Configuring Okta as Identity Provider
Set up your Identity Provider and then use these settings for the Identity Awareness![]() Check Point Software Blade on a Security Gateway that enforces network access and audits data based on network location, the identity of the user, and the identity of the computer. Acronym: IDA. (see Identity Awareness).
Check Point Software Blade on a Security Gateway that enforces network access and audits data based on network location, the identity of the user, and the identity of the computer. Acronym: IDA. (see Identity Awareness).
Use Cases
-
To prevent cyber-attacks, Check Point requires access to your third-party Identity Provider to retrieve and report identity of the users attacked.
-
Administrators can enforce different sets of rules for different users and groups. After you integrate Identity Provider with Harmony Connect, you can select users and groups within the security policy
 Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection..
Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection..
To configure Okta as an Identity Provider:
-
 Verify your domain
Verify your domain
-
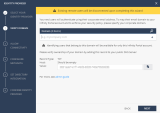
On the Verify Domain page, enter your organization domain.

Note - You need this step to ensure successful identification for all the users that belong to your organization and connected behind your branch offices. To learn more on the process, see Domain Verification.
-
The DNS record is generated below.
Click to copy this generated DNS record value.
-
Enter this generated DNS record to your DNS server as a TXT record.
-
Click Next on the Verify Domain page.
Check Point makes a DNS query attempt to verify your domain configuration.

Note - It may take some time until the DNS record is propagated and can be resolved.
-
-
 Create an application in the Okta Portal
Create an application in the Okta Portal
-
Log in to your Okta Portal.
-
Make sure the view is set to Classic UI (not Developer Console).
-
Navigate to Applications and click Add Application.
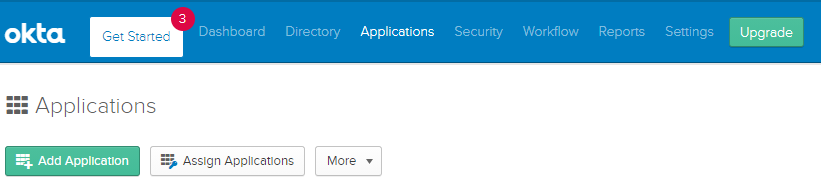
-
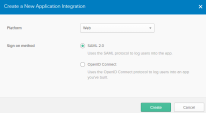
Click Create New App.
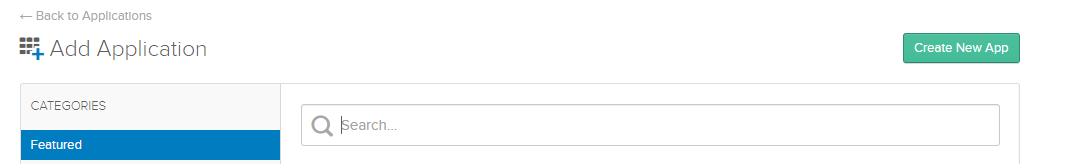
The Create a New Application Integration panel opens.
-
For Platform, select Web, and select SAML 2.0 for Sign on method. Click Create.
You are now in Create SAML Integration.
-
In General Settings, set the application name to Check Point Harmony Connect and click Next.
-
-
 Allow connectivity
Allow connectivity
-
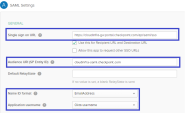
In the Allow Connectivity page, copy the Entity ID and the Reply URL.
-
Go back to the Okta Portal and edit the SAML settings:
-
-
 Set user and group attributes
Set user and group attributes
-
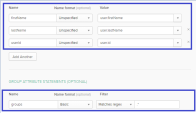
In the same SAML settings page, set attribute statements:
-
Name - firstName
Name format - unspecified
Value - user.firstName
-
Name - lastName
Name format - unspecified
Value - user.lastName
-
Name - userId
Name format - unspecified
Value - user.id
-
-
Set group attribute statement:
Name - groups
Name format - Basic
Filter - Matches regex, value: .*
-
Click Next.
-
Click Finish.
-
-
 Upload Federation Metadata file
Upload Federation Metadata file
-
Create Metadata file (available in the Classic UI view only):
-
After you create the metadata XML file in the Okta Portal, go to the Allow Connectivity page in the Check Point Infinity Portal and click Next.
-
In the Configure Metadata page, upload the Federation Metadata XML that you created in your Okta Portal.

Note - Check Point uses the service URL and the name of your Certificate to identify your users behind the sites.
-
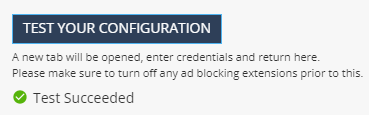
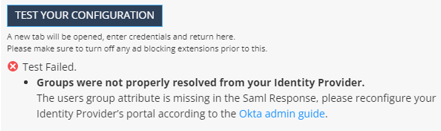
Click Test your configuration to test your Identity Provider configuration.
-
Enter the Identity Provider credentials. This tests the configuration and shows the result:
Test passed:
Test failed:
-
Click Next.
Check Point verifies the metadata of your Identity Provider.
-
-
 Set up Users and Groups Synchronization
Set up Users and Groups Synchronization
Set up permissions to allow selection of users and user groups from your Okta directory in the Harmony Connect Policy.
-
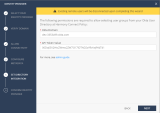
In the Okta Portal, check your Okta domain. Usually, this name appears in the address bar and in your account name.
-
Click the icon on the right to the Okta domain name to copy it.
-
Paste the Okta domain name in the Okta Domain field on the Set Directory Integration page of the Identity Provider wizard.
-
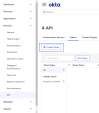
Back in the Okta Portal, navigate to Security > API > Tokens and click Create Token.
-
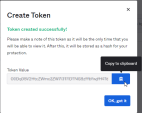
In the window that opens, enter the token name and click Create Token.
The window shows the Token Value that you must copy; otherwise, you can lose it.
-
Click the icon on the right of the Token Value to copy it to the clipboard.

Best Practice - Check Point recommends you save the Token Value in a separate file to retrieve it when it is required.
-
In the Harmony Connect Identity Provider wizard, on the Set Directory Integration page, paste the Token Value into the API Token Value field.
-
To test the users and group synchronization between the Infinity Portal and Identity Provider, click Start User and Group Sync Test.
If the test fails, repeat step Set up users and groups synchronization to reconfigure the user and group synchronization parameters.
-
Click Next.
-
-
 Confirm Identity Provider Integration
Confirm Identity Provider Integration
In the Confirm Identity Provider page, click Add to complete the wizard.
The Identity Provider installation is ready. Follow the steps below to complete the integration of the Okta Identification.
-
 Enable Identity Awareness
Enable Identity Awareness
(Optional) When you configure your Identity Provider and set the list of the excluded IP or network addresses, click Enable Identity Awareness for remote users or Enable Identity Awareness for branch sites or both and click Apply Changes.

Note - After the Identity Awareness update completes, a new notification appears on the Infinity Portal Notifications
.
To disable Identity Awareness, clear the selection.
-
 Bypass Authentication
Bypass Authentication
When you enable Identity Awareness, you can enter one or more IP addresses for Check Point to bypass. The traffic from these IP addresses is not redirected to the Identity Provider authentication page. Use this for devices such as printers, servers, or Internet of Things (IoT).
To add the bypass authentication in the Identity Awareness window:
-
Go to Policy > Identity Awareness > Bypass authentication from these sources.
-
Enter the IP address and click [+] to add it.
-
Click Update.

Note - After the Identity Awareness update completes, a new notification appears on the Infinity Portal Notifications
.
-
-
 Enforce access control rules for specific users and groups
Enforce access control rules for specific users and groups
To get policy enforcement for users and groups, add users and groups to the policy: