Legacy Exclusions
You can exclude specific objects (exclusions) from inspection by Harmony Endpoint. You can add exclusions to a rule![]() Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. or create global exclusions that apply to all rules.
Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. or create global exclusions that apply to all rules.
Adding Exclusions to a Specific Rule
To add exclusions to a specific rule:
-
Go to Policy > Threat Prevention > Policy Capabilities.
-
Select the rule for which you want to create the exclusion
-
In the Capabilities & Exclusions pane, click Exclusions Center.
-
Expand an exclusion category. For example, Anti-Bot -> URL Filtering Exclusions.
Note - Global Exclusions is read-only. To add Global Exclusions, see Adding Global Exclusions.
-
Expand Rule Exclusions.
-
Select the exclusions you want to add to the rule.
-
Click OK.
-
In the bottom right corner of the policy configuration pane, click Save.
-
From the top, click Install Policy.
Adding Global Exclusions
To add global exclusions that apply to all the rules:
-
Go to Policy > Threat Prevention > Global Exclusions.
-
Expand an exclusion category. For example, Anti-Bot -> URL Filtering Exclusions.
-
Select the exclusions you want to add to the rule.
-
Click Save.
-
From the top, click Install Policy.
Adding Exclusions from Security Overview
To add exclusions from Security Overview:
-
Go to Overview > Security Overview.
-
Right-click the security event and select Drill Down.
-
Right-click the event and select one of these options:
-
Create Exclusion for Effective Rule
The Edit Exclusions Center window appears and automatically adds the exclusion.
-
Create Exclusion for All Rules
-
If Global Exclusions is not enabled, the Edit Exclusions Center window opens and automatically adds the exclusion to all the rules under Policy Capabilities.
-
If Global Exclusions is enabled, the Edit Exclusions Center window opens and automatically adds the exclusion to Global Exclusions. For more information, see Adding Global Exclusions.
-
-
-
Click OK.
-
Click Save for all the modified policies.
- Click Install Policy.
Notes:
-
You cannot add exclusions for Forensic events triggered by Anti-Bot
 Check Point Software Blade on a Security Gateway that blocks botnet behavior and communication to Command and Control (C&C) centers. Acronyms: AB, ABOT..
Check Point Software Blade on a Security Gateway that blocks botnet behavior and communication to Command and Control (C&C) centers. Acronyms: AB, ABOT.. -
You cannot add exclusions for Forensic events triggered by Anti-Malware
 A component of the Endpoint Security client that protects against known and unknown viruses, worms, Trojan horses, adware, and keystroke loggers. engine that has no reference event.
A component of the Endpoint Security client that protects against known and unknown viruses, worms, Trojan horses, adware, and keystroke loggers. engine that has no reference event. -
This procedure is not supported for macOS endpoints.
Adding Exclusions from Logs
To add exclusions from the Logs menu:
-
Go to Logs menu.
-
Right-click a log to add and configure an exclusion to your endpoint device. This redirects you to the appropriate rule, section, and capability.
-
Select one of these options to apply the exclusions:
-
Effective option: For a specific device or a user rule.
-
All options: For a specific rule.
-
Notes:
-
This option is available only for Harmony Endpoint client version E86.20 and later.
-
For Harmony Endpoint client version 86.20 or earlier, or for unsupported blades/capabilities, you are redirected to the relevant rule in the exclusions center to create exclusions.
Adding a New Exclusion to an Exclusion Category
To add an exclusion to an exclusions category:
-
Do one of these:
-
Go to Policy > Threat Prevention > Policy Capabilities.
-
Go to Policy > Threat Prevention > Global Exclusions.
The Edit Exclusions Center window appears.
-
-
Click
 .
.The New Exclusion window appears.
-
Specify these details:
-
Exclusion
-
Method
-
Value
-
(Optional) Comment
-
To add the exclusion to all the rules, select the Add to all rules checkbox. This step does not apply to Global Exclusions.
Note - If the current rule contains this exception, then the system adds a duplicate exclusion.
-
-
Click OK.
-
In the bottom right corner of the policy configuration pane, click Save.
-
From the top, click Install Policy.
Editing an Exclusion
To edit an exclusion:
-
Do one of these:
-
Go to Policy > Threat Prevention > Policy Capabilities.
-
Go to Policy > Threat Prevention > Global Exclusions.
The Edit Exclusions Center window opens.
-
-
Expand an exclusion category. For example, Anti-Bot -> URL Filtering Exclusions.
-
If you are editing a local exclusion, expand Local Exclusions. This step does not apply to Global Exclusions.
-
Select the exclusion you want to edit.
-
Click
.
The Edit Exclusion window appears.
-
Specify these details:
-
Exclusion
-
Method
-
Value
-
(Optional) Comment
-
To apply the changes to all the rules that contain this exclusion, select the Update all rules checkbox. This step does not apply to Global Exclusions.
-
To add the exclusion to all the rules that does not contain this exclusion, select the Add to all rules checkbox. This step does not apply to Global Exclusions.
-
-
Click OK.
-
In the bottom right corner of the policy configuration pane, click Save.
-
From the top, click Install Policy.
Below is the list of supported exclusions.
By default, the Anti-Bot component inspects all entities except:
-
Process - Name of an executable
-
URL - Website URL
-
Domain - Full Domain name
-
Protection Name - Predefined malware signature
-
IP range - Internal or external IP address
You can exclude specific domains from a rule. Click + to add the required domain you want to exclude from the rule.
Syntax
-
* indicates a string or a character. For example, A* can be ADomain or AB or AAAA.
-
? indicates a character. For example, A? can be AA or AB or Ab.
For example:
|
If you enter |
It excludes these |
It does not exclude these |
|---|---|---|
| www.domain.com |
|
|
| domain.com |
|
- |
| sub.domain.com |
|
https://sub2.domain.com |
|
*.domain.com |
Sub-domain of domain.com such as:
|
|
Harmony Endpoint scans files when you create, open, or close them.
When you exclude a trusted process from inspection, it's file or network operation is not scanned. Exclude a process only if you are sure, it is not Malware.
|
|
Best Practice - We recommend excluding a process if:
|
Windows
You can exclude only .EXE files.
Syntax:
Fully qualified paths or an environment variable for the trusted executable.
Examples:
-
C:\Program Files\MyTrustedDirectory\MyTrustedProgram.exe -
%programdata%\MytrustedProgram.exe
macOS
Syntax:
Fully qualified path for the trusted executable file.
Example:
/Applications/FileZilla.app/Contents/MacOS/filezilla
Files and Folder Exclusions are applied to all types of scans except contextual scan. The reason for configuring exclusions is to reduce the CPU usage of Anti-Malware.
|
|
Note - Files and folders must be excluded only if they are located in a Trusted zone or are considered a low-risk target for viruses. |
Windows
Syntax:
Directory paths must end with a backlash.
Examples:
-
Directory:
-
C:\Program Files\MyTrustedDirectory\ -
%programdata%\MyTrustedDirectory\
-
-
Specific file:
-
C:\ProgramFiles\MyTrustedDirectory\excludeMe.txt -
%programdata%\MyTrustedDirectory\excludeMe.txt
-
-
File type:
-
*.exe -
\\ServerName\Share\folder\file.txt or \\ip_addres\Share\folder\file.txtdepending on a way file is attached. -
C:\Program Files\MyTrustedDirectory**.exe(recursive exclusion - applies for all.exeinC:\Program Files\MyTrustedDirectory\and all subfolders)
-
-
For Harmony Endpoint client version E80.80 or higher, you can exclude MD5 hash from the scheduled malware scan. For example:
-
md5:0123456789012345-
Exclude by hash in any folder
-
-
md5:0123456789012345:app.exe-
Exclude by hash and exact file name
-
-
md5:0123456789012345:c:\folder\app.exe-
Exclude by hash and full path
-
-
md5:0123456789012345:%ENV%\app.exe-
Exclude by hash and environment variable
-
-
-
For Harmony Endpoint client version E86.10 or higher, you can exclude URL from the scheduled malware scan. For example:
-
url:*.example.com -
url:http://*.example.com -
url:http://example.com/* -
url:www.example.com/abc/123 -
url:*192.168.* -
url:http://192.168.*
-
|
|
Notes for URL exclusions-
|
|
|
Note - For Windows, files and folder names are not case-sensitive. |
macOS
Syntax:
Directory path, a specific file, or a file type. Environment variables are not supported.
Example:
Trusted directory
-
/Users/Shared/MyTrustedDirectory/
Specific file
-
/Users/*/Documents/excludeMe.txt
File type
-
*.txt
|
|
Note - For macOS, files and folder names are case-sensitive. |
You can exclude some riskware files and infections from the scheduled malware scan on your computer.
|
|
Best Practice:
|
Syntax
Infection name and protection name in your log.
Example:
-
EICAR-Test-File
|
|
Notes -
|
You can exclude specific folders, domains or SHA1 hashes from the Threat Emulation![]() Check Point Software Blade on a Security Gateway that monitors the behavior of files in a sandbox to determine whether or not they are malicious. Acronym: TE., Threat Extraction
Check Point Software Blade on a Security Gateway that monitors the behavior of files in a sandbox to determine whether or not they are malicious. Acronym: TE., Threat Extraction![]() Check Point Software Blade on a Security Gateway that removes malicious content from files. Acronym: TEX. and Zero-Phishing protection.
Check Point Software Blade on a Security Gateway that removes malicious content from files. Acronym: TEX. and Zero-Phishing protection.
Domain exclusions
-
Relevant only for Harmony Endpoint extension for Browsers.
-
To exclude an IP, in the Element field, enter IP address followed by subnet mask in the format <X.X.X.X>/ <subnet mask >. For example, to exclude a computer with IP address 192.168.100.30, enter 192.168.100.30/24.
-
Domain exclusions must be added without http, https or any other special characters except asterisk (*).
Domain exclusions can be added with or without www.
-
Sub-domain exclusions are supported.
Exclusion of a domain will exclude all its subdomains as well.
For example:
|
If you enter |
It excludes these |
It does not exclude these |
|---|---|---|
| www.domain.com |
|
|
| domain.com |
|
- |
| sub.domain.com |
|
https://sub2.domain.com |
|
*.domain.com |
Sub-domain of domain.com such as:
|
|
SHA1 exclusions -
-
Relevant only for Threat Emulation blade (File system monitoring).
For Harmony Endpoint version E86.40, SHA1 exclusion is supported on Harmony Endpoint extension for browsers as well (not including Internet Explorer). SHA1 can be used to exclude downloaded files from File Protection and local HTML files from Zero Phishing.
-
It is not supported with Internet Explorer.
-
File Reputation exclusions are set by SHA1.
-
Macro exclusion - To exclude the office files which includes a macro, set exclusions for the SHA1 hash of the macro.
For example, if an exclusion is set to SHA1 hash of the macro, all the files which includes this macro are excluded.

Notes -
-
This is supported with Endpoint Security Client
 Application installed on end-user computers to monitor security status and enforce security policies. version E88.00 or higher.
Application installed on end-user computers to monitor security status and enforce security policies. version E88.00 or higher. -
To view the hash of a macro, see the Description in the Forensic Details section in the Card of the event. For more information see, Adding Exclusions from Logs.
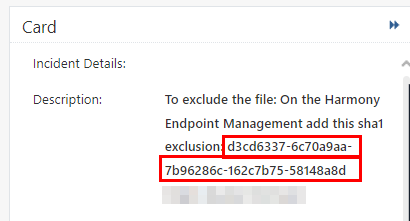
-
-
Relevant only for Threat Emulation blade (File system monitoring).
-
Folder path cannot contain environment variables.
-
When you exclude a folder, enter the folder as a windows path. For example:
C:\Program Files\MyTrustedDirectory\ -
If the path of created file begins with exclusion, it will be excluded.
-
For Endpoint Security Client version E87.10 or higher, if the value of exclusion start with
FileEx:\\then the value will be treated as path to the file.To exclude specific type of files in a folder, use the following format:
FileEx:\\<Path_to_directory>\*.<file_extension>.
For example,FileEx:\\D:\mydir\*.xlswill exclude all XLS files inD:\mydirfolder. -
Folder exclusions support wildcards. These wildcards are supported:
? - Each question mark masks one character.
* - Each star masks zero or more characters.
-
It is not advised to add * in the middle of path exclusions, as it may hurt the performance.
-
Exclude network files by path
\\ServerName\Share\folder\.This excludes all files located under\ServerName\Share\folder\\.
You can exclude these elements from the Anti-Exploit protection:
-
Protection Name - Predefined malware signature
-
Process - To exclude an executable
Currently there are five different Anti-Exploit protections available. Following is a list of the protections per-name.
Syntax for exclusions:
|
Protection |
Protection Rule Name |
|---|---|
|
Import-Export Address Table Parsing |
Gen.Exploiter.IET |
|
Return Oriented Programming |
Gen.Exploiter.ROP |
|
VB Script God Mode |
Gen.Exploiter.VBS |
|
Stack Pivoting |
Gen.Exploiter.SP |
|
RDP Vulnerability (CVE-2019-0708) |
Gen.Exploiter.CVE_2019_0708 |
|
RCE Vulnerability (CVE-2019-1181) |
Gen.Exploiter.CVE_2019_1181/2 |
Excluding a protection means that files will not be monitored by Anti-Exploit.
-
Process and protection
-
C:\Program Files\MyTrustedDirectory\excludeMe.exe -
Gen.Exploiter.ROP
-
-
Protection
-
Gen.Exploiter.ROP
-
You can exclude these elements from the Anti-Ransomware and Behavioral Guard protection:
-
Folder – To exclude a folder or non-executable files
-
Process - To exclude an executable by element, MD5, and signer.
-
Certificate - To exclude processes based on the company that signs the certificate.
-
Protection - To exclude signature by it's name.
|
|
Notes:
|
Syntax:
-
Folder can contain environment variables
-
Folder cannot contain wildcards (*)
-
By default, sub-folders are included.
Excluding a Certificate / Process means that files modified / created by a certain process will not be backed up, or monitored by Anti-Ransomware and Behavioral Guard.
Windows
Syntax:
-
You must specify the process name or full path to the process
-
Exclusion can contain environment variables
-
Wildcards are supported.
Note - This is supported with Endpoint Security client version E86.70 and higher.
Examples:
-
Full path
-
C:\Program Files\MyTrustedDirectory\
-
-
Process
-
C:\Program Files\MyTrustedDirectory\ExcludeMe.exe
-
-
Certificate
-
Microsoft
-
-
md5: 0123456789012345
-
Protection: win.blocker
macOS
Syntax:
-
You must specify full path or wildcard
-
Path or file name can contain wildcards
-
Paths are case sensitive
Examples:
-
Full path or Xcode exclusion:
:/Appliations/Xcode.app/Contents?MacOS/Xcode
-
To cover all Xcode-related executables (not only GUI app):
/Applicatoins/Xcode.app/*
Excluding a Certificate / Process means that files modified / created by a certain process will not be backed up, or monitored by Anti-Ransomware and Behavioral Guard.
You can exclude these elements from monitoring:
-
Process - To exclude an executable by element, MD5 and signer.
-
Certificate - To exclude processes based on the company that signs the certificate.
Syntax:
-
Process can be excluded by name only, or by full path.
For example
C:\Program Files\MyTrustedDirectory\excludeMe.exe -
Full path can contain environment variables.
-
Full path CANNOT contain wildcards.
-
Certificate
-
Microsoft
-
-
md5:0123456789012345
-
Exclude a process by hash.
-
-
Excluding a Certificate / Process means that files modified / created by a certain process will not be backed up, or monitored by Anti-Ransomware and Behavioral Guard.
|
Example |
Supported/Unsupported |
Description |
||
|---|---|---|---|---|
|
C:\Program Files\MyTrustedDirectory\* |
Not supported |
Excludes all the processes under MyTrustedDirectory |
||
|
C:\Program Files\MyTrustedDirectory\excludeMe.exe |
Supported |
Excludes the excludeMe.exe under MyTrustedDirectory |
||
|
excludeMe.exe |
Supported |
Process can be excluded by name only.
|
||
|
%ProgramFiles%\MyTrustedDirectory\excludeMe.exe |
Supported |
Full path can contain environment variables.
|
||
|
C:\*\process.exe |
Not supported |
Full path cannot contain wildcards. |
You can exclude a file or process from quarantine. You can define the exclusion by these criteria: certificate, file, folder, MD5 hash, SHA1 hash, and file extension. When an element is excluded from quarantine, even if there is a detection of malware, the file is not quarantined.

