Managing Quarantined Files
Quarantine Management helps protect the network by isolating potentially harmful files and applications (malware, ransomware, suspicious files, and so on), preventing threats from spreading across the environment. It offers a centralized view, enabling security teams to manage quarantined items efficiently. Administrators can respond quickly to incidents, inspect suspicious content, and resolve issues by restoring safe files or removing malicious ones.
To view the Quarantine Management page, from the left navigation panel, click Asset Management > Quarantine Management.
|
|
Note - Quarantine Management feature is supported only on the Harmony Endpoint Security client for Windows version E89.05 and later. |
Benefits
-
Centralized control: View and manage quarantined items across all endpoints from a unified location.
-
Safe investigation: Download and analyze quarantined files in a secure, password-protected format for further examination by SOC analysts.
-
Efficient threat response: Restore or delete files in bulk across impacted devices, swiftly addressing actual threats and false positives.
Viewing Quarantined Files and Applications
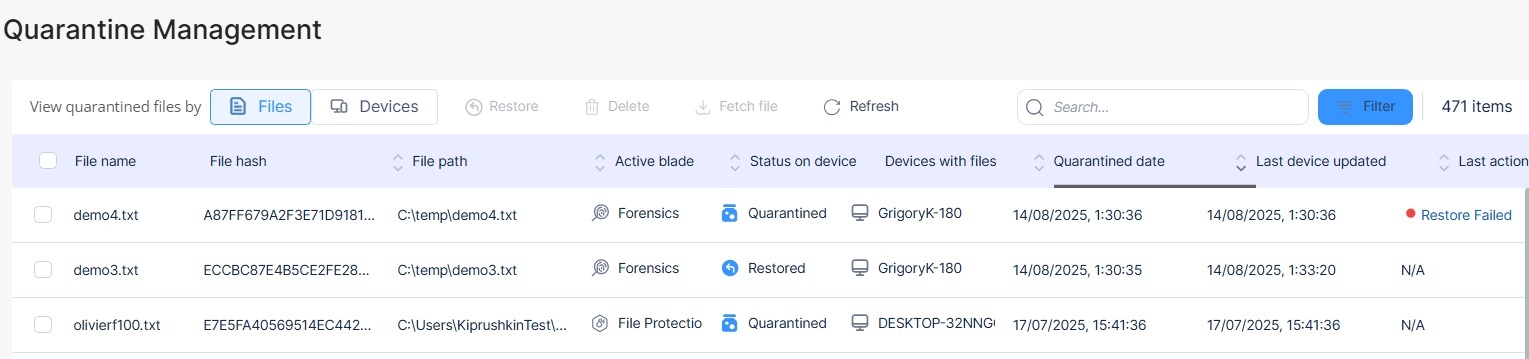
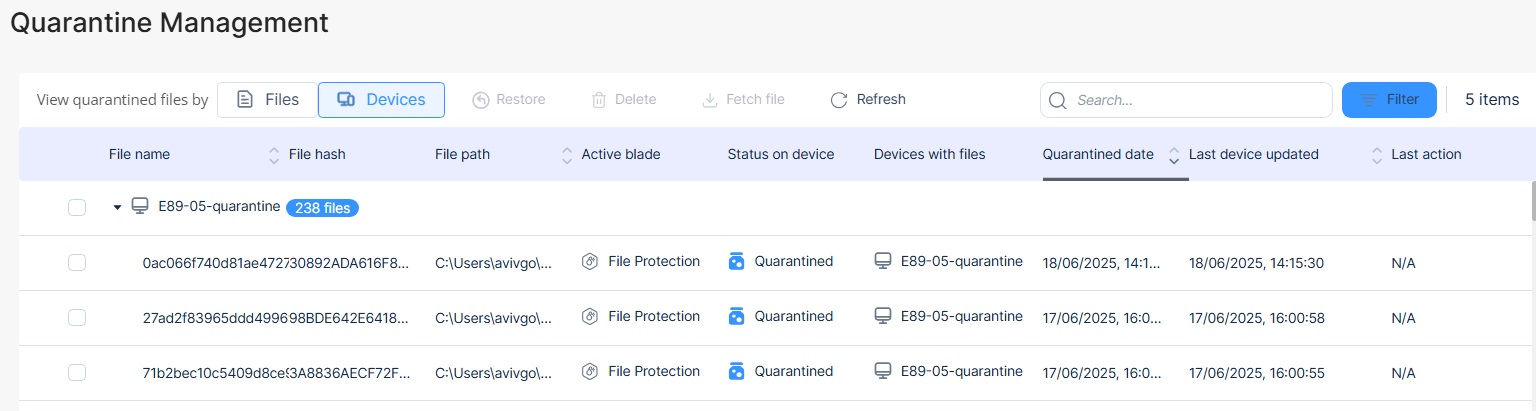
The Quarantine Management page shows all quarantined files and applications in two switchable views:
-
View by Files: Each row represents an individual file. Shows file details including name, path, hash, responsible blade, status, and the number of devices where this file was quarantined.
-
View by Devices: Each row represents an individual endpoint. It shows device details, including name, operating system, version, and the total count of quarantined files on that device.
To change the view, click Files or Devices next to View quarantined files.
| Column | Description |
|---|---|
|
File name |
Name of the quarantined file. |
|
File hash |
Hash of the quarantined file. |
|
File path |
Location of the quarantined file on the device. |
|
Active blade |
Security blade that quarantined the file. For example, Anti-Malware |
|
Status on device |
Status of the quarantined file.
|
|
Devices with files |
Name of other devices that have the same quarantined file. |
|
Quarantined date |
Date on which the file was quarantined. |
|
Last action |
Recent action taken on the quarantined file. |
|
Last device updated |
The date on which the device was recently updated. (Appears only on Devices view) |
Acting on Quarantined Files and Applications
Administratorscan take these actions on the quarantined files and applications:
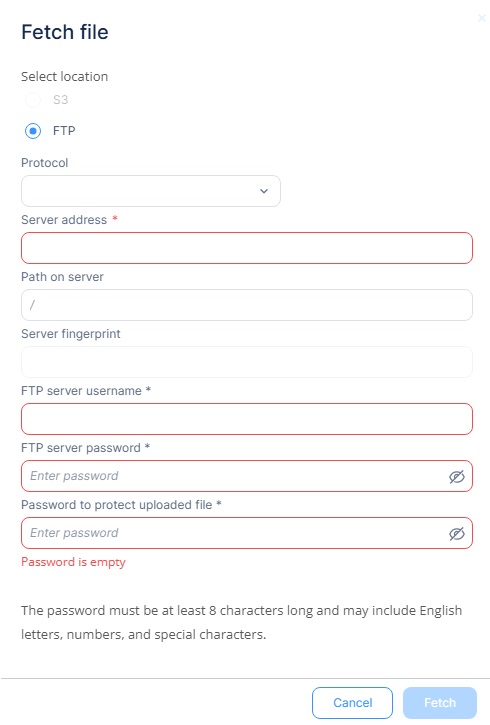
Fetching (download) a quarantined file
The Quarantine Management page allows you to download quarantined files for further analysis or inspection and ensure secure handling.
|
|
Note - You can fetch only one file at a time. |
-
Choose the quarantined file to download.
-
Select where you want to upload the file:
-
To upload the file to AWS S3:
-
Select S3.
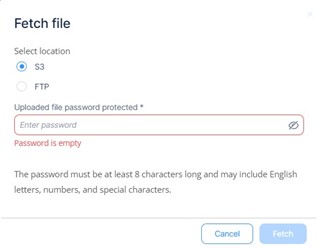
-
In the Uploaded file password protected field, enter a password.
You need this password to open the file in AWS S3.
-
Click Fetch.

Notes -
-
To upload a file to S3, the file size must not exceed 25 MB.
-
The file is retained only for 30 days in S3.
-
You can archive up to 100 MB of files.
-
-
To upload the file to your corporate FTP server:
-
Restoring a quarantined file
Restoring a quarantined file allows an administrator to recover a file that was incorrectly identified as malicious.
|
|
Notes -
|
To restore or exclude a quarantined file:
-
Choose the file to restore using the multi-select checkboxes.
-
Click Restore.
-
Select one of these options:
-
To restore a file from quarantine, select Restore only.

Notes:
-
The system restores the file to the same location from where it was quarantined.
-
If Harmony Endpoint detects the same file as malicious in any other endpoint, it quarantines the file again.
-
-
To restore a file and also exclude it from quarantine in the future, select Exclude and Restore.
The system adds an exclusion to the Global Exclusions which affects all endpoints on the network, ensuring that the file is not flagged as malicious again.
-
-
Click Proceed to complete the restoration.
The system sends a push operation to the relevant device.
Deleting a quarantined file
Deleting a quarantined file permanently removes it from the system, ensuring it cannot be restored or executed again. This action is typically used for files identified as confirmed threats, such as malware or spyware.
-
Go to the Quarantine Management page.
-
Using multi-select checkboxes, select the file you want to delete permanently.
-
Click Delete.
In the confirmation pop-up that appears, click OK.

Note - Once a file is deleted, it cannot be restored.