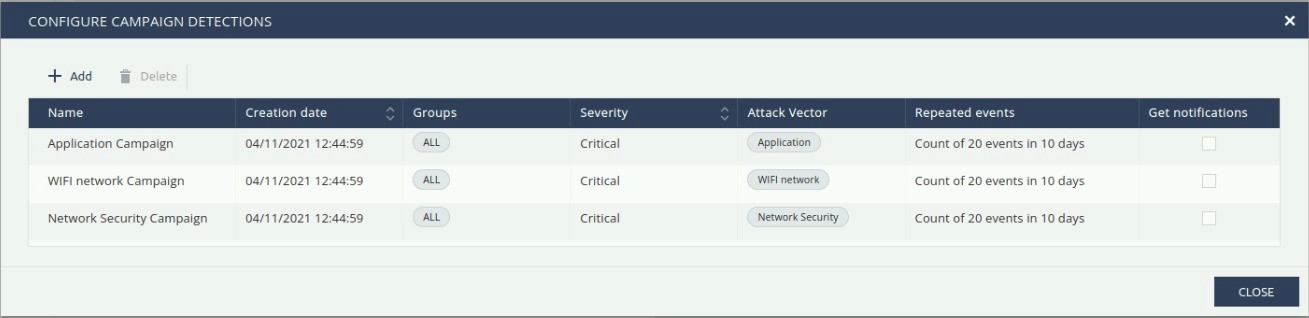
To create a new campaign detection click on Configure > +Add:
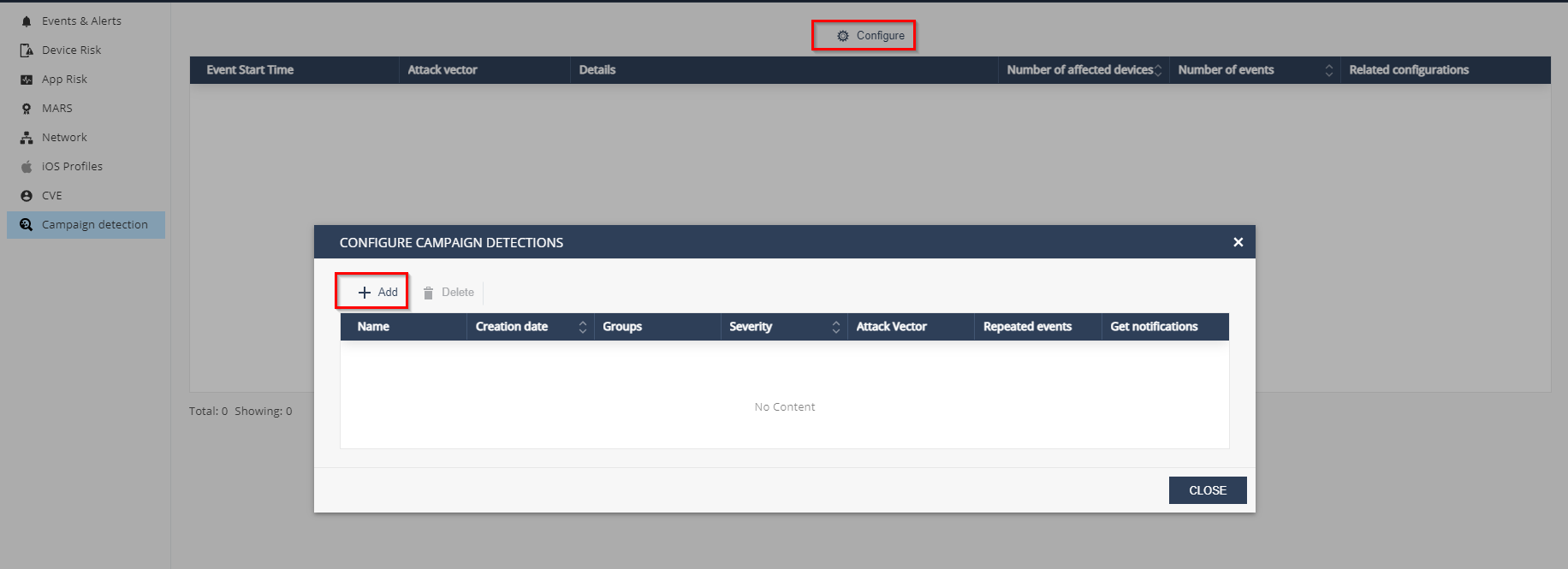
In the configuration window you can give your campaign a name, select the device groups to apply the campaign, the events’ severity and one or several attack vectors.
The count of events per period of time will define the scope of your campaign.