Viewing Endpoint Posture
After the scan is complete, Harmony Endpoint shows the detected Common Vulnerability and Exposures (CVE) and its Common Vulnerability Scoring System (CVSS).
For the supported applications for scan and patch management, see sk181034.
|
|
Note -
|
To view the posture for endpoints, click Asset Management > Posture Management.
If you see the following screen, make sure to configure the posture assessment settings. See Configuring Posture Assessment Settings.
Vulnerabilities by Severity

The Vulnerabilities by Severity widget shows the total number of vulnerable CVEs by severity.
Top 5 Risky Apps

The Top 5 Risky Apps widget shows the top five applications with vulnerable CVEs and their average CVSS score.
For example, if Visual C++ 2008 has different CVEs, then the average CVSS score is 9.3.
Top Vulnerable Devices

The Top Vulnerable Devices widget shows the top five vulnerable endpoints (most vulnerable CVEs detected).
The number to the left of the machine name indicates the total number of CVEs detected in the machine.
To view vulnerable CVEs in the machine, click the machine name. It shows the details in the Vulnerability Assessment Table.
There are
-
Vulnerabilities view - Shows all the vulnerable CVEs and their CVSS score detected in the endpoints. See Vulnerability Assessment Table
-
Devices view - Shows devices that have at least one CVE detected.
Patches By Status

The Patches By Status widget shows the total number of patches by the status.
Click the status to filter the Vulnerability Assessment Table by the status.
Vulnerability Assessment Table
The Vulnerability Assessment table shows the details about the detected CVE and its CVSS score.
|
Item |
Description |
|---|---|
|
Export |
Exports the table information. Supported exports are:
For more information on vulnerability and posture reports, see Reports in theViewing Operational Overview, Security Overview and Reports. |
|
Refresh |
Refresh the table information. |
|
Search |
Enter the required search options. |
|
Toggle Filters |
Opens the Filters widget. You must specify the filter criteria. |
|
Scan All |
Scans all devices for CVEs. See Scanning Devices. |
|
Scan Now |
Scans selected devices for CVEs. See Scanning Devices. |
|
Patch |
Updates patches to the specified CVEs. See Applying the Patch for CVEs. |
|
Perform any of these Push Operations:
|
|
|
Add Filter |
Allows you to filter the columns by a specific value. |
|
Group by CVE |
Lists CVEs by group. |
|
Group by Application |
Lists CVEs by application. |
|
Expand All |
Expands CVEs listed by application. |
|
Collapse all |
Collapses CVEs listed by application. |
|
CVSS Score |
CVSS score of the detected CVE. |
|
CVE Number |
Click the CVE number to view CVE Details Widget and all impacted devices:
|
|
App Name |
Application name. |
|
App Version |
Application version number. |
|
Last Detected |
Date and time the CVE was last detected. |
|
First Detected |
Date and time the CVE was first detected. |
|
Affected Devices |
Number of machines with vulnerable CVEs. |
|
Comments |
Add a comment. For example, do not patch this device. |
|
Device Name |
Click the device name to view the Device Details Widget and all CVEs in the device:
|
|
OS |
Operating System name. |
|
OS Version |
Operating System version. |
|
Last Scan Status |
Shows the status of the latest scan. The supported statuses are:
|
|
Last Scanned |
Date and time the machine was last scanned. |
|
Number of Vulnerabilities |
Number of vulnerabilities detected in the machine. |
|
Number of Apps At Risk |
Number of applications in the machine with vulnerable CVEs. |
|
Comments |
Add a comment. For example, do not patch this device. |
|
Application view |
|
|
App Name |
Application name. Click the application name to view all the CVEs affecting the corresponding application. It takes you to the Vulnerabilities view and shows the relevant information. For more details, see Vulnerability view. |
|
App Version |
Application version number. |
|
Patch Name |
Full name of the patch. |
|
Patch Size |
Size of the patch file. |
|
First Detected |
Date and time the CVE was first detected. |
|
Last Detected |
Date and time the CVE was last detected. |
|
Affected Devices |
Number of devices that have the application affected by the corresponding CVE. Click the number to view all the impacted devices for the corresponding patch. It takes you to the Devices view and shows the relevant information. For more details, see Devices view. |
|
Patch Status |
Status of the patch of the CVE. For more information, see Patch Status Messages. |
Patch Status Messages
|
Category |
Status |
Description |
|---|---|---|
|
Patch Status States
|
Downloading |
Patch is currently being downloaded. |
|
Downloaded |
Patch has been successfully downloaded and verified. |
|
|
Executing |
Patch installation is in progress. |
|
|
Pending |
Patch is awaiting verification |
|
|
Updated |
Patch has been successfully installed and verified. |
|
|
Replaced |
Patch has been superseded by another patch and will not be installed. Install the latest patch to fix this CVE. |
|
|
Failed |
Patch installation failed. |
|
|
Download Failed |
Patch download failed. |
|
|
Detailed Status States |
||
|
Initial States
|
Update Available |
Patch is available for download; URL exists and download method is automatic. |
|
Update Not Available |
Patch URL is missing or download method is not automatic |
|
|
Download States
|
Downloading |
Patch download is in progress. |
|
Download Failed |
Download failed due to a specific reason. |
|
|
Ready |
Download completed successfully. |
|
|
User Interaction States
|
Pending UC |
Waiting for user response or user postponed the action. |
|
Pending Execution |
The user-approved or forced installation time has passed, but another patch in the deployment set is still being installed. |
|
|
Installation States
|
Executing |
Patch is currently being installed. |
|
Pending Scan |
Installation finished; awaiting the scan to verify that patch is no longer needed. |
|
|
Pending Reboot |
Installation finished but system reboot is required. |
|
|
Final States
|
Updated |
Patch successfully installed and verified; no longer appears in scans. |
|
Failed |
Installation failed. |
|
|
Not Installed |
Installation completed but patch still appears in verification scan. |
|
|
Replaced |
Patch was replaced by another patch. |
|
|
Cancelled |
The operation was canceled before completion because the administrator initiated a different deployment using the Patch Now feature. |
|
|
Interrupted |
Patch disappeared from scan results (likely installed by another process). |
|
|
Download Failure Reasons
|
HTTP errors |
Network connectivity issues, server unavailable, or authentication failures. |
|
Signature validation failed |
Downloaded file failed digital signature verification. |
|
|
Patch file does not exists |
File missing after download attempt. |
|
|
Failed to create packager (Err=X) |
System component initialization failure. |
|
|
Failed to initialize packager (Err=X) |
Packager configuration failure. |
|
|
Cannot get patch download info |
Unable to retrieve patch metadata from vendor. |
|
|
Failed to get installable patches (Err=X) |
System error retrieving available patches. |
|
|
Installation Failure Reasons
|
Patch installation failed (Error=X) |
Where X is the exit code from the patch installer. Exit code 0: Success Exit code 3010: Success but reboot required Other codes: Various installer-specific errors |
|
Failed To create Process |
Unable to start the patch installation process. |
|
|
Deployment process finished with status X |
Process completed with non-zero exit code. |
|
Device Details Widget

To view the Device Details widget, in the Vulnerability Assessment Table, under the Device Name column, click a device name.
The Device Details widget shows:
-
Operating System name.
-
Operating System version.
-
Date and time the device was last scanned.
-
Number of vulnerabilities detected in the device.
-
Number of applications at risk.
-
Comment
CVE Details Widget
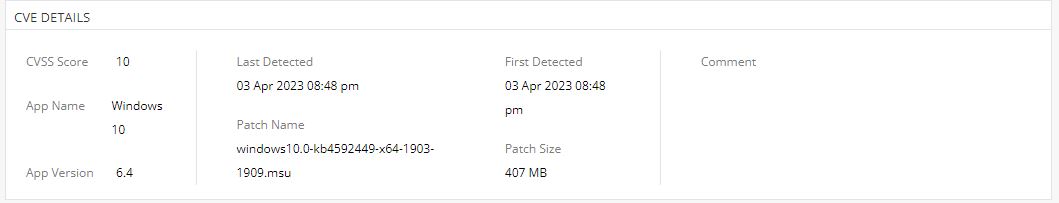
To view the CVE Details widget, in the Vulnerability Assessment Table, under the Vulnerabilities view, click a CVE number.
-
CVSS score of the device.
-
The application with the CVE.
-
The version of the application with the CVE.
-
Date and time the CVE was last detected.
-
Date and time the CVE was first detected.
-
Patch name available for update.
-
Size of the patch available for update.
-
Comment
Scanning Devices
You can scan devices for vulnerable CVEs or to verify if the patch has been applied or not.
|
|
Note - To start the scan for the first time:
You can start subsequent manual scans by clicking Scan Now in Asset Management > Posture Management or by using the Run Diagnostics push operation. |
To scan the devices:
-
Go to Asset Management > Posture Management.
-
To scan specific devices:
-
From the View list, select Devices.
-
Select the devices and click
.
-
-
To scan all the devices affected by the CVE:
-
From the View list, select Vulnerabilities.
-
Select the CVE and click
.
-
Mitigating Vulnerable CVEs
You can mitigate vulnerable CVEs by either isolating or applying the patch.
Isolating a Device
You can isolate a device from the network until you patch its vulnerable CVEs.
To isolate devices:
-
Go to Asset Management > Posture Management.
-
To isolate specific devices:
-
From the View list, select Devices.
-
Select the devices and click Push Operation > Isolate Device.
-
-
To isolate all the devices affected by the CVE:
-
From the View list, select Vulnerabilities.
-
Click the vulnerability.
-
Select the devices and click Push Operation > Isolate Device.
Harmony Endpoint initiates the Isolate Device push operation. For more information, see Push Operations.
-
Applying the Patch for CVEs
|
|
Notes:
|
To apply a patch for CVE:
-
Go to Asset Management > Posture Management.
-
To apply patches for specific vulnerabilities:
-
From the View list, select Vulnerabilities.
-
Select the CVEs and click
.
The Patch Details window appears.
-
Click Update Patch.
-
-
To apply the patches for specific device:
-
From the View list, select Devices.
-
Select and click the specific Device Name.
The Device Details window appears.
-
Select the CVEs and click
.
The Patch Details window appears.
-
Click Update Patch.
-
Verifying the Applied Patch
|
|
Note - Make sure that the vendor sites are accessible for the endpoints to download the patches directly. |
-
Scan the device to verify that all CVEs are patched.
-
If all the CVEs are patched and if the device is isolated (To verify, go to Asset Management > Organization > Computers, from the View list, select Host Isolation, and then view the Isolation Status column) from the network, then add the device back to network. To add:
-
Go to Asset Management > Posture Management.
-
From the View list, select Devices.
-
Select the devices and click Push Operations > Release Device.
-
-
If required, reboot the device. To reboot:
-
Go to Asset Management > Posture Management.
-
From the View list, select Devices.
-
Select the devices and click Push Operations > Reboot Device.
-